- Home
- Public Sector
- Public Sector Blog
- Helping Federal organizations achieve CDM requirements Part 3 of 4 – Vulnerability Management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Welcome to part 3 of the 4-part blog series Helping Federal organizations achieve CDM requirements for What is on the Network – Vulnerability Management (Vul). You can find the previous 2 blog posts at the links below.
Part 1 (HWAM) Helping Federal organizations achieve CDM requirements Part 1 of 4 – What is on the Network (HWAM) -...
Part 2 (SWAM) Helping Federal organizations achieve CDM requirements Part 2 of 4 - Software Asset management - Mic...
Vulnerability Management (VUL)
Microsoft Defender Vulnerability Management (MDVM) is included in Microsoft Defender 365/Defender for Endpoint (MDE). This enables staff to deliver upon many of their extended detection and response (XDR) needs in a single portal located at https://security.Microsoft.com for commercial cloud and GCC customers, and https://security.microsoft.us/ GCC-H customers.
MDVM standard is included in the baseline price of Microsoft Defender for Endpoint (MDE), and Microsoft has also recently added a premium tier for MDVM that provides more advanced monitoring and assessment capabilities. For further information about standard vs. premium please refer to the following article Microsoft Defender Vulnerability Management | Microsoft Security.
When an endpoint (IOS, Android, Mac, Linux, Windows) is onboarded to the MDE service; MDE will continuously inventory software installed on each device and check the software against a known vulnerabilities database. For systems that have not been onboarded into MDE, there are a few methods that will be described below for performing vulnerability management against network devices and unmanaged devices.
MDVM Dashboard
To access MDVM, administrators simply connect to the Microsoft Defender 365 portal and navigate to the “Endpoints” section. Under Endpoints, the Vulnerability Management menu can be expanded to produce seven menus. The first menu is the “Dashboard”. The MDVM dashboard provides an executive view of an organization displaying information like Exposure score, Top security recommendations, Secure Score, Top exposed devices, Top vulnerable software, expired certificates, and remediation activities and is a great place to get an overview of the organization’s security posture.
Figure 1: Microsoft Defender Vulnerability Management
Security Recommendations
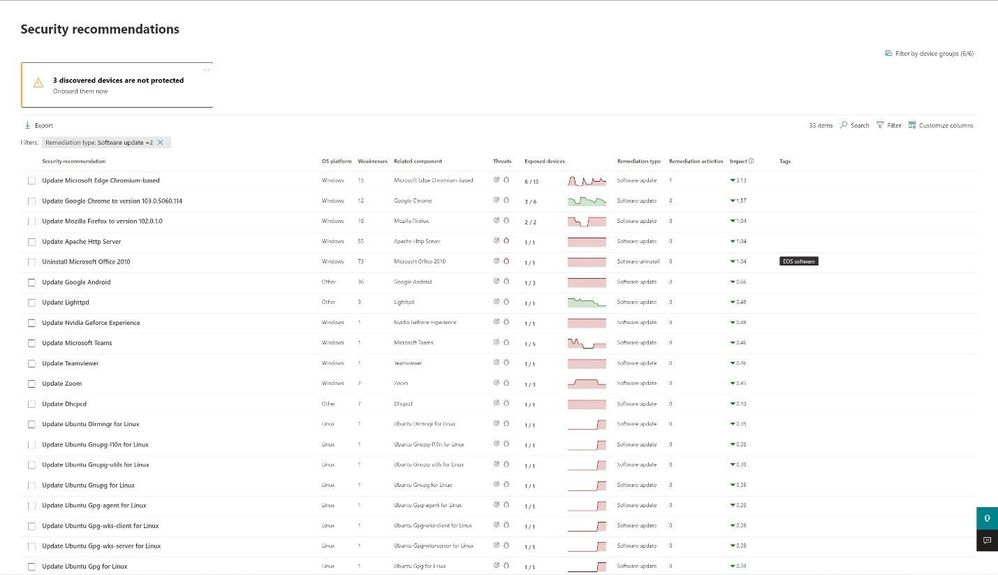
Selecting the Recommendations menu will present configuration and software recommendations to staff. Administrators can further filter the view by operating system, onboarded, not onboarded, software, configuration, and many other filters. By default, you will see a list of the currently installed software in your organization and how many known “weaknesses” each piece of software currently has. The threats column helps to identify if these weaknesses are being targeted in their organization, or if there are known active exploits in the wild.
