- Home
- Public Sector
- Public Sector Blog
- Microsoft Sentinel: Maturity Model for Event Log Management (M-21-31) Solution
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
As cyber-attacks grow in number and severity against federal government systems, comprehensive cloud security mechanisms are more important than ever. Recent attacks, including SolarWinds, highlight the necessity of having sufficient logs for investigation and response when attacks occur.
Recently, the Biden Administration has introduced OMB M-21-31 which requires federal government customers to rapidly move towards log event management capabilities to improve the ability to investigate and respond to cloud security attacks.
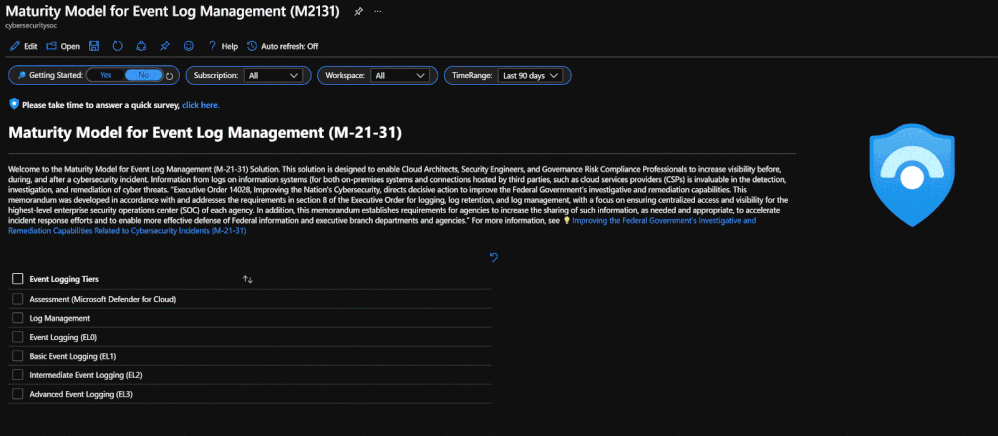
This initiative guides federal agencies to understand log event management and is broken up into four tiers of maturity. For customers ingesting data from multiple sources, cloud providers, and on-premises environments, it is a daunting task to consider begin to address the complex requirements of M-21-31.
