- Home
- Public Sector
- Public Sector Blog
- October 2023 - Microsoft 365 US Public Sector Roadmap Newsletter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Newsworthy Highlights |
Announcing general availability of Universal Print in GCC/GCC High!
We are excited to announce that we are bringing Universal Print to government organizations with the general availability of Universal Print in GCC/GCC High. Universal Print in GCC/GCC High aims to offer full feature parity with what exists in the commercial cloud today, while remaining compliant with certifications that are required for U.S. government organizations.
Microsoft 365 Government Community Call
Join Jay Leask and other members of the Government Community live on LinkedIn!
Where to Start with Microsoft Teams Apps in Gov Clouds
Customers in our Office 365 government clouds, GCC, GCCH, and DoD, are continuing to evolve how they do business in the hybrid workplace. As Microsoft Teams is the primary tool for communication and collaboration, customers are looking to improve productivity by integrating their business processes directly into Microsoft Teams via third-party party (3P) applications or line-of-business (LOB)/homegrown application integrations.
Microsoft 365 Government Adoption Resources
Empowering US public sector organizations to transition to Microsoft 365
What’s New in Microsoft Teams | September 2023
These features currently available to Microsoft’s commercial customers in multi-tenant cloud environments are now rolling out to customers in the US Government Community Cloud (GCC), US Government Community Cloud High (GCC-High), and/or the United States Department of Defense (DoD).
Release News |
Teams
Deploy new Microsoft Teams with Microsoft 365 Apps
Workflows replacing Connectors within Microsoft Teams channels menu - GCC
Monitoring Notifications for meeting quality using Real-time telemetry in General Availability – GCC...
Purview
New features in Insider Risk Management
Viva Insights
Diversity, equity and inclusion report is now available in VIVA insights - GCC
References and Information Resources |
Microsoft 365 Public Roadmap
This link is filtered to show GCC, GCC High and DOD specific items. For more general information uncheck these boxes under “Cloud Instance”.
Stay on top of Microsoft 365 changes
Here are a few ways that you can stay on top of the Office 365 updates in your organization.
Microsoft Tech Community for Public Sector
Your community for discussion surrounding the public sector, local and state governments.
Microsoft 365 for US Government Service Descriptions
· Office 365 Platform (GCC, GCCH, DoD)
· Office 365 U.S. Government GCC High endpoints
· Office 365 U.S. Government DoD endpoints
· Microsoft Purview (GCC, GCCH, DoD)
· Enterprise Mobility & Security (GCC, GCCH, DoD)
· Microsoft Defender for Endpoint (GCC, GCCH, DoD)
· Microsoft Defender for Cloud Apps Security (GCC, GCCH, DoD)
· Microsoft Defender for Identity Security (GCC, GCCH, DoD)
· Azure Information Protection Premium
· Exchange Online (GCC, GCCH, DoD)
· Office 365 Government (GCC, GCCH, DoD)
· Power Automate US Government (GCC, GCCH, DoD)
· Outlook Mobile (GCC, GCCH, DoD)
Be a Learn-it-All |
|
Public Sector Center of Expertise We bring together thought leadership and research relating to digital transformation and innovation in the public sector. We highlight the stories of public servants around the globe, while fostering a community of decision makers. Join us as we discover and share the learnings and achievements of public sector communities. |

|
|
Microsoft Teams for US Government Adoption Guide
|

|
|
|
|
Message Center Highlights |
SharePoint Online
MC678064 — UseRemoteAPIs functionality change
<30 Days
Today, we are announcing the removal of consideration for the UseRemoteAPIs permission within SharePoint Online. Meaning that while the setting remains in the UX for a short time, it will no longer be used as part of the authorization flow for API calls made to CSOM and classic REST APIs. Please see the linked blog post for additional details.
When this will happen:
We will begin rolling out in mid-October 2023 and expect to complete by late October 2023.
How this affects your organization:
Within SharePoint you can build permission levels through combining permissions, including the ability to modify existing service permissions. Within this system, the permission listed in the UX as “Use Remote Interfaces - Use SOAP, Web DAV, the Client Object Model or SharePoint Designer interfaces to access the Web site” was originally intended to prevent anonymous users in public SharePoint internet sites from accessing the APIs.
As the service evolved, this original meaning has been lost. Today the setting provides no additional protection.
We expect no disruption to users or the service during the rollout of this change.
What you can do to prepare:
This announcement is for your information and there is nothing to do associated with this change.
MC674728 — SharePoint admin control for App registration / update
Rolled Out
This is an enhancement to the security measures for administrative governance that modifies the default procedures for SharePoint app registration via AppRegNew.aspx page and permission updates via AppInv.aspx page. Following the implementation of this change, site collection admin will be unable to register app or update app permissions through above pages unless authorized explicitly by the SharePoint tenant admin.
Upon attempting to register an application on AppRegnew.aspx page, a notification will be displayed stating "Your SharePoint tenant admin doesn't allow site collection admins to create an Azure Access Control (ACS) principal. Please contact your SharePoint tenant administrator."
Similarly, upon attempting to update app permissions on AppInv.aspx page, a notification will be displayed stating "Your SharePoint tenant admin doesn't allow site collection admins to update app permissions. Please contact your SharePoint tenant administrator."
Kindly note that app registration and permission update via Microsoft Azure portal are not impacted by this change.
When this will happen:
The rollout process has been launched in late August and is expected to conclude in mid-September.
Note: We acknowledge that the previous MC Post (MC660075) was not published to the Government Cloud organizations as intended. We understand that this has caused inconvenience, and we sincerely apologize for that.
How this will affect your organization:
With this update site owners will not be able to register/update apps unless the tenant admin explicitly allows it.
To modify the default behavior, the tenant administrator must execute the following shell command to explicitly establish the flag as TRUE, thereby superseding the default value of FALSE. The service principal can only be created or updated by the tenant administrator by default. However, when the flag is set to TRUE, both the SharePoint tenant admin and site collection admin will be able to create or update the service principal through SharePoint.
The shell command is: Set-SPOTenant -SiteOwnerManageLegacyServicePrincipalEnabled $true
Note: The property ‘SiteOwnerManageLegacyServicePrincipalEnabled’ becomes visible in tenant settings after SharePoint Online Management shell is updated to 16.0.23710.12000 or a later version. But before this rollout, the value will always be TRUE even explicitly set to FALSE. It will only automatically be switched to FALSE as the default value after the rollout is launched.
What you need to do to prepare:
No proactive measures are required to prepare for this change. Nevertheless, it is advisable to inform your users of this modification and update any relevant documentation as necessary.
MC666623 — (Updated) New Stream (on SharePoint) web part release
<30 Days
Microsoft 365 Roadmap ID 124800
Updated September 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
This is an important message for customers who publish videos to SharePoint Pages and news posts. As noted in Message Center post MC561187, the Stream (Classic) webpart in SharePoint will be retired on August 15, 2023.
The Stream (on SharePoint) web part will support configuration of a single video and multiple videos for videos stored in OneDrive or SharePoint.
When this will happen:
The Stream (on SharePoint) webpart will begin its general availability roll out in mid-August 2023, and we expect the rollout to complete by mid-October 2023 (previously mid-September).
How this will affect your organization:
Your organization will not be able to use Stream (Classic) webpart after August 15, 2023.
All existing SharePoint pages and news posts that were built using Stream (Classic) webpart will continue to function as usual. Please follow this documentation for detailed information for videos post migration: https://learn.microsoft.com/en-us/stream/streamnew/migration-details
Before availability of the new Stream (on SharePoint) web part, you can currently use video eligible webparts such as “File and Media”, “Hero”, “Highlighted content” and “List” webparts to publish videos/playlists from Stream (on SharePoint) to SharePoint Pages.
Post availability of this web part, we would recommend you use it for publishing single video and multiple videos from a folder and continue using “List” web part for publishing a playlist to SharePoint Pages.
What you need to do to prepare:
Please follow this documentation for detailed timelines and video publishing guidance on the new Stream.
MC653734 — (Updated) SharePoint: User experience and Image Coherence in SharePoint Online (SPO)
>60 Days
Updated September 27, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are currently working to improve user experience by providing a coherent profile photo experience across Microsoft 365. This primarily impacts those users of SharePoint online (SPO) who neither have an exchange license nor are using Delve for uploading images. This may also impact a small number of SPO admin who upload the user profile image on behalf of the end users.
When this will happen:
We will begin rolling out this change in early October 2023 (previously mid-September) and expect to complete by late March 2024.
How this affects your organization:
Currently, for users who do not have an Exchange License and have uploaded multiple different images across different apps in Microsoft 365, it is likely that SPO displays images uploaded locally in SPO which will be different from User Profile images in other Microsoft 365 apps.
To ensure that the same image is available across all Microsoft 365 experiences, going forward, SPO will display images sourced via MS Graph endpoint from Microsoft People System (MPS). This implies that the image uploaded via other apps in Microsoft 365 will take precedence and get displayed in SPO instead of the locally available image in SharePoint. There is no action required from users at this point.
For users with Exchange licenses there is no functional change.
To ensure profile coherence, we will disable local uploads from SPO to mysite host and instead enable centralized uploads to Microsoft People System (MPS).
What you can do to prepare:
For all users identified above: The profile image will no longer be edited/uploaded through SPO “Edit Profile UI” experience or through “Person Immersive” UI experiences. Instead, all such users would be requested to use the “Universal Me” control available on top right corner of the SharePoint Home page for uploading images. Alternatively, they can also use Delve to upload profile images.
For SPO admins: Admins who upload the user profile image on behalf of the end users will no longer be able to upload images via SPO Admin Centre. Instead, all SPO admins will be requested to upload user profile images via MAC Admin Centre or AAD admin center.
We are providing an early heads-up to ensure our customers have sufficient time to adapt to upcoming changes as we will not be able to grant any extension for this change.
MC564196 — (Updated) Microsoft Stream: Playlist View in SharePoint List Webpart
Rolled Out
Microsoft 365 Roadmap ID 124808
Updated September 6, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can soon select a playlist to be displayed in the list webpart in the full-blown playlist view along with video playback.
When this will happen:
Standard Release: We will begin rolling out in early June 2023 and expect to complete rollout by mid-September 2023 (previously late August).
How this will affect your organization:
- Users will be able to select a playlist from the list picker while configuring the list webpart.
- Users will be able to see the full-blown playlist view as the default view for playlists.
What you need to do to prepare:
There is no action required at this time, this change will be enabled automatically.
MC561187 — (Updated) Stream Classic webpart retirement and new Stream (on SharePoint) webpart availability
<30 Days
This change is associated with Microsoft 365 Roadmap: 124800
Updated September 19, 2023: We have updated the timeline below. Thank you for your patience.
This is an important message for customers who use the Stream (Classic) webpart to add videos to SharePoint Pages and news posts. Microsoft will retire the Stream (Classic) webpart on Aug 15, 2023 and it will no longer be available for use after this date. The Stream (Classic) webpart will be replaced by the new Stream (on SharePoint) webpart.
When this will happen:
The Stream (Classic) webpart will be retired on August 15, 2023.
The Stream (on SharePoint) webpart will begin its general availability roll out in mid-August (previously mid-June), and we expect the rollout to complete by mid-October 2023 (previously mid-September).
How this will affect your organization:
- Your organization will not be able to use Stream (Classic) webpart after August 15, 2023.
- All SharePoint pages and news posts that were built using Stream (Classic) webpart with single video as a source will continue to play your videos until February 2025.
- After your organization migrates video content to Stream (on SharePoint), single videos configured on the Stream Classic webpart continues to play inline while channels configured on the webpart is replaced by a button that redirects to the migrated folder location.
- If you would like to publish videos from Stream (on SharePoint) on SharePoint Pages, you can currently use video eligible webparts such as “File and Media”, “Hero”, “Highlighted content” and “List” webparts. Additionally, you will be able to use the new Stream (on SharePoint) webpart when it becomes available.
- For re-publishing Stream Classic webpart videos post migration, users will have to manually do so using the share URL via above mentioned webparts.
What you can do to prepare:
Please follow this documentation for detailed timelines and video publishing guidance on the new Stream: Stream (Classic) web part transition plan & new Stream Webpart
MC531214 — (Updated) SharePoint: Improving the Page Authoring Experience
Rolled Out
Microsoft 365 Roadmap ID 117376 and 117377
Updated September 21, 2023: We're excited to have launched several new improvements to the page authoring experience over the last few months. In a previous post, we mentioned we would be moving the "add section" feature to be inline on canvas. Based on the feedback we received, we are currently reconsidering the best way to design this user experience and will have a new update for you soon. For now, you can expect to still find the "add section" in the left toolbar.
We are releasing new improvements to the Page authoring experience in SharePoint. These new improvements should help reduce clutter, increase productivity, and add more value for users when editing a page.
When this will happen:
We will begin rolling out in late-March and expect to complete rollout by late August 2023 (previously late June).
How this will affect your organization:
The new updates will include:
- Surfacing the layout options in the web part toolbars, including in Quick Links, Events, People, Hero, News, and Title Region
- Moving the “add section” action to be inline on canvas and visible on hover
- Introducing a consolidated and enhanced Image web part toolbar
- Adding new text overlay capabilities in the Image web part, such as the ability to change positions, text size and styling, text box color and opacity, and image overlay color and transparency.
What you need to do to prepare:
There is nothing you need to do at this time.
MC617059 — (Updated) Introducing New Feature in Project Online
Rolled Out
Updated September 12, 2023: We have updated the rollout timeline below. Thank you for your patience.
In 2019, we introduced Project for the Web, a versatile project service designed to streamline project management and collaboration. Since then, we have been continuously improving and expanding the capabilities of this product. We are excited to share that we have recently added several new features that will further enhance your project management experience. To encourage users to explore Project for the Web, we have added a few promotional elements within Project Online, enabling users to access the service using their existing project licenses.
When this will happen:
Standard Release: We will begin rolling out late July (previously early July) and expect to complete by late September (previously late August).
How this will affect your organization:
End users of your organization using project online will see banners promoting project for the web. No other functionality will be affected.
We understand that some SharePoint site admins may prefer not to display promotional elements related to Project for the Web to their users. To address this, we have provided an option for admins to disable these elements. Simply uncheck the "Turn on exploration" setting located by clicking the settings icon (gear icon) and then choosing PWA settings > Additional Server settings > Project for the web Discovery on or before August 24th. This will ensure that your users will not be prompted to try Project for the Web. You may turn this On/Off at any time you prefer.
Please be aware that if the Project for the Web service is already disabled for your tenant, this new feature will have no impact on your existing setup. You can continue using Project Online as you have been doing without any interruptions.
What you need to do to prepare:
You need not do anything for this change. We have provided an option for admins to disable these elements. Simply uncheck the "Turn on exploration" setting located in Settings > Additional Server settings > Project for the web Discovery. This will ensure that your users will not be prompted to try Project for the Web.