Figure 2 Security recommendations
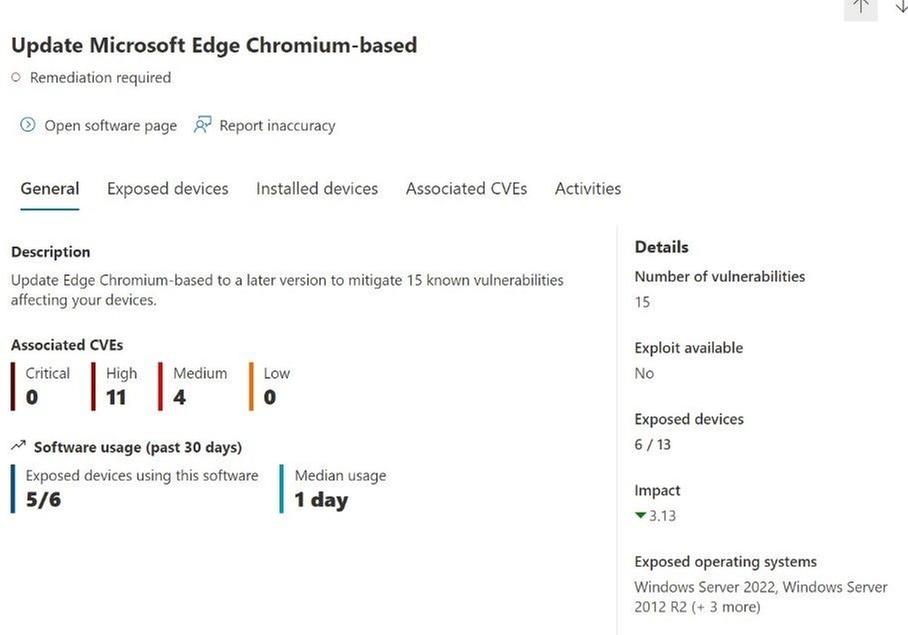
Upon selecting a recommendation, a window opens with an overview of the recommendation and a series of tabs showing the number of exposed devices, devices with the software installed, activities and any CVE’s related to the software.
Figure 3 Recommendations overview
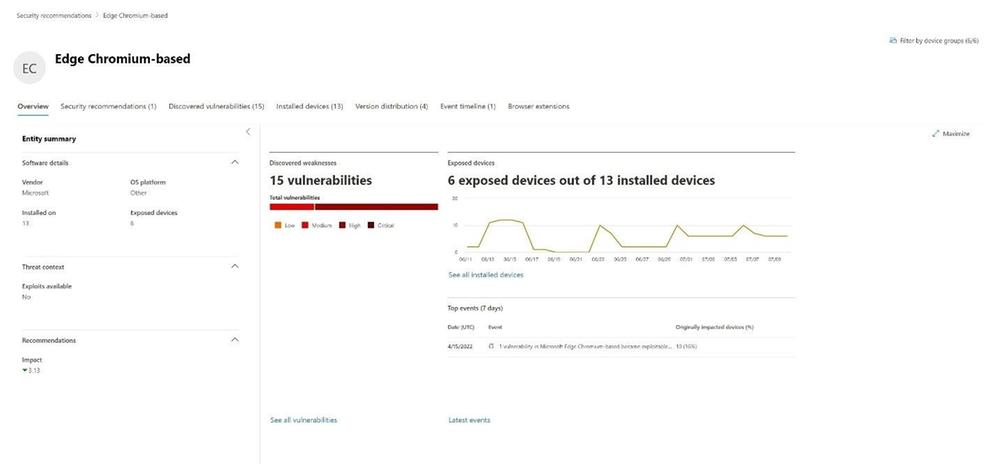
Staff can further select the “Open Software Page” to drill into a specific piece of software to better understand the vulnerabilities, installed devices, versions, event timeline, or browser extensions.
Figure 4 Software information view
Weakness Database
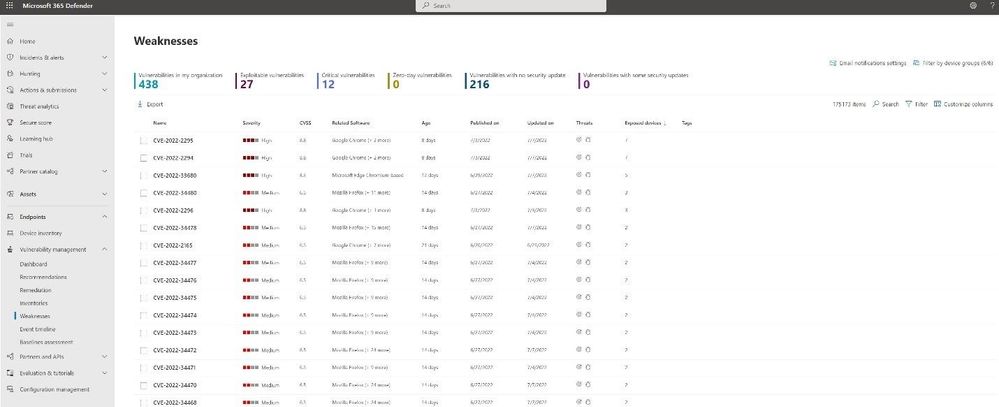
To understand if your organization is exposed to a CVE, MDVM provides a Weaknesses database that analysts can search to better understand a vulnerability. By default, the view is scoped to known weaknesses within an organization, but the filter can be changed to a global view to help search the entire database.
