- Home
- Public Sector
- Public Sector Blog
- June 2023 - Microsoft 365 US Public Sector Roadmap Newsletter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Newsworthy Highlights |
How Microsoft 365 helps public sector organizations embrace generational diversity
Empowering your workforce with modern productivity, collaboration, and security tools can help your agency embrace generational diversity and across four critical areas: recruitment, retention, productivity, and learning.
Microsoft releases CMMC guidance to raise the security and identity baseline for Defense Industry
Identity continues to be the most common way bad actors get through cyber defenses. Therefore, identity controls are one of the most fundamental aspects of CMMC and this post is going to focus on Azure AD as a way of meeting CMMC's identity requirements.
Getting started on your data security journey
3 key considerations for your data security journey.
Teams Emergency Operations Center version 2, now available!
We are excited to announce our latest update to the Teams Emergency Operations Center, Version 2!
Universal Print in GCC and GCC High AMA and Private preview
We are excited to announce the upcoming private preview and AMA of Universal Print in GCC and GCC High. This has been a long-awaited availability for government organizations and this private preview will have full feature parity with what exists in the commercial cloud today. With Universal Print, government organizations can feel confident that their printing solution offers security and quality for employees and admins alike.
Three lessons learned about the future of cloud security at RSA
RSA is an annual event that brings together professionals across the security industry to discuss the latest trends and challenges in cloud security. The conference provides a platform for attendees to learn from experts, network with peers, and explore new products and technologies.
Transforming State and Local Government IT: Discover the Benefits of Microsoft 365 Government
In the post-pandemic world, state and local IT leaders are spending an increasing amount of time and investments navigating new ways of work, such as hybrid work rationalization, the phenomenon of 'quiet quitting,' and embracing the concept of goblin mode. While technological advancements offer exciting opportunities, optimizing these changes pose specific challenges for IT leaders in government.
Microsoft 365 Government Community Call
Join Jay Leask and other members of the Government Community live on LinkedIn!
Where to Start with Microsoft Teams Apps in Gov Clouds
Customers in our Office 365 government clouds, GCC, GCCH, and DoD, are continuing to evolve how they do business in the hybrid workplace. As Microsoft Teams is the primary tool for communication and collaboration, customers are looking to improve productivity by integrating their business processes directly into Microsoft Teams via third-party party (3P) applications or line-of-business (LOB)/homegrown application integrations.
Microsoft 365 Government Adoption Resources
Empowering US public sector organizations to transition to Microsoft 365
What’s New in Microsoft Teams | May 2023
We have a great line-up of new features to announce.
Release News |
Teams
Closed Captions available for Teams Video Clips on chat – GCC May, GCCH June, DoD July
Live captions in Teams will become more easily discoverable, adaptable, and easier to consume with t...
Timeline markers in Teams meeting recording for when a screen was shared - GCC
Purview
New retention actions in Power Automate integration are now available in Public Preview
eDiscovery support now available for Microsoft Loop Components created from Teams and Outlook via Mi...
References and Information Resources |
Microsoft 365 Public Roadmap
This link is filtered to show GCC, GCC High and DOD specific items. For more general information uncheck these boxes under “Cloud Instance”.
Stay on top of Microsoft 365 changes
Here are a few ways that you can stay on top of the Office 365 updates in your organization.
Microsoft Tech Community for Public Sector
Your community for discussion surrounding the public sector, local and state governments.
Microsoft 365 for US Government Service Descriptions
· Office 365 Platform (GCC, GCCH, DoD)
· Office 365 U.S. Government GCC High endpoints
· Office 365 U.S. Government DoD endpoints
· Microsoft Purview (GCC, GCCH, DoD)
· Enterprise Mobility & Security (GCC, GCCH, DoD)
· Microsoft Defender for Endpoint (GCC, GCCH, DoD)
· Microsoft Defender for Cloud Apps Security (GCC, GCCH, DoD)
· Microsoft Defender for Identity Security (GCC, GCCH, DoD)
· Azure Information Protection Premium
· Exchange Online (GCC, GCCH, DoD)
· Office 365 Government (GCC, GCCH, DoD)
· Power Automate US Government (GCC, GCCH, DoD)
· Outlook Mobile (GCC, GCCH, DoD)
Be a Learn-it-All |
Public Sector Center of Expertise
We bring together thought leadership and research relating to digital transformation and innovation in the public sector. We highlight the stories of public servants around the globe, while fostering a community of decision makers. Join us as we discover and share the learnings and achievements of public sector communities.
Microsoft Teams for US Government Adoption Guide
Message Center Posts and Updates for Microsoft Teams in GCC |
Looking for what’s on the map for Microsoft Teams and only Teams in GCC?
Go right to the GCC Teams Feature Communications Guide
Message Center Highlights |
SharePoint Online / OneDrive for Business
MC565167 — Microsoft OneDrive: PDF Annotation and Interactable Form Fields
<30 Days
Microsoft 365 Roadmap ID 124802
Using the "Edit" action in Microsoft OneDrive for the Web, you can seamlessly annotate with hand-drawn ink into your PDF documents and have your modifications automatically saved to your OneDrive account. Additionally, OneDrive for Web allows you to interact with form fields, making it simple for editing and modifying PDF documents.
When this will happen:
Targeted Release: We will begin rolling out in late May 2023 and expect to complete rollout by early June 2023.
Standard Release: We will begin rolling out in early June 2023 and expect to complete rollout by late June 2023.
How this will affect your organization:
Steps to annotate with hand-drawn ink using Edit action on OneDrive for Web:
- Open the desired PDF file to be annotated in OneDrive for Web.
- Click on the Edit action at the top left corner of the screen to enter the annotation edit mode.
- You can use up to four annotation types available at the middle left of the screen.
- You can modify the color or stroke thickness of the annotation by clicking on the pencil or highlighter a second time.
- Once done with the annotations, use the Save action located at the top left corner of the screen to exit annotation edit mode and save all changes made to the PDF document.
Steps to interact with PDF document that has form fields on OneDrive for Web:
- Open the desired PDF file that contains interactable form fields in OneDrive for Web.
- Click on a form field to begin interacting with it.
- Press Enter to complete your edits or use the TAB key to navigate to the next interactable form field.
- After making all necessary changes to the form fields, select the Save option located in the top left corner of the screen to save all modifications made to the PDF document.
What you need to do to prepare:
You may want to notify your users about this new capability and update your training and documentation as appropriate.
MC565161 — Relocating Sync Command in OneDrive's My Files view to Settings
30-60 Days
Microsoft 365 Roadmap ID 124902
We are relocating the Sync command in OneDrive for Business Web for My Files. Currently the command is in the command bar, and we are moving it to the setting gear.
When this will happen:
Targeted Release: We will begin rolling out in early June and expect to complete rollout by mid-June.
Standard Release: We will begin rolling out mid-June and expect to complete rollout by late July.
How this will affect your organization:
All functionality will remain the same for users, the only change is a new entry point for the command.
What you need to do to prepare:
There is no action required from you at this time. You may want to notify your users of this update. For additional information, please visit this page.
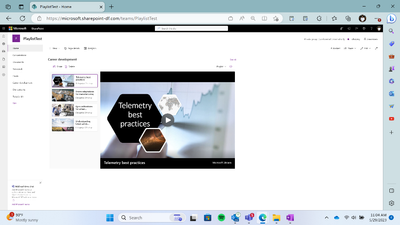
MC564196 — Microsoft Stream: Playlist View in SharePoint List Webpart
<30 Days
Microsoft 365 Roadmap ID 124808
Users can soon select a playlist to be displayed in the list webpart in the full-blown playlist view along with video playback.
When this will happen:
Standard Release: We will begin rolling out in early June 2023 and expect to complete rollout by late June 2023.
How this will affect your organization:
- Users will be able to select a playlist from the list picker while configuring the list webpart.
- Users will be able to see the full-blown playlist view as the default view for playlists.
What you need to do to prepare:
There is no action required at this time, this change will be enabled automatically.
MC561187 — (Updated) Stream Classic webpart retirement and new Stream (on SharePoint) webpart availability
30-60 Days
This change is associated with Microsoft 365 Roadmap: 124800
Updated May 30, 2023: We have updated the content to show as intended. Thank you for your patience.
This is an important message for customers who use the Stream (Classic) webpart to add videos to SharePoint Pages and news posts. Microsoft will retire the Stream (Classic) webpart on Aug 15, 2023 and it will no longer be available for use after this date. The Stream (Classic) webpart will be replaced by the new Stream (on SharePoint) webpart.
When this will happen:
The Stream (Classic) webpart will be retired on August 15, 2023.
The Stream (on SharePoint) webpart will begin its general availability roll out in mid-June, and we expect the rollout to complete by mid-July.
How this will affect your organization:
- Your organization will not be able to use Stream (Classic) webpart after August 15, 2023.
- All SharePoint pages and news posts that were built using Stream (Classic) webpart with single video as a source will continue to play your videos until February 2025.
- After your organization migrates video content to Stream (on SharePoint), single videos configured on the Stream Classic webpart continues to play inline while channels configured on the webpart is replaced by a button that redirects to the migrated folder location.
- If you would like to publish videos from Stream (on SharePoint) on SharePoint Pages, you can currently use video eligible webparts such as “File and Media”, “Hero”, “Highlighted content” and “List” webparts. Additionally, you will be able to use the new Stream (on SharePoint) webpart when it becomes available.
- For re-publishing Stream Classic webpart videos post migration, users will have to manually do so using the share URL via above mentioned webparts.
What you can do to prepare:
Please follow this documentation for detailed timelines and video publishing guidance on the new Stream: Stream (Classic) web part transition plan & new Stream Webpart
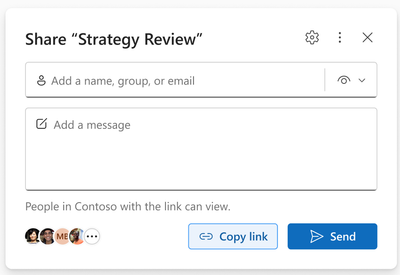
MC560718 — OneDrive: Simplified Sharing
<30 Days
Microsoft 365 Roadmap ID 124933
We are completely revamping the Sharing control to help you and your organization share more easily and confidently. You can focus on the people you want to share with and how you want to share with them. The link scope is always shown at the bottom of the dialog and can be modified at the top-right, under the settings gear, to best fit your scenarios prior to sharing with others. The copy link section now returns a quick success toast when the link successfully copied to clipboard. The ability to share to Outlook is still available for users who enabled it in the top menu.
When this will happen:
Targeted Release: We will begin rolling out late May and expect to complete by early June.
Standard Release: We will begin rolling out early June and expect to complete by late June.
How this will affect your organization:
Users who interact with the OneDrive/SharePoint will be able to see this refreshed experience.
Note: Some users may see this feature before others in your organization.
What you need to do to prepare:
There is no action required from you at this time. We recommend making your users aware of this upcoming update.
MC559933 — (Updated) OneDrive: Restore files to original location when turning off folder backup
<30 Days
Updated June 1, 2023: We have updated the rollout timeline below. Thank you for your patience.
OneDrive: Restore files to original location when turning off folder backup.
This feature provides new functionality for users who turn off folder backup (also known as “PC folder backup” and “known folder move”). When users turn off folder backup, they will have the option to restore the files back to their original location. Note: when a folder contains files stored only in the cloud, those files will not be moved; they will remain in the cloud
When this will happen:
Standard Release: This is currently rolling out and will complete rolling out in late June (previously late May).
Note: Some users may see this feature before others in your organization.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
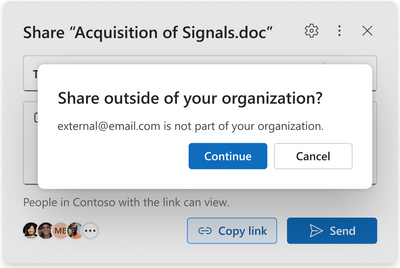
MC559250 — OneDrive: Sharing Experiences - Improved external sharing in the sharing control
<30 Days
Microsoft 365 Roadmap ID 100713
In the current sharing control, if your admin or organization allows external sharing, you're required to go to the sharing settings and select the right link type in order to successfully share externally. In the new experience, we make things a lot easier for you: as soon as you choose an external person to share with using a company link, we will display a prompt to confirm your choice. If confirmed, the link will automatically change from an internal-only link to a "Specific People" link, and you can simply proceed to share. Otherwise, we will display a simple error message that says, "This link won't work for people outside of your organization." As always, this new experience respects the organization's settings around external sharing and default link types.
When this will happen:
Targeted Release: We will begin rolling out late May and expect to complete by early June.
Standard Release: We will begin rolling out early June and expect to complete by late June.
How this will affect your organization:
Users who interact with the OneDrive/SharePoint Sharing control will be able to see this new experience.
Note: Some users may see this feature before others in your organization.
What you need to do to prepare:
There is no action required from you at this time. We recommend making your users aware of this upcoming update.
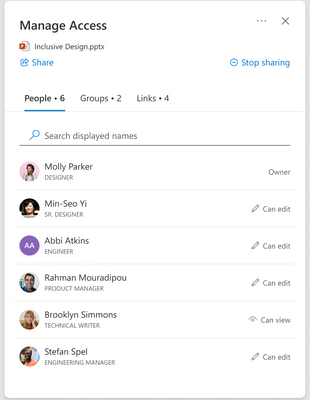
MC554155 — (Updated) OneDrive: Sharing Experiences - Refreshed Manage Access
30-60 Days
Microsoft 365 Roadmap ID 83726
Updated May 19, 2023: We have updated the timeline below. Thank you for your patience.
We are completely revamping the Manage Access experience to be more people-centric and more usable. You can now view the extensive list of all the people who have gained access to your files, search for an individual or a group and manage their access with even more control. You can also drill down into the group or link information for more details.
When this will happen:
Targeted Release: We will begin rolling out in late May (previously mid-May) and expect to complete rollout by mid-June (previously early June).
Standard Release: We will begin rolling out in mid-June (previously early June) and expect to complete rollout by mid-July (previously late June).
How this will affect your organization:
Users who interact with the OneDrive/SharePoint will be able to see this new Manage Access experience.
Note: Some users may see this feature before others in your organization.
What you need to do to prepare:
There is no action required from you at this time. We recommend making your users aware of this upcoming update. Please find additional information in this documentation.
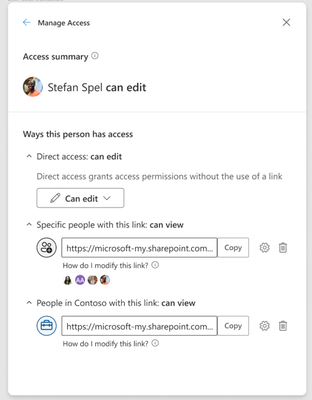
MC545906 — (Updated) SharedWith and SharedWithDetails column in OneDrive and SharePoint will no longer be updated
30-60 Days
Updated: We have updated the content below for additional clarification. Thank you for your feedback.
We will be retiring the SharedWith and SharedWithDetails columns from OneDrive and SharePoint starting in early June. For customers who are looking to understand who has access to content, we recommend utilizing features like the Microsoft 365 Audit Logs and the Manage Access experience.
When this will happen:
We'll be gradually rolling this out to customers in early June, and the roll out will be completed by the end of July.
How this will affect your organization:
As described in this documentation, the SharedWith and SharedWithDetails column do not accurately reflect the permissions and people who have access to an item. As such, the column has been hidden by default in OneDrive and SharePoint for 3+ years. With this change, we will no longer update the SharedWith fields during sharing operations. The data within the column will move to being considered customer content and will not be updated or changed by Microsoft.
In a future update, we will stop provisioning this column entirely.
What you need to do to prepare:
We recommend using Microsoft 365 audit logs or the Manage Access experience to understand which users have permission to an item.
Please click Additional Information to learn more.
Use sharing auditing in the audit log
See who a file is shared with in OneDrive or SharePoint
MC525663 — (Updated) SPO Site Sharing will now use Azure B2B Invitation Manager
<30 Days
Microsoft 365 Roadmap ID 117557
Updated June 1, 2023: We have updated the content for clarity. Thank you for your patience.
We are updating the SharePoint Online Site Sharing backend to use Azure B2B Invitation Manager instead of the legacy SharePoint Invitation Manager.
When this will happen:
This change will begin rolling out in late March, and complete rollout by late June (previously late May).
How this will affect your organization:
Today, sharing just the SharePoint site goes through the original SharePoint Invitation Manager which always creates guest users in your organization's directory. We are now updating this flow & experience to use the Azure B2B Invitation Manager instead. The sharing flow will remain identical to what users see today, but external recipients will now go through your organization's B2B Invitation Manager experience.
Note: This change will only impact sharing of sites. Users who share files or folders will continue to receive the same experience they have today.
What you need to do to prepare:
You may want to review your Azure B2B Invitation Manager policies.
Power Platform
MC555498 — Announcing Public preview of 'Record’ access checker
Rolled Out
We are rolling out a public preview of a new capability of the access checker feature that will be available in all regions globally by Wednesday, May 31, 2023. Currently, record owners can share their records with other colleagues to collaborate in Microsoft Dataverse but are unable to identify all users who have access to their records. This new capability of access checker will enable these owners to review a list of users who have access to a specific record through the application client.
