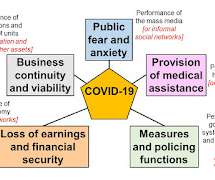
Covid-19: Elements of a Scenario
Disaster Planning and Emergency Management
MARCH 11, 2020
It is now more than ten years since there was a general push to induce countries to plan for pandemics (WHO 2005). US Homeland Security Council 2005, UK Government 2008), while in others it did not. In Britain, they also include the Brexit negotiations and the shape of the post-Brexit economy that will emerge after 2020.









Let's personalize your content