Figure 5 Weakness database
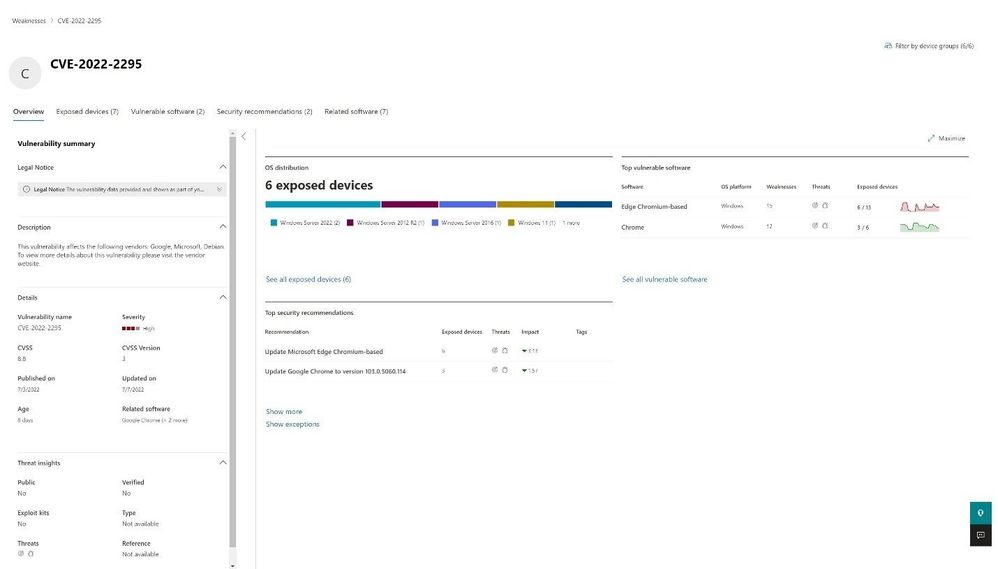
After selecting a weakness (CVE), an additional window will open that provides a description of the vulnerability to include the CVSS score, when it was updated, and various pieces of information.
Figure 6 Weakness Database selection
With more complex vulnerabilities like Log4j, often organizations may not understand all the related software that could be impacted by a CVE. By selecting the “Related software” tab, MDVM lists other pieces of software that may be exposed to a CVE to help organizations better understand their exposure and overall risk.
Figure 7 Related Software view
If an analyst selects the “Open Vulnerability page” button, a richer view of the vulnerability is opened helping staff gain deep insights into the vulnerability.
Figure 8 CVE information view
Event Timeline
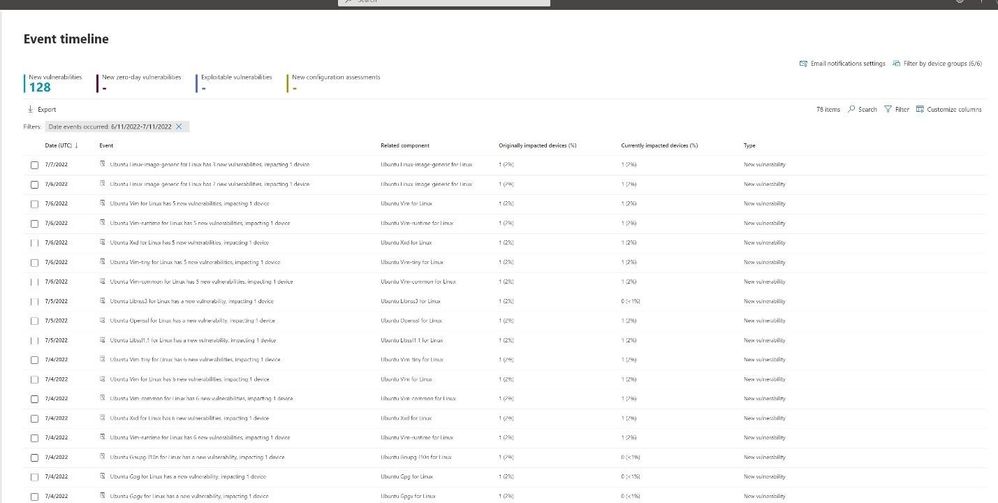
Understanding when an organization was first exposed to a weakness is critical. MDVM provides an event timeline that shows when each weakness was discovered, what percentages of devices were impacted when it was originally discovered, and what percentage of devices are currently impacted.