Power Platform
MC678807 — Change required for your user provisioning process
Rolled Out
We applied a change to user provisioning and user record matching from Microsoft Entra to prevent the reuse of User Principal Names (UPNs). Previously, users with recycled UPNs had access to business records of which they never had access to or ownership.
What action do I need to take?
If you currently use UPN match to import data into Dynamics 365, you must make the following changes to your process:
- Create the user records in Microsoft Entra before starting your data import process.
- Sync the user(s) from Microsoft Entra into the environment(s) where you intend to perform data import. You can perform this sync using any of the following methods:LISTBREAK
- Adding a security group to the environment
- Adding the user manually in the environment
- Using PowerShell scripts to add the user to the environment
- Leveraging Force sync in Power Automate flows
- Once the system syncs the user(s) into the environment (see verification instructions below), run your data import workflows.
To verify that the user has been added to your environment:
- From the Microsoft Power Platform admin center, select the environment to which you added users via one of the multiple methods listed above.
- Select Settings > Users + permissions > Users.
This will display the list of users that have already been added to the environment. This list includes users with enabled and disabled status.
MC675134 — Power Platform - Announcing General Availability of Access Check to view all users who have access to a record
Rolled Out
We are preparing an update that will allow record owners to view all users who have access to their record(s). This update is expected to be released by the end of September.
What actions do I need to take to prepare?
This feature will be enabled by default in your environment after the release of the update by the following two settings that will be introduced. You can reset these settings to better fit your business needs:
- IsAccessCheckerAllUsersEnabled: This allows the admin to see who has access to the record.
- IsAccessCheckerNonAdminAllUsersEnabled: This allows the admin, owner of the record, and users who have access to the record to see who has access.
For additional information, please check the following documentation:
- Use access checker to view all users who have access to your record | Microsoft Learn
- Check your user access and permissions – Power Apps | Microsoft Learn
- How to change default environment database settings - Power Platform | Microsoft Learn
MC674691 — Power Platform admin center – Allow list new PPAC API endpoint by 9/15
Rolled Out
A new API endpoint is now being called from the Power Platform Admin Center website.
What action do I need to take?
Please allow list the following endpoints based on your hosted region in your network firewall settings:
- Public: https://api.admin.powerplatform.microsoft.com
- Gov: https://api.gcc.admin.powerplatform.microsoft.us
- High: https://api.high.admin.powerplatform.microsoft.us
- DoD: https://api.admin.appsplatform.us
- Mooncake: https://api.ppac.partner.microsoftonline.cn
If you have already allowlisted these endpoints, no further action is needed.
Why is this action needed?
If you do not allow list the above endpoints, you may encounter errors or a functionality loss when using the Power Platform admin center. We recommend performing this update as soon as possible.
MC673981 — (Updated) Discontinuing platform support - Power BI app support for Windows devices.
>60 Days
Updated September 12, 2023: We have updated the content below with additional information.
Power BI Windows app will reach retirement on December 31, 2023. There will be no support for the Power BI Windows app after this date. Current users have access to their accounts via Power BI for the Web and can switch to this option any time prior to retirement.
When this will happen:
December 31, 2023
How this will affect your organization:
As of December 31, 2023, the Power BI Windows app will no longer be available to download from the Microsoft apps store, and no product updates for that app will be released after that date.
We recommend current users to use the Power BI Online service to view their Power BI content.
This change only applies to the Power BI Windows app; It does not affect the Power BI Desktop app.
What you can do to prepare:
We recommend users to use Power BI Online service to view their Power BI content on those devices.
We will continue to innovate and create new features that empower organizations to uncover more powerful insights and translate them into impact.
What's new and planned for Power BI
MC673725 — Power Automate – End of support for the List Flows as Admin action with Power Automate Management connector - reminder 1
Rolled Out
On Thursday, June 15, 2023, the List Flows as Admin action reached end of support and was replaced with the List Flows as Admin (V2) action.
Due to the ongoing usage levels and the rollout of CreatedBy support to GCC, we have determined that more time is needed before enforcing the deprecation at runtime.
How does this affect me?
Enforcement is expected to begin in October. Enforcement will cause the calls to the backing API of List Flows as Admin to fail at runtime and impact the following:
- Older PowerShell cmdlet versions.
- Older Center of Excellence Starter Kit versions.
- Calls to the deprecated List flows as Admin action.
For additional details and support, please see the community forum post Transition to List Flows as Admin V2. The forum post will be monitored for questions.
What action do I need to take?
- Transition to using the List Flows as Admin (V2) action for your new and existing flows. Existing flows can be found with the PowerShell script in Transition to List Flows as Admin V2.
- If you have the COE Starter Kit installed, update COE Starter Kit to the latest release.
- If you use PowerShell, update the Microsoft.PowerApps.Administration.PowerShell module.
Microsoft Planner
MC677519 — Personal Plans in Planner
<30 Days
Microsoft 365 Roadmap ID 171611
Today in Planner, two types of plans are supported: group-based plans, which are shared through a Microsoft 365 group, and Lightweight plans, which are shared through a simple list of members stored in Planner (rosters). Planner now also supports a new type of plan called Personal plans. Personal plans are shared only with the creator, who is the sole member and owner of the plan. These plans can be shared with a Microsoft 365 group at any time but will not be accessible by anyone other than the creator until then.
To enable Personal plans, we are introducing a new type of container in the Planner service, which is called “user containers”. Personal plans are simply the plans attached to Planner user containers.
The basic functionality of Personal plans is:
- Personal plans can be created through Graph APIs. There is no current way to create them in the Planner UI.
- Once created, Personal plans appear in Planner alongside all other plans in Planner and can be interacted with via the UI the same way.
- All plan features are available for personal plans with the exception of comments on tasks, uploaded attachments, and links to OneNote/SP Site. To get access to these features, you must be in a plan linked to a Microsoft 365 Group.
- A Personal plan can be linked at any time to a group container. At that point all members of the group can access the plan and all functionality of Microsoft 365 Group plans are available.
- Once a plan has been linked to a Microsoft 365 group container, it cannot be moved back to a user container. It is possible to remove members from the group, but the plan is now tied to the lifecycle of the group.
Additional notes:
- There are no changes to Planner licensing or storage for Personal plans compared to existing Microsoft 365 group plans.
When this will happen:
Standard Release: We will begin rolling this feature out in mid-October 2023 and will complete by late October 2023.
How this will affect your organization:
When this feature is released, plans can be created outside of Microsoft 365 Groups groups. Personal plans are not subject to existing Microsoft 365 group controls.
What you need to do to prepare:
There is no action needed to prepare for the release of Personal plans.
MC669735 — (Updated) Rosters in Microsoft Planner Supporting Container Sensitivity Labels
30-60 Days
Microsoft 365 Roadmap ID 155837
Updated September 27, 2023: We have updated the rollout timeline below. Thank you for your patience.
Customers will soon be able to apply container labels to rosters in Microsoft Planner. This is enabled directly in Planner by using Microsoft Graph APIs. When this feature is rolled out, the roster sensitivity labels can be set to respect the policy settings. If the tenant admin has made container labels mandatory and has set a default label, then the default label will be used for roster creation through Microsoft Loop client.
- On the Loop client, if the default label is provided, it will be used as the roster's lable when creating the roster. The roster system will not allow the user to create an unlabeled roster or to un-label a previously labeled roster.
- On the Microsoft Graph API, if a request is made and the label is not included, the request is rejected as the default label is not applied by the service. Users will need to ensure that a default label is provided when labels are mandatory so that roster creation does not fail.
Note: The container sensitivity label applied to a roster applies only to the information in Microsoft Planner and does not protect or encrypt the information when it syncs with the Loop client.
When this will happen:
We will begin rolling out in late October 2023 (previously mid-September) and is expected to complete by late November 2023 (previously mid-October).
How this will affect your organization:
Rosters can be configured with container labels being mandatory. When container labels are set to mandatory for rosters, ensure a default label is available otherwise rosters cannot be created unless a label is set. On the Microsoft Graph API, if a request is made and the label is not included, the request is rejected. (Note: default label is not applied by our service).
What you need to do to prepare:
By setting a container label to mandatory for an existing roster, there may be an impact to third parties used in your organization. For third parties using the labels Graph API, attempts to create a label-less roster will fail if labels are mandatory as the default label will not be applied by our service. To ensure roster creation does not fail when labels are mandatory, it is the client responsibility (third party responsibility) to apply the default label by either updating the apps (if under admin control) or modifying the dependency on such apps or by making labels not mandatory.
MC664477 — (Updated) See your Recent Microsoft Planner plans and Microsoft To Do Lists on Microsoft 365 Homepage
30-60 Days
Microsoft 365 Roadmap ID 149272
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
Currently, you cannot see your recently accessed Planner plans or Microsoft To Do lists in your Microsoft 365 homepage. With this update, you will be able to see and access all your recent plans and lists alongside your Microsoft Project for the web projects, Word documents, PowerPoint decks, and more on office.com.
When this will happen:
- This update will begin rolling out in early October 2023 (previously September) and is expected to be completed by mid-November 2023 (previously early November).
How this will affect your organization:
With this update, your organization’s plans and lists will be visible from the office.com home page as opposed to solely from Planner and Microsoft To Do apps. This means you will be able to open your plans and lists directly from the Microsoft 365 homepage, just as you are able to open your Project projects, Word documents, Excel sheets, and all other Microsoft Office files.
What you need to do to prepare:
There is no action required to prepare for this change. Plans and lists for users in your tenant will begin to appear on the Microsoft 365 homepage as soon as the rollout reaches your tenant.
Microsoft Viva
MC676544 — Viva Connections "Top News" Card Updated to Include More News Source Options
<30 Days
Microsoft 365 Roadmap ID 173074
Improvements are coming to the Viva Connections Top News Card, which will be rebranded as the "News Card." These enhancements will introduce greater configurability and the ability to create multiple News Card instances, while the default configuration will remain consistent with the Top News Card.
When this will happen:
We will begin rolling out in mid-October 2023 and expect to complete rollout by late October 2023.
How this will affect your organization:
News Source Customization: You can now tailor the News card to display news from specific sources or a list of chosen sites within your organization. This is in addition to the default configuration, which features only boosted news as earlier. This improvement enables you to focus on news relevant to specific areas of your organization, ensuring that your end users stay well-informed.
Multiple News Card Instances: The updated News card allows you to create multiple instances with different settings, letting you curate news experiences for various purposes within your organization. For example, you can have one card named "Top News" with the default configuration, a second card with a custom name that specifically displays HR news from relevant intranet/SharePoint sites, and a third card for "Leadership News," etc.
What you need to do to prepare:
If you are an existing user of Top News card, it will continue to work as-is without any action required from your side. However, if you want to create multiple instances of the card with different news sources, you can do so with this update.
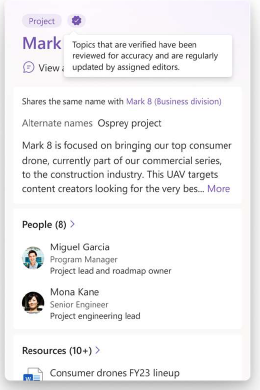
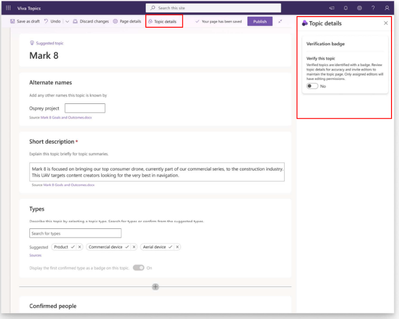
MC673980 — (Updated) Microsoft Viva: Verified Topics Badges
<30 Days
Microsoft 365 Roadmap ID 118239
Updated September 12, 2023: We have updated the rollout timeline below. Thank you for your patience.
With this update, editors can mark published topics as Verified in Microsoft Viva and add a specific group of SMEs as editors to the topic. Verification helps readers identify topics with added reliability. Topics that are Verified are identified by a special badge and indicate the content is reviewed for accuracy and are regularly updated by assigned editors. Assigned editors will be informed of being added to the topic via an email.
When this will happen:
Preview: Rollout has begun and is expected to be complete by early September 2023.
Standard Release: Rollout will begin early September 2023 and is expected to complete by late September 2023 (previously mid-September).
How this will affect your organization:
Users can add a Verified badge to a topic to indicate that it's been manually reviewed for accuracy by a subject matter expert. To add a Verified badge:
- Go to the topic page of the topic that you want to verify.
- Select Edit to enter edit mode.
- Choose Topic details. This will open the Topic details pane.
- Move the Verify this topic toggle to Yes.
- Select Manage.
- Optionally, add a description that’s specific to the verification. For example, you could write what department verified the topic and who to contact with questions.
- Assign editors who can make changes to the topic. All assigned editors will receive an email notification.
- Select Republish.
Note: The person who verifies the topic will be automatically assigned as an editor and can't be removed. Knowledge managers are always able to edit the topic.
Assigned editors can add or remove other editors. They can also unmark the topic as verified if the topic is no longer meeting your organization’s standards for verification. To remove or change a verifier, the new verifier must be in the assigned editors list or a knowledge manager. The new verifier needs to unmark the topic as verified and verify it again.
What you need to do to prepare:
For additional information on how to use Viva Topics, please visit this page.
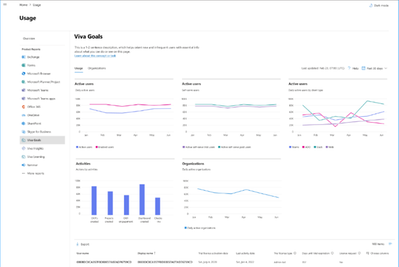
MC673710 — (Updated) Microsoft 365 admin center: Viva Goals Usage Report
TBD
Updated September 12, 2023: We are not moving forward with rolling out this feature at this time and will communicate via Message center when we are ready to proceed. We apologize for any inconvenience.
A new report will be made available to help you understand how Viva Goals is used within your organization. The new usage report in the Microsoft 365 admin center will provide metrics on the number of active users including trial and paid licenses and platform distribution (Teams, Slack, Azure DevOps, and Web) with the ability to view 7/30/90/180 day timeframes.
When this will happen:
We are not moving forward with rolling out this feature at this time and will communicate via Message center when we are ready to proceed.
How this will affect your organization:
Using the Viva Goals Usage report, admins will be able to view metrics for how people in your organization are using Viva Goals and in which platforms.
What you need to do to prepare:
Admins can assign the available licenses in their tenant to individual users based on their usage and license requests, via the Microsoft 365 admin center. Once released, you can view Viva Goals reports by going to the Microsoft 365 admin center -> Reports -> Usage -> Viva Goals.
For more information on Viva Goals please visit Introduction to Microsoft Viva Goals.