How can I enable this feature?
This capability can be enabled in your environments for your users to preview.
There are two OrganizationSettings values that you can change using the OrganizationSettingsEditor tool:
- IsAccessCheckerAllUsersEnabled: This allows the admin to see who has access to the row.
- IsAccessCheckerNonAdminAllUsersEnabled: This allows the admin, owner of the record, and users who have access to the row to see who has access.
To learn more about this new access checker capability, review our documentation covering how to check your user access and permissions and learn how to use access checker to view all users who have access to your record.
If you require any assistance, please contact Microsoft Support.
MC553090 — Announcing General Availability for Microsoft Power Platform tenant isolation
Rolled Out
We are excited to announce that tenant isolation for Power Platform is now generally available (GA) in all clouds. Tenant isolation makes it easy for administrators to ensure that connectors used in apps and flows can be harnessed in a safe and secure way within the tenant, while minimizing the risk of data exfiltration outside the tenant.
Tenant isolation is generally available on Wednesday, May 10, 2023, in all regions and clouds. The change removing the “preview” tag in Power Platform admin center is being deployed in all regions and will be available worldwide by Saturday, May 20, 2023.
How will this affect me?
Tenant isolation enables administrators in your organization to restrict AAD-based connections from other tenants into their tenant (inbound access control) and from their tenant into other tenants (outbound access control) via Power Platform applications and flows. When enabled, tenant isolation will protect organizations from inbound or outbound connections for all cross-cloud scenarios.
Power Platform tenant isolation enforces restrictions on connections within the realm of Power Platform connections without impacting cross tenant access to services outside of Power Platform. Depending on the business use case, administrators have the option to specify an explicit list of exceptions and allow some tenants to either connect to or from the target tenant, or both inbound and outbound directions. When configured, these tenants will bypass tenant isolation controls. These configurations are available for administrators through an easy-to-use experience in the Power Platform admin center.
Enabling tenant isolation is a best practice that we recommend for all customers. It complements other controls, such as conditional access, by restricting what tenants end-users are connecting from or to, an evaluation that is performed post connection authentication.
Where can I learn more?
Review the tenant isolation documentation to find more details about Power Platform tenant isolation and how you easily configure the policy and any exceptions rules.
Microsoft Viva
MC555186 — Microsoft Viva: Automatic Topic Relationships available in GCC
Rolled Out
Microsoft 365 Roadmap ID 106765
The ability for AI to suggest relationships between topics is now available for Viva Topics customers in our Government Clouds.
When this will happen:
This is now available for GCC customers.
How this will affect your organization:
These suggested related topics appear on the topic card, page and answers.
What you need to do to prepare:
There is nothing you need to do to prepare. For additional information on how to create a topic, please visit this documentation.
Microsoft Teams
MC567504 — Updated companion mode for Android meetings
Rolled Out
Microsoft 365 Roadmap ID 109606
This feature allows you to add your Android device to an ongoing meeting, making it easy to chat, react, share, and more.
When this will happen:
Standard Release: We will begin rolling out early June 2023 and expect to complete by mid-June 2023
How this will affect your organization:
The feature introduces Companion Mode for Android users.
What you need to do to prepare:
Nothing is needed to prepare. However, feel free to test this feature once it has rolled out.
MC567496 — Introducing Dark Mode in Teams Admin Center
<30 Days
We're excited to announce the addition of Dark Mode for Teams Admin Center. This highly anticipated feature will offer a visually appealing interface while reducing eye strain.
When this will happen:
We will begin rolling this out in early June 2023 and expect to complete rollout by end of June 2023.
How this will affect your organization:
Administrators will see a toggle button on the top right corner of the Teams admin center Dashboard to toggle ON or OFF between the light mode and dark mode.
What you need to do to prepare:
You may want to notify your Teams administrators about this new capability and update your training and documentation as appropriate.
MC566318 — Microsoft Teams: Manage Surface Hubs as Teams Devices from Teams admin center - GCCH
<30 Days
Microsoft 365 Roadmap ID 127471
With Microsoft Teams admin center, you'll soon be able to manage your Surface Hub devices with Microsoft Teams.
When this will happen:
Rollout will begin in early June and is expected to be complete by late June.
How this will affect your organization:
In the Teams admin center, tenant administrators will find the section - 'Surface Hubs' under the 'Teams devices' section, in the left navigation panel. This section will display the list of all the Surface Hubs enrolled for the tenant and their key details such as - Signed-in user, device health, and IP address. Focused details are available by clicking on the device to navigate to the individual device details page - such as software health, OEM serial number, meeting activity of the signed-in user, and list of the operations carried out on the device.
Details present on the individual device page:
- Health - shows the Connectivity health and Software health of the device.
- Details - shows the device related properties such as - Device name, IP address, OEM serial number, Tags, etc.
- Activity - shows the meeting details of the user signed-in on the device.
- History - lists the asynchronous operations carried out on the devices.
There are some navigational tools present to help you manage the inventory:
- Manage tags - add and remove tags to the users to organize them as needed.
- Filter - filter on the field of your choice to identify the required devices.
- Search - search for specific devices based on their username, display name, device name, or the tags associated with them.
- Export - export the list of devices and their details in a csv file.
The administrator managing the devices can carry out a variety of operations on these devices:
- Restart devices
- Download device logs
- Edits settings
What you need to do to prepare:
You do not need to do anything to prepare. This change will take effect automatically and Surface Hubs will get enrolled if they are online and signed-in. If you do not see your devices enrolled on the Teams admin center, please try updating them.
For more information around managing Surface Hubs, please refer to Manage Surface Hubs from Teams admin center.
MC565156 — Teams Room Windows: Simplified Device Registration Process for Microsoft Teams Rooms Pro Management Portal
<30 Days
We are pleased to announce an enhancement to the device registration process for Windows-based Teams Rooms devices on the Pro Management portal, aimed at making it more convenient for IT admins.
With the upcoming Teams Rooms app update (v. 4.17) scheduled for release by the end of June 2023, we have streamlined the registration process for Windows-based Teams Rooms devices. IT admins will no longer need to manually download and install the Pro Management agent on each device.
Instead, the Pro Management agent will be automatically downloaded and installed onto the Windows-based Teams Rooms devices as part of the Teams Rooms app update. This improvement simplifies the agent deployment and device enrollment tasks for IT admins, reducing their workload.
Once the Pro Management agent is successfully installed and connected, devices with the Teams Rooms Pro license will be automatically enrolled and visible on the Pro Management portal. This eliminates the need for any additional user action, making the process more efficient.
We understand the importance of a seamless and hassle-free device registration experience for IT admins. This update aims to improve the overall management process and reduce friction when connecting Windows-based Teams Rooms devices to the Pro Management portal.
Stay tuned for the upcoming Teams Rooms app update (v. 4.17) to take advantage of the simplified device registration process and enhance your device management capabilities with the Pro Management service.
How this will affect your organization:
MTRW Devices with Teams Room Pro license will automatically enroll into the pro management portal for state of the art monitoring and remote management capabilities for Microsoft Teams Rooms
What you need to do to prepare:
No action needed.
MC564198 — Microsoft Teams: Breakout rooms support and Select Together Mode for everyone on Microsoft Teams Rooms on Windows
30-60 Days
Microsoft 365 Roadmap ID 95680, 126105
The latest version of Teams Rooms on Windows app 4.17 update includes new in-meeting experiences including:
- Breakout room support
- Choose your Together Mode scene and select it for everyone
When this will happen:
We will begin rolling out in mid-June and expect to complete rollout by late July.
How this will affect your organization:
Breakout room support:
Teams Rooms on Windows can participate in a breakout room and be moved in and out of the main meeting, depending on a meeting organizer’s control. Breakout room organization is not intended experience for Teams rooms and is not offered.
1) Join a breakout room
- When an organizer turns ON the ‘Automatically move people to rooms’ setting, room users see the ‘We’ll move you to your assigned room in 10 seconds’ notification.
- When an organizer turns OFF ‘Automatically move people to rooms’ setting
2) Return to the main meeting
- When an organizer turns ON ‘Automatically move people to rooms’ setting, room users see the ‘We’ll move you back to the main meeting in 10 seconds’ notification.
- When an organizer turns ON ‘Automatically move people to rooms’ setting:
Choose your Together Mode scene and select it for everyone:
- Teams Rooms on Windows can now choose a Together Mode scene that fits your meeting type, using the view switcher on console.
- When your Teams Rooms on Windows is an organizer or presenter, you can have all of the participants see the same scene by clicking the ‘Select for everyone’ checkbox and ‘Apply’ button.
What you need to do to prepare:
Kindly notify your users about this new experience and update your training and documentation as appropriate.
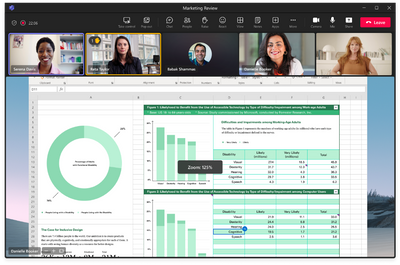
MC564195 — Introducing zooming controls while viewing screenshare
>60 Days
Microsoft 365 Roadmap ID 116010
This change is applicable to Microsoft Teams users using meetings and calls.
Users in a Teams call or meeting will now see new buttons to zoom in, zoom out and restore the original size of the incoming screenshare. This will greatly enhance the experience of users viewing screenshare. (Ability to zoom was previously only available using pinch to zoom gesture on trackpad or other shortcuts.)
When this will happen:
Targeted Release: We will begin rolling out early June and expect to complete by mid-June.
Public Preview: We will begin rolling out early June and expect to complete by mid-June.
Standard Release: We will begin rolling out early July and expect to complete by mid-July.
GCC-High and DoD: We will begin rolling out in late August and expect to complete rollout by mid-September.
How this will affect your organization:
This experience has no impact on tenant/admin. Users can now use new buttons to zoom in, zoom out and restore the original size of the incoming screenshare instead of using gestures/shortcuts.
Note: This feature is currently not available when watermark (applicable for Teams Premium only) is enabled.
What you need to do to prepare:
You can update your support and/or knowledgebase articles as necessary.
MC561700 — Microsoft Teams: App Suggestions by Task in In-Context Stores
30-60 Days
Microsoft 365 Roadmap ID 122527
Users think about which tasks they need to complete, such as creating a survey, inside Microsoft Teams. Soon, app suggestions will be organized by tasks that the apps support as opposed to conventional categories (productivity, project management). As a result, the new categorization will reduce the amount of time users need to spend learning about these apps – helping them to work more effectively.
When this will happen:
GA: Rollout will begin in early June 2023 and is expected to be complete by mid-June 2023.
GCC: Rollout will begin in mid-June 2023 and is expected to be complete by late June 2023.
GCCH: Rollout will begin in mid-July 2023 and is expected to be complete by late July 2023.
How this will affect your organization:
The task-based app suggestions will be added to the Tabs, Messaging Extension, and Bots in-context Stores.
What you need to do to prepare:
There is no action required at this time. You may want to notify your users of this update.
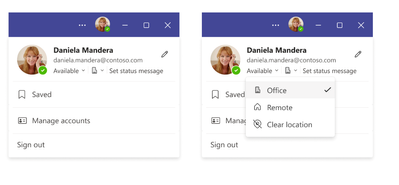
MC561188 — Microsoft Teams: Set your Work Hours and Location
>60 Days
Microsoft 365 Roadmap ID 125375
Set your work location for the day in Microsoft Teams so your team can learn about your availability for in-office and remote collaboration.
When this will happen:
Targeted Release and Preview: We have begun rollout and expect to complete rollout by late May.
Standard Release: We will begin rolling out in early June and expect to complete rollout by early August.
How this will affect your organization:
We are highlighting Microsoft 365 features that will bring transparency and focus on where you and your colleagues are working: work hours and location. These features will appear in Outlook on the web and Teams and bring the flexibility of enabling users to share where they are working. You’re already accustomed to managing and sharing your schedule in Outlook and Teams. With these additional features, Microsoft 365 is now location-aware – giving more information to you and colleagues to work better together.
Microsoft 365 already helps you manage and share your work schedule and availability. The work hours and location features allow you to specify more details about your work schedule and preferences, like from where you’re working (remotely or in office) and whether you work different hours on different days.
Teams gives you the flexibility to easily change the location for that day, without impacting the rest of your week. For example, after a few hours in the office, you decide to finish up your work from home. To change your location from Teams, simply click on your profile on the top right corner of the Teams window, view your account settings menu and change your work location for that day.
You can also update your location from any device with Teams. If you want to quickly look up where someone is working from, you can view their location in their profile card next to their availability.
What you need to do to prepare:
There is no action required from you at this time. You may want to notify your users of this update.
MC561186 — (Updated) Microsoft Teams: Block Meeting Chat Access in External, Non-Trusted Meeting Joins
>60 Days
Microsoft 365 Roadmap ID 123975
Updated June 1, 2023: We have added a link to additional details.
Microsoft Teams IT Admins will soon be able to block internal users from accessing chats when these users join meetings organized on external non-trusted tenants, including cross-cloud join. This release of Microsoft Teams' new meeting chat setting will be rolling out across MS Teams Desktop, Mobile and Web and will provide a new way for tenants to manage users' chat access in meetings hosted on external non-trusted tenants.
When will this happen:
Targeted Release: We will begin rollout in early July and expect to complete rollout by mid-July.
GA: We will begin rollout in mid-July and expect to complete rollout by late July.
GCC: We will begin rollout in early August and expect to complete rollout by mid-August.
GCCH: We will begin rollout in mid-August and expect to complete rollout by late August.
DoD: We will begin rollout in mid-September and expect to complete rollout by late September.
How this will affect your organization:
- IT Admins can modify this setting for internal users from the Teams Admin Center under External Meeting Chat or from PowerShell under AllowExternalNonTrustedMeetingChat. Internal users who have External Meeting Chat as OFF from the Admin Center or AllowExternalNonTrustedMeetingChat as False from the PowerShell will not have read or write chat access in meetings hosted on external non-trusted tenants on any Teams platforms.
What you need to do to prepare:
You may want to notify your users about this new setting and the potential effect on their chat access when joining external meetings.
MC560732 — IT Admin Webinar Usage Report in TAC with Updates
>60 Days
Microsoft 365 Roadmap ID 124764
Webinar usage reports will be available for IT admins to view all webinars created by users in your tenant who are able to create webinars (AllowWebinar set to ON). In addition to this new reports we are enhancing IT admin experience with following updates:
- Teams Admin Center UX to configure event policy settings without using PowerShell
- New event policy setting called AllowedQuestionTypesInRegistrationForm to allow control of which registration form question types can be used by the webinar users to add to webinar registration page
When this will happen:
Standard Rollout: Rollout will begin in mid-July 2023 and is expected to be complete by late July 2023.
GCC: Rollout will begin in late July 2023 and is expected to be complete by early August 2023.
How this will affect your organization:
Webinar Usage Reports:
These changes do not affect webinar end users but only IT admins. On the Usage Report page of the left navigation pane under Analytics & reports in Teams Admin Center, you can choose Webinar Usage Reports from the reports dropdown. With the new usage reports IT admins can quickly and easily view usage of webinar within your tenant over any time window.
Teams admin center UX:
There will be a new page called Event policies under Meetings section in the left-hand navigation pane of Teams Admin Center. You will be able to configure the event policy settings and create new policies for different users as you can in current Meeting policies for meetings.
Newly added AllowedQuestionTypesInRegistrationForm setting:
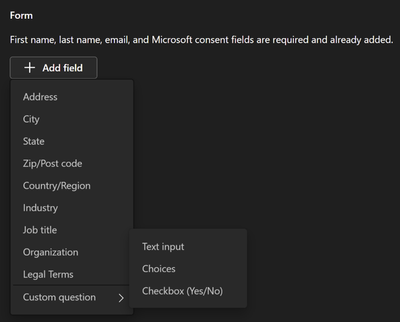
Registration form questions currently available to all users include the following three types:
- Default questions – Required questions for all webinars and all attendees. Cannot be removed.
- First name, last name, email, Microsoft consent field (Teams Events specific terms and conditions)
- Predefined questions – Questions cannot be edited by organizer. Organizer has option to add and make required.
- Address, city, State, Zip/Post code, Country/Region, Industry, Job title, Organization, Legal terms
- Custom questions – Questions can be customized with string of organizer’s choice. Organizer has option to add and make required.
- Text input (free text question with free text response), choice (multiple choice), checkbox (Boolean type)
This setting will have the following setting options: default only, default and predefined only, or all Questions. Default value will be “all questions”.
What you need to do to prepare:
There is nothing you need to do to prepare. For additional information, please visit this documentation.
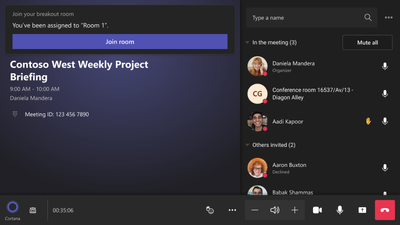
MC559253 — Microsoft Teams: Breakout Rooms Pre-meeting Room Creation and Participant Assignment (GCC-H)
<30 Days
Microsoft 365 Roadmap ID 85436
We are adding the ability for meeting organizers to pre-create rooms ahead of a meeting start and perform participant assignment tasks (both auto and manual) in advance.