Figure 9 Event timeline
Network Devices and Unmanaged Devices
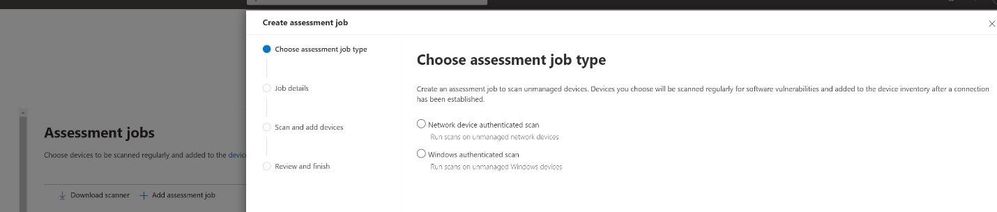
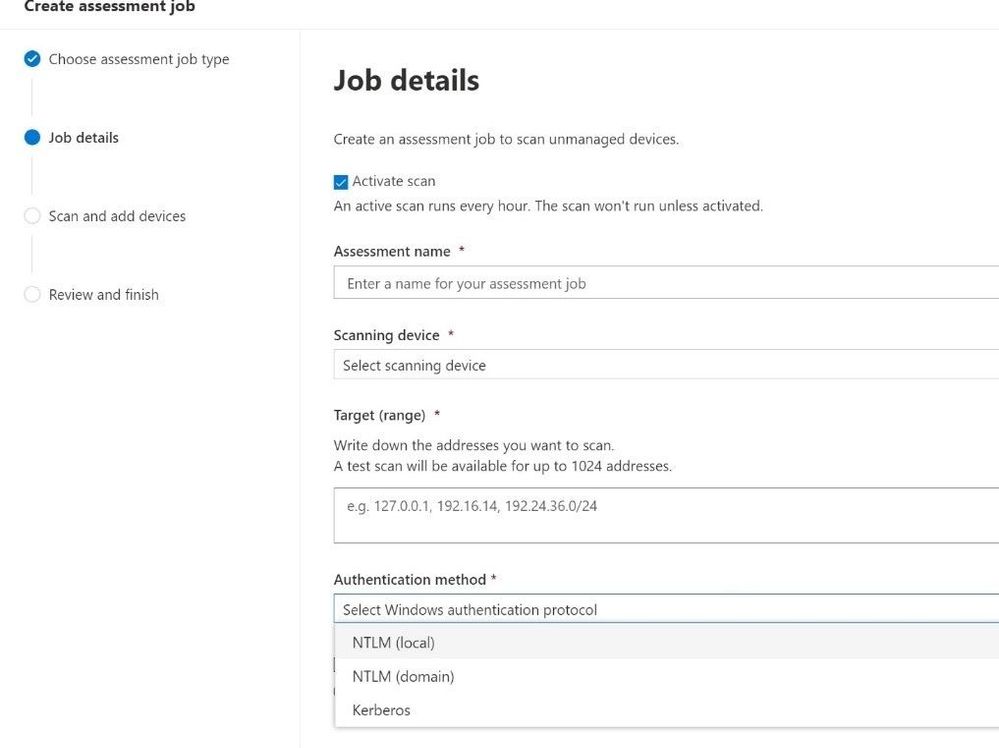
Earlier, I mentioned that MDVM can also discover vulnerabilities in unmanaged devices. This can be done in a few ways. The first, is via an authenticated scan. This method can be used for network devices or Windows devices that have not yet been onboarded into MDE. From the MDE setting menu, staff selects “Assessment jobs” and then selects which type of assessment they would like to perform.
- Network devices
- Windows authentication
Figure 10 Create Assessment job
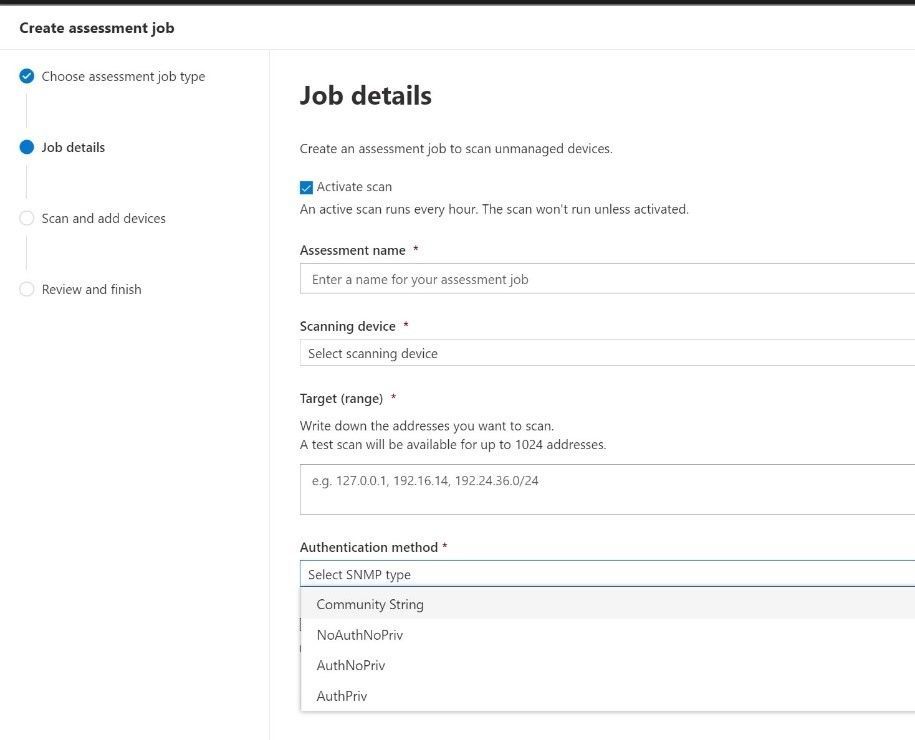
When selecting “Network device authentication scan” staff will input serveral pieces of information like the IP range, the scanning device, and the authentication settings for SNMP.
