- Home
- Public Sector
- Public Sector Blog
- Preparing for Security Copilot in US Government Clouds
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
With the announcement of Security Copilot back in March, there has been a growing demand to understand and expand the role of machine learning (ML) in security. This demand is especially apparent in the US government space, where these advancements have a direct impact on national security.
Security Copilot is the first generative AI security product to help defend organizations at machine speed and scale. It combines the most advanced GPT4 model from OpenAI with a Microsoft-developed, security-specific model, powered by Microsoft Security’s unique expertise, global threat intelligence and comprehensive security products. To bring the power of Azure OpenAI to government agencies, Microsoft is excited to launch an initial preview of Azure OpenAI Service in Azure Government in Q1 CY2024. While there is no roadmap for Security Copilot in Azure Government, given Security Copilot’s tremendous potential, customers are already asking how they can prepare to leverage Security Copilot once it is broadly available in US Government clouds.
To start, there are many security features across the Microsoft stack that leverage ML today:
- Fusion in Microsoft Sentinel, a correlation engine based on scalable machine learning algorithms, to automatically detect multistage attacks by identifying combinations of anomalous behaviors and suspicious activities that are observed at various stages of the kill chain
- User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel, behavioral profiles of an organization’s entities (such as users, hosts, IP addresses, and applications) across time and peer group horizon based on logs and alerts from Sentinel’s connected data sources
- Anomaly detection in Microsoft Defender for Cloud, Machine learning is applied to determine normal activity for deployments and then rules are generated to define outlier conditions that could represent a security event
- Automatic Attack Disruption in Microsoft 365 Defender, correlating millions of signals to identity and disrupt active ransomware, man-in-the-middle, and business email compromise attacks (Note: AAD is a recently released capability and is not yet available to GCC and GCC High customers. Please connect with your Microsoft Account team for product roadmap updates)
These are out of the box features that customers can turn on today, with minimal configuration required. These features benefit from the power of machine learning and help defenders respond at the speed of AI. These tools also give customers an opportunity to get hands-on with the security products that feed Security Copilot.
To that end, to be in the best position to take advantage of the AI capabilities afforded by Security Copilot when they do become more broadly available, customers should adopt Microsoft 365 Defender, Sentinel and Intune today. Security Copilot does not replace any of these products; it enhances them.
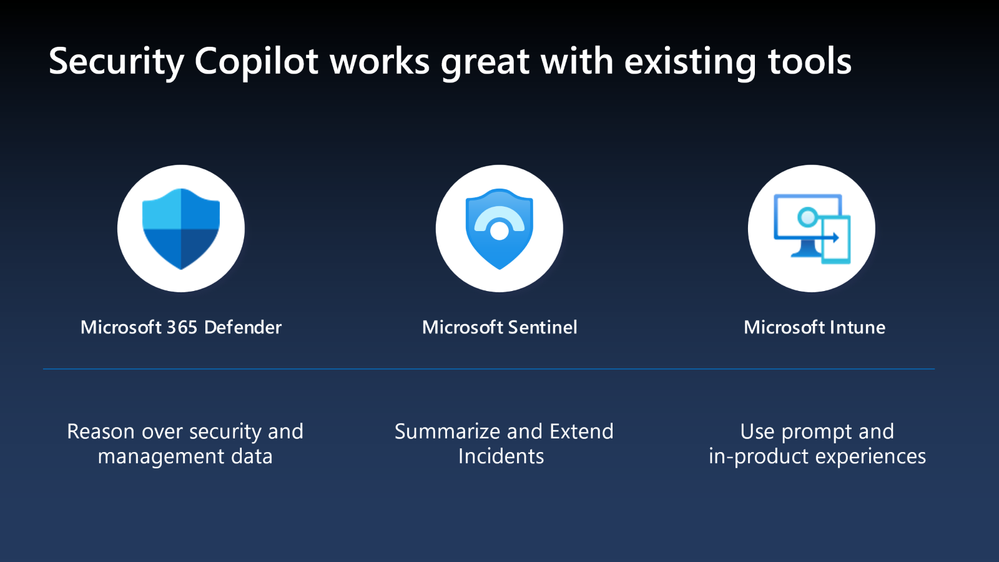
The three primary Security Copilot use cases are security posture management, incident response, and security reporting.
Security posture management is the most proactive use case. Security Copilot synthesizes information on anything that might expose an organization to a known threat and provides prescriptive guidance on how to protect against those potential vulnerabilities.
In terms of incident response, Security Copilot can quickly surface an incident, enrich it with context from other data sources, assess its scale and impact, and provide information on what the source might be, and again, guide the analyst through the response and remediation steps with recommendations. Security Copilot provides single pane of glass visibility by pulling in data from other sources like Defender and Sentinel and then correlating and analyzing that data all together.
And finally security reporting. In security, seconds count. Security Copilot delivers customizable reports that are ready to share and easy to consume, empowering analysts to focus more on high value tasks pertinent for securing the organization, while keeping leadership and stakeholders in the loop. Engaging with Security Copilot in natural language, security analysts can take advantage of this tool’s ability to easily translate incident response or hunting insights into a PowerPoint slide or email.
And this is where the integrations play in. Microsoft 365 Defender insights empower SOC analysts to investigate and respond at the incident level, disrupt in-progress attacks, and unify security and identity & access management. Sentinel is where we manage logs, detect advanced threats, monitor and alert in real-time, and provide compliance and reporting. Intune provides insights on device inventory, helps enforce configurations and policies, deploys and updates software, and delivers conditional access.
What does this look like in real life? Let’s say we have an incident in Sentinel where a user downloaded a file from a malicious IP address. Intune can help us understand what devices are associated with this user and their compliance status. Copilot brings these insights together in a central place; including recommendations to improve device health. We can take this investigation one step further by asking Copilot to hunt across Defender to see if the potential compromised user in this incident is associated with any other alerts. This empowers the SOC analyst to investigate related activity based on the user identity, knowing it could be compromised. With Copilot turning natural language into KQL queries to conduct the hunting, there is no burden on the SOC analyst to be a KQL expert. Integrating these insights in Copilot gives the SOC analyst the power to coordinate defenses across the entire digital estate, with a single view across incidents, device health & inventory, and more.
There is a global shortage of 3.5 million skilled cybersecurity professionals. The need for knowledgeable cloud security professionals is evident in every industry, including the US Government. Security Copilot has the potential to be a bar raiser – evaluating the less-skilled or deeply trained security analyst to be a more serious hunter and responder. Microsoft is excited about how the next iteration of ML-based security features will empower US Government security teams and in doing so, enhance national security.
Read more:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.