- Home
- Public Sector
- Public Sector Blog
- Microsoft Security Copilot and NIST 800-171
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Security Copilot and NIST 800-171
It is with bated breath that we await the publication of a Proposed Rule and final draft of Cybersecurity Maturity Model Certification (CMMC) 2.0. Simultaneously, the National Institute of Standards and Technology (NIST) just released the final draft of NIST Special Publication 800-171 Revision 3 (NIST 800-171r3) and initial draft of NIST 800-171Ar3, the assessment requirements for NIST 800-171r3. These publications are important because one of the primary requirements for CMMC is that organizations will need to implement most, if not all, of NIST 800-171r3’s controls for Level 2 certification.
Many commercial businesses in the Defense Industrial Base (DIB) with current and future CMMC requirements have relied on native security solutions in Microsoft 365 GCC/GCC High and Azure Government to meet previous iterations of NIST 800-171. DIB organizations have implemented these native solutions to various degrees of maturity, and staffed and trained their organizations to manage them or relied on a Managed Security Service Provider (MSSP) to do so. Thankfully NIST 800-171r3 is not a significant uplift from previous versions per the final draft, and new AI technologies may generate additional ROI on previous investments.
Implementation and management of cybersecurity technology, to meet a regulatory requirement or not, has financial implications. Thus, it is promising to see early reports of organizations reducing time and resource constraints by deploying Microsoft Security Copilot in private preview and the early access program. Despite no public timeline on the availability of Microsoft Security Copilot (Security Copilot) in Microsoft’s US-sovereign cloud offerings, it’s worthwhile to explore how companies in the DIB may use these AI-powered capabilities to meet NIST 800-171r3 security requirements, detect and respond to threats more efficiently, and ultimately defend against threats with finite or limited resources.
System and Information Integrity (3.14.)
3.14.1. Flaw Remediation
There are many places to start within the framework, but this requirement family is a great launching point. The first set of requirements within the family is 3.14.1 Flaw Remediation and asks organizations to “Identify, report, and correct system flaws.” Security Copilot’s power is most evident when reasoning over a multitude of systems and the signals they generate to identify flaws or potential vulnerabilities. In the unified Microsoft Defender XDR portal, Security Operations Center (SOC) analysts and security administrators can reason over incidents or known vulnerabilities. Security Copilot can explore attack path analysis to expose vulnerabilities across M365, Azure, AWS, and GCP. Then after understanding the attack path intuitively suggest to the SOC user where this vulnerability may also exist across the environment and generate the KQL query to investigate further.
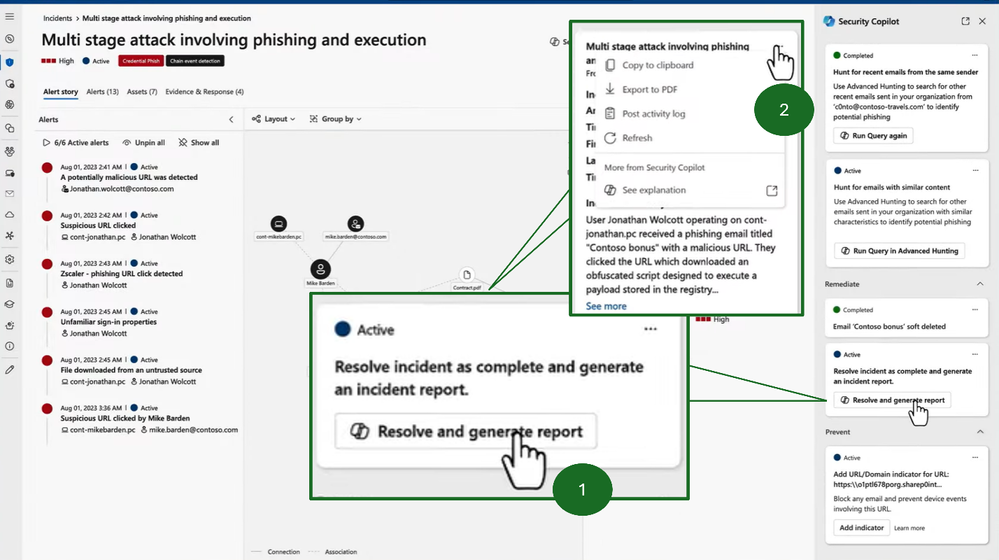
Security Copilot expedites and simplifies the SOC user’s ability to identify the extent, severity, and resolution of the flaw all by using natural language prompts. Moreover, the reporting functionality shown below on a sample incident response demonstrates how users can also easily report to designated personnel. This is a phishing related incident, but software and firmware related risks can also be identified and remediated.