This is rolling out on desktop only.
When this will happen:
Rollout will begin in mid-June and should be complete by late June.
How this will affect your organization:
Via this capability, organizers of Channel and Private meetings will be able to perform the following Breakout Rooms configuration tasks before a meeting begins:
- Bulk creating / deleting rooms
- Adding / deleting / renaming individual rooms
- Configuring meeting options for each room
- Adjusting settings for breakout rooms session (timer, selecting breakout rooms managers and more)
- Pre-assigning participants via both manual and automatic assignment options
Before a meeting starts, meeting organizers will be able to access a new tab in scheduling form called Breakout rooms that will enable them to pre-create breakout rooms and pre-assign participants.
Note:
- During live session, rooms will only be managed via the Breakout Room panel in the meeting itself (organizer or BR manager are required to join the meeting)
- Only invited attendees will be available for assignment, up to 300 participants, including channel members in case of Channel meetings.
What you need to do to prepare:
You may want to notify your users about this new capability and update your training and documentation as appropriate.
Learn more: Use Breakout Rooms in Teams meetings
MC557818 — Group Policy Assignment Support for Additional Policies in Teams Powershell Module
Rolled Out
Microsoft is now extending group policy assignment support to additional policy types via Teams PowerShell Module (TPM). Admins can create new groups in Microsoft 365 admin center or can use existing groups to assign custom policies for various policy types in Teams PowerShell Module.
As your organization expands, your requirements become increasingly nuanced and multifaceted. A "one size fits all" approach is no longer tenable. Therefore, this capability will enable your organization to have different custom policies for various policy types assigned to user groups for specific needs. You will not have to rely on global (org-wide default) policies or direct policy assignments via manual user selections.
When this will happen:
This new update will be available for policies mentioned in subsequent section by late May 2023 for all Microsoft Teams commercial licenses.
How this will affect your organization:
The group policy assignment feature lets you assign custom policies to groups that were created in the Microsoft 365 Admin center. The Teams PowerShell Module (TPM) supports M365 groups, distribution lists, mail-enabled security groups, and security groups for group policy assignment. Apart from core policies such as meeting policies, calling policies, and messaging policies, group policy assignment support is now extended to the below policy types in TPM:
- Application Access Policy
- Call Hold Policy
- Carrier Emergency Call Routing Policy
- Cortana Policy
- Dial Out Policy
- Education Assignments App Policy
- Emergency Calling Policy
- Enhanced Encryption Policy
- Events Policy
- External Access Policy
- Feedback Policy
- Files Policy
- IPPhone Policy
- Media Logging Policy
- Meeting Branding Policy
- Meeting Template Permission Policy
- Mobility Policy
- Notification And Feeds Policy
- Room Video Tele Conferencing Policy
- Synthetic Automated Call Policy
- Teams Branch Survivability Policy
- Template Permission Policy
- VDI Policy
- Video Interop Service Policy
- Voice Routing Policy
- Voicemail Policy
Admins will first have to manage groups in the Microsoft 365 Admin center, and then go to the Teams PowerShell Module to perform the group policy assignment for various policy types.
What you need to do to prepare:
Follow below steps to be prepared:
- Review how the policy assignment for users and groups works.
- Review how policy takes effect for users due to precedence rules.
- You can then review groups that you have created in Microsoft 365 admin center or create new groups.
- Based on your organization's needs, you can assign custom policies for these policy types to user groups via Microsoft Teams PowerShell Module.
- To remove a pre-existing custom direct policy assignment, use GRANT to assign null policy to make way for group policy assignments to take effect (due to precedence rules mentioned in #2).
MC557808 — Follow up MC515531: Pronouns on Profile Cards in Microsoft Teams and Outlook Web
<30 Days
Microsoft 365 Roadmap ID 86382 and 115511
This is a follow up to MC515531 (February '23) as we continue working on rolling this out to all environments.
We’re adding a new feature to the profile card in Microsoft 365. Users in your organization will soon be able to add pronouns directly to their profile card in Outlook on the web and Teams. Pronouns are the words we use to replace someone's name in a sentence, such as “he,” “she,” or “they” in English.
When this will happen:
- Targeted Release: Rollout will begin late February. - Complete
- Standard Release: Rollout will begin in late March. - Complete
- GCC rollout is expected to start at the end of May.
- GCCH rollout is expected to start in early June.
- DoD rollout is expected to start in late June.
How this will affect your organization:
The ability to allow people in your organization to display their pronouns on the profile card is OFF by default for your tenant. If elected, after you have turned pronouns ON, it is optional for users to add pronouns to their profile.
Pronouns will be shown next to the name in the top section of the profile card in Outlook on the web and Teams. Pronouns will be visible to everyone in your organization. If you want people in your organization to have the option of adding pronouns to their profile, you will have to turn pronouns ON for your tenant.
What you need to do to prepare:
Whether or not to share or publicly display pronouns is always up to an individual. Pronouns should never be assigned by a person to another person. It should be up to the person using them to decide when, where, and which pronouns are used – including whether to use this feature, should it be turned on.
Knowing someone’s pronouns does not always equate to knowing their gender identity. Administrators are encouraged to understand any applicable local laws, regulations, and cultural norms that may pose additional risks to employees should their pronouns be publicly displayed and take this into consideration as a decision is reached whether to or not to turn on this feature.
If the feature is utilized, it is recommended that internal and/or external subject matter experts in transgender inclusion be engaged to consider how pronoun display can complement (not substitute) more comprehensive efforts to support transgender communities in your organization.
Once pronouns roll out, you may want to notify your users about this new capability and update your training and documentation as appropriate.
See our available documentation below:
- For Admins: Pronouns in Microsoft 365
- Pronouns on your profile in Microsoft 365
- Pronouns Best Practices
- Frequently Asked Questions About Pronouns
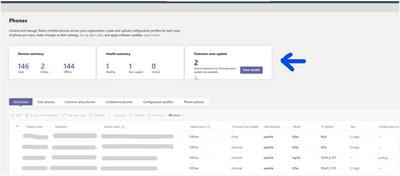
MC556779 — Track and pause firmware auto-updates for Teams devices from Teams admin center
Rolled Out
Microsoft 365 Roadmap ID 119389
We are introducing enhancements to firmware auto-updates for Android-based Teams devices in Teams admin center.
These enhancements -
- Make it easier to organize devices to manage rollout of new releases.
- Improve visibility into the update process - which devices are getting updated and when.
- Improve the regularity with which devices receive updates.
- Make the update process more robust by adding additional internal guardrails.
When this will happen:
Standard Release: Rollout is currently underway and expected to complete by late May 2023.
How this will affect your organization:
Administrators using Teams admin center to manage Teams devices will see the following changes on the pages for Teams Phones, Displays, Panels, and Teams Rooms on Android:
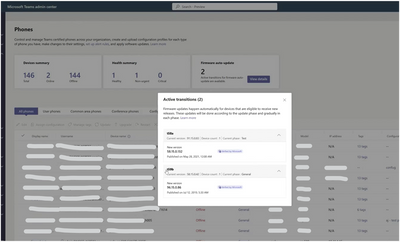
- New widget which displays active updates along with their details
- Admins can select "View details" to view releases that are currently rolling out for their tenant, including information such as device model, number of devices eligible, and active phase. Admins can use this information to identify devices that will be receiving updates.
- Option to temporarily pause (and resume) auto-updates in the Actions menu
- Enabling Pause stops all firmware auto-updates for the tenant for 15 days. If an update is already scheduled it will be cancelled.
- Admins may choose to resume auto-updates before 15 days elapse.
- Software versions released by Microsoft are marked as "Verified by Microsoft".
Refer to Update Teams devices remotely for more details about the auto-updates.
What you need to do to prepare:
No action is required from you. Firmware auto-updates will continue to follow update phases configured by you.
MC556772 — Microsoft Teams: A new default home screen and an enhanced custom background feature for Teams Rooms on Windows
30-60 Days
Microsoft 365 Roadmap ID 124774
The latest version of Teams Rooms on Windows app 4.17 update includes new and improved home screen features, including:
- New default home screen experience with modern UI update
- Enhanced custom background feature for Teams Rooms Pro users.
When this will happen:
Roll out begins mid-June and is expected to be completed by late July.
How this affects your organization:
New default home screen
The refreshed home screen with modern UI/UX updates for Teams Rooms on Windows was released as ‘opt-in’ in 4.16 app version to allow IT Admins to prepare for changes (M365 Public Roadmap #117952).
In June with the 4.17 app release, the modernized home screen becomes the default experience. Please see this documentation for important checks and changes.
Enhanced custom background (Teams Rooms Pro SKU only)
On Teams Rooms with the new home screen experience and Teams Rooms Pro license: IT admins will have the option to specify up to 3 background images and identify which image is applied on the main room display, extended room display, and room console, using the following XML settings:
<Theming>
<ThemeName>Custom</ThemeName>
<CustomBackgroundMainFoRDisplay>file1.jpg</CustomBackgroundMainFoRDisplay>
<CustomBackgroundExtendedFoRDisplay>file2.jpg</CustomBackgroundExtendedFoRDisplay>
<CustomBackgroundConsole>file3.jpg</CustomBackgroundConsole>
</Theming>
Please carefully review the following input requirements for this feature to work as expected:
- Images must be in PNG, JPG, JPEG, and BMP format
- <CustomBackgroundMainFoRDisplay> – this XML setting specifies background for the right side of the dual display which has the calendar; input in this setting is required regardless of whether the device is in single or dual display mode
- <CustomBackgroundExtendedFoRDisplay> – this XML setting specifies background for the left side of the dual display which has the time and room info; input in this setting is required when dual display setting is ON
- <CustomBackgroundConsole> – this XML setting specifies background for the room console; input in this setting is optional
To avoid cropping of background images, use the following image dimensions (based on 1080p display standards) for each screen aspect ratio respectively:
- 16:9 – 1920 x 1080 px (minimum image dimension required for room displays)
- 21:9 – 2560 x 1080 px
- 3:2 – 1920 x 1280 px
- 16:10 – 1280 x 800 px (minimum image dimension required for room consoles)
If a 4K image with a 3840 x 2160 px dimension is applied to a 4K display, the full image will be shown. However, if the dimensions of the image and the display do not match, the image scales to fill the frame while preserving the image aspect ratio (without letterboxing) and/or the image is cropped from the center. For example:
- If a 1080p image (1920 x 1080 px) with 16:9 aspect ratio is applied on a 21:9 display, the image scales to fill the frame without distorting the image, and is cropped from the center
- If a 4K image (3840 x 2160 px) is applied on a 1080p display, the image is cropped from the center
Note that once these new custom background XML settings are applied, the legacy custom theme settings will be disregarded. For more information, please see the Microsoft Learn site for the updated custom background guidelines to be published closer to the release.
What you need to do to prepare:
Kindly notify your users about this new experience and update your training and documentation as appropriate.
MC556150 — Microsoft Teams: Collaborative Stageview
<30 Days
Microsoft 365 Roadmap ID 93769
Users can now open app content in a separate Teams window that’s been built for collaboration.
When this will happen:
Standard Release: We will begin rolling out early June 2023 and expect to complete by late June 2023.
How this will affect your organization:
Collaborative Stageview is a new type of Teams window that allows users to engage with content and conversation, side-by-side. For apps that have built their experience for Collab Stage, it allows users to:
- Open their content from eligible adaptive cards directly into a new Teams window
- Engage with their app content in a large Teams canvas
- Continue the conversation from which they came, within the Collaborative Stageview side panel
What you need to do to prepare:
Users opening apps in the Teams web client will be unaffected by this change. In the web client, Collaborative Stageview will fall back to the current Stageview modal.No action is required from admins. Apps that have built for Collaborative Stageview will pop out into new Teams windows.
MC555188 — Device State Change and Submit to Approve Admin Notifications Available in Teams admin center
Rolled Out
In public cloud, Teams admin center has monitoring and alert functionality where admins can get notified if a device's state has changed or if a custom app is submitted for admin approval.
In GCC cloud, Admins can soon use different sets of rules available under the Notifications and alerts section in the Teams admin center to monitor Teams capabilities and receive alerts. For example, you can actively monitor the health of Teams devices such as IP Phones, Teams Rooms on Android, and others if they unexpectedly go offline.
When this will happen:
We will begin rolling out in mid-May and expect to complete rollout by late May.
How this will affect your organization:
Your organization can use Teams monitoring and alerting to do the following items:
- Automatically manage Teams capabilities
- Be alerted if they show something unexpected.
- Take corrective actions to get things back on track.
You must be a global admin in Microsoft 365 or a Teams service admin to configure alerting rules. To use this feature:
- Sign into the Teams admin center.
- From the left navigation, select Notifications and alerts.
- Choose the rule you want to configure from Rules.
What you need to do to prepare:
There is nothing required from you at this time. If you would like to use this feature, please configure rules appropriately for your organization. For additional information, please visit this documentation.
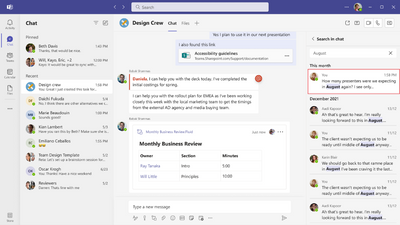
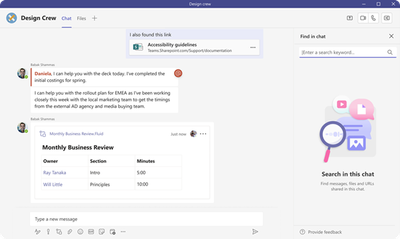
MC554158 — (Updated) A new experience to search within chat and channels.
>60 Days
Microsoft 365 Roadmap ID 122550
Updated June 1, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are excited to introduce a new and improved experience to search within chats and channels.
When this will happen:
- Standard: We will begin rolling this out in mid-June (previously early June) and expect to complete rollout by early July (previously mid-June)
- GCC: We will begin rolling this out in mid-July (previously late June) and complete rollout by early August.
- GCC-H: We will begin rolling this out in late July (previously early July) and complete rollout by mid-August.
- DoD: We will begin rolling this out in mid-August (previously late July) and complete rollout by early September.
How this will affect your organization:
A few key enhancements include:
- The new in-chat and in-channel Search experience will now be available in the right handrail, making it possible to see your chat/channel list and your new search results in one single view. The initiation can be done using the keyboard shortcut Ctrl+F(win) or Cmd +F (Mac):
Chat:
Channel:
Note: Search capability on the new Channels experience is currently available on the main view, and we will extend it to the conversation view very soon.
- In addition to the keyboard shortcut, a dedicated button ‘Find in Channel’, placed on the channel info pane can be used to initiate contextual search:
Note: we are working on bring the search entry point to the chat surface soon.
- We now have introduced enhanced captioning and keyword highlighting to aid the discernment of results in chat and channel:
- In-chat search will now also be available in pop-out chats.
- High-fidelity music mode: You will not receive high-fidelity audio if you turn on spatial audio with other attendees in the meeting with music mode enabled. You will need to disable spatial audio and then rejoin the meeting to get the full-band audio.
MC554154 — (Updated) Teams Rooms on Android support for GCCH
30-60 Days
Microsoft 365 Roadmap ID 121548
Updated June 1, 2023: We have updated the content below with additional information. Thank you for your patience.
Teams Rooms on Android and the Teams Admin Center will fully support GCC-H customers. This is feature available only with the Teams Rooms Pro license.
When this will happen:
We will begin rolling out in mid-June (previously early June) and expect to complete by mid-July (previously early July).
How this will affect your organization:
Pro License customers in GCCH will be able to sign into Teams Rooms on Android and also leverage Teams Admin Center for managing their MTRAs.
Note: The following features are not available in GCC-High.
- People counting in a meeting
- Starting a whiteboard
- Report a problem
- 1 on 1 call recording
MC553265 — TeamsOnly Users Will Anonymously Join Skype for Business Meetings Once Microsoft Removes the Legacy SfBO Infrastructure
Rolled Out
How this will affect your organization:
Some tenants have TeamsOnly users joining on-premises Skype for Business meetings as authenticated users. Please be aware that once Microsoft removes the legacy Skype for Business Online infrastructure, which started in October 2022, TeamsOnly users will only be able to join Skype for Business meetings as anonymous users via the Skype for Business web application.
What you can do to prepare:
You can ensure meetings scheduled by all users (whether on-premises or TeamsOnly) in your organization are Teams meetings, which enables authenticated meeting join for any user in the organization (subject to policy configuration). To achieve this, take the following actions:
- For users assigned Skype for Business Only, or Skype for Business with Teams Collaboration modes, change the coexistence mode to Skype for Business with Teams Collaboration and Meetings. This mode offers the same functionality as the other two, except new meetings scheduled by the user will be Teams meetings instead of Skype for Business meetings. When you assign this mode directly to a user (as opposed to at the tenant level), it will by default also automatically convert any Skype for Business meetings to Teams meetings organized by that user. You can learn how to change coexistence settings here.