MC666967 — (Updated) Microsoft Viva: Default Connections Experience on Desktop
30-60 Days
Microsoft 365 Roadmap ID 152560
Updated October 3, 2023: We have updated the rollout timeline below. Thank you for your patience.
A new default experience on desktop is being released for Viva Connections that’s easier and faster to set up and optimizes content to deliver a modern employee experience. The new experience focuses on essential job tasks, personalized content, easy access to other Viva experiences, and better alignment with the mobile experience. It uses existing assets from your organization’s home site and Viva Connection’s Dashboard, Feed, and Resources. If your organization already has Viva Connections set up, you’ll have the option to choose to keep the existing desktop experiences that features the home site or to use the new home experience. Learn more about the new Viva Connections home experience.
When this will happen:
Rollout will begin in late September 2023 (previously early September) and is expected to be complete by late December 2023 (previously late October).
How this will affect your organization:
The default Connections desktop experience will automatically update in Microsoft Teams for customers who are currently using Viva Connections. When this feature is released, customers with existing home sites can choose to keep the existing desktop experience. With the new default desktop experience, admins and editors will be able to edit content and manage permissions from Microsoft Teams.
What you need to do to prepare:
To prepare for this change, help admins and editors for Viva Connections learn more about how to customize the default experience and how permissions work.
End users in your organization will use the same entry point in Teams as the previous desktop experience. When they view the new experience for the first time, visual prompts will walk them through the main functions of the design and how to interact with different elements. Share guidance with end users.
Microsoft Teams
MC678853 — Microsoft Teams for VDI: New Microsoft Teams Desktop Client in Public Preview
<30 Days
VDI customers using Azure Virtual Desktops, Windows 365, Citrix and VMware can soon use the new Microsoft Teams client.
Optimized VDI users on the new Teams client will continue to enjoy the same feature set as in the classic Teams client, and more (like Channels 2.0).
The new desktop client has been redesigned from the ground up, focusing on better performance, simpler user experience and reduced resource consumption. With these pillars as a foundation, the new app adopts Fluent UI, transitions from Angular to React for building user interfaces, moves data processing out of the main thread to a client data layer worker, and lastly, replaces Electron to leverage WebView2 as the host.
The installer has also been redesigned as an MSIX package, with a new install folder location (C:\Program Files\WindowsApps) and new profile location (Appdata\Local\Packages\MSTeams_8wekyb3d8bbwe).
These improvements make the new Teams:
- More responsive (faster application launch time, faster meeting joins, faster chat and channel navigation and scrolling)
- Less resource intensive (reducing CPU, RAM and Storage on the virtual machine, allowing for higher user densities in VDI environments).
When this will happen:
Public Preview: We will begin rolling out in early October 2023 and expect to complete rollout by late October 2023.
How this will affect your organization:
In order to rollout the new Microsoft Teams client to your organization, you can either:
1) "Rip and Replace": uninstall the classic Teams client and install the new one (recommended method)
2) Install both apps 'side by side' and let the user switch between them by using the toggle on the top left of the UI. You can control who sees the toggle by configuring the Teams Admin Center policy "Teams update policy."
What you need to do to prepare:
Admin documentation and download link can be found here.
In order to support the new Microsoft Teams client, the following minimum VDI and OS software versions are required:
Windows Operative System for the virtual desktop:
- Windows 10.0.19041 or higher (single or multiuser)
- Windows Server 2019 (10.0.17763) -coming soon
- Windows Server 2022 (10.0.20348)
- Windows Server 2016 is NOT supported. Please plan upgrades.
AVD/W365:
- RD Client Windows 1.2.1755
- RD Client Mac 10.7.7
- WebRTC Redirector Service 1.1.2110.16001
Citrix:
- Workspace app Windows 2203 LTSR (and any CU), or 2302 CR
- Workspace app Linux 2207
- Workspace app Mac 2302
- Workspace app Chrome/HTML5 2301
- VDA 1912 CU6 or 2203 LTSR, or 2212 CR
RegKey to Add on VDAs:
HKLM\SOFTWARE\WOW6432Node\Citrix\WebSocketService
Key (Multi-SZ) : ProcessWhitelist
Value: msedgewebview2.exe
VMware:
- Horizon Agent 7.13.1, or 2103
MC678852 — Out-of-box Controlled-content meeting template (Premium)
30-60 Days
Microsoft 365 Roadmap ID 91286
We are launching an out-of-the box template for meetings with external participants. The controlled content access template has preset defaults for meeting options to provide tight controls over lobby bypass, who can present, allowing chat across meeting lifecycle/in-meeting, and who can record.
When this will happen:
Standard Release: We will begin rolling out in mid-October and complete by late October 2023.
GCCHigh: We will begin rolling out early October and complete by mid-October 2023.
GCC: We will begin rolling out early November and complete by mid-November 2023.
DoD: We will begin rolling out mid-November and complete by late November 2023.
How this will affect your organization:
The use of this out-of-box template is to remove the manual set-up needed for meeting with external participants. One can access this template by going to Teams Calendar > Schedule meeting > Controlled-content meeting template. This template is also available in Outlook. Please go to Teams Meeting drop down and select Controlled-content meeting template.
What you need to do to prepare:
Please share about this functionality with your users.
MC678851 — Require Background Blur (Teams Premium)
<30 Days
Microsoft 365 Roadmap ID 163967
We are introducing granular controls to the existing Organizational Defined Background capability which is part of Teams Premium now. With the granular controls, admins will be able to show only custom backgrounds, require background blur, or preset an organizational background.
Organizational defined backgrounds - provides catalog of org backgrounds for user to choose from
- Show only custom backgrounds (launched July 2023) - when configured, users will only have the option to apply a custom background.
- Require background blur (ETA October) - when enabled, if a user does not have a background image applied their video background will be blurred.
- Preset organizational background (ETA end of November) - when enabled, a user will have a preset background defined by IT without the ability to change the background.
Go to Teams Admin Center > Meeting Policies > Customization Policies > Meeting backgrounds to enabled 'Apply background blur when no effect is selected.'
When this will happen:
Standard Release: We will begin rolling out early October and expect to complete by late October.
How this will affect your organization:
This will provide admins who have Teams Premium licensed users in their org with additional background controls.
MC678850 — Cloud IntelliFrame available on the new Microsoft Teams experience
30-60 Days
Microsoft 365 Roadmap ID 161428
Cloud IntelliFrame is an experience that allows online meeting attendees to see people in Teams Rooms more clearly, enhancing the hybrid meeting experience by creating smart video feeds of in-room participants. The smart video feed is created by zooming into their faces and eliminating distractions. You can see the expressions and gestures of the people in the room more easily, which will help improve collaboration in hybrid meetings. It creates equity in hybrid meetings as everyone can be seen and heard.
Cloud IntelliFrame is now available on the new Microsoft Teams experience.
When will this happen:
We will begin rolling out to Production tenants in mid-October.
GCC and GCCH will begin rollout by early November.
How will this affect your organization:
All Microsoft Teams Rooms on Windows with a Pro license equipped with cameras in the supported camera list will automatically opt-in to Cloud IntelliFrame. Online participants on the new Microsoft Teams experience (Windows or Mac) will have the option to see IntelliFrame video from the Room. They can switch it on by right clicking on the Room tile and selecting Turn on IntelliFrame.
People in the Room can disable IntelliFrame by using in-meeting settings on the console. This turns off Cloud IntelliFrame and switches back to standard view for the Room. All online attendees would then see the standard view from the Room.
Supported Cameras:
The following camera models when deployed in a Microsoft Teams Room on Windows with a Pro license will automatically use Cloud IntelliFrame.
- AVer CAM520 Pro
- AVer CAM520 Pro2
- EagleEye Cube USB
- HD Pro Webcam C920
- Jabra PanaCast
- Logitech Rally system
- Logitech BRIO
- Logitech ConferenceCam CC3000e
- Logitech MeetUp
- Logitech Webcam C925e
- Logitech Webcam C930e
- Microsoft® LifeCam Studio
- Polycom EagleEye IV USB Camera
- PTZ Pro 2
- PTZ Pro Camera
- Lenonvo ThinkSmart Cam
- Lenovo ThinkSmart One
- Yealink UVC30
- Yealink UVC34
- Yealink UVC50
- Yealink UVC80
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC678311 — Microsoft Teams: Meetings Apps in GCCH and DoD
30-60 Days
Microsoft Roadmap ID 166985
Microsoft Teams is now adding support for apps in meetings and enabling events/APIs for conversational Bots in GCC-High and DoD
Meetings enable collaboration, partnership, informed communication, and shared feedback. The meeting space can deliver a user experience for each stage of the meeting lifecycle. A meeting lifecycle includes pre-meeting, in-meeting, and post-meeting app experience, depending on the user type and user's role in a Teams meeting. Apps in Meetings allow meeting participants to be more productive by accessing services, content and data in a specific space in a meeting. Developers can create applications that create scenes for meetings, provide notifications to users, populate in-meeting dialogs, and more with meeting app extensibility.
When this will happen:
GCCH: Rollout will begin in early October 2023 and is expected to be complete by late October 2023.
DoD: Rollout will begin in early November 2023 and is expected to be complete by late November 2023.
How this will affect your organization:
This feature brings Conversational bot events/APIs and meeting apps to GCCH and DoD across all supported meeting types. Admins can manage applications that take advantage of conversational Bot events/APIs and meeting app capabilities from Teams Admin Center. This includes allowing/blocking apps, manage org-wide app settings, auto install and pre-pin apps based on admin approval.
What you need to do to prepare:
In a Microsoft 365 Government - GCC, GCCH and DoD deployment of Teams, all applications that use conversational Bots events/APIs and meeting app capabilities are blocked by default. The launch of this feature does not change that.
You can review current org-wide app settings for M365 government and determine how you want to manage applications and the application permissions.
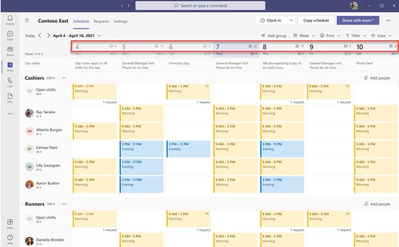
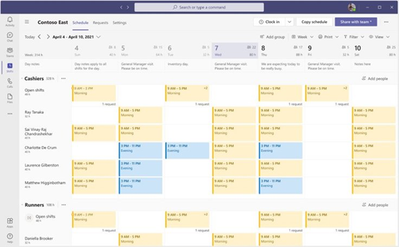
MC678309 — Microsoft Teams: Usability Improvements in Shifts app
30-60 Days
Microsoft 365 Roadmap ID 146855
We are thrilled to announce a series of exciting product enhancements in Shifts designed to empower frontline managers and workers to achieve more:
- Graph API for Day Notes
- People Count Display on Shift Calendar
- Full Name Display
- Last Filter View Saved
- Shifts Notes in Day View
- Manager Controlled Privacy Settings for Frontline Workers
When this will happen:
We will begin rolling out in early October 2023 and expect to complete rollout by late November 2023.
How this will affect your organization:
Now, managers have the flexibility to add day notes using the Graph API, in addition to the Shifts app. This powerful capability allows customers to seamlessly integrate relevant day notes from third-party or line-of-business applications, enhancing the Shifts experience.
Frontline managers can now make more informed staffing decisions with the introduction of the people count display on the Shifts calendar (team level and schedule group level).
- This feature provides a clear view of staffing levels, ensuring that the right workforce is scheduled for the day, week, or month.
- Managers can see the scheduled people count at both the team, and schedule, group levels.
Team members' full names will also now be visible in the team schedule.
- This helps managers quickly identify staff members, especially when names are lengthy, by allowing them to hide profile pictures.
This new feature automatically saves the last filter settings, so when users relaunch the Shifts app, their preferred view from the last session is readily available.
- We understand that frontline managers use various filters to customize their Shifts view. Our latest feature automatically saves the last filter settings, so when users relaunch the Shifts app, their preferred view from the last session is readily available.
Managers can save time when in Day view by seeing the Shifts' notes inline.
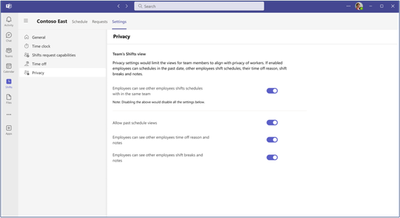
Frontline managers now have the power to manage time-off reasons and notes visibility for their employees, enhancing data privacy and control.
- Frontline managers can control the Frontline worker views in Settings at the team level.
- Managers can enable or disable the Team Shifts View, giving Frontline workers the ability (or not) to see their colleagues' shifts.
- Managers can restrict how far back Frontline workers can view their coworkers' schedules, ensuring historical data privacy.
- Managers can limit the level of detail Frontline workers can access about their coworkers' schedules, excluding sensitive information like Shift notes and break durations.
What you need to do to prepare:
There is nothing you need to do to prepare for these changes. You may want to notify users of these updates.
MC678061 — Reminder: SIP certificate final switch to new MSPKI Certificate Authority
Rolled Out
Following two tests on September 5th and 19th Microsoft will perform final switch to the new Certificate Authority (CA) on October 3rd starting at 10 AM UTC.
All Microsoft SIP endpoints will be gradually switched over to use certificates where the certificate chain will roll up to “DigiCert Global Root G2” Certificate Authority (CA).
When this will happen:
October 3, 2023
How this affects your organization:
If your Session Border Controllers (SBCs) are not properly configured with the new Certificate Authority (CA) your Direct Routing incoming and outgoing calls will fail after the switch. Please work with your SBC vendor directly for further guidance on SBC configuration.
The change requirement and test were communicated to Direct Routing customers through Message Center posts as well as Service Health Incidents in the Microsoft Admin Portal (MC540239, TM614271, MC663640, TM674073, MC674729). In addition, Microsoft announced the planned test and upcoming changes in: What's New Direct Routing - Microsoft Teams | Microsoft Learn , and posts were made on LinkedIn and in other Tech Community articles such as: TLS certificate changes to Microsoft 365 services including Microsoft Teams
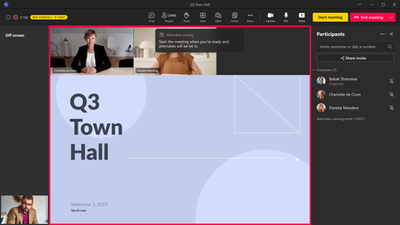
MC678001 — Microsoft Teams Premium Town hall
<30 Days
Microsoft 365 Roadmap ID 173182
To simplify the virtual event experience on Teams, we are integrating our live event capabilities into our Teams meeting experience. This will create a unified experience for users whether they are hosting a small meeting, customer-facing webinar, or company-wide town hall. As a part of this integration, we are introducing Town halls in Microsoft Teams, a new experience to host and deliver large-scale, internal events to create connections across an organization. Town halls will provide a one-to-many format with advanced production capabilities and a structured approach for attendee engagement. With town halls, customers can host various types of internal as well as external events including company-wide town halls, all hands, global team meetings, internal broadcasts, fireside chats, and more.