NIST states that flaws can be “discovered during security assessments, continuous monitoring, incident response activities, and system error handling”. Organizations now can conduct this degree of discovery across all systems in the environment with machine speed and seamlessly provide a list of recent security flaw remediation actions to an assessor. Security Copilot enables companies to meet this requirement, but also early studies show Security Copilot delivered gains in efficiency up to and above 60 percent for tasks like preparing reports.
3.14.2. Malicious Code Protection
DIB companies are required to implement, configure, and update “malicious code protection mechanisms” to “perform scans” and “block”/”quarantine malicious code” or take other actions. At Microsoft Ignite several features were discussed in detail or announced around automatic attack disruption and decoy generation for malicious activity on the endpoint. Not only are security professionals gaining these powerful features in Microsoft Defender XDR, Sentinel and Security Copilot are fully imbedded into the same platform experience. Additionally, Microsoft Defender for Cloud signals are integrated to also provide users with a comprehensive vantage point into all areas where malicious code can be inserted, including structured and unstructured data in cloud infrastructure.
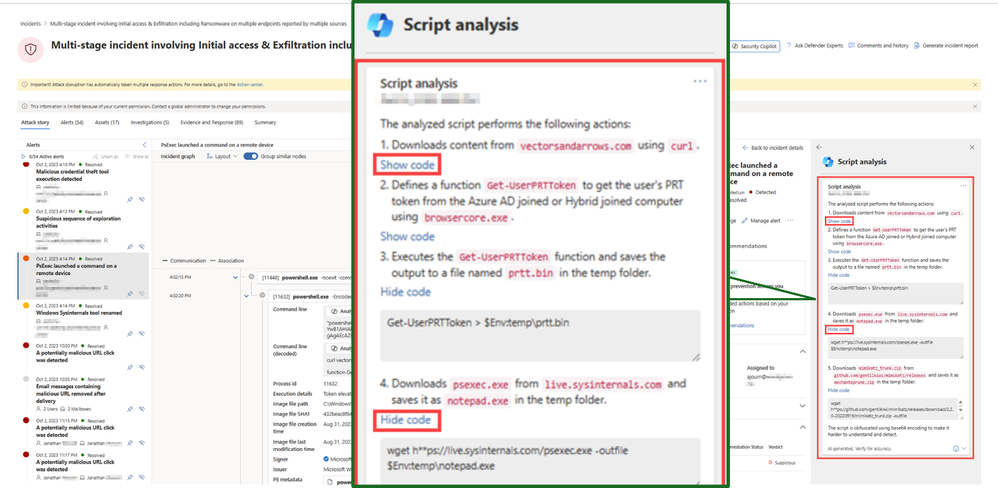
The breadth of signals aggregated into a single platform can be a significant time saver for users who have traditionally had to toggle between multiple portals and understand how each tool functions. Security Copilot brings additional relief to SOC analysts who do not have the time or skillset to analyze malicious code signals across endpoints, systems, applications, etc. Users can more quickly assess rather or not malicious code has been injected across the entire estate at machine speed, and Security Copilot elevates the user’s ability to also dissect script or code-based attacks. Specifically, Security Copilot can scan a significant number of PowerShell, batch, and bash lines in moments and offer a detailed explanation in natural language as to why a certain segment of code or script is malicious. Lastly, it can take this analysis and help the user identify other areas where this script may be running and how to mitigate.