- For users that are in Islands mode, you can require them to always schedule meetings in Teams by assigning them an instance of TeamsMeetingPolicy with the PreferredMeetingProviderForIslandsMode=Teams. You can assign this policy in the Microsoft Teams admin center or in the Teams PowerShell Module. See examples here.
- To ensure any existing Skype for Business meetings are converted to Teams meetings (e.g., if you have Islands users), you can use Start-CsExMeetingMigration to trigger the Meeting Migration Service to convert a user's meetings to Teams.
Please ensure your organization understands the behavior described above. Click Additional Information to learn more.
MC537412 — (Updated) Teams Rooms: Windows 11 support for Teams Rooms on Windows devices
Rolled Out
Microsoft 365 Roadmap ID 122148
Updated June 1, 2023: While our rollout plans have not changed, based on feedback from customers who need some additional time to test Windows 11, we are offering a temporary hold on Windows 11 upgrade to customers until November 20, 2023. Customers who want to utilize this option MUST follow these instructions before mid-June 2023 (before 4.17 app update) to delay upgrade to Windows 11.
Instructions:
- Set this registry key to put the Windows 11 upgrade on an MTR on hold.
- Path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PPI\SkypeSettings
- Key: CBU11
- Data: 1 (as a dword)
- Delete the registry key to resume the upgrade.
Important: If you do not set this registry key prior to 4.17 app update (releasing in mid-June), eligible devices will automatically upgrade to Windows 11. Please also note that this only applies to existing in market/ in channel devices not on application version 4.17, and that OEMs have already moved to Windows 11 based images (due to end of sales for Windows 10 IoT Enterprise in Oct 2023, and lead time needed for OEMs to create media).
Teams Rooms on Windows devices that are eligible for Windows 11 upgrade will receive the Windows 11 22H2 release in June 2023 (previously May). This will be offered and installed on their devices with 4.17 dot release. Devices that are not eligible due to an incompatible processor will continue to use Windows 10 per Windows hardware support policy. These devices will be offered Windows 10 22H2 release.
Devices that cannot upgrade to Windows 11 will continue to be supported until the end of Windows 10 End of servicing for General Availability Channel or hardware support from OEM, whichever comes first. Windows 10 releases information atWindows 10 release information. Please note, not all Windows releases are supported for Teams Rooms, to find supported version, see Microsoft Teams Rooms app version support.
In addition, Teams Rooms on Windows OEMs will shift their manufacturing to Windows 11 IoT Enterprise as Windows 10 IoT Enterprise end of license sales is fast approaching (10/14/2023). OEMs with existing Windows 10 licenses inventory (or to support recovery media for existing Windows 10 based devices) may continue to provide Windows 10 based images for some time that should automatically update to Windows 11 post setup. All OEMs are expected to move to Windows 11 IoT Enterprise based images in future. Customers should ensure all new hardware purchases check for Windows 11 compatibility to future proof their device investment.
When this will happen:
Standard Release: We will begin rolling out early May and expect to complete by late May.
How this will affect your organization:
Microsoft Teams Rooms on Windows application release 4.17 will be available in June 2023 (previously May). This app will allow eligible Teams Rooms on Windows devices to receive Windows 11 22H2 update through Windows update. After the dot release has booted normally at least once, customers can either wait for 8 days for Windows 11 22H2 to install automatically or can pull the latest Windows 11 update from Windows Updates manually by checking for updates from the Windows Settings app. Devices that are not eligible will be offered Windows 10 22H2 release.
To check if your device is eligible for Windows 11, you can either check the list of eligible Intel processors for Windows 11 at https://learn.microsoft.com/en-us/windows-hardware/design/minimum/supported/windows-11-supported-int...
What you need to do to prepare:
To ensure that there are no issues preventing the Windows update in your environment, it is recommended to manually update a small set of devices to 4.16.134.0 (Release notes for Microsoft Teams Rooms---manual-update-only) and check for updates, after 4.16.134.0 release has been installed and booted normally at least once on them. From admin mode, check for updates using the Windows Settings app: Windows 11 22H2 or Windows 10 22H2 (depending on what’s supported for your devices) should be offered and should download and install. If the updates are not offered or installed, check for external policies (such as MDM or Active Directory Group Policies) that might be in place for your organization that could block this update.
MC528955 — (Updated) Microsoft Teams: New Files app in Teams
<30 Days
Microsoft 365 Roadmap ID 97677
Updated May 9, 2023: We have updated the rollout timeline below. Thank you for your patience.
Securely store, organize, and collaborate on all your files anytime, from anywhere and across all of your devices with the new files app experience in Teams. The new files app brings a modern experience to all of your content from your chats, channels or meetings including any location from OneDrive or SharePoint.
When this will happen:
Preview: We will complete rollout by late March.
Standard Release: We will begin rolling out in early April and expect to complete rollout by mid-April.
GCC: We will begin rolling out in late May (previously early May) and expect to complete rollout by mid-June (previously late May).
GCC-H: We will begin rolling out in mid-June and expect to complete rollout by late June.
DoD: We will begin rolling out in late June (previously early June) and expect to complete rollout by mid-July (previously late June).
How this will affect your organization:
Users can easily discover and locate files that are relevant right within the Teams app. This makes it possible to locate, share and collaborate with OneDrive files without leaving the Teams app and switching between various apps. An updated menu bar will help you navigate to your content quickly.
- Home: Get back to your recently accessed files
- My files: Access your personal OneDrive files
- Shared: Find files shared with you and files you have shared across M365
- Downloads: Locate files downloaded from Teams on your computer
- Quick Access: Pin document libraries or channels files tab to access them quickly
The existing Files app that is enabled by default will automatically be updated with new files app experience.
What you need to do to prepare:
There is nothing you need to do to prepare.
MC523053 — (Updated) Microsoft Teams: Explicit Recording Consent for Teams Meetings
30-60 Days
Microsoft 365 Roadmap ID 107781
Updated May 25, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Teams is going to support an Explicit Recording Consent meeting policy. When the policy is applied, the Teams meeting window will request explicit consent of all participants to be recorded. Before a user gives consent, the user’s audio, video, and screenshare/consent-share won’t be captured in the meeting recording.
When this will happen:
Standard and GCC: We will begin rolling out in late March and expect to complete rollout by mid-April.
GCC-High: We will begin rolling out in late May (previously late April) and expect to complete rollout by mid-June (previously early May).
DoD: We will begin rolling out in late June (previously late May) and expect to complete rollout by mid-July (previously early June).
How this will affect your organization:
Explicit Recording Consent is OFF by default and is an IT admin policy-controlled feature. Admins can choose to enable the feature either for the entire tenant or for specific individuals based on their business needs.
When the policy is applied, Teams meetings set up by these individuals will request explicit consent from all participants to be recorded.
Before a user gives consent, their audio, video, and screenshare/content-share will be disabled during the meeting. This will prevent their audio, video, and screenshare/content-share from being recorded.
Participants' consent is logged and can be accessed as part of the Attendance Report.
What you need to do to prepare:
You may want to update your training materials indicating that this policy is now supported.
Admins can use PowerShell to enable or disable this feature using the following examples, and the Teams Admin Center will soon support the policy setting as well.
- Set CsTeamsMeetingPolicy -Identity Global -ExplicitRecordingConsent "Enabled"
- Set CsTeamsMeetingPolicy -Identity Global -ExplicitRecordingConsent "Disabled"
Please keep in mind of the following dependencies and limits when deciding to enable the feature:
- The feature relies on Attendance Report; for customers who have disabled the Attendance Report, end users will not be able to enable their mic, camera, or screensharing/content-sharing when a recording is started. If you are unable to enable Attendance Report, we recommend waiting for a future update.
- To avoid disruptions for end-users, they should be using the most recent version of Teams.
- In meetings requiring explicit consent, users joining from unsupported endpoints, such as older client versions and CarPlay, will not be able to enable their mic, camera, or screenshare/content-sharing during recording.
- Teams meeting rooms user and PSTN users can still get recording notifications as of today, but they cannot provide explicit recording consent, and their consent data will be logged as "not applicable" or "auto consent".
MC520319 — (Updated) Microsoft Teams Rooms on Android: User Experience Update 1 2023
<30 Days
Microsoft 365 Roadmap ID 119621, 119620, and 119622
Updated May 9, 2023: We have updated the rollout timeline below. Thank you for your patience.
This update introduces several new features for Teams Rooms on Android that improve the meeting join, content sharing, and hybrid collaboration experiences.
When this will happen:
Roll out to production started late April (previously early March) and is expected to be completed late June (previously by late April).
Note that there can be a delay between when features are released by Microsoft and when they become available on a device model and make. If an update isn't available on your device, check with your device manufacturer for information on when it might become available.
How this will affect your organization:
Join Teams meeting with ID
Users can enter any valid meeting ID and passcode to join a Teams meeting from a Teams Room, making meeting join easier for participants when the room is uninvited to the meeting.
Meet app updates
Users can quickly start an ad-hoc meeting in the room with a tap using the Meet button on home and invite participants to the new meeting. P2P and group calling functionalities are moved under the Call application.
Room reservation extension
During a meeting, in-room users can extend the existing room reservation when the room is available within their desired timeframe. Users can find the option to extend the room reservation on the More menu located at the meeting utility bar. Admins can turn on the “Extend room reservation” setting in the device settings to enable this feature.
Front row
Front row is a layout designed to enhance hybrid meetings for in-room participants: users can see remote attendees at eye level, making the interaction more natural between participants regardless of whether they are in-room or remote. Meeting chat is seen on the right panel and, for dual screens, raised hands are displayed on the left panel for increased visibility. Admins can set front row as the default layout in the device settings. Users can also select front row from the layout switcher on the meeting utility bar.
Meeting chat in Gallery, Large gallery, and Together mode
To promote inclusion, users can choose to show meeting chat on the front of room display in any meeting layout using the layout switcher. Admins can disable the "Show meeting chat" setting in the device settings if needed.
HDMI auto share controls
Admins can control the automatic sharing of HDMI content in a room with the “Automatically share to the room display” setting in the device settings. Admins can disable this setting to require users to tap "Share" after plugging in the HDMI or USB-C cable before content sharing begins. Otherwise, HDMI content is automatically presented to the room display in and out of a meeting by default once users plug in an external source via HDMI ingest.
HDMI audio share
In-room users can share PC system sound when sharing content via HDMI in and out of a meeting. PC system audio is played locally through the room speakers and added into the conference sound for remote participants to hear. If needed, in-room users can turn off audio-sharing in a meeting from the Share menu so that PC system audio does not play into the meeting but continues to play locally. Admins can turn off the “Include audio” setting in the device settings to disable PC system audio from being passed via HDMI.
Annotations
When a participant who’s joining from their desktop initiates an annotation session, in-room users can see the annotations made by other meeting participants on top of the shared content. In-room users can also add annotations using a touch display when the permissions set by the presenter allows other participants to do so. More information on how to use annotations can be found here.
Watermark-enabled meetings support
Teams Premium licensed meeting organizers can safeguard confidential meetings by enabling watermark. Watermark-enabled meetings will show the room account applied as a watermark on top of supported shared content and the video participants' camera stream to deter leaks. More details about this Teams Premium feature are found here.
What you need to do to prepare:
Please plan on updating all Microsoft Teams Rooms on Android in your tenant to the latest version through the Teams Admin Center. Once devices are updated, you can control new functionalities through the device settings and notify your users about these new capabilities and update your training and documentation as appropriate.
MC515531 — (Updated) Pronouns on Profile Cards in Microsoft Teams and Outlook Web
30-60 Days
Microsoft 365 Roadmap ID 86382 and 115511
Updated June 1, 2023: We have updated the rollout timeline below. Thank you for your patience.
We’re adding a new feature to the profile card in Microsoft 365. Users in your organization will soon be able to add pronouns directly to their profile card in Outlook on the web and Teams. Pronouns are the words we use to replace someone's name in a sentence, such as “he,” “she,” or “they” in English.
When this will happen:
- Targeted Release: Rollout will begin late February.
- Standard and GCC: Rollout will begin in late March (previously early March) and is expected to be complete by early April (previously late March). - Complete
- GCC-High: Rollout will begin mid-June and is expected to be complete by late June.
- DoD: Rollout will begin mid-July and is expected to be complete by late July.
How this will affect your organization:
The ability to allow people in your organization to display their pronouns on the profile card is OFF by default for your tenant. If elected, after you have turned pronouns ON, it is optional for users to add pronouns to their profile.
Pronouns will be shown next to the name in the top section of the profile card in Outlook on the web and Teams. Pronouns will be visible to everyone in your organization. If you want people in your organization to have the option of adding pronouns to their profile, you will have to turn pronouns ON for your tenant.
What you need to do to prepare:
Whether or not to share or publicly display pronouns is always up to an individual. Pronouns should never be assigned by a person to another person. It should be up to the person using them to decide when, where, and which pronouns are used – including whether to use this feature, should it be turned on.
Knowing someone’s pronouns does not always equate to knowing their gender identity. Administrators are encouraged to understand any applicable local laws, regulations, and cultural norms that may pose additional risks to employees should their pronouns be publicly displayed and take this into consideration as a decision is reached whether to or not to turn on this feature.
If the feature is utilized, it is recommended that internal and/or external subject matter experts in transgender inclusion be engaged to consider how pronoun display can complement (not substitute) more comprehensive efforts to support transgender communities in your organization.
Once pronouns roll out, you may want to notify your users about this new capability and update your training and documentation as appropriate.
See our available documentation below:
- For Admins: Pronouns in Microsoft 365
- Pronouns on your profile in Microsoft 365
- Pronouns Best Practices
- Frequently Asked Questions About Pronouns
MC509577 — (Updated) Visio Personal App in Teams
30-60 Days
Microsoft 365 Roadmap ID 109596
Updated May 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
Visio will be available soon as a Teams Personal App. There are no changes to the existing file open behavior, however there are new abilities that the Visio Personal App can provide. Additionally, this change comes with a number of UX improvements to the Office ribbon in Teams to provide a decluttered experience consistent with Office for the Web.
When this will happen:
App rollout has begun and is expected to be completed by mid-July 2023.
How this will affect your organization:
The Visio personal app will come pre-installed for all users. New abilities that Visio Personal App will provide include:
- Ability to pin the app to the app bar for easy entry point.
- Right click the app icon in the app bar to pop out documents in a new window, to allow multi-tasking between Teams chats and document editing.
- App home page to navigate documents, view recommended files, or create new file.
Changes to the Office ribbon in Teams include:
- Introduction of the Share menu, consistent with Office for the Web
What you need to do to prepare:
No action is required from admins at this time; the Visio personal app will be available to all users.
MC501981 — (Updated) Microsoft Teams: Automatic lowering of a user's Raised Hand after speaking - DoD
TBD
Microsoft 365 Roadmap ID 90022
Updated May 16, 2023: We have made the decision to postpone rolling out to DoD organizations at this time. We will communicate via Message center when we are ready to proceed.
Teams will soon have a feature that will alert attendees in meetings that have raised their hands and already had their questions addressed to automatically lower their hand. This will allow meeting organizers the opportunity to focus on unanswered questions.
This release will be rolling out only to Microsoft Teams Desktop users.
When will this happen:
Public Preview will roll out in mid-February (previously early February).
Rolling out to Production will begin in mid-March and expect to complete rollout by late April (previously late March). - Complete
GCC will begin rolling out in late April (previously late March) and complete by early May (previously early April). - Complete
GCC-H will begin rolling out in late May (previously late April) and complete by early June (previously early May). - Complete
DoD has been cancelled and we will communicate when we are ready to proceed.
How this will affect your organization:
Users who raise their hand in a Teams meeting and speak in the meeting will see a notification informing them that their hand will automatically be lowered soon. They will be able to choose to keep their hand raised. If the user doesn't take action on the notification, their hand will automatically lower. This should ensure smoother meeting facilitation for organizers and presenters.
What you need to do to prepare:
You may want to notify your users about this new capability and update your training and documentation as appropriate.
MC499441 — (Updated) The Room Remote feature for desktop
TBD
Microsoft 365 Roadmap ID 95482
Updated May 9, 2023: We will not be rolling out to GCC or GCC-High organizations at this time. We will communicate via Message center when we are ready to proceed with those organizations.
The Room Remote feature enables touchless meetings by allowing users to control a nearby shared meeting room device from their Desktop/PC with Teams client.
This feature was first launched on Mobile and will now be available on your Desktop device formfactor.
When this will happen:
Rollout is expected to start mid-February (previously mid-January) and will complete mid-December (previously late March).
How this will affect your organization:
This new feature will be automatically available on the Teams Desktop Client on your Windows Desktop PC so long that the Room Remote feature is enabled on the shared meeting room device and in TAC.
What you need to do to prepare:
No preparation work required.
MC496629 — (Updated) Changes coming to how dialed phone numbers are matched to users – GCCH & DoD
>60 Days
Updated May 11, 2023: We are updating this message as a reminder.
Starting at the beginning of July 2023 Microsoft will be changing how numbers dialed by Teams users or arriving from the PSTN match the number assigned to users. This process is often referred to as Reverse Number Lookup (RNL).
