- Home
- Public Sector
- Public Sector Blog
- New Insider Risk Management features in general availability
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Safeguarding sensitive information is a core objective of Cybersecurity Maturity Model Certification (CMMC) 2.0. Government agencies bear the responsibility of handling a vast array of critical data, ranging from classified documents and personal records of citizens to national security information. The consequences of a data breach in this context can be dire, encompassing compromised national security, identity theft, and unauthorized access to confidential information.
Traditionally, many organizations rely on tools like data loss prevention (DLP) to manage insider risks. While these tools are essential for protecting data from loss, they often can’t distinguish if an alert is triggered by a first-time or repeat offender scenario, without extensive manual work to correlate multiple signals from various sources. Therefore, relying solely on content classification-based policies can result in security teams being overwhelmed with alerts, potentially causing them to miss detecting critical data security risks caused by insiders. To address this challenge, a dedicated and purpose-built Insider Risk Management solution that is integrated with a Data Loss Prevention solution can be incredibly helpful for government organizations.
Microsoft Purview Insider Risk Management is such a solution. It comes equipped with ready-to-use insider risk indicators and machine learning (ML) models that allow organizations to quickly detect risks and take action. The solution correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies to manage security and compliance. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
Today, we are excited to announce the general availability of more than 25 features for government and commercial customers who have appropriate licenses. Here are a few highlights of the newly launched capabilities:
- Detect anomalies with ML-enabled cumulative exfiltration detection
- Get high-quality insider risk alerts with sequence detections and Microsoft Purview Communication Compliance integration
- Enhance risk detection with 15+ new built-in indicators and physical badging connector
- Reduce noise with signal deduplication and exclusions
- Get started more easily with insider risk analytics and quick policies
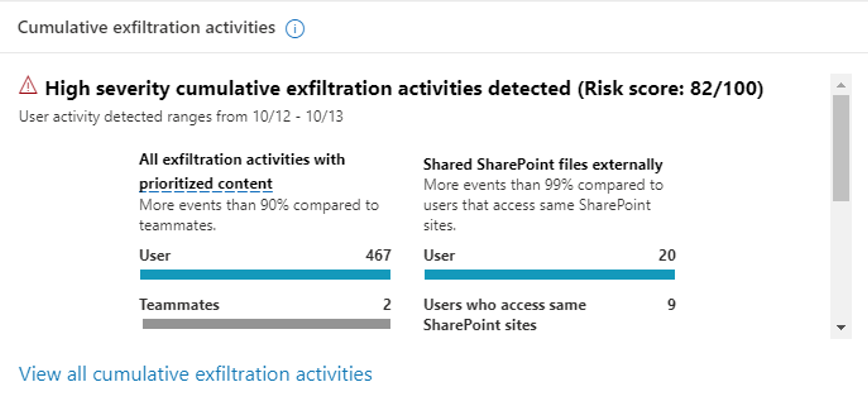
Detect anomaly with ML-enabled cumulative exfiltration detection
Detecting data security incidents caused by insiders who gradually exfiltrate sensitive enterprise data over time can pose a significant challenge. These insiders may employ tactics such as printing one file on a given day, emailing another file on a different day, and so forth, to covertly extract sensitive data without raising suspicion. However, with the Cumulative Exfiltration Activities Detection (CEAD) ML model, Insider Risk Management can effectively identify this pattern of gradual data exfiltration.
CEAD detects insider risks by comparing the exfiltration activities performed by a user over a certain time with the normal amount performed by users in your organization over the past 30 days or against their peer group's activity norms. By doing so, CEAD effectively detects insider risks that could potentially result in data theft or leaks. This built-in and ready-to-use feature enhances organizations' ability to safeguard valuable data assets.
Get high-quality insider risk alerts with sequence detections and Microsoft Purview Communication Compliance integration
Sequence detection is one of the most effective and valuable indicators to detect hidden insider risks. It helps piece together a series of activities around files and automatically weave them into a sequence of events to help suggest user intent. For example, when a user performs a single action, such as printing confidential files, it might not necessarily indicate good or bad intent. However, if the user renames a file to appear less sensitive before printing the files and subsequently deletes them, it could suggest an intent to exfiltrate data while evading detection. Unfortunately, traditional content-based data security solutions may fail to detect this incident because file was renamed. Fortunately, with Microsoft Purview Insider Risk Management, organizations can identify these elusive insider risks through high-quality alerts generated by sequence detection.

With this latest announcement, sequences not only serve as policy indicators but also function as policy triggers. It means that when a user exceeds predefined thresholds in a sequence of actions, the policy will initiate the assignment of risk scores. For example, if a user downloads files, renames them, uploads them to personal cloud storage, and subsequently deletes the files, the insider risk policies will promptly alert the security teams to investigate other indicators of the user's activities that may lead to potential data security incidents. Leveraging sequence detections as policy triggers can greatly enhance the quality of insider risk alerts, enabling security teams to concentrate on mitigating critical risks.
