Google Ad Grants Improve Your Library’s Chances of Being Found in Search: How To Apply and Manage This Incredible Opportunity
Super Library Marketing
APRIL 22, 2024
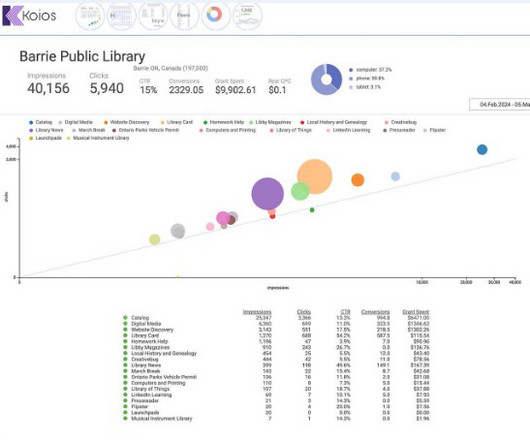
Koios has successfully applied for and managed Google Ad Grants for public libraries since 2017. First, you create a Google for Nonprofits account,” explains Maggie. Google’s policies require active management of advertising accounts, which means they expect you to check the account at least once per month,” explains Maggie.

































Let's personalize your content