3.14.3. Security Alerts, Advisories, and Directives
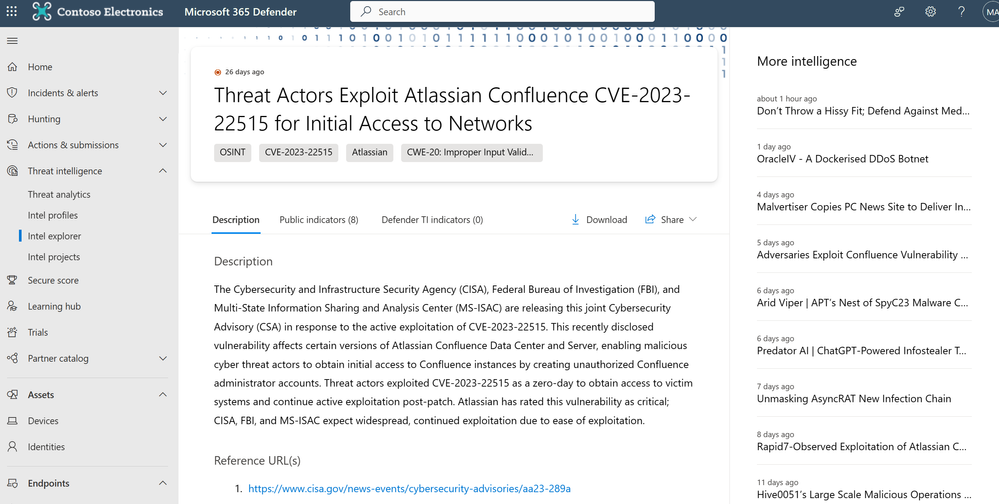
Microsoft Defender Threat Intelligence already “receive(s) system security alerts, advisories, and directives” for DIB organizations to review and disseminate internally. The traditional experience is shown below where users can research the nature of a threat and various indicators of compromise.
Now, with Security Copilot, cybersecurity professionals are intelligently notified of the most critical exposures for their organization based upon AI analysis of the environment. This allows users to prioritize threats and instantly summarize content with Security Copilot for situational awareness and dissemination. Moreover, Security Copilot also enables organizations to shorten the gap between receiving advisories to implementing the guidance within them and according to “established time frames”. From the Microsoft Defender XDR portal, a single user with proper access can see the threat, ask Security Copilot further questions about the threat, identify possible exposure, and take suggested action or assign the action based on recommendations.
3.14.6 System Monitoring
This requirement is far reaching and necessitates the ability to monitor for “attacks and indicators of potential attacks”, “unauthorized connections”, “unauthorized use of the system [holding or accessing CUI]”, and “inbound and outbound communications” for unusual or unauthorized activities. Security Copilot is now imbedded or integrated across each facet of the Microsoft toolset. Users can quickly investigate potential attack paths in Azure Government and Microsoft 365, as well as illuminate identity-based threats such as elevated privileges, access policy changes and more. Better yet, Security Copilot can enrich attack context to include information from Microsoft Purview. This means the user can understand if an effected system includes CUI or other sensitive information and provide a thorough description of “access patterns” and all “characteristics of access”.