When this will happen:
Standard Release: We will begin rolling out early October 2023 and expect to complete mid-October 2023
How this will affect your organization:
Town hall will replace Teams Live Events and be available for Microsoft 365 and Office 365 customers and advanced capabilities in town hall will be available for Teams Premium customers. The new town hall experience will be generally available and start to roll out globally to commercial customers on October 5. Starting at launch, town hall will have an ongoing release of features to create parity with Teams Live Events functionality and will reach full feature parity ahead of Teams Live Events retirement in September 2024.
Our recommendation is that customers (both existing and new) start using town hall as it becomes generally available in October. Advanced town hall functionality in Teams Premium provides the following capabilities, everything in basic town hall functionality (co-organizer support; automated invitation and email recording emails; green room; manage what attendees see; RTMP-in; RTMP-out; on-demand recording; live transcription (AI-generated); AI-generated captions; and attendee reporting) plus:
- Attendee capacity of 20,000 attendees
- Host up to 50 concurrent events across a tenant
- Email customization
- Microsoft eCDN support with real-time insights and monitoring
- Live translation captions (up to 10 languages)
Scale up to 20k
Real Time event Analytics. (found inside reporting tab)
Custom Email Communications
Support up to 10 languages for Transcription
10 languages: en-us (English), ja-jp (Japanese), es-es (Spanish), pt-pt (Portuguese), fr-fr (French), zh-cn (Chinese), de-de (German), it-it (Italian), ko-kr (Korean), ru-ru (Russian)
What you need to do to prepare:
This feature will be enabled by default upon release with Premium subscription, however if required by Admin Policy, can be disabled.
Please update PowerShell module to the latest version before making Large Scale Meeting Event policy changes.
To disable Town hall use the following script:
Set-CsTeamsEventsPolicy -Identity <policy name> -AllowTownhalls Disabled
To disable Public Town hall utilize the following parameter (this will affect Webinars as well)
-EventAccessType : EveryoneInCompanyExcludingGuests
Everyone: Enables creating events to allow in-tenant, guests, federated, and anonymous (external to the tenant) users to join the event. (enables/disables a public Large Scale Event)
Note: Learn more about town hall when documentation becomes available on adoption.microsoft.com and learn.microsoft.com on October 5.
MC677839 — (Updated) Microsoft Teams: Customization for Watermark in Meetings (Premium)
<30 Days
Microsoft 365 Roadmap ID 98414
Updated October 3, 2023; We have updated the rollout timeline below. Thank you for your patience.
Microsoft Teams meeting organizers can soon choose between a single watermark or a repeated watermark with the additional ability to set the opacity of the watermark. The single watermark will display in the viewer's email on top of the shared content and/or video in a clean and discreet manner. The opacity option will enable meeting hosts to set the transparency of the watermark to their liking. When the single/repeated watermark option is enabled and the opacity is set via Meeting options, the watermark will be enforced for all meeting attendees.
When will this happen:
We will begin rolling out in late October 2023 (previously early October) and expect to complete rollout by late October 2023.
How this will affect your organization:
Admins can let users organize a protected meeting with the option to adjust the opacity to their liking.
Admins can have the option to set a meeting policy based on the company's requirements regarding the watermark. They can force either a single or repeated pattern and set a transparency level that the meeting host will be unable to change. If the company's guidelines are not as strict, the IT admin can enable the meeting host to set the pattern and transparency level for the individual meetings.
The default in Teams admin center would be repeated with 30% transparency along with the permission granted to the organizer to customize the values in Meeting options while scheduling the meeting. If an admin wants to, they can further go and set other values as default and remove the permissions. If the permission is removed, the organizer would see the default value set by the admin in Meeting options. The organizer will not be able to update it.
What you need to do to prepare:
To enable the watermark feature for users when they schedule a meeting, admins can take the following steps Teams admin center:
- Navigate to Meetings > Meetings policies > Add
- Scroll to the bottom where it says Watermark and toggle the switch for whichever one you'd like to enable watermark on
Scheduling a meeting in Teams:
- Click on Calendar on the left panel.
- Navigate to the top right corner and click "+ New meeting".
- Enter meeting details accordingly.
- On the right side, click on "More options."
- Scroll down to "Apply a watermark to shared content" and "Apply a watermark to everyone's video feed", enable whichever one you would like. If you decide to enable "Apply a watermark to shared content" you can choose which pattern you would like, repeated or single and choose the transparency level to your liking. The same follows if you enable "Apply a watermark to everyone's video feed".
- Once the customization is set, click Save.
Now you can save your meeting and watermark customization will be applied once the meeting starts.
MC677517 — Availability of Incoming webhook connector in Microsoft Teams – GCCH
30-60 Days
Microsoft 365 Roadmap ID 166986
Connectors allow users to subscribe to receive notifications and messages from your web services. Connectors and Webhooks in GCCH is disabled by default. To enable, the Tenant Admin is required to follow the steps listed in the “What do you need to do to prepare” section.
When this will happen:
Standard Release: We will begin rolling out late October 2023 and expect to complete by mid-November 2023.
How this will affect your organization:
GCC High customers will now have access to the Incoming webhook connector. Connectors and Webhooks help to connect the web services to channels and teams in Microsoft Teams. Webhooks are user-defined HTTP callback that notifies users about any action that has taken place in the Teams channel. Connectors allow users to subscribe to receive notifications and messages from your web services. They expose an HTTPS endpoint for your service to post messages in the form of cards.
What you need to do to prepare:
Teams Tenant Admin will need to execute Exchange PowerShell commands as described in the Manage Microsoft 365 connectors and custom connectors - Microsoft Teams | Microsoft Learn to enable Connectors in their tenant.
Ensure ‘ConnectorsEnabled’, ‘ConnectorsEnabledForTeams’ and ‘ConnectorsActionableMessagesEnabled’ flags are set to true. Please note - it may take up to 24 hours for these flags to propagate in Exchange Online. Setting these flags will allow users to load the Connectors dialog and Configuration pages successfully.
However, you will find that no Connector apps are available for immediate use. As a Teams Tenant admin, you can manually upload the app manifest in Teams app store to publish the app to your organization as a custom/LOB (Line of Business) app. To acquire a 3rd party (3P) connector of choice, please reach out to the 3P vendor and Microsoft SME, to assess the availability of the desired connector in GCCH. The 3P vendor should be able to provide you the app manifest to leverage this hugely valuable feature, in your organization.
Please note that only the Connector app currently allowed is an Incoming Webhook connector.
The process to be used to upload Incoming Webhook as Teams custom app can be referred here - Manage custom app policies and settings - Microsoft Teams | Microsoft Learn
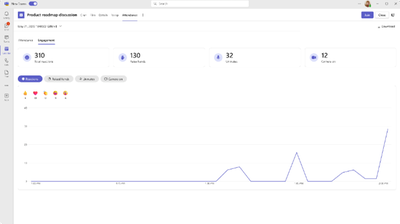
MC677231 — Microsoft Teams: Engagement Information in Teams Attendance Report (Premium)
30-60 Days
Microsoft 365 Roadmap ID 162171
The new engagement information will enable organizers to view meeting engagement data such as total reactions, raised hands, cameras turned on, and more in the "Attendance" tab after a meeting or webinar.
When this will happen:
Targeted Release: We will begin rolling out in early October 2023 and expect to complete rollout by mid-October 2023.
Standard Release: We will begin rolling out in late October 2023 and expect to complete rollout by early November 2023.
How this will affect your organization:
If your tenant turns ON the Attendance Report, organizers will see engagement information in the "Attendance" tab in calendar or meeting chat. Information will include count of reactions, raised hands, unmutes and cameras turned on at meeting level and attendee level.
What you need to do to prepare:
If you need engagement information in Attendance Report, please make sure the "Attendance Report" policy is turned ON by both the admin and the organizer.
Note: If the end user opts out of the Attendance Report in Teams settings, then the user's engagement information will not be shown in the Attendance Report.
MC676300 — (Updated) Microsoft Teams: Choose Which Users to Notify When Publishing a Task List
<30 Days
Microsoft 365 Roadmap ID 144248
Updated October 3, 2023: We have updated the rollout timeline below. Thank you for your patience.
The task publishing experience in Microsoft Teams will soon allow you to choose which users to notify when you publish or unpublish a task list. You'll soon have the ability to choose which members of teams receiving the tasks should get a notification in their Teams activity feed: all owners and members, owners only, or no one. Similarly, you will be able to choose who to notify when unpublishing a task list.
When this will happen:
Rollout will begin in mid-October 2023 (previously late September) and is expected to be complete by late October 2023.
How this will affect your organization:
If you are using the task publishing feature, you will see the additional notification options in the confirmation screen when you publish or unpublish a list.
What you need to do to prepare:
You do not need to take any additional steps to prepare.
MC676296 — Ratings and Reviews for Apps on Teams now Available
<30 Days
Microsoft 365 Roadmap ID 122300
We are announcing the upcoming launch of the "Ratings and Reviews" feature for apps on Microsoft Teams. This new addition will empower users to view feedback from customers for apps from Microsoft and other third party app publishers. Users can also provide feedback on apps they've installed, and by default these reviews will be marked as anonymous. Not only this, but app publishers will also have the capability to respond to these reviews via the Partner Center, thereby enabling a new mode of communication between partners and end users. Furthermore, this experience is powered by Microsoft AppSource's Ratings Service, hence ensuring the availability of reviews on the AppSource website as well as the Teams client experience. This feature is part of our continuous effort to enhance user experience and transparency within the Teams environment.
When this will happen:
Standard Release: We will begin rolling out in mid-October 2023 and expect to complete rolling out in late October 2023.
How this will affect your organization:
Users can now leverage customer sourced feedback for apps that they wish to install on Teams, thereby aiding their app discovery and installation experience.
What you need to do to prepare:
No action item is needed on behalf of the IT Admin for enabling this feature. This experience is controlled by the Optional Connected Experiences, and can be turned off by referring to this documentation.
MC675813 — Simplifying Meeting Join Experiences on Teams Mobile
30-60 Days
Microsoft 365 Roadmap ID 146741
We are improving the meeting join experience on Teams Mobile (iOS / Android) in several ways:
- Streamlining the meeting join process by reducing the number of steps it takes to join the meeting, particularly for users joining from externally of the organization.
- Users who join without signing in will now have the capability to preset and preview video / audio settings prior to joining the meeting.
- Simplifying the join process for users with multiple accounts by improving the account switching user experience.
When this will happen:
Standard Release: We will begin rolling out mid-October and expect to complete by mid-November.
How this will affect your organization:
Mobile users will see an improved and refreshed experience when joining meetings.
What you need to do to prepare:
No action required - this is a user experience update.
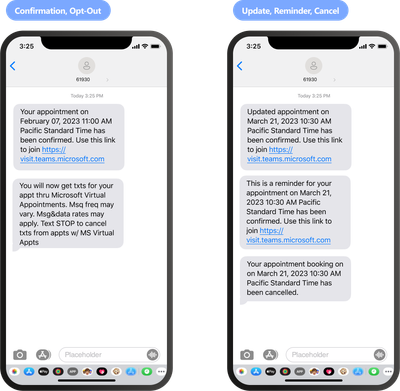
MC675812 — SMS Text Notifications in Virtual Appointment Teams Meeting Template - Expansion to UK Canada (Premium)
>60 Days
Teams Premium users in the United Kingdom and Canada will soon have the ability to send SMS text notifications about a meeting in the Virtual Appointment Teams Meeting template. This Premium feature will be available to all users that have a Teams Premium license and access to the Virtual Appointment Teams Meeting Template.
When this will happen:
Public Preview: We will begin rolling out in early November 2023 and expect to complete rollout by mid-November 2023.
Standard Release: We will begin rolling out in late November 2023 and expect to complete rollout by early December 2023.
How this will affect your organization:
When released, all users within your organization that are eligible will see the SMS text notification feature within the Virtual Appointment Teams Meeting template. Eligible users are users that have a Teams Premium license, access to the Virtual Appointment Teams Meeting Template, and access to the SMS notification feature.
Improve the meeting experience of external guests by ensuring they stay up to date on the details of their virtual appointment and can join from anywhere. When scheduling a virtual appointment, the meeting organizer will be able to input the external guest's phone number. The external guest will receive an SMS text message that provides details of their appointment (date/time) and a meeting join link so they can easily join the meeting from a mobile browser. They will receive a text message if the date or time of the meeting changes, if the meeting is cancelled, and will receive a reminder 15 minutes before the appointment. The user can opt out to all text messages for all meetings from the Virtual Appointment Teams Meeting Template by replying 'STOP' to the text message. They can opt back in at any time by replying 'START'.
What you need to do to prepare:
If you do not want users within your tenant to be able to access the SMS text notification feature in the Virtual Appointment Teams Meeting Template, you can implement a user-level policy via PowerShell to restrict access to this feature.
Use the Get-CsTeamsVirtualAppointmentsPolicy cmdlet to fetch policy instances of TeamsVirtualAppointmentsPolicy. Each policy object contains a property called EnableSmsNotifications. This property specifies whether your users can choose to send SMS text notifications to external guests in meetings that they schedule using a virtual appointment meeting template. If EnableSmsNotifications is set to Disabled/False, then the user(s) with the policy set will not see the SMS notification feature or phone number field in the Virtual Appointment Teams Meeting Template.
Please refer to relevant documentation on configuring this setting here. We also recommend updating any end user documentation in your organization related to the Virtual Appointment Teams Meeting Template.
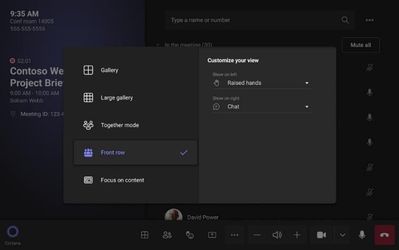
MC675503 — Meeting Protection Support and Improved View Switcher for Teams Rooms on Android
>60 Days
The latest version of Teams Rooms on Android Update 3 (2023) includes new in-meeting experiences including:
- Improved view switcher and front of room display controls
- Meeting protection support - End-to-end Encryption for meetings and Sensitivity labels
When this will happen:
We will begin rolling out in late November 2023 and expect to complete rollout by late December 2023.
How this will affect your organization:
The updated interface for the Teams Rooms on Android View Switcher menu provides users with more control of the front of room display(s) during a meeting and enables customizations including visibility of the meeting chat and selected meeting components displayed on the left and right panel for Front Row. IT admins can configure the default number of panels and default components on panel(s) using the local device setting.
Teams Rooms on Android devices applies the Teams Premium meeting security features including end-to-end encryption and sensitivity labels if the meeting organizer has them turned ON.