We are excited to announce the Microsoft Sentinel: Maturity Model for Event Log Management (M-21-31) Solution. This solution consists of (1) Workbook, (8) Analytics Rules, (4) Hunting Queries, and (3) Playbooks.
Watch the demo to learn more! Microsoft Sentinel: Maturity Model for Event Log Management Solution - YouTube
Content Use Cases
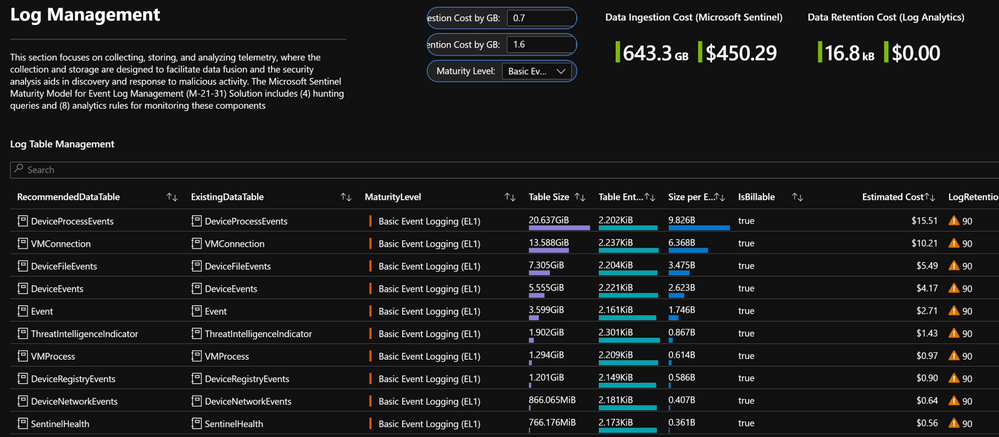
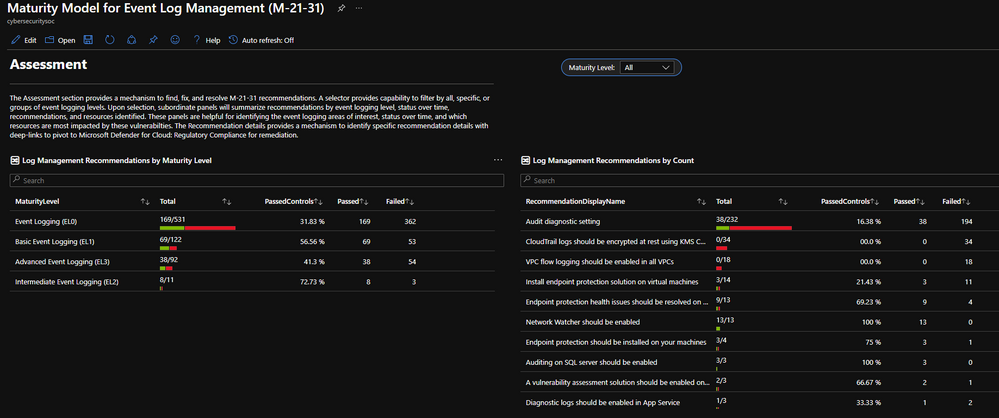
- Microsoft Sentinel: Maturity Model for Event Log Management (M-21-31) Workbook: The solution provides actionable insights into log management posture and intuitive steps for remediation to driving compliance across event logging maturity levels. The workbook serves as a starting point for designing and reporting event log management capabilities by providing visibility into current posture mapped against the four maturity tiers.
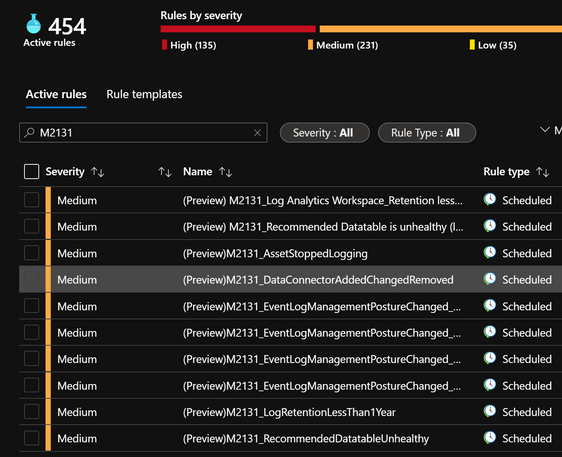
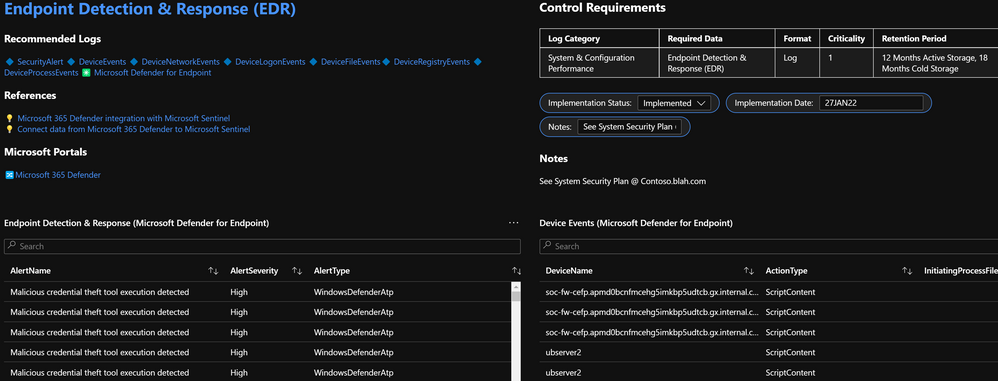
- (8) Analytics Rules: Analytics rules and hunting queries empower security teams with ongoing monitoring and assessment. Analytics rules ensure compliance over time by tracking the agent, asset, data connector health and more to ensure log flow over time.