Figure 11 Network Device assessment
For windows endpoints the menu is similar, but with different Authentication methods (NTLM and Kerberos).
Figure 12 Windows Device assessment
The second method is done via active and passive probing on the network from endpoints. When MDE discovery is enabled, Windows nodes will actively or passively “probe” devices on the network to discover the asset and potential vulnerabilities.
Figure 13 MDE discovery settings
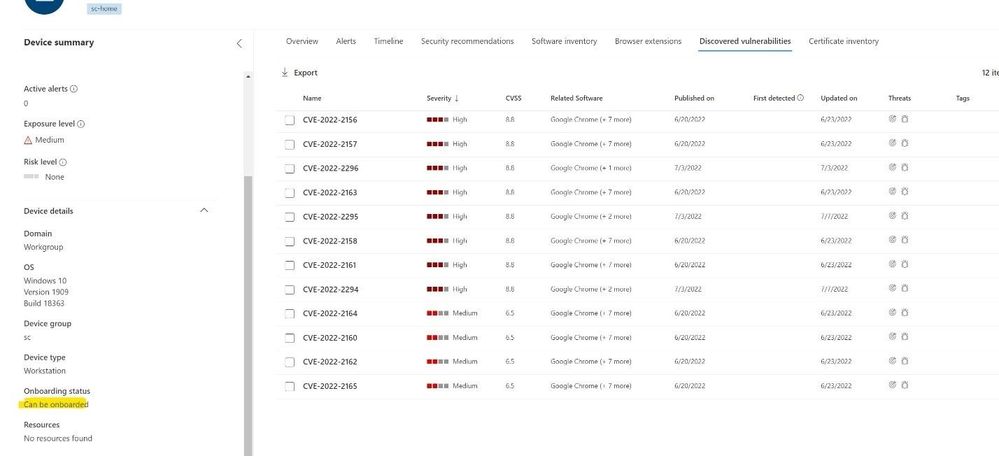
The below device was discovered on the network however, is not managed by MDE, nor are authenticated scans against this device. The device has a status of “Can be onboarded” but still lists several CVEs on the machine. This data is surfaced during active and passive scanning that is done via a managed MDE endpoint.
Figure 14 Unmanaged Node vulnerability information
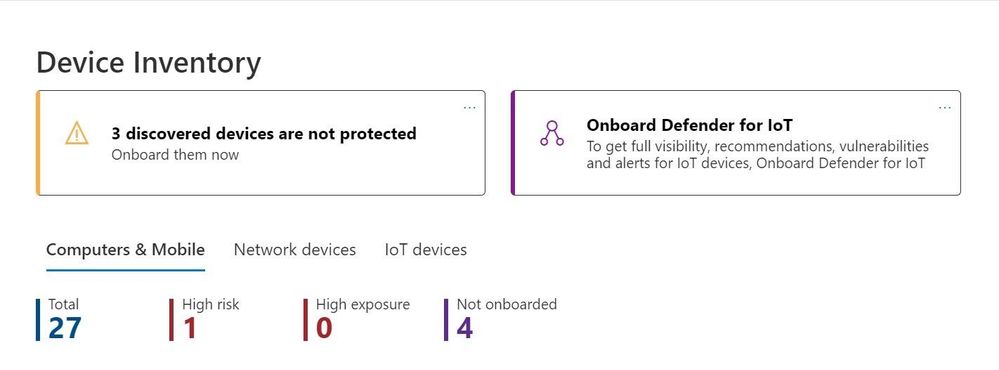
Device Inventory
Additionally, from the Device inventory page staff can view the vulnerability information of each device type from computer, mobile, network and IoT devices.