Note: Features need to be activated through the Meeting options in Teams Calendar or Outlook on desktop or mobile devices. To enable the features a Teams premium license may be required.
If End-to-end Encryption is enabled, the Teams Rooms on Android will display a shield with a lock icon next to the view switcher. This icon includes a 20-digit group key that can be verified with other meeting participants.
Note: Together mode and Large Gallery are not available during End-to-end Encrypted Meetings, but meeting chat is permitted. If a Teams meeting is set with a Sensitivity Label, room users will be informed that the label has been applied when clicking the shield with a lock icon.
What you need to do to prepare:
Please notify your users about this new experience and update your training and documentation as appropriate.
MC675501 — Microsoft Teams: Watermark support for recording playback (Premium)
<30 Days
Microsoft 365 Roadmap ID 137654
Recording can now be enabled for watermarked meetings (Watermark feature requires a Teams Premium license). An email ID will be displayed as the watermark during the meeting recording playback. Once a meeting has concluded, users can access the recorded content on both web and mobile platforms to watch the recording with watermarking.
When this will happen:
We will begin rolling out in mid-October and expect to complete by late October.
How this will affect your organization:
IT admins can now encourage meeting hosts to enable recording for watermarked meetings. The recording playback will be watermarked with the participants' email ID to avoid information leakage and add a layer of protection.
What you need to do to prepare:
You may need to update the documentation for your users to mention the existence of this feature.
- In a watermarked meeting, the meeting organizer and the co-organizer can now start recording by clicking on the "start recording" button.
- Once the meeting/recording has ended, participants can retrieve the link in the meeting chat and open the recording on the web.
- When the recording is opened on the web, they will see their individual email ID as the watermark on the meeting.
- When a meeting is recorded by the organizer, it will be saved onto their SharePoint and be able to download since they are the owner of the recording.
- The download option is only for the person who recorded the meeting (file owner). The owner can provide access to the other person.
- On the recording, it will add the email ID of the user who clicked on the recording file to watch the recording playback in the browser.
- The owner of the file will see their own email ID all over the recording.
- As a participant/other viewer of the file, if I watch the recording on the web, I would see my email ID all over the recording.
You can find more details about Watermark in Teams Premium in this documentation: Watermark for Teams meetings.
MC675500 — Teams Panels Recognized and Visible in Teams Rooms Pro Management Portal
30-60 Days
We are pleased to announce that Teams Panels will soon appear and be supported in the Teams Rooms Pro Management Portal. Panels will start to appear under the Rooms and Inventory pages. The device health signals and management functionality will be similar to what is offered on Teams Rooms on Android devices.
When this will happen:
Rollout is expected to start in late October 2023 and is expected to be complete by late November 2023.
How this will affect your organization:
On the Rooms page, you will have the ability to see the status of the Panel, the IP address, serial number, and app and firmware version. You can remotely restart the device, add it to a Group, or record an issue. You can also view the current configuration profile, the update history, and search for and apply a profile. If you want to change a configuration profile or make a new one, you will need to use the Teams Admin Center.
On the Inventory page, you will be able to see Panels at a room level. The device type listed will depend on whether the Panel is sharing its resource account with another device. Regardless, after clicking on the room and then the ‘Inventory’ page, you will be able to see the Panel listed as a device.
What you need to do to prepare:
No update is required.
MC675496 — Microsoft Teams: Green screen feature in Teams Meetings
30-60 Days
Microsoft 365 Roadmap ID 117941
This feature was originally announced in MC529415 (March '23) and was delayed for our Government customers. We are now ready to proceed and apologize for the delay.
Microsoft Teams will soon be releasing a new green screen feature for users. The virtual background with a green screen will provide an enhanced virtual background effect.
When this will happen:
We will begin rolling out in late October and expect to complete by late November.
How this will affect your organization:
Green screen improves the sharpness and definition of the virtual background effect around your face, head, ears, and hair. It also allows you to show a prop or other object in your hand to be more visible to other participants in a call.
Supports the following:
- Desktop platforms: Windows and macOS with Intel chips, not supporting Mac M1/M2
- Device: Requires a solid color screen or clean background wall behind you
- User Experience: Users must apply a background effect in Teams meetings to enable the green screen effect and should select the correct backdrop color so that the effect is applied correctly and better quality is achieved
Known limitations:
- Green screen will automatically disable background blur and Together Mode while being compatible with Presenter modes like Standout, Side-by-Side and Reporter, PowerPoint Live Standout, and background replacement (JPEG/PNG).
- Transparent or translucent objects cannot produce a good green screen effect.
- If the object is too thin, it cannot be properly detected.
To enable:
Please make sure that you have applied a background effect in Teams meeting before enabling the green screen effect and chosen the correct backdrop color so that the effect is applied correctly. Please also ensure you have a solid color screen or clean background wall behind you.
- After you join a meeting, click the “More” icon in the meeting toolbar, go to “Video effects.”
- When the “Video effects” panel page is open, go to “Green Screen Settings” in Backgrounds section and click the link to turn on the Green screen toggle button under “Teams settings -> Devices -> Green screen.”
- Click the backdrop icon and move your mouse cursor into the Preview box to manually pick backdrop color.
- Return to your meeting.
What you need to do to prepare:
You may want to update your training materials indicating that this feature is available to users.
MC675282 — Wiki retirement and the future of note taking in Teams Channels
>60 Days
We are announcing that Wiki's will be retired from Teams by April ’24. We are offering note taking capabilities through Teams Channels powered by OneNote.
When & how we are retiring Wiki:
- Stage 1 – (Timeline – October 2023) Users won't be able to create new wikis, but they can continue to access (read/write) their existing wiki. In standard channels users will have the option to export their wiki content to OneNote. Once users export their content to OneNote, the Wiki is available as read only.
- After exporting, each wiki in a channel appears as separate section in OneNote and each Wiki page will be a separate page in OneNote.
- Stage 2 – (Timeline – End of CY ’23 or Jan ’24) Wiki tab in channel will not be supported; users will be easily able access (read/write) content in Wiki app. Users can also export their content to OneNote. Users will be able to easily navigate to Wiki app from channels.
- Stage 3 – (Timeline – April 2024) Wikis tab and wiki App wouldn't be able to accessible in Teams and users wouldn't be able to export. Users can download their wiki files from SharePoint.
With this release in October, users have an option to export their wiki content to OneNote notebooks in Teams standard channel. After exporting users can go to the Notes tab to collaborate using OneNote in channels.
Note: With this change users can continue to access and edit existing wikis but can’t create new wikis in Teams channels.
OneNote provides an enhanced note taking experience.
- Easy collaboration across the team
- View all channel notes in a team in one place organized within a single notebook.
- Rich editing with typing, ink annotations, highlighting, file attachments, etc.
- Easy recall & search for channel notes within OneNote on any platform
What you can do to prepare:
We urge users to export their channel wikis to OneNote once it is available.
If your organization has not enabled OneNote you can review this documentation:
FAQs:
Why is Teams retiring wiki?
- Our users’ needs for note taking are evolving every day and the current capabilities & infrastructure of Wiki will not be able to cater to those needs in future. We understand that moving away from wiki is a difficult change and we want to help our users throughout the changes.
How can I take notes in channels after this change?
- New channels will now come with a OneNote notebook (Microsoft 365 brand for note taking). OneNote brings goodness of richer formatting, better organization, search within OneNote app and keeps the experience consistent across Microsoft 365.
When & how are we retiring Wiki?
- Stage 1 – (Timeline – early October 2023) Users won't be able to create new wikis, but they can continue to access (read/write) their existing wiki. Users also have the option to export their content to OneNote. Once users export their content to OneNote, the Wiki is available as read only.
- After exporting, each wiki in a channel appears as separate section in OneNote and each Wiki page will be a separate page in OneNote.
- Stage 2 – (Timeline – End of CY '23 or Jan '24) Wiki tab in channel will not be supported; users will be easily able access (read/write) content in Wiki app. Users can also export their content to OneNote.
- Stage 3 – (Timeline – April 2024) Wikis tab and wiki App wouldn't be able to accessible in Teams and users wouldn't be able to export. Users can download their wiki files from SharePoint.
What happens to my existing data?
- Your data is accessible from SharePoint as per retention policy even after Wiki is retired. You can download wiki content from SharePoint.
Does end user need to export wiki one by one or in bulk?
- End users will have to export wikis one by one per Wiki tab. If there are more than wiki tabs in a channel, then users will have to export them separately. Users can export their wiki by visiting Wiki tab.
Who can export Wiki to Notes?
- Any team member who has access to add/remove tab in a channel can export their Wiki.
Is there a bulk export option available at tenant level?
- No, users can export their wikis as per their convenience.
Known limitation:
- OneNote notes only work in Default (Light) and High contrast mode.
- Wiki export option is only available from standard channels, for private channels wiki, users will have manually copy to OneNote or any app of their choice.
MC675281 — Generate unique join links for external presenters so they can easily join events
30-60 Days
Microsoft 365 Roadmap ID 123149
Organizers can set up events and effortlessly add external presenters, who will receive exclusive Teams join links. These links enable external presenters to directly enter the event, eliminating the need for organizers to manually admit them from the event lobby or modify their event role during the session. This creates a hassle-free event experience for organizers and presenters!
External Presenters are considered people outside of your organization, including guests (AAD/B2B/non-AAD), federated, unfederated, and anonymous users (non-AAD).
This feature is available for webinars only. This is not a Teams Premium feature.
When this will happen:
Standard Release: We will begin rolling out late October and expect to complete by early November.
GCC: We will begin rolling out late October and expect to complete by early November.
How this will affect your organization:
We suggest updating your internal documentation to include this new feature.
The email template that external presenters will receive will look like the template below.
What you need to do to prepare:
This feature will appear on the webinar scheduling forms when it's fully rolled out.
MC675276 — Teams Network Assessment Tool Urgent Update Required
Rolled Out
Note: If your organization is not using the Teams Network Assessment Tool you can safely disregard this message.
An update has been released for the Teams Network Assessment Tool on September 7th, 2023 (Version 1.5.0.0).
This update is required in order for the tool to continue working with full functionality. Older versions of the tool previous to version 1.4.0.1 will stop working on October 2nd, 2023.
The following functionality will continue to work after this date:
- Perform connectivity checks.
- /infraconnectivitytest Perform HTTP stack infra tests.
- /interfaces Dumps the list of the interfaces found.
However, the quality check functionality (/qualitycheck switch in the tool) will no longer function.
For the quality check functionality to work you must update the Teams Network Assessment Tool by October 2nd, 2023.
The quality checks will fail with the following errors:
- ERROR: Call setup failed – Failed to establish connection with local relay.
- ERROR: Check that the relay is configured correctly in your config file.
- ERROR: Recommend running the connectivity checker for more details.
It is recommended you update your Teams Network Assessment tool as soon as possible to avoid any unexpected failures. The update is available at Microsoft Downloads at the following link: Microsoft Teams Network Assessment Tool - download.
MC674737 — (Updated) Microsoft Teams: Emojis, GIFs and Stickers Unified in One Picker
>60 Days
Microsoft 365 Roadmap ID 84023
Updated September 27, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can soon find all of their emojis, GIFs, and stickers in a combined picker in Microsoft Teams.
When this will happen:
Standard Release: We will begin rolling out in early November 2023 (previously early October) and expect to complete rollout by late November 2023.
Gov Clouds: We will begin rolling out in early December 2023 and expect to complete rollout by late January 2024.
How this will affect your organization:
Users can find emojis, GIFs, and stickers combined in one menu under the smiley face icon. All the fun content will remain as normal for users to add in their messages.
What you need to do to prepare:
There is nothing you need to do to prepare.
MC674419 — Retire Microsoft Teams Single-window UI in VDI for your organization
>60 Days
We will be retiring the Single Window UI feature from Microsoft Teams when optimized for VDI beginning January 31st 2024. Instead we recommend the utilization of Multi Window UI (also known as the new meeting experience), which is where we will continue to invest our development resources.
The Multi-window capability provides users with the option to pop out chats, meetings, calls, or documents into separate windows to help streamline their workflow while their call or meeting is in progress.
Accessing Teams and chats will be possible while keeping the popped-out call or meeting window visible - whether that's on the same screen as the main Teams client or on a secondary display.
It also brings new experiences to VDI such as ‘Call Me’, Background Blurring and Effects, Large Gallery, Together mode, Transcriptions and more.
Additionally, meeting and call controls such as mute, video, chat, leave, and more are now located at the top of the meeting window so that they are always available and never block the underlying content.
With Single-window, Microsoft Teams UI behaved like a ‘single pane of glass’, and if users tried to multi-task for example by clicking on a chat while there was a call in progress, this would trigger the appearance of a floating window in the UI (see picture below, bottom left).
In addition, the pre-join meeting experience would display the peripherals and audio options on the bottom, under the self-preview (see picture below, top left).
Once the user joins a meeting, the meeting and call controls bar is docked at the bottom/center of the UI (see picture below, middle left).
When this will happen:
January 31, 2024
How this will affect your organization:
You are receiving this message because our reporting indicates one or more users in your organization are using Single Window UI in Teams.
This mode is present when users are running old versions of the VDI stack, or the Teams client (older than 1.5.00.11865).
Minimum version requirement for Multi Window:
- Citrix:
- Citrix VDA 1912 CU6 LTSR
- Citrix VDA 2112 CR
- Citrix Workspace app for Windows 2203 CU1
- Linux and Mac 2209
- ChromeOS 2301
- VMware:
- VMware Horizon Agent 7.13.1 , or 2203
- Azure Virtual Desktops or Windows 365:
- RD Client Windows 1.2.1755
- RD Client Mac 10.7.7
- WebRTC Redirector Service 1.1.2110.16001
Recommended versions:
- Citrix: Latest Current Releases for Workspace app and VDA. Or latest CUs for LTSRs.
- VMware: Latest Horizon Agent
- AVD/W365: Latest RD Clients in Public release, and latest WebRTC Redirector Service.
Impact to users:
Users will no longer be able to use video or screensharing when they are using Microsoft Teams optimized for VDI when this change is implemented.
We'll be gradually rolling this deprecation out to customers in late January and complete this by January 31st 2024.
What you need to do to prepare:
To avoid work disruptions, we recommend you either:
- Update your VDI Infrastructure and Microsoft Teams versions to the minimum level supporting Multi-window
- Use Microsoft Teams in non-optimized mode (a.k.a server-side rendering, incurring higher VM resource consumption like CPU, RAM and Network traffic). For instructions on how to disable optimization, check your VDI Vendor’s documentation (AVD/W365, Citrix, VMware)
MC673978 — Custom Meeting Themes Now Available for Light Theme Meetings (Premium)
Rolled Out
Custom Meeting Themes, a Teams Premium feature, will now support branding assets for light theme meetings. IT admins will be able to upload brand image and logo that specifically appear for users using light theme meetings to a customization policy.