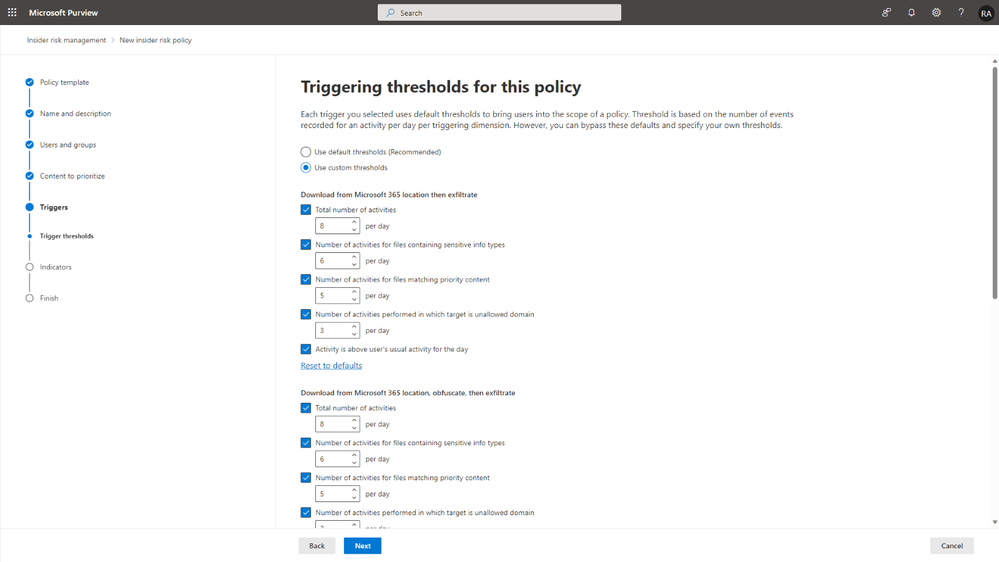
Furthermore, in addition to sequence detections as policy triggers, security teams can now also leverage non-compliant communication as an early sign of security risks that trigger alerts and the assignment of risk scores. Employees who use enterprise workspace channels to send content prohibited by their organization’s policies – such as threatening or harassing messages – can potentially pose wider data security risks, particularly if they display routine disregard for compliance. With this new capability, security teams can utilize risk signals from Microsoft Purview Communication Compliance as insider risk policy triggers, enabling more proactive measures to get ahead of potential security incidents.
Enhance risk detection with 15+ new built-in indicators and physical badging connector
One of the invaluable benefits of Microsoft Purview Insider Risk Management is its offering of numerous ready-to-use insider risk indicators, which are collected, deduplicated and curated for organizations to use to detect critical insider risks. We are thrilled to announce the general availability of over 15 built-in insider risk indicators, including sending Teams messages that contain sensitive information types, downgrading sensitivity labels applied to SharePoint files, and accessing sensitive or priority SharePoint files, just to highlight a few. With this robust set of new indicators, organizations can more effectively detect and manage potential insider risks that may lead to a data security incident.
Furthermore, organizations can now integrate log data from physical control and access platforms through our physical badging connector. For example, security teams can bring in data like user IDs, access point IDs, and access time and dates into Insider Risk Management, allowing organizations to gain insights into users' activities when accessing priority properties, like data centers.
Reduce noise with signal deduplication and exclusions
Dealing with a large volume of alerts and conducting investigations can drain resources and offer a low return on investment. It can be frustrating for organizations to sift through the noise and identify the true risks. Microsoft Purview Insider Risk Management introduces several enhancements to help organizations reduce noise and pinpoint the most critical insider risks.
One source of noise may originate from the system itself. In the absence of a purpose-built insider risk management solution, security teams typically spend a significant amount of time in deduplicating signals from audit logs. However, with this update, Microsoft Purview Insider Risk Management effectively processes and deduplicates system-generated signals for the most common 18 signals, all while retaining the risk context. This valuable feature can considerably reduce the time spent by security teams on manually dismissing low-quality alerts, enabling them to focus on identifying and addressing the most critical risks.
Another source of noise can be organization specific. For example, an organization may wish to exclude activities on a commonly used non-sensitive SharePoint site, as they contribute unnecessary alerts. We are delighted to announce that security teams now have the capability to configure exclusions based on file paths, sensitive information types, site URLs, and keywords. The file type exclusion now also extends to email attachments.

Get started more easily with insider risk analytics and quick policies
Are you excited about the announcements we shared today? If you haven't started using Microsoft Purview Insider Risk Management yet, with appropriate licensing, here are some easy ways to get started.
- Turn on insider risk analytics: The analytics capability helps assess your organization's insider risks before you create any policy. It scans your production environment and presents an aggregated view that provides org-wide insights, including the percentage of users who have engaged in exfiltration activities. With this update, we are pleased to announce that analytics now also displays anomaly and sequence detection insights, in addition to the top exfiltration activities. You can also opt in for a monthly email that summarizes the latest analytics insights, keeping you informed about your organization's insider risk posture.