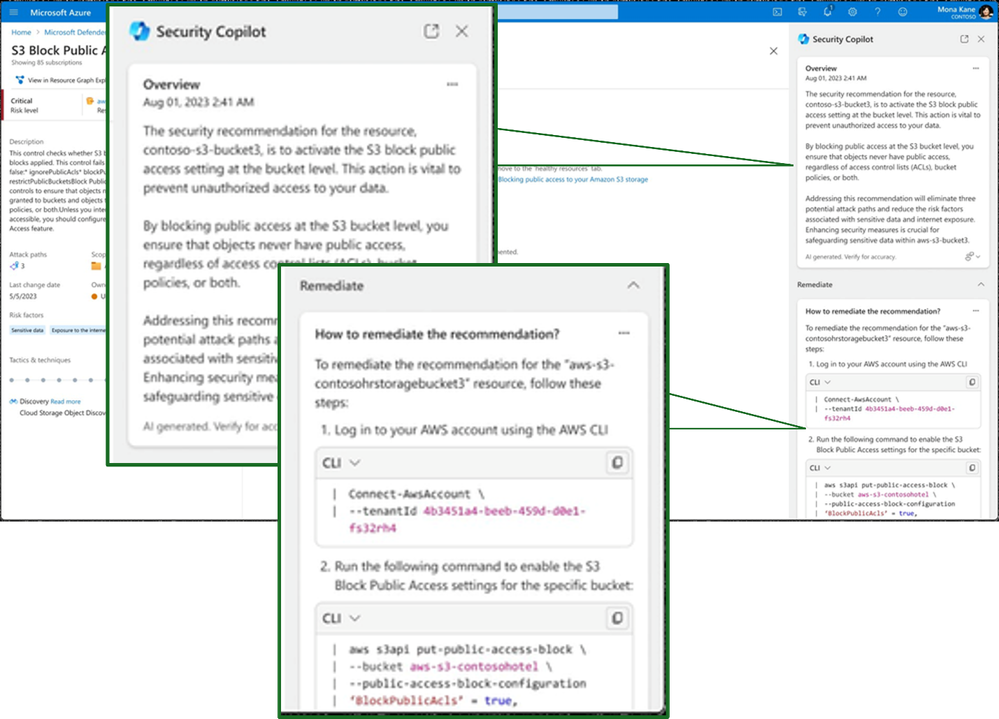
Additionally, Security Copilot can reason over network and device access alike to intelligently alert cybersecurity analysts of unauthorized connections. With integration in Microsoft Intune, Security Copilot can generate suggestions on device policies and simulate the outcomes without the security administrator having to create an end-to-end test scenario or conjure a policy to address new scenarios, which can be time consuming. Defender for Cloud integration shown below allows Security Copilot to provide intuitive explanations of unauthorized connections or potential threats, as well as paths to remediation.
Meeting NIST 800-171 with Limited Resources
DIB companies have voiced with every regulatory release during comment periods that cybersecurity demands exceed their collective budgetary ability and personnel capabilities. Microsoft Security Copilot is an advanced security solution that helps companies protect CUI and prepare for CMMC assessment by elevating the skillset of every cybersecurity tool and professional in the organization. It offers a range of features, including automated threat detection, real-time alerts, and advanced analytics, to help companies stay ahead of potential threats and safeguard CUI. With Microsoft Security Copilot, companies can streamline their security and compliance processes, making it easier to manage and protect data.
Covered at Ignite and within this blog, a recent study to measure the productivity impact for “new in career” analysts found participants using Security Copilot demonstrated 44 percent more accurate responses and were 26 percent faster across all tasks.3
According to the same study:
- 86 percent reported that Security Copilot helped them improve the quality of their work.
- 83 percent stated that Security Copilot reduced the effort needed to complete the task.
- 86 percent said that Security Copilot made them more productive.
- 90 percent expressed their desire to use Security Copilot next time they do the same task.
Attackers will adapt techniques, threats will grow, NIST 800-171 may go through additional revisions, but resources could be static for DIB companies. Security Copilot supercharges the teams and tools we have today for the threat landscape tomorrow.
This blog is one in a series to cover applications of Microsoft Security Copilot for NIST 800-171.
Additional Resources
Preparing for Security Copilot in US Government Clouds
Level-up Your Threat Intelligence Program with Microsoft
Microsoft unveils expansion of AI for security and security for AI at Microsoft Ignite
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.