This is a Teams Premium feature and requires a Teams Premium or Advanced Communications license to use.
Note: Light theme meetings is only available on the New Teams client.
When this will happen:
We will begin rolling out in early September 2023 and expect to complete rollout by mid-September 2023.
How this will affect your organization:
Admins will be able to upload light theme brand image and logo assets to their tenant's customization policies in the Teams admin center.
What you need to do to prepare:
Work with your organization's marketing and brand manager to acquire the proper light theme brand image and logo assets. Asset requirements can be found in the Tenant Admin documentation.
MC673975 — Teams Rooms Pro GCC licenses to now include the Teams Rooms Pro Management service plan
<30 Days
Microsoft 365 Roadmap ID 141826
Teams Rooms Pro customers in GCC will have the Microsoft Teams Rooms Pro Management service plan included in their license. Starting in early October, all new Teams Rooms Pro licenses will have these automatically included. Existing Teams Rooms Pro customers in GCC will have their licenses updated shortly afterwards. These changes will be observable in the Microsoft 365 Admin Center.
When this will happen:
We will begin rolling this out in early October 2023 and expect to complete by late October 2023.
How this will affect your organization
All Teams Rooms Pro licensed devices in GCC will be able to enroll their devices into Teams Rooms Pro Management
What you need to do to prepare
No additional steps are required to facilitate this licensing update.
MC673714 — (Updated) Microsoft 365 admin center: New Premium Teams Usage Report
<30 Days
Microsoft 365 Roadmap ID 163426
Updated September 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
A new product usage report will be available within Microsoft 365 admin center usage reports to help Admins understand how Microsoft Teams Premium is being used within their organization by daily active users, features, and by paid and trial license types.
Teams Premium usage reports will include daily active users, and three features in the first release: org-defined backgrounds, custom together mode, and live translation caption. Additional feature metrics coming in future iterations.
The report displays trends over the last 7/30/90/180 days, including a per-user view, and contains the user’s last active date and license information.
When this will happen:
Standard release. We will begin rolling out beginning late September 2023 (previously early September) with completion expected by late October 2023 (previously late September).
How this will affect your organization:
Admins with the correct permissions will soon have access to new usage reports for Teams Premium.
What you need to do to prepare:
To access the new reports, go to Reports -> Usage -> Teams Premium.
For more information regarding these reports, please review the following documentation.
MC671824 — (Updated) Power Automate app changing name to "Workflows" within Microsoft Teams
30-60 Days
Microsoft 365 Roadmap ID 131294
Updated September 6, 2023: We have updated the rollout timeline below. Thank you for your patience.
To provide a unified workflow experience within Microsoft Teams we will be merging the existing Workflows app with the Power Automate app. With this merger the Power Automate app will be changing its name to "Workflows".
There will be no change to user experience within the app. Users will still be able to manage all their flows within the app along with browsing workflow templates or creating a new flow from scratch. Whether you have existing workflows in the Power Automate app or the Workflows app your workflows will persist in the new unified app. Users will still be able to configure new workflows through the various app entry points (tab, bot, message extension, message action, personal app).
When this will happen:
Targeted Release: We will begin rolling out early October 2023 (previously mid-September) and expect to complete by mid-October 2023 (previously late September).
Standard Release: We will begin rolling out mid-October 2023 (previously late September) and expect to complete by early November 2023 (previously early October).
GCC Release: We will begin rolling out early November and expect to complete by early November 2023.
How this will affect your organization:
Power Automate app will be changing its name to "Workflows".
The app will be pre-installed for all Teams users when this merger is released. If users had uninstalled this app previously it will show for them again and they will need to uninstall.
Teams Admin Center: If admins previously disabled the Power Automate app it will still remain disabled after the merger. However, if admins had previously disabled the old Workflow app, since that app no longer exists, they will need to go back into TAC and disable the new Workflows app.
What you need to do to prepare:
Consider bringing awareness to your users about this change if your tenant uses the Power Automate app within Microsoft Teams.
MC668258 — (Updated) Microsoft Default for Tag Management to include Team Members
Rolled Out
Microsoft 365 Roadmap ID 88318
Updated September 6, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are updating Microsoft Default setting to Team Owners and Members for Teams Tag Management settings in Teams Admin Center.
If you have already explicitly made a selection to your Tag Management settings your tenant will not be affected by this change.
If you have not made changes to Tag Management settings, Microsoft Default settings will apply for your tenant. Microsoft Default settings currently map to "Team Owners" value but this update will change it to "Team Owners and Members".
As Admin, please set tag management settings to reflect tenant-level preference. Select “Team Owners” to keep tag management limited to Team Owners, or select “Team owners and members” to allow all team members to create and edit tags.
In Teams client, users will still see the same options as they do today: "Team Owners" and "Team owners and members".
When this will happen:
- Preview: We will begin rolling out mid-August 2023 and expect to complete by early September 2023 (previously late August).
- Targeted Release: We will begin rolling out late August 2023 and expect to complete by mid-September 2023 (previously early September).
- Standard Release: We will begin rolling out late August 2023 and expect to complete by mid-September 2023 (previously early September).
How this will affect your organization:
- If you have already explicitly made a selection to your Tag Management settings your tenant will not be affected by this change.
- If you have not made changes to Tag Management settings, Microsoft Default settings will apply for your tenant. Microsoft Default settings currently map to "Team Owners" value but will map to "Team Owners and Members" with this change.
If you are an EDU tenant, non-owner students cannot manage tags as long as the Tenant level settings is Team Owners or Microsoft Default. We will continue to respect explicit and preferred tenant settings over Microsoft Default settings. Select your preferred tag management setting for your tenant to ensure you are not impacted by future changes.
What you need to do to prepare:
As tenant Admin, please change your tag management settings to your preferred setting. Here are some steps you can take:
- Sign in to Microsoft Teams admin center at https://admins.teams.microsoft.com.
- In the left navigation pane under Teams section, select Teams settings
- Under Tagging section, select your preference for "Who can manage tags"
MC661228 — (Updated) Join third-party meetings from Teams
<30 Days
Microsoft 365 Roadmap ID 138139
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
When a third-party meeting is created from Outlook or OWA, participants of the meeting will now be able to Join the meeting directly from Microsoft Teams. The participants will see "Join" button on the Teams calendar events card and in the meeting details page. On clicking the Join button, the link will route the users to the browser or the third-party application to join the meeting. This experience will be available on both mobile and desktop.
When this will happen:
We will begin rolling out mid-September 2023 (previously late August) and expect to complete by mid-October 2023 (previously early September).
How this will affect your organization:
This will impact all Teams users who attend and organize third-party meetings from Outlook.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
MC661224 — (Updated) Channel meeting invitation | Allow organizer to send a channel meeting invite to everyone in team
<30 Days
Microsoft 365 Roadmap ID 142405
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
Channel meeting invitations will now allow channel meeting organizers the ability to share invites on personal calendars of all channel members.
When this will happen:
Standard Release: We will begin rolling out in mid-September 2023 (previously late August) and expect completion by late October 2023 (previously late September).
How this will affect your organization:
Often, channel meetings get missed since users are not appropriately notified about them. With the added enhancement, meeting organizers can turn a toggle button on the scheduling form when scheduling a channel meeting. Once the toggle is turned on and meeting is saved, all channel members will be notified of the meeting on their main work calendar.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC649939 — (Updated) Join Microsoft Teams Meetings by a Meeting ID and Passcode – GCCH & DoD
>60 Days
Microsoft 365 Roadmap ID 94620
Updated September 7, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Teams users will soon be able to join meetings by Meeting ID. This release of Microsoft Teams Meeting ID will be rolling out across Microsoft Teams Desktop, Mobile and Web and will provide an additional way for users to join a Microsoft Teams meeting by entering a digital ID and Passcode.
When this will happen:
GCC-H: We will begin rolling out in mid-November 2023 (previously mid-September) and expect to complete rollout by late November 2023 (previously mid-October).
DoD: We will begin rolling out in late November 2023 (previously late October) and expect to complete rollout by early December 2023 (previously late November).
How this will affect your organization:
All meetings will have a Meeting ID and passcode that is automatically assigned to a Microsoft Teams user and added to the meeting invite under the meeting link. Meeting attendees can join the meeting by entering the Meeting ID. For all meeting attendees, the pre-join, lobby and security will remain the same.
- To join a meeting by ID in Outlook, you can find the meeting details section in the meeting invite in Outlook in the details for Meeting ID and Passcode. You can enter this Meeting ID and Passcode on the Teams app or the Website to join the meeting.
- To join a meeting by ID on Teams desktop, you can enter a Meeting ID and Passcode to join the meeting from the Calendar in the Teams app. You will see the option to join meeting by ID in the top right corner of the calendar.
- To join a meeting by ID from a Web Page, we are introducing a public web page where users can enter the Meeting ID and Passcode for any meeting to initiate a meeting join.
- To join a meeting by ID on mobile for both iOS and Android, you can enter a Meeting ID and Passcode using the meet icon in the top right corner of the Calendar in the Teams app.
What you need to do to prepare:
You may want to notify your users about this new capability to join meetings and update your training and documentation as appropriate. Meeting ID and Passcode can be used on the app and Teams website link to join a meeting. There will continue to be individual separate sections for existing Video conferencing ID and Dial in by Phone, which are independent of Meeting ID.
MC649917 — (Updated) Microsoft Teams: Stream Preview and Playback in Teams Chat and Channels
<30 Days
Microsoft 365 Roadmap ID 127596
Updated September 7, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can preview and play Stream videos directly in Teams Chat and Channel without having to open them in a browser and going to Stream.
When this will happen:
We will begin rolling out in late July 2023 and is expect to complete rollout by late October 2023 (previously late August).
How this will affect your organization:
Stream videos that are saved in OneDrive and SharePoint are now embedded in chat and channels enabling users to preview and play them directly in Teams without the need to open a browser window.
What you need to do to prepare:
There is nothing required from you at this time. You may want to notify your users and update any relevant training documentation as appropriate.
MC649047 — (Updated) Call delegation feature enhancements
<30 Days
Microsoft 365 Roadmap ID 123753
Updated September 19, 2023: We have updated the content below with additional resource information.
Call delegation feature enhancements -
Delivering a more tailored experience for delegates and delegators with a refreshed, simplified UI in the Calls app, and the ability for delegates and delegators to join active calls, if permitted.
When this will happen:
Standard Release: We will begin rolling out mid-August 2023 and expect to complete by late October 2023 (previously late September) for Teams Desktop and Teams Phone devices.
How this will affect your organization:
After this change users will notice a new UI experience for delegation, if permitted they will be able to join active calls on the delegator line.
What you can do to prepare:
If you use boss delegation in your tenant, you can review the permissions for delegates. Join active calls is OFF by default for delegates, delegators do not need permission to join active calls on their line.
Please ensure that your Teams phone devices are updated with the latest application from Teams Admin Centre to get access to the feature.
Review the following resources:
- Share a phone line with a delegate in Microsoft Teams
- Enhancements for Delegation in Teams Phone
- Get started with Microsoft Teams phones
- What's new in Microsoft Teams devices
MC642265 — (Updated) Cloud IntelliFrame: A New Way to See People in Teams Rooms
Rolled Out
Microsoft 365 Roadmap ID 130219
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience
Cloud IntelliFrame is a new experience that allows online meeting attendees to see people in Teams Rooms more clearly, enhancing the hybrid meeting experience by creating smart video feeds of in-room participants. The smart video feed is created by zooming into their faces and eliminating distractions. You can see the expressions and gestures of the people in the room more easily, which will help improve collaboration in hybrid meetings. It creates equity in hybrid meetings as everyone can be seen and heard.
Cloud IntelliFrame will be rolling out across Microsoft Teams Rooms on Windows with Pro license and can be viewed on Microsoft Teams Desktop (Windows & Mac) with any license.
When this will happen:
Standard Release: We will begin rolling out to commercial tenants in mid-August and expect to complete rollout by late September 2023 (previously early September).
GCC and GCCH will begin rollout by mid-August.
This experience is not available for DoD.
How this will affect your organization:
All Microsoft Teams Rooms on Windows with a Pro license equipped with cameras in the supported camera list will automatically opt-in to Cloud IntelliFrame. Online participants on Microsoft Teams Desktop (Windows and Mac) will see the IntelliFrame video feed by default from Rooms with these cameras.
An icon on the top right of the Room video feed indicates that Cloud IntelliFrame is being displayed.
People in the Room can disable IntelliFrame by using in-meeting settings on the console. This turns off IntelliFrame and switches back to standard view for the Room. All online attendees would then see the standard view from the respective Room.
People on Teams Desktop can also toggle IntelliFrame on/off by right clicking on the Room video tile and selecting ‘Turn off IntelliFrame’. This switches off the IntelliFrame view just on their Teams client.
The following camera models when deployed in a Microsoft Teams Room on Windows with a Pro license will automatically use Cloud IntelliFrame:
- AVer CAM520 Pro
- AVer CAM520 Pro2
- BRIO 4K Stream Edition
- EagleEye Cube USB
- HD Pro Webcam C920
- Jabra PanaCast
- Logi Rally Camera
- Logitech BRIO
- Logitech ConferenceCam CC3000e
- Logitech MeetUp
- Logitech Webcam C925e
- Logitech Webcam C930e
- Microsoft® LifeCam Studio
- Polycom EagleEye IV USB Camera
- PTZ Pro 2
- PTZ Pro Camera
- ThinkSmart Cam
- Yealink UVC30
- Yealink UVC34
- Yealink UVC50
- Yealink UVC80
- Yealink UVC86
What you need to do to prepare:
You may want to notify your users about this capability. Cloud IntelliFrame shows the smart feed when there are 9 or less people in the room. It automatically switches between the standard room view and IntelliFrame view based on in-room activity. For example, if someone enters the meeting room, the view would automatically switch to standard room view until the individual settles down.
Cloud IntelliFrame is ideal for focus rooms and medium spaces. Large spaces may not be ideal as people furthest from the camera may appear blurry after digital zoom. You may also want to switch off Cloud IntelliFrame in Rooms with glass walls without any privacy filter.
To switch off Cloud IntelliFrame in a room:
- Follow this guide to create an XML configuration file
- Add the following element: <CloudIntelliFrame>False</CloudIntelliFrame>
- Restart the console to process the configuration changes.
MC611685 — (Updated) Click Through Collaborative Annotations Layer in Teams Meetings
TBD
Microsoft 365 Roadmap ID 127900
Updated September 15, 2023: We are postponing the rollout of this feature at this time, and it will only be available in the new Teams experience. We apologize for any inconvenience.
We are rolling out an enhancement to the current Collaborative Annotations experience whereby screen sharers can click through the annotations layer and interact with underlying content without stopping the existing annotation session. After a sharer initiates annotations from their presenter toolbar, sharers will be able to interact with their background to edit their content by default.