The change applies to users with an assigned phone number with an extension using the following formats:
- Where the last several digits of the base number are also added as the extension. For example, +14025557334;ext=334, where 334 is both included in the base number and as the extension.
- Where both the base number and extension are unique for each user. For example, +14025557253;ext=3111 and +14025556567;ext=3112
- Where the base number is common, and the extension is unique for each user. For example, +14025557000;ext=111 and +14025557000;ext=112
The users configured with this type of phone number are either Teams users or Skype for Business Server on-premises users.
This may be a breaking change if your Teams dial plans and Direct Routing Session Border Controllers are not configured to convert dialed numbers into the full number assigned to the user including the extension.
When this will happen:
We will begin rolling out this change at the beginning of July 2023 and will be complete by mid-August 2023.
How this will affect your organization:
You might be impacted by the change, if you have users configured with phone numbers with extensions.
Today, when a call is made to a phone number, the lookup to see if that number is assigned to a specific user works as follows:
- if a call is made to +14025557334;ext=334, we will find the user configured with the phone number +14025557334;ext=334
- if a call is made to +14025557334, and there is no user configured with +14025557334, we will find the user configured with the phone number +14025557334;ext=334.
This can be an issue in situations where the same base number is used for multiple users. For example:
- User Alice is assigned +14025557000;ext=111
- User John is assigned +14025557000;ext=112
If a call is made to +14025557000, and there is no user configured with +14025557000, we would match to the first user found with +14025557000 as a base number (Alice in this case).
Based on customer feedback, we are changing the matching logic to be an exact string match between the called number and the full phone number configured for a user.
After the change, in the above examples, we will not find a user configured with the phone number +14025557334, +14025557253 or +14025557000 and calls to those number will not match to a user instead of potentially being routed to the wrong person.
What you need to do to prepare:
If you have users configured with phone numbers with the extensions, to prevent calls not being matched to the intended user, please ensure that dialed numbers from Teams users and incoming PSTN calls are formatted to exactly match the full phone number configured on the user accounts.
Check that your tenant dial plans include normalization rules that can translate abbreviated dial strings to the full phone number configured on users. In example above, the following phone number normalization rule will translate a dialed 3-digit number to the full phone number configured on the users to ensure calls will succeed:
- Pattern ^(\d{3})$ and Translation +14025557$1;ext=$1
Check that any phone number manipulation/translation rules used on your Direct Routing Session Border Controller are capable of making the translation to the full phone number configured on your users.
For more information, see:
MC494734 — (Updated) Teams update: Expanded view of the profile card in Teams
<30 Days
Microsoft 365 Roadmap ID 109526
Updated June 1, 2023: We have updated the rollout timeline below. Thank you for your patience.
Beginning in March, users in your organization will be able to use expanded views of the profile card in Teams. The expanded view is already available in Outlook and includes more information, like an overview of the profile, contact information, organizational chart, and LinkedIn tab.
When will this happen:
We will begin rolling out this feature in late May (previously late April) and expect to complete the rollout in late June (previously early May).
What you need to do to prepare:
No preparation is needed for this change. For more information about what users can see on profile cards, see Profile cards in Microsoft 365.
Microsoft Stream
MC556774 — Microsoft Stream playlist is being rolled out to GCCH and DoD
<30 Days
Microsoft 365 Roadmap ID 124797
Microsoft Stream Playlist allows users to organize and share videos across OneDrive and SharePoint both for self-curation as well as to share multiple videos in one go with their audiences. The feature is already available in GA and GCC-M. It's now being rolled out to GCC-H and DoD
When this will happen:
Standard Release: We will begin rolling out late May and expect to complete by early June.
How this will affect your organization:
There will be no impact across tenants. You'll just have an additional way to organize and share videos.
What you need to do to prepare:
There is no specific preparation needed.
MC556773 — View video analytics for ODSP videos
<30 Days
Microsoft 365 Roadmap ID 124873
Video specific analytics for ODSP videos are being made available in the Governments cloud. Users will be able to experience total views and viewers for the last 7, 30, 90 days and all time within the playback experience. They can also access the viewership retention chart to identify the most popular parts of the videos and pinpoint where viewers are dropping off.
When this will happen:
Standard Release: We will begin rolling out late May and expect to complete by early June.
How this will affect your organization:
There will be no impact on the tenant. Users will additionally be able to see analytics for videos they have access to.
What you need to do to prepare:
There is no specific preparation needed.
MC536884 — (Updated) Microsoft Stream: Search a Video Transcript to Stream
<30 Days
Microsoft 365 Roadmap ID 117583
Updated May 30, 2023: We have updated the rollout timeline below. Thank you for your patience.
This feature allows users who are viewing a video to search for keywords contained in the video transcript. This feature is available on video files that have transcripts and are stored in OneDrive or SharePoint.
When this will happen:
Rollout will begin in late May (previously late April) and is expected to be complete by mid-June (previously early June).
How this will affect your organization:
Users can navigate through the search results and click on a portion of the transcript to be taken to the respective spot in the video. Users will need view or edit permissions on a file to search the transcript.
Note: This feature is for searching the transcript of a single video. Users also have the option to search the transcripts of all videos they have permissions to view using Microsoft 365 search.
What you need to do to prepare:
There is no action required from you at this time as this feature will be enabled automatically. For information on viewing, editing and managing video transcripts, please visit this documentation.
Microsoft Purview
MC567472 — Microsoft Purview Records Management: Enhancing inherited and auto-applied retention label behavior in Exchange Online
30-60 Days
We are releasing an enhancement to better align Exchange item lifecycle behaviors with the principles of retention and labeling principles shared with other workloads like SharePoint Online.
This change affects items which have a Microsoft Purview retention label or legacy MRM tag auto-applied or inherited from a parent folder which is then moved to the "Deleted Items" folder either by drag & drop or manual deletion. It does not affect existing behavior for items that are 'permanently' deleted by the user (for example, using the SHIFT+DEL combination), items that have no Microsoft Purview retention labels applied, or items which have a Microsoft Purview retention label or legacy MRM tag applied manually by the user.
The enhancement includes multiple behavior changes which are summarized in the 'How this will affect your organization' section below.
When this will happen:
Rollout will begin at the end of June and is expected to be complete by the end of August.
How this will affect your organization:
The following behaviors will change for items that have an auto-applied retention label, a retention label inherited from a parent folder, or a legacy MRM tag inherited from a parent folder:
- Items with any retention setting applied by Microsoft Purview (any label which retains content for a period of time even if a user deletes them) will have that retention setting enforced when moved to the "Deleted Items" folder regardless of how it was applied or if a default MRM tag applies to the "Deleted Items" folder.
- For items which do not retain content and only enforce deletion after a certain period of time or any other action, when moved to the "Deleted Items" folder will behave as follows:
- If a Microsoft Purview retention label is auto-applied to an item, it will remain applied to the item regardless of whether there is a default MRM tag applied to the "Deleted Items" folder and actions will be processed accordingly based on the auto-applied label's settings.
- If a Microsoft Purview retention label or MRM tag is applied to the item by inheritance from a parent folder and a default MRM tag is not applied to the "Deleted Items" folder, the inherited label/tag will remain applied to the item and actions processed accordingly based on the label/tag settings.
- If a Microsoft Purview retention label or MRM tag is applied to the item by inheritance from a parent folder and a default MRM tag is applied to the "Deleted Items" folder, the label or tag with the shortest deletion period will win and its actions will be processed accordingly based on that winning label or tag settings
This change does not affect:
- The behaviors of any other folders within the mailbox.
- Items that are 'permanently' deleted by the user (for example, using the SHIFT+DEL combination).
- Items that have no Microsoft Purview retention labels or legacy MRM tags applied.
- Items that have a Microsoft Purview retention label or legacy MRM tag manually applied by the user.
What you need to do to prepare:
No action is needed to enable this change; however, you may want to update your documentation and end-user training to incorporate the change in behavior.
Get started with Records Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Learn about retention for Exchange
MC564199 — Microsoft Purview: Service side auto-labeling supports excluding specific locations in SharePoint, OneDrive, Exchange
<30 Days
Microsoft 365 Roadmap ID 124908
We're rolling out a new feature for Microsoft Purview Information Protection to enable greater flexibility in defining the scope of your service-side auto-labeling policies.
When this will happen:
Rollout will begin in mid-June and is expected to be complete by end of June.
How this will affect your organization:
Service-side auto-labeling expands location scoping from All or specific inclusion to specific exclusion. You can scope policies in SharePoint, OneDrive, or Exchange to include All but exclude certain accounts/sites.
What you need to do to prepare:
Get started with Information Protection in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Automatically apply a sensitivity label in Microsoft 365
MC560728 — (Updated) Microsoft Purview compliance portal: General availability of new Insider Risk Management capabilities
30-60 Days
Updated June 1, 2023: We have updated the rollout timeline below. Thank you for your patience.
Coming soon to general availability, Microsoft Purview Insider Risk Management will be rolling out multiple features including an enhanced alert experience, cumulative exfiltration anomaly detection, sequence detection enhancement, new insider risk indicators, trainable classifier support, and new noise management capabilities.
the following Microsoft 365 Roadmap IDs: 83966, 93259, 98160, 115492, 115494, 117601, 117602, 117603, 117604, 117607, 117608, 124772, 124775, 124857, 124860, 124861, 124862, 124863, 124864
When this will happen:
Rollout will begin in early June and is expected to be complete by late July (previously late June).
How this will affect your organization:
The following capabilities will soon be generally available within the Insider Risk Management solution:
Enhanced alert triage experience introduces various improvements to the alert review experience to accelerate time to action, including the ability to further drill into detected sequences within activity explorer, add new alert filtering capabilities, and explore the user activity timeline view with a richer alert history.
Policy customization from alert review experience allows admins to customize an Insider Risk Management policy and adjust policy thresholds from within the alert review experience instead of going through the policy configuration wizard, so customization decisions can be made in the context of alert review activities.
Cumulative exfiltration anomaly detection helps identify data exfiltration risks when a user’s exfiltration activities across all egress channels over the past 30 days exceed organization or peer group norms. A risk score is assigned if the user's cumulative exfiltration activity is unusual compared with others within the same organization or with the same role.
Sequence detection in Insider Risk Management has a few updates:
- Sequence detection can recognize both allowed and unallowed domains, configured by admins with appropriate permissions. Sequences that involve allowed domains will be excluded from being scored, and sequences that involve unallowed domains will receive higher risk scores.
- Sequence detection can be used as a policy trigger. For example, if admins define a sequence such as downloading from a Microsoft 365 location, obfuscating, exfiltrating, then deleting, users who perform the sequence of activities will match the policy and the alert will show up in Insider Risk Management.
- Allows admins to select sequences in data leak and data theft policies without the requirement to select underlying individual indicators. This will allow admins to create more targeted policies with improved alert signals.
New insider risk indicators:
- Increased set of first party indicators will be available in Insider Risk Management, including user activities in Endpoint (Windows 10), Microsoft Teams, Azure Active Directory, SharePoint Online, and Microsoft Defender for Cloud Apps.
- Label downgrading insights can detect users downgrading sensitivity labels on files or SharePoint sites.
- Physical access indicators and connector will allow admins to define priority physical assets. With priority physical assets enabled and the physical badging data connector configured, Insider Risk Management can correlate signals from an organization’s physical control and access systems with other user activities to help make more informed response decisions for alerts.
Trainable classifiers will be supported in Insider Risk Management to recognize various content types specific to your organization.
Noise management capabilities:
- File path exclusions allow admins to configure file path exclusions, so activities around files with specific file paths won’t generate alerts.
- Sensitive information type exclusions allow admins to define sensitive information type exclusions, so files that contain certain sensitive information types won’t generate alerts.
- File type exclusions will extend to email attachments to help reduce noisy signals.
- System noise generated by a single user activity will be de-deduplicated, reducing noise in alerts without losing risk context.
- Site URL and keyword exclusions allow admins to configure SharePoint site URL and keyword exclusions, so activities involving these sites or file names and email subject lines containing certain keywords won’t generate alerts.
Bulk import and export of domains allows admins to upload or download a CSV file of unallowed, allowed, and third-party domains in insider risk settings to fine-tune the detection of activities involving certain domains.
Integration with Communication Compliance: admins with the right permissions can use a Communication Compliance event to configure insider risk policies. This feature helps customers gain more context and identify potentially higher-risk activities that may result in a data security incident such as exfiltration of sensitive information.
What you need to do to prepare:
- To enable cumulative exfiltration activities detection and new insider risk indicators, admins can visit Insider risk settings > policy indicators to choose those new indicators.
- To configure allowed and unallowed domains and all types of exclusions, admins can visit Insider risk settings > intelligent detections.
- To configure physical access indicators, admins will need to set up a connector in the compliance portal to import physical badging data.
- To leverage new indicators and integration with Communication Compliance, admins with the right permissions can visit Policies page to create a new policy or add indicators to existing policies.
- No action is needed to enable other features.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
Get started with Insider Risk Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Learn about insider risk management
MC557813 — Microsoft Purview Data Lifecycle and Records Management: Simulation mode for retention labels
30-60 Days
Microsoft 365 Roadmap ID 109569
We're introducing "simulation mode" in Microsoft Purview Data Lifecycle Management and Microsoft Purview Records Management for auto-labeling policies of retention labels.
When this will happen:
Rollout will begin in late June and is expected to be complete by end of July.
How this will affect your organization:
Simulation mode enables compliance administrators to test their retention auto-labeling policy configuration by identifying which content may be matched by the policy. The simulation of a policy can take as little as a few hours (dependent on the amount of data analyzed), helping admins to rapidly test, modify, and confidently deploy their retention labels through automatic labeling.
Simulation mode will work with policies that apply labels when content contains sensitive information or based on content’s properties or metadata using KQL (Keyword Query Language) queries.
What you need to do to prepare:
There's nothing you need to do to prepare or access this new functionality. To leverage this feature, you will find in the wizard to create a new auto-labeling policy a new step called "Mode". To explore simulation mode, choose the option ‘Test the policy before running it.’
Get started with retention labels and policies in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Learn more about simulation mode
Blog: Simulation mode for retention labels
MC557812 — Microsoft Purview Records Management – Disposition review automatic approval
30-60 Days
Microsoft 365 Roadmap ID 124880
To provide enhanced flexibility to the existing multi-stage disposition review feature in Microsoft Purview Records Management solution, we are adding an ability to automatically approve disposition for each stage after a specific number of days if no action has been taken by a reviewer.
When this will happen:
Rollout will begin in early June and is expected to be complete by early July.
How this will affect your organization:
Once this feature rolls out, Records Management administrators in your organization can create retention labels and choose to turn on automatic approval of disposition for each stage in the label after a specific number of days. Additionally, they can also edit the existing retention labels and choose to turn on this capability to automatically approve disposition of items in each stage. When automatic approval is turned on, if no manual action is taken by any reviewers within the configured auto-approval time period, the item automatically moves to the next disposition stage. If the item is in the only or final stage of disposition review, the item automatically becomes eligible for permanent deletion. Post rollout, this capability will be turned off by default and must be turned on by Records Management administrators for each retention label in their file plan if they would like to use it. The default period for automatic disposition approval is 14 days but Records Management administrators can choose a custom period between 7 and 365 days.
What you need to do to prepare:
There is nothing you need to do to receive this feature. You may consider updating any training or reference material for your Records Management administrators and evaluate if you would like to use this new capability.
Get started with Records Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Disposition of content
MC556780 — Microsoft Purview compliance portal: New and updated Sensitive Information Types (SITs)
Rolled Out
In our continued efforts to improve the coverage and accuracy of out-of-the-box sensitive information types (SITs), we have added 7 new SITs and updated the definition of 2 existing SITs.
When this will happen:
Rollout will begin in mid-May and is expected to be complete by end of May.
How this will affect your organization:
The following new and updated SITs will soon be available to be used in Microsoft Purview compliance solutions including Data Loss Prevention, Auto Labeling, Communication Compliance, and Microsoft Cloud App Security.
New SITs available (see definitions:(
- UAE identity card number
- UAE passport number
- South Korea passport number
- South Korea driver's license number
- Malaysia passport number
- Singapore passport number
- Singapore driver's license number
Updates to existing SITs:
|
SIT name |
Existing definition |
Additional patterns we will look for |
|
Japan Bank |
Seven or eight digits: o four digits bank account branch code o a space or dash (optional) o three digits |
Ten to twelve digits: o three digits followed by a space or dash (optional) o four digits bank account branch code followed by o a space or dash (optional) o three digits |
|
Washington State Driver's License number |
The number is 12 characters in length: o The first five characters are the first five letters of the licensee’s last name, substituted with an asterisk if the name is shorter than five characters. o The following two characters are the initials of the first and middle name. o The next three characters are digits o The last two characters are letters or digits |
ID number with 12 characters with “WDL” then 9 random (no vowels or Q or V): o The new pattern starts with “WDL” followed by nine letters and numbers. o It will not contain any vowels or the letters Q and V. o It will not contain any special characters. o The 10th position is always a number.
Reference: Major changes coming to Wash. state driver's licenses | KOMO (komonews.com), DLN_Real-ID-Fact-Sheet.pdf (driving-school.com) |
What you need to do to prepare:
No action is needed to enable these changes. Your existing policies (including DLP policies) need not be changed.