Figure 15 Device Inventory
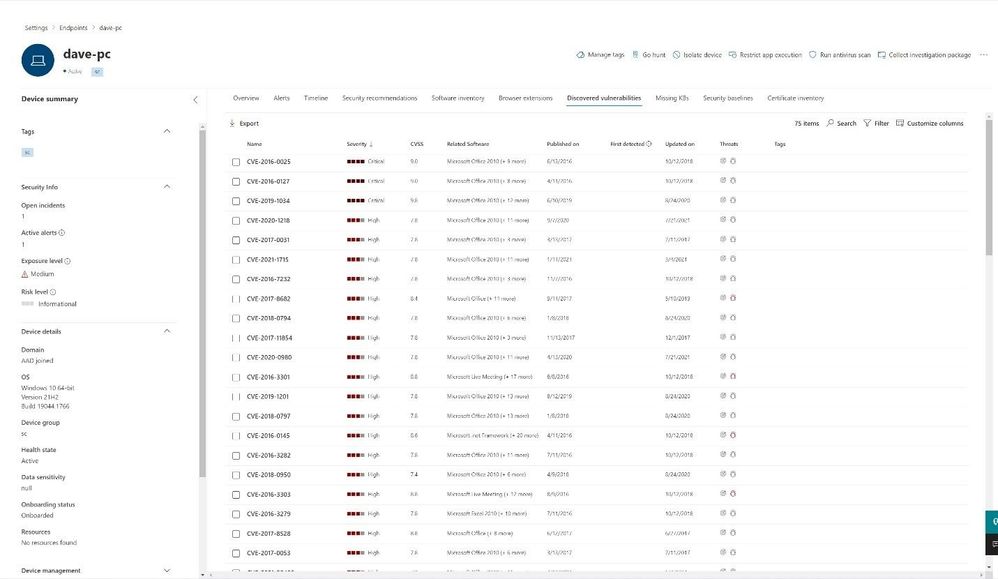
Selecting a device will present a device centric view that helps staff view a timeline, recommendations, browser extensions, discovered vulnerabilities, missing KBs, a security baseline, and certificate inventory.
Figure 16 Device level vulnerability view
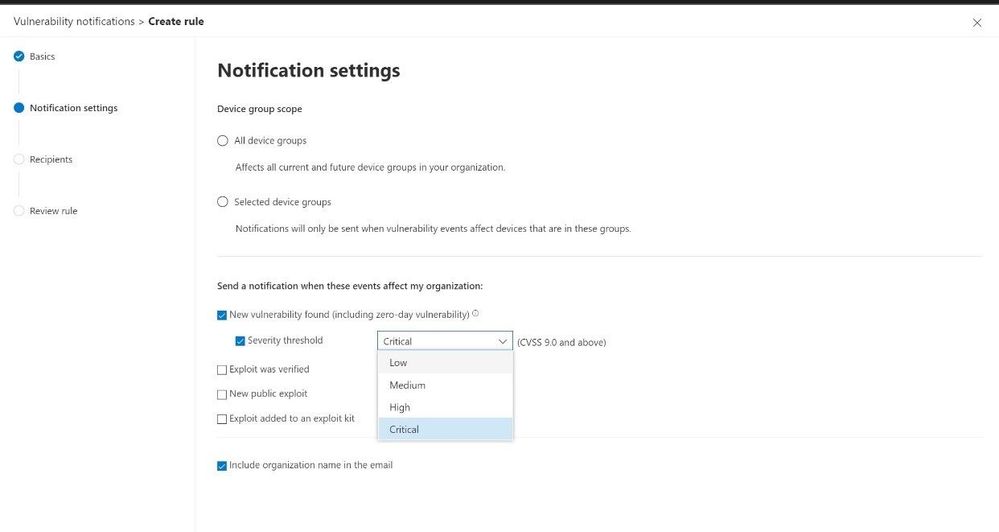
Notifications
Security staff are often overwhelmed with deadlines and data to manage, so it’s understandable that reminders or notifications when new vulnerabilities appear in the organization can be very helpful. Staff can configure a set of rules based on severity, new public exploit, and various other criteria. This helps busy staff receive reminders when new weaknesses appear in the organization and enables them to quickly drill into the information to see how exposed the organization may be.