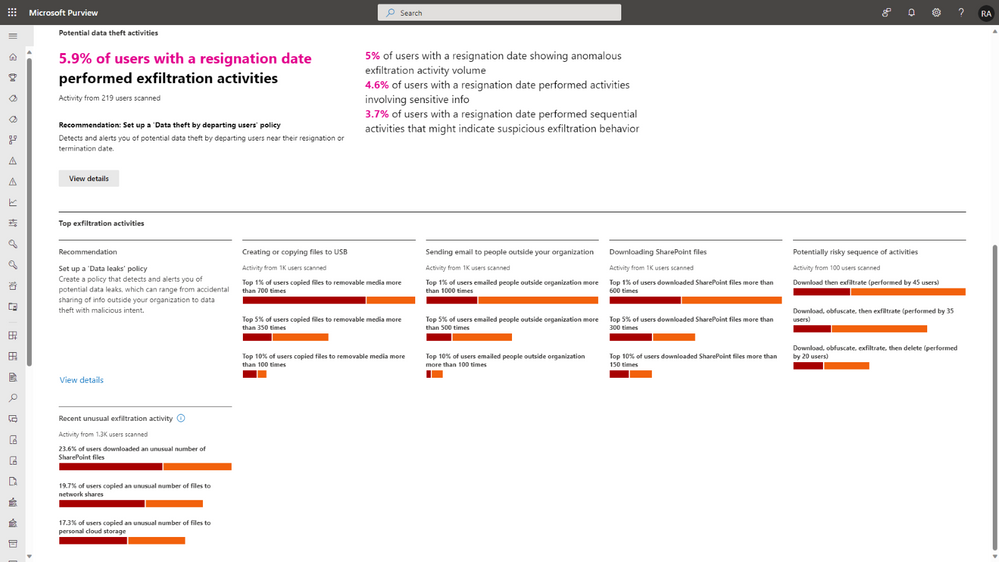
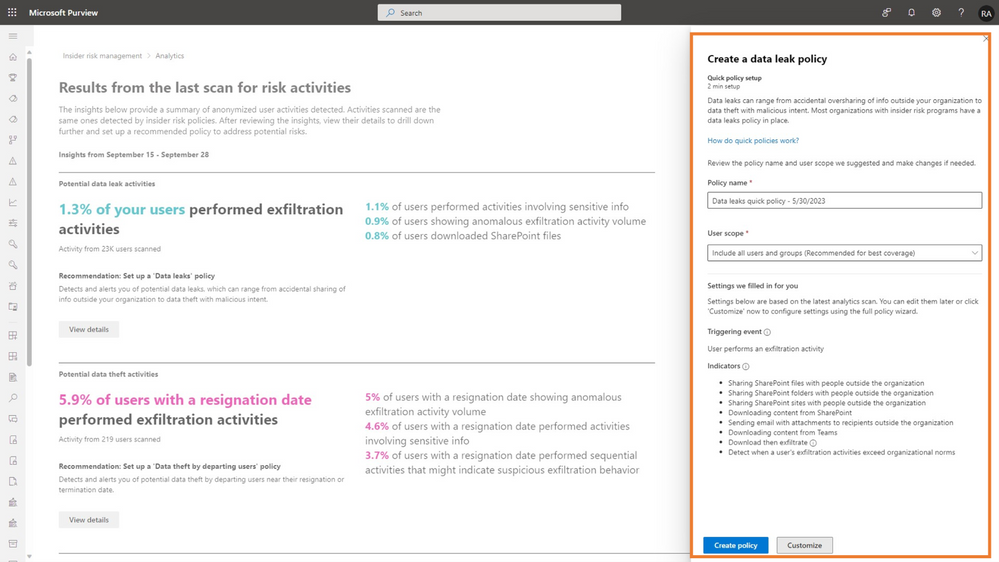
- Set up quick policies: Once you enable analytics, Insider Risk Management can use the aggregated insights as a baseline to recommend a default set of policy configurations and thresholds. Security teams can use these recommendations to create an insider risk policy with just one click. The quick policies provide you with a solid starting point, enabling you to begin receiving alerts and insights while further fine-tuning the policies.
Explore more Insider Risk Management resources
We are thrilled to share these announcements with you. Here is a summary of the next steps and other resources to help you and your organization get started with these capabilities:
- Watch the Insider Risk Management Mechanics Video to see the product in actions.
- Read the latest blogpost of Insider Risk Management
- Learn more about Insider Risk Management in our technical documentation.
- If you own Insider Risk Management and are interested in learning more about Insider Risk Management, leveraging Insider Risk Management to understand your environment, or building policies for your organization or investigate potential risky user actions, check out the resources available on our “Become an Insider Risk Management Ninja” resource page.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.