Get started with sensitive information types in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Sensitive information type entity definitions
MC556771 — Microsoft 365 Compliance Center update: eDiscovery PowerShell cmdlet supporting certificate-based authentication (CBA)
Rolled Out
Microsoft 365 Roadmap ID 106112
This is a follow up to the post MC515529. Basic authentication is no longer supported and has been retired. See Deprecation of Basic Authentication in Exchange Online | Microsoft Learn.
When this will happen:
Basic authentication will be retired by end of May 2023 for any tenants that had an exception.
How this will affect your organization:
This change will affect the authentication method of your organization’s eDiscovery scripts that relied on a username and password stored in a local file/vault.
What you need to do to prepare:
Assess if the changes will affect your organization’s eDiscovery workflow. If so, update internal documentation and script authentication. Provide training to all eDiscovery users in your organization and update relevant documentation if needed.
Refer this article for support on CBA - App-only authentication in Exchange Online PowerShell and Security & Compliance PowerShell | Microso...
MC552329 — Microsoft Purview eDiscovery (Standard) to eDiscovery (Premium) case upgrade tool (preview)
Rolled Out
Microsoft 365 Roadmap ID 109542
Coming soon to public preview, we are releasing a tool to allow eDiscovery administrators to upgrade their existing eDiscovery (Standard) case to eDiscovery (Premium) to unify cases into a single platform.
When this will happen:
Rollout will begin in mid-May and is expected to be complete by end of May.
How this will affect your organization:
With this tool, an eDiscovery administrator will be able to select a particular case from eDiscovery (Standard) cases list to move to eDiscovery (Premium).
All upgraded cases will have their existing search and hold retained. This upgrade is architected to change the case type and not perform any actual migration of the hold policies. This means no hold is removed and no new hold is re-created in the process. This ensures no data is lost or erased in the migration process.
Note: The case upgrade can be triggered by an eDiscovery Administrator only.
Choosing to upgrade a case from eDiscovery (Standard) to eDiscovery (Premium)
What you need to do to prepare:
Assess if the changes will change your organization’s eDiscovery workflow. If so, update internal documentation and provide training to all eDiscovery users in your organization as needed.
The upgrade is not reversible so please ensure you test this process with a few test cases before proceeding with a mass upgrade.
You can access the eDiscovery (Premium) solution in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Microsoft Purview eDiscovery solutions
MC551014 — (Updated) Microsoft Purview eDiscovery (Premium): Review Set – Advanced filters
30-60 Days
Microsoft 365 Roadmap ID 124796
Updated May 25, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are excited to introduce several usability enhancements for filtering items in review sets within the eDiscovery (Premium) solution in the Microsoft Purview compliance portal.
When this will happen:
Rollout will begin in mid-June (previously mid-May) and is expected to be complete by mid-July (previously mid-June).
How this will affect your organization:
With the new advanced filters feature, admins can do the following:
- quickly search for filter conditions
- create complex filters using either "AND" or "OR" conditions
- easily iterate your queries with undo and redo buttons
- manage saved filters (edit name, delete) without having to navigate to another panel
- use "Is empty/Is not empty" conditions for each filter
Compound query, is empty condition, searchable keys
Edit name, Delete
What you need to do to prepare:
No action is needed to enable these updates. Once the rollout is complete, you can take advantage of the new grouping options and configurations in your eDiscovery (Premium) review sets. Distribute the relevant documentation to your organization's eDiscovery admins and managers for a better understanding of the new enhancements.
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Query the content in a review set
MC550037 — (Updated) New functionality coming to Microsoft Purview Compliance Manager
<30 Days
Microsoft 365 Roadmap ID 102404 and 124884
Updated May 25, 2023: We have updated the rollout timeline below. Thank you for your patience.
We're introducing new functionality to Microsoft Purview Compliance Manager to enable integration with Microsoft Defender for Cloud. Additionally, we're rolling out connectors for Salesforce and Zoom to enable increased visibility across your data estate.
When this will happen:
Rollout will begin in early May and is expected to be complete by late June (previously late May).
How this will affect your organization:
Your current assessments will not be affected by this update. However, this update will allow you to add automated, resource-level testing across Azure, Google Cloud Platform (GCP), Amazon Web Services (AWS), Salesforce, and Zoom to our existing Microsoft 365 assessments. This will help you assess your compliance posture more comprehensively across your data estate.
What you need to do to prepare:
To use the Microsoft Purview Compliance Manager integration with Microsoft Defender for Cloud, you will need to enable either the Foundational CSPM or Defender CSPM plan and assign the standards you wish to assess to your Azure subscriptions. For GCP and AWS environments, you would also need to set up relevant connector(s) in Defender for Cloud.
Get started with Compliance Manager in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Microsoft Purview Compliance Manager
MC546441 — (Updated) Licensing Check implementation for Teams DLP
<30 Days
Updated May 9, 2023: We have updated the content below for clarity. Thank you for your feedback.
Microsoft Purview Data Loss Prevention (DLP) for Teams helps organizations prevent sensitive data from being shared via Microsoft Teams channel or chat session. To prevent users from sharing sensitive information on Teams, customers need to assign Microsoft 365 E5/A5/G5/F5 licenses to their users as Teams DLP is made available through Microsoft 365 E5/A5/G5/F5 licenses. You can find a list of licenses that include Teams DLP capability here.
Please note – this is not a new change and Teams DLP has been a part of the Microsoft 365 E5/A5/G5/F5 licenses since it was launched.
Currently organizations with Microsoft 365 E3/G3/A3/F3 licenses assigned to their users are able to create Teams DLP policies, however starting June 30, 2023, organizations will require Microsoft 365 E5/A5/G5/F5 (or equivalent) licenses to use Teams DLP.
When this will happen:
June 30, 2023
How this will affect your organization:
You are receiving this message as a reminder to ensure your users who are currently covered with Teams DLP policies have the required Microsoft 365 E5/G5/A5/F5 licenses before June 30 2023. If you already have the mentioned E5 licenses, this message is not relevant to you, and we request you kindly ignore this message.
If your users within the scope of your Teams DLP policies are assigned Microsoft 365 E3/G3/F3/A3 licenses, post June 30, 2023, your existing Teams DLP policies covering these users will become dormant and will not process any Teams messages for data loss prevention. You will not be able to create new Teams DLP policies or make changes to your existing Teams-only DLP policies that cover these users, and these users will not be block/audited while sharing sensitive information over Teams. The existing alerts while the policy was active will continue to be available for triage and remediation but no new alerts will be generated for these users.
If you have a DLP policy that covers multiple locations and one of the locations is Teams, that policy will continue to be active for all other locations except Teams. You will be able to edit such policies and remove Teams as a location in the policy configuration experience.
Please note that your Teams only DLP policies will not be deleted and will continue to be visible in the Microsoft Purview compliance portal for future use in the event that you are able to assign the required licenses to your users.
We recommend you assign the users within the scope of the Teams DLP policies appropriate Microsoft 365 E5/G5/A5/F5 licenses to continue to benefit from Teams DLP.
See which licenses include Teams DLP here.
Learn more about Teams DLP here.
MC545909 — (Updated) Microsoft Purview Insider Risk Management multiple feature enhancements
<30 Days
Microsoft 365 Roadmap IDs 117605, 122283, 122284, and 122285
Updated May 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
Coming soon to general availability, Microsoft Purview Insider Risk Management is rolling out enhancements to alert experience, policy wizard, quick policies onboarding experience, and recommended actions.
When this will happen:
Rollout will begin in late May (previously early May) and is expected to be completed by the late June (previously late May).
How this will affect your organization:
The following capabilities will soon be generally available within Insider Risk Management:
- Enhanced alert experience will display alert details such as an explanation of why an alert was created so you are able to review the riskiest user actions that may result in a data security incident in an alert.
- Policy wizard enhancements will simplify configuration of indicators, sequence detection, cumulative exfiltration detection, and risk score boosters.
- Enhancements to the Insider Risk Management quick policies onboarding experience will enable administrators to create a policy with a new one-step process.
- Recommended actions enhancements will include the ability to turn on weekly or daily email notifications for key events such as high severity alerts and all warnings summary along with additional suggestions to help optimize policy configurations.
What you need to do to prepare:
No action is required to enable these capabilities.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
Get started with Insider Risk Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Learn about insider risk management
MC541159 — (Updated) Microsoft 365 admin center: Viva Goals Usage Report
<30 Days
Microsoft 365 Roadmap ID 117599
Updated May 30, 2023: We have updated the rollout timeline below. Thank you for your patience.
A new report will be made available to help you understand how Viva Goals is used within your organization. The new usage report in the Microsoft 365 admin center will provide metrics on the number of active users including trial and paid licenses and platform distribution (Teams, Slack, Azure DevOps, and Web) with the ability to view 7/30/90/180 day timeframes.
When this will happen:
Rollout will begin in early June (previously late May) and is expected to be complete by late June (previously late May).
How this will affect your organization:
Using the Viva Goals usage report, Admins will be able to view metrics for how people in your organization are using Viva Goals and in which platforms.
What you need to do to prepare:
Admins can assign the available licenses in their tenant to individual users based on their usage and license requests, via the Microsoft admin center. Once released, you can view Viva Goals reports by going to the Microsoft 365 admin center -> Reports -> Usage -> Viva Goals.
For more information on Viva Goals visit Introduction to Microsoft Viva Goals.
MC538383 — Microsoft Purview eDiscovery (Premium): Enhancements for Teams meeting recordings
Rolled Out
Microsoft 365 Roadmap ID 106101
Updated May 9, 2023: This release is complete for Preview.
Coming soon to public preview, we're rolling out enhancements to Teams meeting recording and video files stored in OneDrive and SharePoint to improve management within eDiscovery workflows.
When this will happen:
Rollout will begin in early April and is expected to be complete by end of April.
How this will affect your organization:
This update enables collection and review of metadata associated with Teams meeting recordings and video files stored in OneDrive and SharePoint including transcripts/captions, chapters, and custom thumbnails.
What you need to do to prepare:
Assess whether these changes will impact your organization's eDiscovery workflow, then update internal documentation and provide user training as needed.
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal.
Learn more: Conduct an eDiscovery investigation of content in Microsoft Teams
MC515536 — (Updated) Microsoft Purview | Data Lifecycle Management and Records Management – Microsoft Graph APIs for extensibility
Rolled Out
Microsoft 365 Roadmap ID 88276
Updated May 11, 2023: We have updated the rollout timeline below. Thank you for your patience.
As a part of our extensibility vision and first release to Microsoft Graph, we are introducing three new APIs for retention labels, events, and event types in the Microsoft Graph beta environment. These APIs will enable you to customize and extend on what we have built in the product so far.
These APIs can be used by compliance admins and developers to manage retention labels in Data Lifecycle and Records Management solutions.
When this will happen:
Rollout will begin in late March (previously late February) and is expected to be complete by late May (previously late April).
How this will affect your organization:
If your organization needs to automate any operation related to retention labels or events, we recommend you achieve this by using the new Graph APIs instead of using PowerShell cmdlets. With Graph, we use REST APIs that support better security, extensibility, and app authentication features.
The three APIs are available under the security node and the endpoints to access them are as follows:
|
Entity name |
Endpoints |
Solution |
|
Labels |
security/labels/retentionLabels |
Data Lifecycle, Records Management |
|
Events |
security/triggers/retentionEvents |
Records Management |
|
Event types |
security/triggerTypes/retentionEventTypes |
Records Management |
What you need to do to prepare:
Permissions
Currently, these APIs are supported through delegated permissions only, which are managed through the Graph interface. We are introducing two new permissions which you will need to access these APIs:
- recordsmanagement.read.all
- recordsmanagement.readwrite.all
Licensing
Access to Data Lifecycle Management and Records Management features varies based on your Microsoft 365 license level. See Microsoft 365 guidance for security & compliance - Service Descriptions for licensing requirement details.
Get started with Data Lifecycle Management and Records Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- Use the Microsoft Graph records management API
- Create retention labels for exceptions
- Start retention when an event occurs
Microsoft Defender / Identity
MC567494 — Microsoft Defender for Identity: Classic portal automatic redirection
<30 Days
Beginning on June 30, 2023, access to Microsoft Defender for Identity legacy portal at portal.atp.azure.com will be unavailable. Any request will be automatically redirected to Microsoft 365 Defender portal at security.microsoft.com.
All new and existing tenants will be automatically redirected to the Microsoft 365 Defender portal, and the option to opt-out will no longer be available.
When this will happen:
June 30, 2023
How this will affect your organization:
Once the forced redirection takes place, any requests to the standalone Defender for Identity portal (portal.atp.azure.com) will be redirected to Microsoft 365 Defender (securtiy.microsoft.com) along with any direct links to its functionality.
Organizations cannot manually opt-out and disable the setting.
What you need to do to prepare:
Ensure your security teams are familiar with Defender for Identity’s features and settings as they are represented in Microsoft 365 Defender. If your security teams need help, please direct them to the updated documentation available here.
MC565271 — System preferred MFA method is Generally Available
>60 Days
In today's landscape, organizations and users utilize various authentication methods with varying levels of security. Unfortunately, users often select less secure MFA methods, even when more secure options are available. This may be due to convenience, lack of awareness, or technical limitations.
To encourage the use of the strongest available method, we are introducing system-preferred authentication for MFA. This system prompts users to sign in with the most secure method they've registered and the one that's enabled by admin policy. This transition from choosing a default method to always using the most secure method will promote better security practices. If users can't use the prompted method, they can choose an alternative MFA method.
When this will happen:
We will begin rolling out in mid-July and expect to complete by mid-August.
How this will affect your organization:
Microsoft managed will be rolled out as enabled. Admins will have the control to disable the feature.
Admins can enable the feature via the admin UX in the Azure Portal or GraphAPI. For example, if a user named "John Doe" registered both SMS and Microsoft Authenticator and used SMS as the default option to sign in, the system-preferred method (Authenticator) will be presented to the user once the feature is enabled.
We launched this with Microsoft-managed set to disabled. As mentioned above, we will be setting "Microsoft-managed" to enabled from the end of June 2023. While we highly encourage you to adopt this feature for your entire tenant, should you need to you can either scope the feature for a segment of your user population or disable it if necessary. The feature will ultimately be set to Microsoft-managed (enabled) for all tenants, with no option to disable it.
To ensure adequate preparation time, detailed timelines will be shared by June. Deploying this feature with the rollout controls is highly encouraged to enhance security and ensure users always use the most secure authentication method first. The feature is now available from your tenant.
What you need to do to prepare:
We strongly recommend that tenants enable the feature.
MC559251 — Update your custom detections to leverage new ActionTypes in DeviceNetworkEvents
30-60 Days
On July 18, 2023, Microsoft will be retiring a subset of signatures found in the "NetworkSignaturesInspected" action type of Advanced Hunting. With the recent integration of Zeek providing advanced protocol parsing capabilities, which result in better visibility into full network sessions compared to the raw packet bytes found in the "NetworkSignaturesInspected" action type of Advanced Hunting today, the effort to consolidate will provide a better overall experience for our customers by reducing the signatures that serve similar functions without the added benefits provided by the new Zeek alternative.
When this will happen:
July 18, 2023
How this affects your organization:
For customers currently using the "NetworkSignaturesInspected" action type, here is a list of signatures that will be deprecated, referenced alongside their alternatives available in Advanced Hunting:
|
Protocol / Signature Name |
Old Action Type |
New Action Type |
|
SSH |
NetworkSignatureInspected |
SshConnectionInspected |
|
FTP_Upload |
NetworkSignatureInspected |
FtpConnectionInspected |
|
FFP_Client |
NetworkSignatureInspected |
FtpConnectionInspected |
|
HTTP_Client |
NetworkSignatureInspected |
HttpConnectionInspected |
|
HTTP_Server |
NetworkSignatureInspected |
HttpConnectionInspected |
|
HTTP_RequestBodyParameters |
NetworkSignatureInspected |
HttpConnectionInspected |
|
HTTPS_Client |
NetworkSignatureInspected |
SslConnectionInspected |
|
DNS_Request |
NetworkSignatureInspected |
DnsConnectionInspected |
What you can do to prepare:
Your organization might be using a "NetworkSignatureInspected" action type in your Advanced Hunting queries and custom detections. Particularly, you might be using a Signature Name that is going to be deprecated soon. Please update your queries with the new action types so that you can leverage this valuable data and avoid breaking your current custom detections.
An example of your old query:
DeviceNetworkEvents
| where ActionType == "NetworkSignatureInspected"
| extend AdditionalFields = todynamic(AdditionalFields)
| where AdditionalFields.SignatureName == "SSH"
Your new query:
DeviceNetworkEvents
| where ActionType == "SshConnectionInspected"
MC556156 — MDA - custom the email sender settings change
Rolled Out
Microsoft Defender for Cloud Apps is making a change to the custom email notification system following the convergence to the unified portal.
When this will happen:
We will begin rolling out this change in mid-May and expect to complete by late May.
How this affects your organization:
All emails will be sent from Microsoft Defender for Cloud Apps and will no longer support the option to customize the email sender identity, in the settings page.