Figure 17 Notification creation wizard
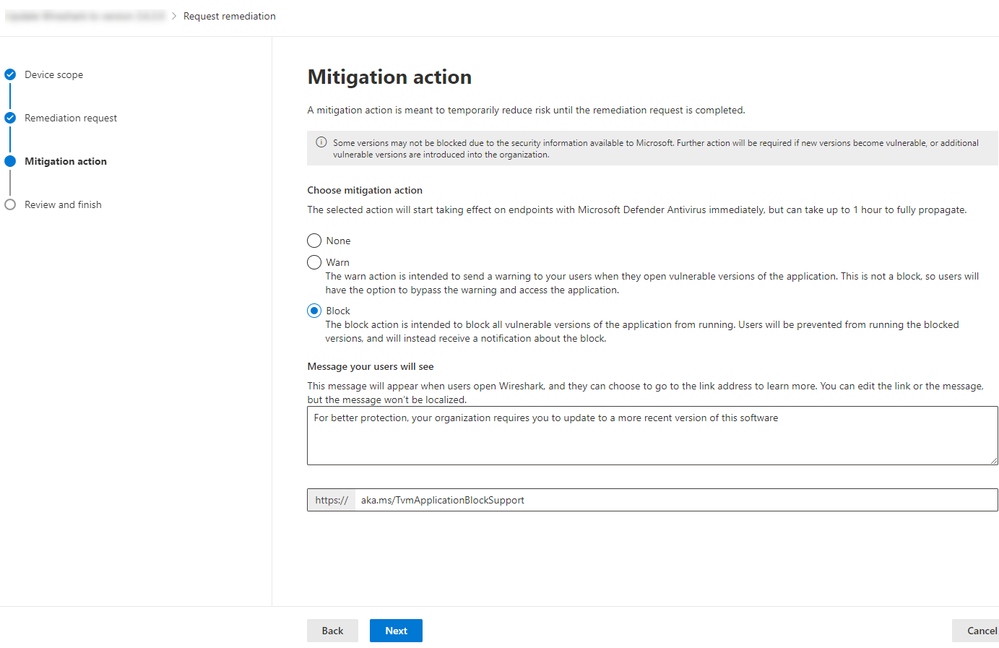
Blocking Vulnerable software
Discovering a vulnerability is just the first step to protecting the organizations. A vulnerability could be a zero day, where there is no patch or fix; or it could just take a long time to update applications across the enterprise. MDVM can perform remediation tasks that can block installed applications from running until the application is patched.
*At the time of this writing the feature is current in preview and more information can be found here Block vulnerable applications (beta) | Microsoft Docs
Figure 18 Mitigation action
After creating a warning or block remediation task, staff can view what blocks have been put in place and additional information about the block.
Figure 19 Mitigation action properties
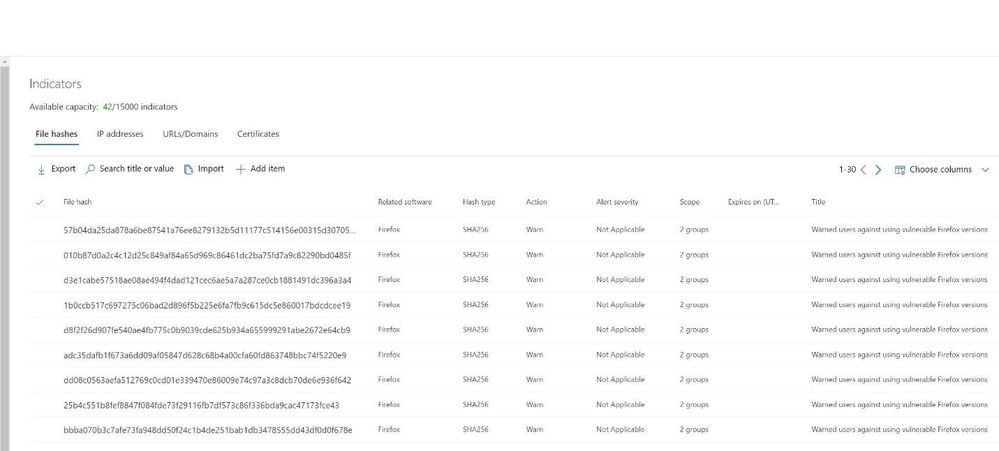
After a block is created, MDE creates a list of SHA256 hashes related to the blocked software that is used to verify which software should be blocked on the endpoints. Staff can see the hash information listed under the indicator’s settings.
Figure 20 MDE Indicators
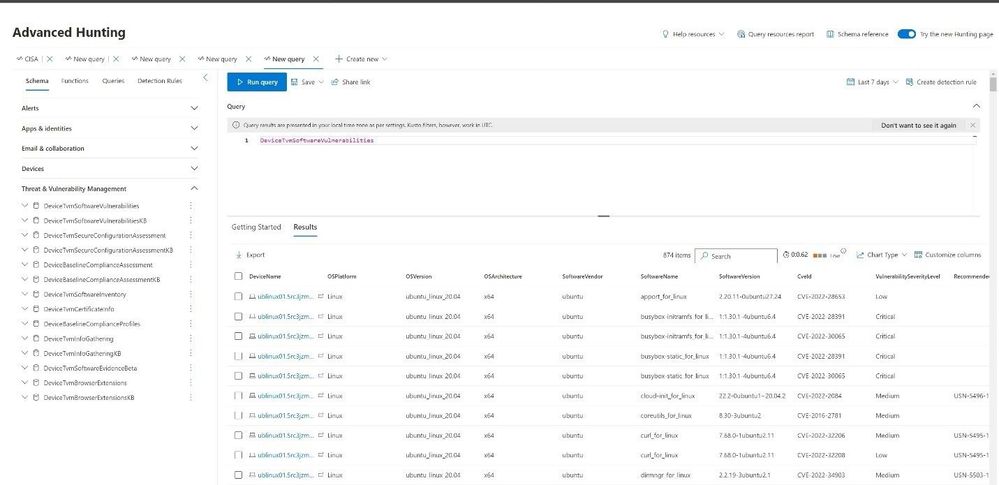
Advanced Hunting and API
Similar to software inventory, MDE stores the vulnerability data in the Threat and Vulnerabilities section in several tables within the Advanced Hunting interface. Using the powerful KQL query language, staff can create extensive queries related to vulnerability management, and combine those tables with various other data sets to get a complete picture of the organization. Since Microsoft Defender 365 hosts tables for the entire XDR solution staff can query information from various tools in this one location.