When this will happen:
We will communicate via Message center when we are ready to proceed.
How this will affect your organization:
Click through is available on desktop (Windows and Mac) and web. When users share their screen in Teams meetings and select Start annotation in the presenter toolbar, they will see a new button, Interact with background, in Microsoft Whiteboard toolset which allows them to interact with underlying content without stopping the existing annotation session.
What you need to do to prepare:
No preparation is needed. You may want to update your training materials indicating that the feature is now supported.
MC579612 — (Updated) Admin Policy for Collaborative Annotations
<30 Days
This change is associated with Microsoft 365 Roadmap ID: 92502
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
With privacy and security restrictions, we have implemented a user-level IT admin policy for admins to choose whether some or all users in the company can use Collaborative Annotations. Currently, there is a way to turn Annotations ON or OFF through cmdlet Set-SPOTenant-IsWBFluidEnabled, this will also influence Whiteboard.
When this will happen:
We will begin rolling out in early August 2023 and expect to complete rollout by late October 2023 (previously late September).
How this will affect your organization:
IT admins will be able to turn ON or OFF Collaborative Annotations from the Teams admin center in Meetings --> Meeting policies.
What you need to do to prepare:
There is nothing you need to do to prepare.
MC579610 — (Updated) Microsoft Teams: Attach Cloud Files in Chat and Channel from Teams Mobile
<30 Days
Microsoft 365 Roadmap IDs 98321 and 98327
Updated September 12, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are introducing the capability to upload files from OneDrive from Teams Mobile chat and channel for iOS and Android. Additionally, users will be able to view Recent files and attach the most used files upfront from the Recent section.
When this will happen:
We will begin rolling out in late June 2023 and expect rollout to be complete by early October 2023 (previously early September).
How this will affect your organization:
To upload files, click on the '+' icon in any chat or channel message when composing and then click on the paperclip icon.
What you need to do to prepare:
There is no action required from you at this time. You may want to notify your users of this update.
MC578280 — (Updated) Animated Backgrounds in Teams Meetings
<30 Days
Microsoft 365 Roadmap ID 122513
Updated September 21, 2023: We have updated the timeline below. Thank you for your patience.
The animated background feature in Teams Meetings allows users to replace their existing background with a dynamic animation for a more immersive virtual environment. It offers various options to enhance meeting experience with creativity and personalization according to users' preferences. Currently, only pre-defined backgrounds from Microsoft are supported. Animated backgrounds are identified by the small video icon in the bottom-left corner of the preview picture.
When this will happen:
Targeted Release: We will begin rolling out in mid-June and expect to complete rollout by late June.
Public Preview: We will begin rolling out in mid-June and expect to complete rollout by late June.
Standard Release and GCC: We will begin rolling out in early July and expect to complete rollout by mid-September 2023 (previously late July).
GCC-High and DoD: We will begin rolling out in late September and expect to complete rollout by late October.
How this will affect your organization:
Users can go to the pre-join screen before the meeting start > Effects and Avatars > Video effects and select a new animated background. Animated backgrounds can be identified by the little video symbol in the bottom left corner of the preview picture.
Users can also change animated backgrounds when they start a meeting and go to More in meeting toolbar > Effects and Avatars > Select an animated background.
- Animated backgrounds are not available on low-end devices and require at least 8 GB RAM, CPU with 4 logical processors.
- Only pre-defined backgrounds from Microsoft are currently supported.
- Using more video filters might slow down background animation, in case of high machine workload.
What you need to do to prepare:
No preparation is needed. You may want to update your training materials indicating that animated backgrounds are now supported Teams meetings.
MC561700 — (Updated) Microsoft Teams: App Suggestions by Task in In-Context Stores
Rolled Out
Microsoft 365 Roadmap ID 122527
Updated September 12, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users think about which tasks they need to complete, such as creating a survey, inside Microsoft Teams. Soon, app suggestions will be organized by tasks that the apps support as opposed to conventional categories (productivity, project management). As a result, the new categorization will reduce the amount of time users need to spend learning about these apps – helping them to work more effectively.
When this will happen:
Standard: Rollout will begin in early November 2023 (previously mid-August) and is expected to be complete by late November 2023 (previously early August).
GCC: Rollout will begin in early November 2023 (previously mid-August) and is expected to be complete by late November 2023 (previously early August).
GCC High: Rollout will begin in early January 2024 (previously early August) and is expected to be complete by mid-January 2024 (previously late August).
How this will affect your organization:
The task-based app suggestions will be added to the Tabs, Messaging Extension, and Bots in-context Stores.
What you need to do to prepare:
There is no action required at this time. You may want to notify your users of this update.
MC561188 — (Updated) Microsoft Teams: Set your Work Hours and Location
30-60 Days
Microsoft 365 Roadmap ID 125375
Updated September 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
Set your work location for the day in Microsoft Teams so your team can learn about your availability for in-office and remote collaboration.
When this will happen:
Targeted Release and Preview: We have begun rollout and expect to complete rollout by late May.
Standard Release: We will begin rolling out in early June 2023 and expect to complete rollout by early November 2023 (previously late August).
How this will affect your organization:
We are highlighting Microsoft 365 features that will bring transparency and focus on where you and your colleagues are working: work hours and location. These features will appear in Outlook on the web and Teams and bring the flexibility of enabling users to share where they are working. You’re already accustomed to managing and sharing your schedule in Outlook and Teams. With these additional features, Microsoft 365 is now location-aware – giving more information to you and colleagues to work better together.
Microsoft 365 already helps you manage and share your work schedule and availability. The work hours and location features allow you to specify more details about your work schedule and preferences, like from where you’re working (remotely or in office) and whether you work different hours on different days.
Teams gives you the flexibility to easily change the location for that day, without impacting the rest of your week. For example, after a few hours in the office, you decide to finish up your work from home. To change your location from Teams, simply click on your profile on the top right corner of the Teams window, view your account settings menu and change your work location for that day.
You can also update your location from any device with Teams. If you want to quickly look up where someone is working from, you can view their location in their profile card next to their availability.
What you need to do to prepare:
There is no action required from you at this time. You may want to notify your users of this update.
MC559256 — (Updated) Microsoft Teams: Hotline Phones (Private Line Automatic Ringdown)
>60 Days
Microsoft 365 Roadmap ID 123749
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
You are receiving this message because our reporting indicates that you are using Teams Phone devices in your organization. We are pleased to announce that soon you will be able to program Microsoft Teams certified phone devices to directly dial a pre-configured phone number or contact, such as emergency services or help desk number in your organization. The hotline phone can be set up directly through the device settings or the Teams Admin Center. The feature will be available on common area phone accounts with Teams Shared Device license.
When this will happen:
- Commercial and GCC rollout is expected to start in late July and should be complete by end of August. - Complete
- GCCH rollout is expected to start in late August and be completed by early November 2023 (previously late September).
- DoD rollout is expected to start in early December and be completed by early January.
What you need to do to prepare:
Please ensure that your Teams phone devices are updated with the latest application from the Teams Admin Center to get access to the feature.
MC554158 — (Updated) A new experience to search within chat and channels.
>60 Days
Microsoft 365 Roadmap ID 122550
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are excited to introduce a new and improved experience to search within chats and channels.
When this will happen:
- Standard: We will begin rolling this out in early October 2023 (previously mid-September) and expect to complete rollout by late October 2023 (previously late September)
- GCC: We will begin rolling this out in mid-October 2023 (previously late September) and complete rollout by late October 2023 (previously late August).
- GCC-H: We will begin rolling this out in late October 2023 (previously late August) and complete rollout by early November 2023 (previously early September).
- DoD: We will begin rolling this out in mid-November 2023 (previously mid-September) and complete rollout by early December 2023 (previously early October).
How this will affect your organization:
A few key enhancements include:
- The new in-chat and in-channel Search experience will now be available in the right handrail, making it possible to see your chat/channel list and your new search results in one single view. The initiation can be done using the keyboard shortcut Ctrl+F(win) or Cmd +F (Mac):
- Note: Search capability on the new Channels experience is currently available on the main view, and we will extend it to the conversation view very soon.
- In addition to the keyboard shortcut, a dedicated button ‘Find in Channel’, placed on the channel info pane can be used to initiate contextual search:
- We now have introduced enhanced captioning and keyword highlighting to aid the discernment of results in chat and channel:
- In-chat search will now also be available in pop-out chats.
MC550081 — (Updated) Microsoft Teams: New Channels Experience
30-60 Days
Microsoft 365 Roadmap ID 91683
Updated October 2, 2023: We have updated the content below with additional information. Thank you for your patience.
A new channels experience in Microsoft Teams has been built with an intuitive design that allows teams to focus and stay on tasks, bring everyone up to speed, and actively engage in real-time. The following features will be rolling out:
- The compose box and recent posts will appear at the bottom (previously top) of the channel by default. Users can configure channels to show new posts at the top via the more options ... menu the top of the channel. It'll now be much easier to start a new post, keep up with the latest conversations and participate - giving users the confidence that they’ve not missed anything.
- Every post is now a true conversation that users can focus on. Users can navigate to a conversation view that makes the discussion more engaging and synchronous, just like a chat. Users can also pop out the post, keep an eye on the discussion, while continuing to work on other topics.
- A streamlined information pane will include all the important contextual information like channel’s members and pinned posts so new team members can quickly on-board and for all members to find the information they need, right in the channel.
- Pin posts to make it easy for everyone to know what’s important in the channel and quickly reference it.
- Simplified badging is making it easier for users to understand when there are new unread activities in teams. In addition, the simplified design helps users focus on the specific channels which requires the most attention, like channels in which the user was @mentioned.
When this will happen:
Targeted Release: Started rolling out in May and is expected to complete in late August 2023 (previously early July). Complete
Standard and GCC: We will begin rollout in early October 2023 (previously mid-September) and expect to complete rollout by late October 2023 (previously mid-August).
GCC-H: We will begin rollout in late October 2023 (previously mid-August) and expect to complete rollout by mid-November 2023 (previously mid-September).
DoD: We will begin rolling out in early November 2023 and expect to complete rollout by mid-November 2023.
How this will affect your organization:
Users in your organization will not need to make any changes and will get the new channels experience by default.
What you need to do to prepare:
Admins will not need to make any changes.
MC549348 — (Updated) Webinar Email feature updates -customize content and time to send reminders
<30 Days
Microsoft 365 Roadmap ID 119391
Updated September 27, 2023: We have updated the rollout timeline below. Thank you for your patience.
Emails for Webinars are critical to engage with registrants and often organizers feel the need to customize the content. To enable this, we are rolling out two features.
- The content of the emails (i.e. all webinar related attendee emails) can be edited by the event organizers. This is reserved for Teams Premium licensed organizers.
- Time to send reminder emails can be configured by the event organizers. This is reserved for Teams Premium licensed organizers.
When this will happen:
Standard Release: rollout will start in mid-July and expected to be completed by end of July.
GCC: rollout will start in mid-October and expected to be completed by late October.
How this will affect your organization:
Email customization is governed by IT admin policy to enable admins to restrict organizers with Teams Premium license from being able to edit the content of the emails. This setting is available in Teams Events policy. Set-CsTeamsEventsPolicy
What you need to do to prepare:
Both these features are reserved for users that have a Teams Premium license. The policy to customize content is enabled by default in commercial SKU.
MC545913 — (Updated) We will stop honoring Caller ID policies using Service calling line ID substitution
<30 Days
Updated September 12, 2023: We have updated this message to ensure visibility to all impacted organizations.
This is the second phase of the retirement of using Service calling line ID substitution in Caller ID policies. The first phase was announced in MC505122 at the end of January 2023.
We will stop honoring the use of Service calling line ID substitution in Caller ID policies when outbound calls are made. We will also remove using Service calling line ID substitution from the Teams admin center and in the New/Set-CsCallingLineIdentity cmdlet in the Teams PowerShell Module.
Customers are required to use the Resource calling line ID substitution.
When this will happen:
The change will be rolling out in late September 2023 and expect to complete by mid-October 2023.
How this will affect your organization:
You are receiving this message because our reporting indicates that your organization are using Caller ID policies using Service calling line ID substitution.
When this change is implemented, Caller ID policies using Service calling line ID substitution will no longer be honored and the outbound call will not have any caller ID substitution. We will still honor other settings on a Caller ID policy using Service calling line ID substitution. We will also remove using Service calling line ID substitution from the Teams admin center and in the New/Set-CsCallingLineIdentity cmdlet in the Teams PowerShell Module.
Your administrators will need to use the Resource calling line ID substitution. This type of substitution uses the phone number of a resource account associated to an Auto Attendant or Call Queue and it supports both Calling Plan, Direct Routing and Operator Connect phone numbers.
What you need to do to prepare:
You should change any existing caller ID policies using Service calling line ID substitution to using Resource calling line ID substitution.
Please review the following resources:
MC525143 — (Updated) Microsoft Teams: Video Clip Feature in Teams for Government Clouds
Rolled Out
Microsoft 365 Roadmap ID 114155
Updated September 27, 2023: We have updated the rollout timeline below. Thank you for your patience.
Video Clips are a new way of working and connecting with coworkers using short video in Microsoft Teams. Users can record, send, and playback video messages in chats on all Teams endpoints. Recording limited to 1min across all platforms.
When this will happen:
GCC: We will start rolling out in mid-March and complete rollout by late March. - Complete
GCC-H: We will begin rolling out in early June (previously mid-Apr) and complete rollout by mid-August 2023 (previously mid-June). - Complete
DoD: We will begin rolling out in mid-June (previously mid-May) and complete rollout by late September 2023 (previously mid-July).
How this will affect your organization:
Teams users will soon be able to record, send and playback video messages in 1:1 and group chats with the Video Clips feature. Recording time will be limited to one minute across all platforms. This feature will be enabled automatically for users, however, Admins can disable this feature via the Teams Admin center.
What you need to do to prepare:
There is no action required from you at this time. For additional information on messaging policies, please visit this documentation. You may want to notify your users of this change and update any relevant training documentation as appropriate.
MC523053 — (Updated) Microsoft Teams: Explicit Recording Consent for Teams Meetings
<30 Days
Microsoft 365 Roadmap ID 107781
Updated September 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Teams is going to support an Explicit Recording Consent meeting policy. When the policy is applied, the Teams meeting window will request explicit consent of all participants to be recorded. Before a user gives consent, the user’s audio, video, and screenshare/consent-share won’t be captured in the meeting recording.
When this will happen:
Standard and GCC: We will begin rolling out in late March and expect to complete rollout by mid-April. - Complete
GCC-High: We will begin rolling out in late May (previously late April) and expect to complete rollout by mid-June (previously early May). - Complete
DoD: We will begin rolling out in mid-October 2023 (previously mid-September) and expect to complete rollout by late October 2023 (previously late September).