Note: All emails will continue to be sent, and there will be no change in content of the email notifications.
What you can do to prepare:
If your organization actively onboarded this custom option - the identity of the sender will change automatically to Microsoft Defender for Cloud Apps.
MC551024 — Microsoft Secure Score is retiring the option to share recommended action details through Microsoft Planner
<30 Days
The option to share recommended actions details from Microsoft Secure Score using Microsoft Planner is being retired.
You can continue to share recommended action details through a link, email or Microsoft Teams.
When this will happen:
We will be making this change early June
How this will affect your organization:
Sharing recommendation details through Microsoft Planner will be no longer supported.
What you need to do to prepare:
If you currently share recommended actions details through Microsoft Planner, use one of the alternate methods available.
MC532607 — (Updated) Microsoft Authenticator Lite in Outlook
Rolled Out
Microsoft 365 Roadmap ID 122289
Updated May 17, 2023: Today we are starting rollout for Authenticator Lite (in Outlook) to enter GA! The Microsoft managed value of this feature will be changed from ‘disabled’ to ‘enabled’ on June 9th. We have made some changes to the feature configuration, so if you made an update before GA (5/17), please validate that the feature is in the correct state for your tenant prior to June 9th. If you do not wish for this feature to be enabled on June 9th, move the state to ‘disabled’ or set users to include and exclude groups.
Authenticator Lite (in Outlook) is a feature that allows your users to complete multi-factor authentication for their work or school account using Outlook on their iOS or Android device. This feature will be enabled on June 9th for all tenants that have not disabled it. If you do not wish for this feature to be enabled on June 9th, move the state to ‘disabled’ or set user include and exclude groups prior to June 9th.
We always recommend having users download Authenticator to complete their sign-ins, where we can offer the most up-to-date security features. However, users that have not downloaded the app to their device can now approve authentication requests and receive TOTP codes in Outlook, bringing the security of Authenticator to a convenient location.
Admins can enable this feature by leveraging the Authentication Methods policy in Azure Active Directory.
When this will happen:
Rollout of this feature in Outlook will begin in early March, starting public preview. Feature controls are available via MS Graph.
This feature will move to general availability in mid-May 2023
On June 9th, this feature will be enabled for all users by default unless admins have taken action to disable or enable it before then. Any settings configured before June 9th will not be changed.
What you need to do to prepare:
Starting mid-March, you can choose to enable this preview for your users from Azure Active Directory. We highly recommend that you enable users that are not already using the Microsoft Authenticator app (or another strong authentication method) for this feature at the start of public preview. This feature brings a security enhancement to those users still using telecom transports to authenticate.
This feature will roll out to tenants in the state ‘Microsoft managed’. For the duration of public preview, leaving the feature set to ‘Microsoft managed’ will have no impact on your users and the feature will remain turned off. In April 2023, we will remove preview tags and enter general availability. At GA, 'Microsoft managed' will remain set to disabled and there will be no tenant impact. On June 9th 2023, if the feature is still set to ‘Microsoft managed’, your tenant will be eligible to be enabled for this feature by Microsoft, as 'Microsoft managed' will be set to enabled. If you do not wish for this feature to be enabled on June 9th, move the state to ‘disabled’ or set users to include and exclude group prior to June 9th.
MC498471 — (Updated) IPv6 coming to Azure AD
<30 Days
Updated May 30, 2023: IPv6 support is rolling out globally across all Azure AD regions, which may have an impact on Azure Active Directory customers. Your users might experience blocks or receive more multi-factor authentication requests than usual. In such cases, we recommend reviewing your tenant’s sign-in logs.
This impact on your tenant could be due to end users connecting from IPv6 ranges that are not configured in your tenant’s Named locations. To address this, please follow the steps outlined on this page to identify IPv6 ranges in your tenant’s environment and configure the necessary settings.
Please share the following guidance with the relevant members of your IT administration team:
- IT / Security Admin: Utilize the sign-in report described in the Identifying IPv6 traffic with Azure AD Sign-in activity reports. Use the resulting address list to determine if any IPv6 ranges need to be added to your Azure AD Security Named locations, following the steps provided. It’s also important to collaborate with your internal networking teams to verify IPv6 ranges for your organization, as required.
- Network admin: Collaborate with your IT/Security admin to identify known IPv6 ranges in your network infrastructure. Add these ranges to your tenant’s existing Azure AD Named locations by following the steps provided.
We will continue to roll out IPv6 across all Azure AD regions until the end of June 2023.
Earlier, we had announced our plan to bring IPv6 support to Microsoft Azure Active Directory (Azure AD) enabling our customers to reach the Azure AD services over IPv4, IPv6 or dual stack endpoints. This is just a reminder that we’ll begin introducing IPv6 support into Azure AD services in a phased approach, starting March 31st, 2023.
If your networks don’t support IPv6, you don’t need to take any action to change your configurations or policies. For most customers, IPv4 won't completely disappear from their digital landscape, so we aren't planning to require IPv6 or to de-prioritize IPv4 in any Azure AD features or services. We will continue to share additional guidance on IPv6 enablement in Azure AD at this easy to remember link https://aka.ms/azureadipv6.
With the growing adoption and support of IPv6 across enterprise networks, service providers, and devices, many customers are wondering if their users can continue to access their services and applications from IPv6 clients and IPv6 networks.
Today, we’re excited to announce our plan to bring IPv6 support to Microsoft Azure Active Directory (Azure AD). This will allow customers to reach the Azure AD services over both IPv4 and IPv6 network protocols (dual stack).
For most customers, IPv4 won't completely disappear from their digital landscape, so we aren't planning to require IPv6 or to de-prioritize IPv4 in any Azure Active Directory features or services.
When this will happen:
We’ve been gradually rolling out IPv6 for some of our services for a while. Starting in late March 2023 we'll begin enabling IPv6 for Azure AD authentication. We will introduce IPv6 support into Azure AD authentication in a phased approach, beginning late March 2023.
What you can do to prepare:
We have guidance below which is specifically for Azure AD customers, who use IPv6 addresses and also use Named Locations in their Conditional Access policies.
If you have public IPv6 addresses representing your network, take the actions that are described in the following sections as soon as possible.
Customers who use named locations to identify specific network boundaries in their organization, need to:
- Conduct an audit of existing named locations to anticipate potential impact;
- Work with your network partner to identify egress IPv6 addresses in use in your environment.;
- Review and update existing named locations to include the identified IPv6 ranges.
Customers who use Conditional Access location based policies, to restrict and secure access to their apps from specific networks, need to:
- Conduct an audit of existing Conditional Access policies to identify use of named locations as a condition to anticipate potential impact;
- Review and update existing Conditional Access location based policies to ensure they continue to meet your organization’s security requirements.
Failing to follow these steps might result in the following impact:
- Users of IPv6 addresses may be blocked, depending on your organization's Conditional Access policies and Identity Protection configurations.
- False positive detections due to 'Mark as trust location' not being checked for your internal networks and VPN’s can result in users being marked as risky.
We will continue to share additional guidance on IPv6 enablement in Azure AD here: IPv6 Support in Azure Active Directory.
Learn more about Microsoft identity:
- Get to know Microsoft Entra – a comprehensive identity and access product family
- Return to the Microsoft Entra (Azure AD) blog home
- Share product suggestions on the Entra (Azure AD) forum
Exchange Online / Microsoft Defender for Office / Outlook
MC556777 — Safe Attachments policy: Retire option ‘Apply the SafeAttachments detection response if scanning cannot complete'
<30 Days
We will be retiring the Safe Attachments option 'Apply the SafeAttachments detection response if scanning cannot complete (timeout or error)' starting early June 2023.
When this will happen:
The change will start rolling out early June 2023 and complete by late June 2023 for WW. For Government clouds, the rollout will start early July 2023 and complete by late July 2023.
How this will affect your organization:
The option ‘Apply the SafeAttachments detection response if scanning cannot complete (timeout or error)’ was added during the early days Safe Attachment policies. However, issues with errors and timeouts in Safe Attachments evaluations have been drastically reduced. In fact, selecting this option today can actually cause false positives (the Safe Attachment policy action is applied to benign messages).
Therefore, this option is being retired. In the future, we’ll add a new option to handle actionable outcomes.
The highlighted option in the screenshot will be retired as per the rollout dates.
Once this change is rolled out, this option is removed from the Safe Attachments policy.
What you need to do to prepare:
No action by admins is required as part of this retirement.
Safe Attachments policy settings
MC556775 — (Updated) Planned Maintenance: Updates to mail encryption from external mail
Rolled Out
Updated June 1, 2023: We have completed this maintenance and the mail will no longer be rejected/NDR. Thank you for your patience.
We have maintenance planned for Exchange:
When this will happen:
- Starting: May 22, 2023
- Ending: May 31, 2023
How this will affect you organization:
As part of this planned maintenance, the following feature areas may be affected: Microsoft Purview Message Encryption. Any customers that use Exchange Mailflow rule or Data Loss Protection to encrypt mail may have incorrectly configured mail to try to apply encryption to external incoming mail. This is not a valid configuration. As a result, this change will explicitly reject the mail back to the original sender. The sender will receive a mail with NDR txt: "Emails NDRed with 550 5.7.162 OmeEncryptionAgent; Permanent Failure 550-5.7.162 Exception encountered: RmException. 550-5.7.162 Exception message: ETR encryption only applies to outgoing mail"
This maintenance is planned outside of normal business hours, to help minimize any impact to your organization.
For organizations with users around the globe, we recognize that "outside of normal business hours" might affect you differently. We apologize for the impact this may have on your users. We are working hard to improve Exchange, to minimize these maintenance windows.
What you need to do to prepare:
During this planned maintenance window, the following workarounds can be used: This is an automatic update. There is no change required to existing data loss prevention policy or mail flow rule, but we do highly recommend administrators to update their policy or mail flow rule to ensure that they have added the condition to that mail is coming from inside the online organization. For details, on setting this, refer to step 6 of Define mail flow rules to encrypt email messages for mail flow rule.
MC556159 — Message List Selection UI updates for Outlook on the Web and New Outlook for Windows
<30 Days
Microsoft 365 Roadmap ID 125905
In order to save space on the message list in Outlook, we are making an UI update: From "selection circles on the left side of each row" to "Select mode that you have to get into before checkboxes appear", using a button in the top-right corner of the Message List. Users may have to acclimate themselves to the new Selection user experience.
In addition, mouse+keyboard multi-selection where users hold down Ctrl or Shift will continue to work as before.
When this will happen:
We will begin rolling out in mid-May 2023 and expect to complete rollout by early June 2023.
How this will affect your organization:
This will affect users who do not have "Sender Images" enabled in the Message List. If you have "Sender Images" turned on, hovering over the images will still show the checkboxes, even if you did not get yourself into "Select Mode". To review if you have "Send image" enabled, go to Settings > Mail > Layout and scroll to "Sender image".
What you need to do to prepare:
There is nothing to prepare for this change.
MC556157 — Edit and Reply disabled in file previewer
<30 Days
We are retiring the option to edit and reply with Word, Excel, and PowerPoint files from attachment previews in Outlook. Users will still be able to edit their files using web or desktop apps and then attach a copy or a link to the file in OneDrive to share it.
When this will happen:
We will start rolling out this change in late June 2023.
How this will affect your organization:
Users of this feature will now have to open the attachment using web or desktop apps and then download a copy or save the edited file to OneDrive before sharing it either as an attachment or a link.
What you can do to prepare:
You may consider updating your training and documentation as appropriate.
MC555190 — Microsoft To Do Web app Available for GCCH and DoD customers
>60 Days
Microsoft To Do Web app will be released for GCCH and DoD customers. Please note that Microsoft To Do will be replacing the legacy tasks module in Outlook for Web.
Microsoft 365 Roadmap ID 124891
When this will happen:
We will begin rollout in early June and aim to be completely rolled out by late June. The toggle for switching between legacy tasks and To Do experience will be available in Outlook Web app until mid-August 2023.
How this will affect your organization:
If applicable, users will get a toggle to transition back to the legacy tasks experience. This toggle will only be available for one month, post which To Do Web will be the only tasks experience in Outlook for Web.
What you need to do to prepare:
You may want to update your internal documentation. Please note, shared lists outside of your organization will not be possible. At the same time, users will not receive shared list notifications.
MC552788 — (Updated) Outlook: Mandatory labeling pre-compose for iOS
<30 Days
Microsoft 365 Roadmap ID 109544
Updated May 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
We have listened customer feedback on Outlook mobile needing to meet the mission of "On the Go" and for organizations to have mandatory labeling enabled without default labeling and would like to have the label selection first before going to compose the email. When the users click "Send", the email could just be sent without any forgotten labeling pop ups. Outlook mobile will introduce a new MDM setting to allow admins to enable this louder mandatory configuration for Outlook mobile clients (iOS and Android) specifically. We will enable Android first in early Q1 of 2023, and iOS will release in Q2 of 2023.
This release will include supporting the new sensitivity bar below the subject line as well as support label colors.
When this will happen:
Outlook iOS Standard Release: We will begin rolling out early May and expect to complete by early June (previously late May).
How this will affect your organization:
- If your organization has a prompter mandatory label experience pre-compose, make sure you enable mandatory label for specific users, and then set Intune MDM setting "com.microsoft.outlook.Mail.LouderMandatoryLabelEnabled" to be "true", then the applied users will see the select label page first before drafting the email when the user start new email.
- If your organization has set Label policy -AdvancedSettings @{HideBarByDefault="False"}, on Outlook mobile you will see the label selection now is below the subject line. If you do not set that value or set it to be True, Sensitivity label will still bel under compose.
- Outlook Android will also support label colors if admin configured so.
What you need to do to prepare:
If you do not want the prompt mandatory UX or the new sensitivity bar, you do not need configure any setting for it. The default new UX will be off.
MC531738 — (Updated) Launching new way to open links in Edge from Outlook for iOS and Android
Rolled Out
Updated May 25, 2023: We have updated the content below with details on how to manage through Intune.
Currently users open links automatically from Outlook for iOS and Android in their default browser. This change will prompt users to choose their browser instead. Users can choose their default browser if they prefer and configure that preference in their Outlook Mobile settings.
We apologize for not communicating about this change sooner, per our commitment to proactive change communication.
When will this happen:
This is currently rolling out.
How will this affect your organization:
- Users will be seeing this experience launch when they open a link.
- If Edge is not installed, they will have the option to download it.
- In Intune, leverage these app configuration policies:
- com.microsoft.outlook.Settings.OpenLinks.UseSystemDefaultBrowser
- com.microsoft.outlook.Settings.OpenLinks.UserChangeAllowed
MC525759 — MDO: Safe Attachments policy: Deprecate policy action ‘Replace’ for malware detections in attachments (Phase 2)
<30 Days
In Safe Attachment policies, as part of Phase 1 changes for ‘Replace’ action retirement (MC424901 August '22), the behavior of the ‘Block’ action was applied to the policies configured with ‘Replace’ action.
As part of Phase 2 of the ‘Replace’ action retirement work, the ‘Replace’ action selection will be removed from the Safe Attachment policies (Microsoft 365 Defender portal and cmdlets). As part of this change, any policies still configured with the ‘Replace’ action will be automatically changed to the ‘Block’ action.
When this will happen:
This change will start rolling out from mid-April 2023 and worldwide deployment will be complete by mid-May 2023. For Government clouds, the deployment will start in mid-June 2023 and will be complete by late-June 2023.
How this will affect your organization:
Once this change is rolled out, the ‘Replace’ action will no longer be available in Safe Attachment policies.
What you need to do to prepare:
No action is needed. Any Safe Attachments policies with the ‘Replace’ action will be updated to the ‘Block’ action.
Please review to learn more:
MC567498 — Outlook on the Web supported browser updates.
>60 Days
This initial communication is to notify customers that starting in Fall 2023 (September 2023), users using unsupported browsers will be redirected to the light version of Outlook on the web. This will align with the experience with other Microsoft 365 web applications (MC518729 February '23).
When this will happen:
We'll be gradually rolling this out to Targeted Release customers in early Fall (September), and the roll out will be completed for Standard release by the end of Fall 2023 (November 2023).
How this will affect your organization:
Once this change rolls out, users in your organization using legacy browsers will be redirected to the light version of Outlook on the web, which only has basic email functions (Learn more about the light version of Outlook).
What you need to do to prepare:
Please check the supported browsers versions and upgrade your organization users' browsers to make sure they can utilize the full set of features from Outlook on the web.
MC553274 — Microsoft Defender for Office 365 empowers end users to report suspicious messages from shared/delegate mailboxes
<30 Days
Microsoft 365 Roadmap ID 115507
Updated May 11, 2023: We have updated the content below with additional information. Thank you for your patience.
Soon, end-users will be able to report messages from shared mailboxes and delegate mailboxes using the built-in Report button in Outlook on the web.
To refresh your memory, these screenshots show the Report buttons in Outlook on the web if you have the simplified ribbon turned on:
Information to keep in mind:
- If the reporting feature is turned off in the Microsoft 365 Defender portal > user reported settings page or if you're using a third-party add-in, you won't be affected by this change.
- Other Outlook clients for Mac, Windows, and iOS and Android will remain unaffected by this change.