- Recommended Data table is unhealthy (last logged received drop)
- Data Connector added, changed, or removed
- Asset stopped logging (heartbeat)
- Log Analytics Workspace: Active Storage is less than 12 Months
- Event Log Management Posture Changed (Event Logging EL0)
- Event Log Management Posture Changed (Basic Event Logging EL1)
- Event Log Management Posture Changed (Intermediate Event Logging EL2)
- Event Log Management Posture Changed (Advanced Event Logging EL3)
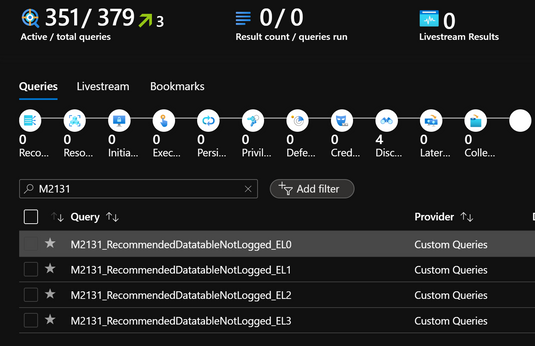
- (4) Hunting Queries: Hunting queries provide a proactive way to understand your logging environment, relative to the four maturity levels.
- Recommended Datatable is not logged
- Event Logging (EL0)
- Basic Event Logging (EL1)
- Intermediate Event Logging (EL2)
- Advanced Event Logging (EL3)
- Recommended Datatable is not logged
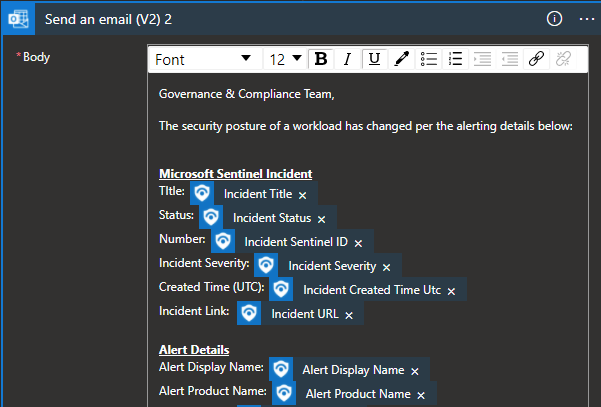
- (3) Playbooks: Playbooks drive automated, consistent response, ensuring security teams can focus their time on what’s important: providing remediation and response based on collected insights from Microsoft Sentinel, rather than navigating across portals for relevant data.
- Notify Log Management Team
- Alert triggers email and teams chat to log management team
- Open DevOps Task
- Alert Triggers an Azure DevOps task to address the Microsoft Defender for Cloud policy recommendations.
- Open JIRA Ticket
- Alert Triggers a JIRA Ticket to address the Microsoft Defender for Cloud policy recommendations.
- Alert Triggers a JIRA Ticket to address the Microsoft Defender for Cloud policy recommendations.
- Notify Log Management Team
Solution Benefits
- Single pane of glass for aggregating, managing, and actioning data from 25+ Microsoft products to address M-21-31 Logging requirements
- Deep links for seamless pivots between products
- Over-time analysis for more complete understanding of security and compliance posture
- One-click, customizable reporting
- Leverage pre-written KQL queries to gain insights from log telemetry with the option to customize for further analysis
Reporting
- 150+ visualizations, recommendations, queries across logs, azure resource graph, policy, metrics, and APIs
- Single-click report exports via Print Workbooks feature
- Integration with Microsoft Defender for Cloud: Regulatory Compliance Assessments
Audience
- Implementers: Design + Build
- Assessors: Audit + Assessment
- Analysts: Monitor + Respond
- Decision Makers: Situational Awareness
- MSSP: Consultants
Getting Started
This content is designed to enable a Maturity Model for Event Log Management and aligning with the M-21-31 requirements. Below are the steps to onboard required dependencies, enable connectors, review content, and provide feedback.
