How to Secure Your Network Identities
GovLoop
DECEMBER 6, 2023
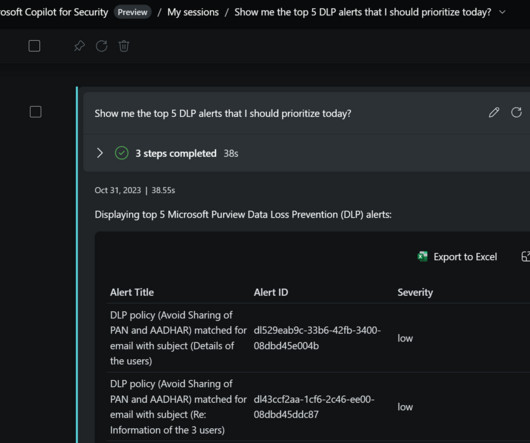
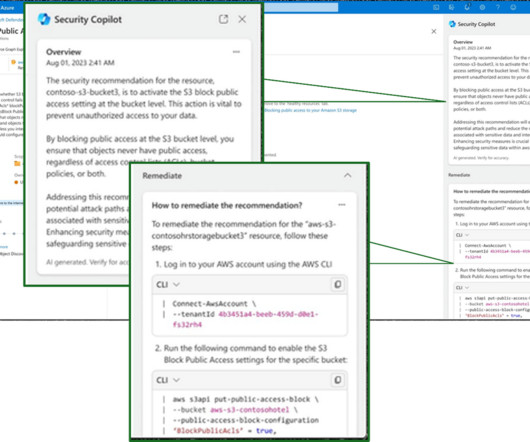
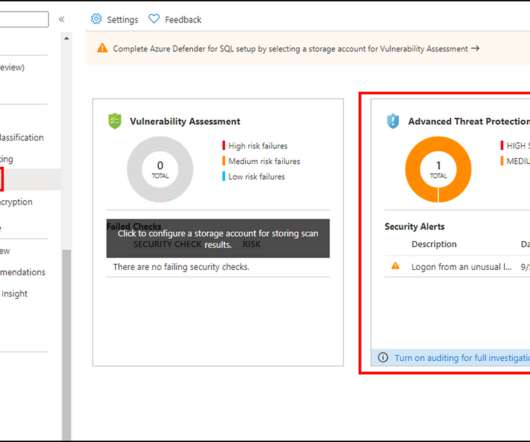
Cloud computing has dramatically changed how agencies offer services, much like smartphones have transformed how people access and use information. But these new data-sharing opportunities create new identity-related risks. Well, I’m now protecting my identity.’” It’s the new network perimeter, she explained.







































Let's personalize your content