- The Microsoft Report Message and Report Phishing add-ins don't have support for shared and delegate mailboxes in Outlook on the web or in other Outlook clients.
- You need to assign Send As or Send On Behalf permission when you set up shared mailboxes for users in your organization. Otherwise, the user will get an error in Outlook on the web when they try to report messages from a shared mailbox. Learn more.
- You need to assign Send As or Send On Behalf permission, along with Read and Manage permissions for delegate access in another user's mailbox. Otherwise, delegates will get an error in Outlook on the web when they try to report messages from the mailbox. Learn more.
- You need to educate users to assign Send As or Send On Behalf permissions, along with Read and Manage permissions when they delegate access to their mailbox. Otherwise, delegates will get an error in Outlook on the web when they try to report messages from the mailbox. Learn more how to educate end users.
When this will happen:
This change will start rolling out in mid-May and should be completed by the early June.
How this will affect your organization:
If message reporting using the built-in button in Outlook is turned on at the user reported settings page, end-users will be able to report messages as Phish, Junk or Not junk from shared mailboxes, delegate mailboxes.
What you need to do to prepare:
No changes are required as your current settings in the user reported settings page will not be changed.
If you have any feedback, please provide it from this Message center post using the text box after you do thumbs up or thumbs down as it will directly reach the responsible team.
MC535260 — (Updated) Microsoft Defender for Office allows submission of up to 100 emails
<30 Days
Microsoft 365 Roadmap ID 115509
Updated May 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
Applicable to Tenants with Exchange Online Protection, Microsoft Defender for Plan 1 or Plan 2 or Microsoft 365 Defender plan.
Coming soon, Microsoft Defender for Office 365 will allow you to submit up to 100 emails at once from quarantine, threat explorer (or real-time detections tool) and User reported page to Microsoft for analysis.
When this will happen:
This change will start rolling out early May (previously late April) and will be completed by early June (previously mid-May).
How this will affect your organization:
This will allow you to make fewer manual submissions while increasing the number of emails you can submit at once.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC383901 — (Updated) Microsoft Defender for Office 365: Hourly option for notifications
<30 Days
Microsoft 365 Roadmap ID 93304
Updated May 9, 2023: We have updated the message to ensure visibility. Thank you for your patience.
We are adding a new hourly option to end user quarantine notifications, which will allow users to rely on receiving prompt notifications about quarantined items when appropriate. With this feature, users will be updated frequently once new items land in their quarantine folder.
When this will happen:
Standard: will begin rolling out in late November 2022 (previously early October 2022) and be completed by late June 2023 (previously late February 2023).
Government: will begin rolling out in early June 2023 (previously early July 2023) and be completed by late June 2023 (previously late July 2023).
How this will affect your organization:
Using the quarantine policy, Admins will be able to configure an hourly notification frequency for users in their organization.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
MC383875 — (Updated) Microsoft Defender for Office 365: updates to quarantine folder storage
30-60 Days
Microsoft 365 Roadmap ID 93302
Updated June 1, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Defender for Office 365 is making some changes to quarantine folder storage. The experience for users will remain the same and users can leverage the delete action to maintain the storage folder for their quarantined messages.
When this will happen:
Standard: will begin rolling out in mid-June and be completed by mid-November (previously mid-September). - Complete
Government: will begin rolling out in mid-January 2023 (previously mid-November 2022) and be completed by late July 2023 (previously late May).
How this will affect your organization:
Non delivery report (NDR):
In the case that a user’s quarantine storage is full, new incoming messages routed to quarantine will be rejected and an NDR will be generated for those messages.
In the case of Zero hour Auto Purge, where malicious items need to be zapped from inbox to quarantine but there is no space, these messages will be instead, added to the junk mail folder.
Note: When there is a False positive Zero hour Auto Purge, messages wrongly moved to the Junk mail folder can be added back to their original location.
New hard delete experience:
Previously, when messages were deleted by users from quarantine, those deleted messages could still be retrievable within a 30-day period after deletion was made. To help users better manage their storage, we will be introducing a hard delete experience whereby once the messages are hard deleted, they can’t be recovered.
Note: End users will only be able to delete quarantine messages that their Administrators has given them access to through the quarantine policy.
What you need to do to prepare:
The goal for this communication is mostly for informational awareness. You may consider updating your training and documentation as appropriate.
Microsoft 365
MC560724 — Text Predictions for OneNote on Windows
30-60 Days
Microsoft 365 Roadmap ID 124909
When this update rolls out, users will see text predictions when writing documents in English in OneNote on Windows. When they see the suggested text, users can accept with the tab or right arrow key or simply keep typing to ignore.
When this will happen:
We will begin rolling out in late June 2023 and expect to complete rollout by late July 2023.
How this will affect your organization:
Text predictions are ON by default and users can disable them as needed. To disable in OneNote on Windows, go to File -> Option -> Advanced -> Editing and switch off Show text predictions while typing.
Disabling this feature in OneNote will not affect other Microsoft apps, such as Word or Outlook.
What you need to do to prepare:
Text predictions is considered a Microsoft 365 connected experience. This feature can be managed through admin policy.
You may want to notify your users about this new capability and update your training and documentation as appropriate.
For more information, please visit this page.
MC560720 — Ink Color Picker for Microsoft Whiteboard
30-60 Days
Microsoft 365 Roadmap ID 124899
Users will soon be able to enjoy a wide range of colors for inking using the latest color picker feature. In addition to color picker, a slider will also be provided to change opacity level of pens. This functionality will be rolled out automatically to Whiteboard for the web, Microsoft Teams, Windows App & Surface Hubs/MTR experiences as well as Annotations in Teams meetings.
When this will happen:
Rollout will begin in early June 2023 and is expected to be complete by late June 2023.
How this will affect your organization:
Users can add new colors to the palette and enjoy more color options for inking in Whiteboard. In addition to the color picker feature, we have also added a slider to change opacity level of pens. Recent colors used will also be available on the color palette and the color picker feature, to further enhance user experience with inking in Whiteboard.
What you need to do to prepare:
There is no action required at this time. You may want to notify your users of this update.
MC559929 — App User Interface update for Microsoft Whiteboard
<30 Days
Microsoft 365 Roadmap ID 124900
This update will visually refresh the Microsoft Whiteboard app user interface for laptops, desktops and tablets while simultaneously making whiteboarding tools upfront and toolbar at the bottom of the screen to improve engagement, discoverability & ease of whiteboarding.
When this will happen:
This functionality will be rolled out in early-June 2023 and is expected to be completed by late June 2023.
How this will affect your organization:
The Whiteboard chrome will undergo a visual refresh making key content creation tools such as notes, reactions, comments, text & shapes surface more prominently, empowering users to easily discover and engage with the same to expedite content creation. Additionally, the toolbar will be repositioned to the bottom of the screen, improving usability & affording more space to view and use the whiteboard especially on smaller screen devices (such as tablets).
This change will hopefully stimulate flexible visual collaboration through Whiteboard among users, allowing them to better express their ideas, whenever & wherever inspiration strikes them next.
What you need to do to prepare:
The feature will be rolled out automatically on Whiteboard web, Teams and the Windows app to all customers.
MC557110 — New details on IE11 desktop application next steps
Rolled Out
Internet Explorer 11 (IE11) visual references, such as the IE11 icons on the Start Menu and taskbar, will no longer be removed by Windows update as previously communicated. Based on customer feedback, organizations will maintain control over determining the timing to remove IE11 UI elements from their devices, if they have not already done so.
Note: IT teams can remove IE11 visual references on Windows 10 devices by using the Disable IE policy.
Additionally, over the coming months a small subset of exceptional scenarios where IE11 is still accessible will be redirected to Edge, ensuring users access a supported and more secure Microsoft browser. Details will be available in the Windows and Microsoft Edge release notes.
As a reminder, IE11 has been out of support since June 15, 2022, and was permanently disabled on February 14, 2023. These changes are intended to provide a better user experience and smoothly transition users from IE11 to Microsoft Edge to ensure a faster and more secure browsing experience.
When this will happen:
- IE11 visuals can be removed at organizations' discretion by using the Disable IE policy
- Changes will be made over the next coming months to redirect a small subset of exceptional scenarios where IE11 is still accessible to Edge.
How this will affect your organization:
- Organizations that have already transitioned from IE11 to Microsoft Edge with IE mode or that have already used the Disable IE policy to remove IE11 visual references will not be impacted by this update. Note: To remove the IE visual references such as on the taskbar or Start Menu, you will need to use the Disable IE policy.
What you need to do to prepare:
If you have not done so already, finish your transition to Microsoft Edge with IE mode to avoid any business disruption related to IE retirement. If you would like to remove all IE11 visuals/entry points, set the Disable IE policy. Details about IE11 changes made can be found in release notes.
If you need help transitioning from IE11 to Microsoft Edge with IE mode, please reach out to Microsoft as soon as possible through one of the following pathways:
- Open a support ticket for help with technical issues
- Request help at no charge from the App Assure team for app compatibility issues
The majority of customers have already moved to Microsoft Edge and are experiencing the performance and productivity benefits of a faster, more secure, and more modern web experience than Internet Explorer (learn more). Microsoft Edge is the only browser with built-in compatibility for legacy IE-based sites and apps with IE mode.
Additional Information
- Read the FAQ to help answer your questions.
We always value feedback from our customers.
MC556155 — Microsoft To Do: Apple Watch app for To Do iOS
<30 Days
Microsoft 365 Roadmap ID 98122
Microsoft To Do users will soon be able to add tasks and view their To Do lists from the Apple Watch app.
When this will happen:
Standard Release: We will begin rolling out in early June 2023 and expect to complete rollout by late June 2023.
How this will affect your organization:
Users with the latest version of the To Do app installed on their Apple watch will see the To Do app logo on their Apple watch. Users can customize their views from the "Watch app settings" page in the main To Do app settings.
What you need to do to prepare:
There is nothing you need to do to prepare. You may want to let your users know about the new functionality.
MC552633 — Announcing the Semantic Index for Copilot
TBD
Today we announced Semantic Index for Copilot – a new capability in Microsoft 365 E3 and E5. A core part of the Copilot System, the Semantic Index is a map of your individual and company data. It is a foundational capability for Microsoft 365 Copilot, and will enhance enterprise search results for Microsoft 365 E3 and E5 – whether customers are using Copilot or not. Semantic Index for Copilot will start rolling out later this calendar year for Microsoft 365 E3 and E5 customers.
How this will affect your organization:
There is no impact to your organization at this time. We will provide advanced notice about the timing as well as additional information on admin controls and settings that can be used to manage this new capability.
What you need to do to prepare:
There is nothing you need to do at this time. As soon as the additional roll out dates are ready to be announced, we will inform you through the Message Center in the Microsoft 365 admin center. You can also follow these features on Microsoft 365 public roadmap website.
Learn more in the blog posts here and here.
MC551020 — Conditional Access and OneNote iPad for features that use Webview
Rolled Out
Note: If your organization does not use the OneNote iPad app you can safely disregard this message.
The OneNote iPad app leverages a technology called WebView for certain features, such as Meeting Details. However, when Azure Active Directory (Azure AD) Conditional Access, as part of Microsoft Entra, is applied to the user of this device, WebView features are not supported, and conditional access checks will fail. This means that, the feature will be inactive and not available for use.
If the Meeting Details feature is unavailable, it is very likely Conditional Access policies have been applied for this user. This is a known limitation related to the enforcement of Conditional Access, and as such, the feature will remain unavailable while it is active.
When this will happen:
This is happening in all builds of OneNote iPad.
How this will affect your organization:
When Azure Active Directory (Azure AD) Conditional Access, as part of Microsoft Entra, is applied to the user of this device, WebView features are not supported, and conditional access checks will fail. This means that, the feature will be inactive and not available for use.
What you can do:
You may consider updating your training and documentation as appropriate.
We apologize for the inconvenience this may cause. If you have any further questions or need additional assistance, please feel free to contact our support team for more information.
MC538725 — (Updated) Microsoft Edge: v.113 - Switch from Microsoft Autoupdate to EdgeUpdater for macOS
Rolled Out
Updated May 9, 2023: We have updated the message for clarification. Thank you for your patience.
Starting with Edge 113, Microsoft Edge for macOS will begin using a new updater called EdgeUpdater.
Note: This change only affects Microsoft Edge on macOS.
Microsoft Edge on macOS
- Timing: Beginning with Microsoft Edge version 113 (scheduled for the week of May 4, 2023)
- Action: If you use update preferences for Microsoft Autoupdate to prevent browser updates, you will need to transition to the new EdgeUpdater UpdateDefault policy before Edge 113 to prevent future automatic updates.
How this will affect your organization:
If you do not transition before the new EdgeUpdater is deployed with Edge 113 (scheduled for the week of May 4, 2023), the new updater will default to updating Microsoft Edge automatically on your macOS devices.
What you need to do to prepare:
To maintain your desired update preferences, you will need to transition to the new EdgeUpdater UpdateDefault policy and set your preferences prior to Edge 113.
Additional information:
We always value feedback and questions from our customers. Please feel free to submit either feedback or questions via Message Center.
MC519243 — (Updated) Message Vertical to be released to special clouds (GCC and GCC-H) in Office.com
<30 Days
Microsoft 365 Roadmap ID 117389
Updated May 25, 2023: We have updated the rollout timeline below. Thank you for your patience.
Office.com users can now easily get messages from both Outlook and Teams that they previously shared with their colleagues. All they need to do is search for the particular communication and navigate to the messages tab. This feature which is currently available worldwide will now be available to GCC and GCC-H customers.
When this will happen:
Standard Release: We will begin rolling out this feature mid-April (previously late March) and expect to complete in mid-June (previously mid-May).
How this will affect your organization:
This feature will be shipped turned on by default and for organizations that don't use Teams or/and Outlook, there is an option to disable this from the Microsoft Admin Center. If your organization uses both Team or/and Outlook, administrators do not need to do anything.
What you need to do to prepare:
Administrators need to inform their users about this new feature so that they can learn about it and use it to easily get Outlook and Teams messages when they are using Office.com without having to switch to the apps.
MC516903 — (Updated) Microsoft 365 admin center: New Visio Usage Reports
<30 Days
Microsoft 365 Roadmap ID 88834
Updated May 9, 2023: We have updated the rollout timeline below. Thank you for your patience.
A new product usage report will be made available within Microsoft 365 admin center usage reports to help Admins understand how Microsoft Visio is used within their organization by daily active users and active users by platform.
The report can be viewed for trends over the last 7/30/90/180 days, includes a per-user view, and contains the user’s last active date and license information.
When this will happen:
Standard release. We will begin rolling out in late May (previously mid-March) and expect rollout to be complete by late June (previously late April).
How this will affect your organization:
Admins with the correct permissions will soon have access to new usage activity reports within Microsoft admin center products for Microsoft Visio.
What you need to do to prepare:
To access the new reports, go to Reports -> Usage -> Visio.
For more information regarding these reports, please review the following documentation.
MC514084 — (Updated) Microsoft 365 admin center: Windows 365 cloud PC advanced deployment guide
Rolled Out
Microsoft 365 Roadmap ID 102406
Updated March 30, 2023: We have updated the rollout timing below. Thank you for your patience.
The Advanced deployment guides & assistance page in the Microsoft 365 admin center and the setup.microsoft.com website will have a new guide to help admins plan, deploy, and scale Windows 365 Enterprise in their organization. Windows 365 is a cloud-based service that provisions and hosts Cloud PCs as virtual machines for users. The guide includes a checklist with Cloud PC configuration tasks, best practices, tools, and recommendations based on a tenant's configuration.
When this will happen:
This guide will be available to Targeted Release in April 2023 and Standard Release in May 2023 (previously March). It can be found on the Advanced deployment guides & assistance page, and shortly after, on setup.microsoft.com.
How this will affect your organization:
Admins will use the Windows 365 Cloud PC advanced deployment guide for recommendations on how to make key decisions and identify prerequisites and tasks needed to deploy Cloud PCs in accordance with their org’s requirements. The guide is organized by IT area (Azure, networking, identity, management, security, and applications) to help admins work with multiple groups and staff members. Admins can track the status of each task within the guide and share tasks with others via email.
What you need to do to prepare:
You don’t need to do anything to prepare for this change.
MC477852 — (Updated) Modern Commenting Experience Coming to Whiteboard
<30 Days
Microsoft 365 Roadmap ID 98083
Updated May 30, 2023: We have updated the rollout timeline below. Thank you for your patience.
With comments you can share your thoughts, celebrate with your teammates, or just have a conversation in Microsoft Whiteboard.
When this will happen:
Rollout will begin in late April (previously late January) and is expected to be complete by mid-June (previously late May).
How this will affect your organization:
Your users would have the following experiences:
- The ability to add comments on a whiteboard to aid in discussion with board participants.
- This will include a comments pane to see all comments on a given whiteboard.
Note: The commenting experience initially will not be supported for the Android and IOS apps. We eventually plan to bring this experience to mobile as well.
What you need to do to prepare:
There is no action required at this time. Continue checking the Microsoft Whiteboard Blog and support pages on details about upcoming features and how best to use them.
Microsoft 365 IP and URL Endpoint Updates |
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.