Figure 21 Advanced Hunting
Often organizations have dashboards or other data repositories where they would like to store vulnerability information. MDVM/MDE provides a rich set of APIs which can be queried to return the data set an organization may desire to put into another system.
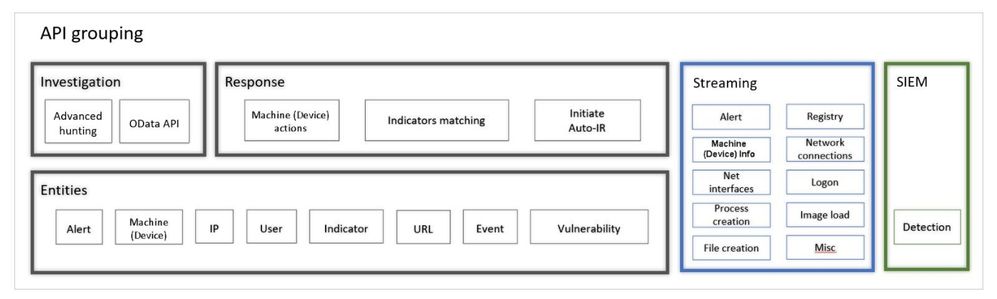
The Defender for Endpoint APIs can be grouped into three:
- Microsoft Defender for Endpoint APIs
- Raw data streaming API
- SIEM integration
Figure 22: MDE APIs
Microsoft Defender for Endpoint API is a multi-layered API that has two subcategories:
- Response API
- Investigation API
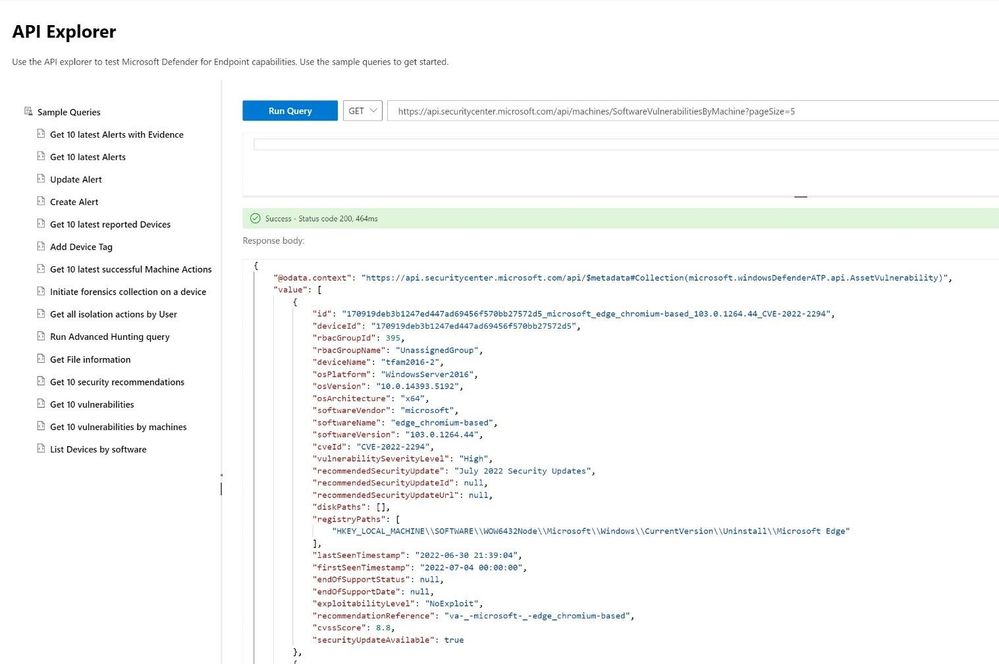
Using the built in API explorer tool can help staff test API calls to validate the correct data is returned and staff can even use the same KQL queries via the advanced hunting API or other built in API calls.
Figure 23 API explorer
Related articles:
- Microsoft Defender Vulnerability Management | Microsoft Docs
- Compare Microsoft Defender Vulnerability Management offerings | Microsoft Docs
- Hunt for exposed devices | Microsoft Docs
- Mitigate zero-day vulnerabilities | Microsoft Docs
- Vulnerabilities in my organization | Microsoft Docs
- Become a Microsoft Defender for Endpoint Ninja - Microsoft Tech Community
- Export software vulnerabilities assessment per device | Microsoft Docs
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.