- Onboard Microsoft Sentinel and Microsoft Defender for Cloud
- Add the Azure Security Benchmark and NIST SP 800-53 Assessments to your dashboard
- Microsoft Defender for Cloud > Regulatory Compliance > Manage Compliance Policies > Select Subscription > Expand Industry & Regulatory Standards > Add More Standards > Add ASB and NIST SP 800-53 Assessments.
- Continuously Export Microsoft Defender for Cloud Data
- Microsoft Defender for Cloud > Enviornment Settings > Select Subscription > Continuous Export > Log Analytics Workspace > Ensure Security Recommendations (All Selected: Low/Medium/High) and Regulatory Compliance (All Standards Selected) is checked > Select Sentinel Workspace as Target > Save
- Deploy Solution
- Commercial: Azure Marketplace > Search Maturity Model for Event Log Management > Configure Options > Create
- Government: Access Solution on Microsoft Sentinel’s GitHub Repo. Select Deploy to Azure Government Button > Configure Options > Create
- Review the Microsoft Sentinel: Maturity Model for Event Log Management (M-21-31) Workbook
- Microsoft Sentinel > Workbooks > Search Maturity Model for Event Log Management (M-21-31)
- Review/Enable Analytics Rules
- Microsoft Sentinel > Analytics > Search M-21-31
- Review Hunting Queries
- Microsoft Sentinel > Hunting > Queries >Search M-21-31
- Review Playbook Automation
- Microsoft Sentinel > Automation > Active playbooks > Search Notify-LogManagementTeam > Enable
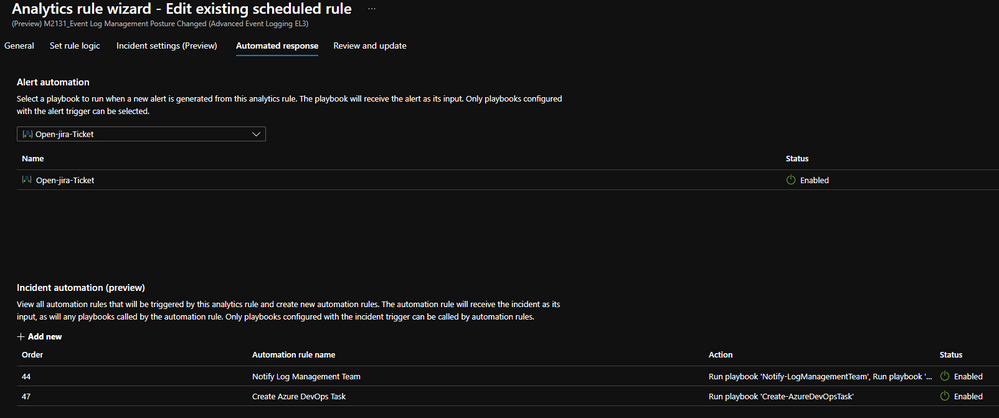
- Create Automation Rule
- Analytics > Search M-21-31> Edit > Automated Response > Add new > Select Actions: Run Playbook > Select Notify-LogManagementTeam and configure automation options > Review > Save > Mirror configuration across all M-21-31 analytics rules. Note, Open JIRA Ticket and Create Azure DevOps Task are additional Playbooks available per organizational requirements.
9. Review the content and provide feedback through the survey
Learn More About Meeting the Cybersecurity Executive Order with Microsoft Security
· Executive Order on Improving the Nation’s Cybersecurity
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.