How this will affect your organization:
Explicit Recording Consent is OFF by default and is an IT admin policy-controlled feature. Admins can choose to enable the feature either for the entire tenant or for specific individuals based on their business needs.
When the policy is applied, Teams meetings set up by these individuals will request explicit consent from all participants to be recorded.
Before a user gives consent, their audio, video, and screenshare/content-share will be disabled during the meeting. This will prevent their audio, video, and screenshare/content-share from being recorded.
Participants' consent is logged and can be accessed as part of the Attendance Report.
What you need to do to prepare:
You may want to update your training materials indicating that this policy is now supported.
Admins can use PowerShell to enable or disable this feature using the following examples, and the Teams Admin Center will soon support the policy setting as well.
- Set CsTeamsMeetingPolicy -Identity Global -ExplicitRecordingConsent "Enabled"
- Set CsTeamsMeetingPolicy -Identity Global -ExplicitRecordingConsent "Disabled"
Please keep in mind of the following dependencies and limits when deciding to enable the feature:
- The feature relies on Attendance Report; for customers who have disabled the Attendance Report, end users will not be able to enable their mic, camera, or screensharing/content-sharing when a recording is started. If you are unable to enable Attendance Report, we recommend waiting for a future update.
- To avoid disruptions for end-users, they should be using the most recent version of Teams.
- In meetings requiring explicit consent, users joining from unsupported endpoints, such as older client versions and CarPlay, will not be able to enable their mic, camera, or screenshare/content-sharing during recording.
- Teams meeting rooms user and PSTN users can still get recording notifications as of today, but they cannot provide explicit recording consent, and their consent data will be logged as "not applicable" or "auto consent".
MC513664 — (Updated) Suggested Files in 1:1 Chats
>60 Days
Microsoft 365 Roadmap ID 95065
Updated September 12, 2023: We apologize for the delay on providing an update for this release. We have updated the rollout timeline below for Standard release. Additionally, we won't be moving forward with rolling this out to Government organizations at this time. Thank you for your patience.
As an extension of Suggested Replies in 1:1 chats, you can now easily save time when you need to send a file in a chat by tapping on a "Share file" suggestion.
When this will happen:
Standard Release: We will begin rolling this out late November 2023 (previously early July) and expect to complete by mid-December 2023.
Government Clouds: We will not be rolling this feature out at this time. We will communicate via Message center when we are ready to proceed.
How this will affect your organization:
Once available, users will be able to tap on a "Share file" action in chat whenever intent is detected to send a file.
What you need to do to prepare:
This feature ships default on; review Manage messaging policies in Teams.
If you wish to disable this feature in your tenant, please disable the Suggested Replies setting that is found in Messaging Policies.
Users also have a setting within the app so they can disable the feature.
MC513049 — (Updated) Video Closed Caption in PowerPoint Live
<30 Days
Microsoft 365 Roadmap ID 114494
Updated October 3, 2023: We have updated the rollout timeline below. Thank you for your patience.
Closed captions will soon be supported for embedded videos in PowerPoint Live for Teams. Video closed captions in PowerPoint Live will be rolling out across Microsoft Teams Desktop and Web and will allow PowerPoint Live users to create accessible presentations that include video.
When this will happen:
We will begin rolling out to PowerPoint Live users in early-March and expect to complete rollout by mid-March.
GCC, GCC-High and DoD: We have begun rolling out and will complete by late October 2023 (previously late September).
How this will affect your organization:
When creating a PowerPoint presentation in PowerPoint for Windows or PowerPoint for Mac, users have the option to include a closed captions file with their video (as shown below).
When the presentation is shared via PowerPoint Live for Teams, any embedded video that includes closed captions stored in a separate file will automatically include the option for attendees to turn on closed captions.
What you need to do to prepare:
To prepare for this change, you may want to notify your users about the new support for video closed captions in PowerPoint Live for Teams, update your training and documentation as appropriate, and encourage your users to make their PowerPoint presentations more accessible by adding closed captions for their embedded videos.
MC496629 — (Updated) Changes coming to how dialed phone numbers are matched to users – GCCH & DoD
<30 Days
Updated September 27, 2023: We are updating this message as a reminder of this change, which has started rolling out. Thank you for your patience.
Microsoft will be changing how numbers dialed by Teams users or arriving from the PSTN match the number assigned to users. This process is often referred to as Reverse Number Lookup (RNL).
The change applies to users with an assigned phone number with an extension using the following formats:
- Where the last several digits of the base number are also added as the extension. For example, +14025557334;ext=334, where 334 is both included in the base number and as the extension.
- Where both the base number and extension are unique for each user. For example, +14025557253;ext=3111 and +14025556567;ext=3112
- Where the base number is common, and the extension is unique for each user. For example, +14025557000;ext=111 and +14025557000;ext=112
The users configured with this type of phone number are either Teams users or Skype for Business Server on-premises users.
This may be a breaking change if your Teams dial plans and Direct Routing Session Border Controllers are not configured to convert dialed numbers into the full number assigned to the user including the extension.
When this will happen:
We will begin rolling out this change in mid-September (previously early July) and will be complete by late October (previously mid-August).
How this will affect your organization:
You might be impacted by the change, if you have users configured with phone numbers with extensions.
Today, when a call is made to a phone number, the lookup to see if that number is assigned to a specific user works as follows:
- if a call is made to +14025557334;ext=334, we will find the user configured with the phone number +14025557334;ext=334
- if a call is made to +14025557334, and there is no user configured with +14025557334, we will find the user configured with the phone number +14025557334;ext=334.
This can be an issue in situations where the same base number is used for multiple users. For example:
- User Alice is assigned +14025557000;ext=111
- User John is assigned +14025557000;ext=112
If a call is made to +14025557000, and there is no user configured with +14025557000, we would match to the first user found with +14025557000 as a base number (Alice in this case).
Based on customer feedback, we are changing the matching logic to be an exact string match between the called number and the full phone number configured for a user.
After the change, in the above examples, we will not find a user configured with the phone number +14025557334, +14025557253 or +14025557000 and calls to those number will not match to a user instead of potentially being routed to the wrong person.
What you need to do to prepare:
If you have users configured with phone numbers with the extensions, to prevent calls not being matched to the intended user, please ensure that dialed numbers from Teams users and incoming PSTN calls are formatted to exactly match the full phone number configured on the user accounts.
Check that your tenant dial plans include normalization rules that can translate abbreviated dial strings to the full phone number configured on users. In example above, the following phone number normalization rule will translate a dialed 3-digit number to the full phone number configured on the users to ensure calls will succeed:
- Pattern ^(\d{3})$ and Translation +14025557$1;ext=$1
Check that any phone number manipulation/translation rules used on your Direct Routing Session Border Controller are capable of making the translation to the full phone number configured on your users.
For more information, see:
Microsoft Intune
MC677834 — Updates to Offline Search in Outlook Mobile on iOS
<30 Days
Microsoft 365 Roadmap ID 153121
Outlook Mobile in iOS now supports offline search capabilities, even for organizations where admins have disabled Apple's Spotlight capability using Intune. While these capabilities are limited to keyword searching (for now), it unblocks users from finding critical information even when they're offline.
When this will happen:
Standard Release: This is currently rolling out and expected to complete by late October 2023.
How this will affect your organization:
If admins in your organization have disabled Apple's Spotlight capability for iOS users (using Intune), it meant that offline search in Outlook Mobile iOS was not available to users impacted by this disablement. This limitation is now lifted, and such users would be able to use offline search. However, this experience is limited and has the following caveats:
- Keyword search works as expected.
- Clicking on a people suggestion does not work and would not display results correctly.
- Using filters (like "Has Attachments") while searching would not work in offline mode.
We're working to further improve our offline search capabilities, add address these known limitations in the future.
What you need to do to prepare:
No admin preparation is needed, this update will be automatically rolled out. Users would need to update their applications to version 4.2328.0 or later to avail this feature.
What you need to do to prepare:
Review the information above and notify your admins and users about the upcoming maintenance and functionality that may be impacted. We will post another message 5 days before this maintenance.
MC675140 — Reminder: Update to the latest Intune App SDK and Intune App Wrapper for iOS to support iOS/iPadOS 17
Rolled Out
To support the upcoming release of iOS/iPadOS 17, update to the latest versions of the Intune App SDK and the App Wrapping Tool for iOS to ensure applications stay secure and run smoothly. For more details see the blog: https://aka.ms/Intune/iOS17-MAM-SDK
Important: If you do not update to version version 17.6.1 or above, you may run the risk of app protection policies not applying to your app.
Organizations using the Conditional Access grant “Require app protection policy” must upgrade their iOS/iPadOS apps to the latest version prior to upgrading to iOS/iPadOS 17 to ensure applications continue to stay secure and maintain access to Conditional Access protected services. Intune will soon report any applications with App SDK versions earlier than 17.6.1 on iOS/iPadOS 17 and later as non-compliant to Conditional Access.
Note: There have been several service change notices to prepare for iOS/iPadOS 17, including MC666161, MC578235, and MC665217. Please review all of your service change notices to prepare for Apple's latest service release.
How this will affect your organization:
For organizations using the Conditional Access grant “Require app protection policy”, if users do not upgrade their apps to the latest version prior to upgrading to iOS 17, the app will fail the “Require app protection policy” Conditional Access check, and these apps will be unable to connect services such as Microsoft 365.
User Impact: Users will need to upgrade their app to maintain access to company data protected by Conditional Access. If they do not upgrade their app, they will need to do so to restore access to these services.
What you need to do to prepare:
If you choose to build or wrap apps targeting iOS 17, you must upgrade to at least version 17.6.1 of the Intune App SDK and Intune App Wrapping Tool for iOS. Here are the public repositories:
Notify your users as applicable, to ensure they upgrade their apps to the latest version prior to upgrading to iOS 17. You can review the Intune App iOS SDK version in use by your users in the Microsoft Intune admin center by navigating to Apps > Monitor > App protection status, then review “Platform version” and “iOS SDK version”. Review applications with iOS SDK version less than 17.6.1.
MC674247 — Microsoft Intune ending support for Android device administrator on devices with GMS access in August 2024
Rolled Out
Google has deprecated Android device administrator management, continues to remove management capabilities, and no longer provides fixes or improvements. Due to these changes, Intune will be ending support for Android device administrator management on devices with access to Google Mobile Services (GMS) beginning August 30, 2024. Until that time, we will support device administrator management on devices running Android 14 and earlier. For more details, read the blog: https://aka.ms/Intune-Android-DA-blog.
How this will affect your organization:
After Intune ends support for Android device administrator, devices with access to GMS will be impacted in the following ways:
- Users will not be able to enroll devices with Android device administrator.
- Intune will not make changes or updates to Android device administrator management, such as bug fixes, security fixes, or fixes to address changes in new Android versions.
- Intune technical support will no longer support these devices.
What you need to do to prepare:
Stop enrolling devices into Android device administrator and migrate impacted devices to other management methods. You can check your Intune reporting to see which devices or users may be affected. Go to Devices > All devices and filter the OS column to Android (device administrator) to see the list of devices.
Read the blog, Microsoft Intune ending support for Android device administrator on devices with GMS in August 2024, for our recommended alternative Android device management methods and information about the impact to devices without access to GMS.
MC674246 — Plan for Change: Removal of Microsoft Graph Beta API Android LOB app properties ‘identityVersion’ and ‘identityName’
<30 Days
With Intune’s October (2310) service release, we will be removing the Android line-of-business (LOB) app properties “identityVersion” and “identityName” from the Microsoft Graph Beta API managedAndroidLobApp resource type. The same data can be found using the Graph API "versionCode” and “versionName” properties.
How this will affect your organization:
If you have automation or reporting using the Android LOB app properties “identityVersion” and “identityName”, you will need update to the “versionName” and “versionCode” properties for the Graph call to continue working.
What you need to do to prepare:
Update your documentation and reporting as needed.
MC650410 — (Updated) Update devices to renew enrollment certificates
>60 Days
Updated October 4, 2023: This change is planned to begin in the first half of 2024; however, devices should be updated as soon as possible.
Previously communicated in MC551013, devices enrolled in Intune will require the following updates to ensure certificate renewal continues to work as expected:
- Windows: Install the January 2023 or newer cumulative update on supported versions of Windows 10 and Windows 11 (KB5019275).
- Android: For the following enrollment methods, devices will need to update to the latest Company Portal version (minimum v5.0.5800):
- Android Enterprise personally owned devices with a work profile
- Android device administrator
- iOS/iPadOS: For devices enrolled with Apple User Enrollment, update operating system to 16.2 or later. Once updated, we recommend users initiating a sync from the Company Portal to ensure the device is online and unlocked. Note: This is not a change to the minimum supported iOS/iPadOS versions in Intune. Devices can continue to enroll on supported versions.
We will begin rolling out this change for Windows and iOS/iPadOS devices on February 15, 2024. For Android devices, this is expected to begin on April 1, 2024.
How this affects my organization:
Our telemetry indicates you have at least one device that has not met these requirements and could be impacted if the certificate expires after this change.
User impact: If devices do not meet these requirements, they might be unable to renew their enrollment certificates and users will lose access to your organization’s resources. Users would then need to re-enroll.
What you need to do to prepare:
Notify your users to update their device based on the requirements above. You can check which devices have expired certificates by using this PowerShell script: Managed Device Certificate Expiry Report
Microsoft Entra
MC678069 — Migrate to the Authentication methods policy in Azure Active Directory by September 30, 2025
>365 Days
On September 30th, 2025 we will be retiring the ability to manage authentication methods in the legacy Multifactor Authentication (MFA) and Self-Service Password Reset (SSPR) policies in Entra ID. Organizations should migrate their methods to the converged authentication methods policy where methods can be managed centrally for all authentication scenarios including passwordless, multi-factor authentication and self-service password reset.
When this will happen:
Note: The date, September 30th, 2025, is an update from the previously communicated retirement date of September 30th, 2024.
What you can do to prepare:
Organizations can migrate their authentication methods manually by following the steps outlined in: How to migrate MFA and SSPR policy settings to the Authentication methods policy for Azure AD.
MC650420 — (Updated) Changes to the registration campaign feature in Microsoft Entra (previously Azure Active Directory)
<30 Days
Updated September 18, 2023: Deployment will begin September 25th and will run to October 20th. These dates replace the dates mentioned in the email "We're enabling a stronger form of multifactor authentication beginning September 15, 2023" that you might have received. We apologize for the inconvenience.
Publicly switched telephone networks (PSTN) such as SMS and voice authentication are the weakest for.... To help your users move away from these less secure MFA methods we are introducing changes to the Microsoft managed state of the registration campaign (aka Nudge) feature in Microsoft Entra (previously Azure Active Directory).
When this will happen:
Starting late September 2023 and expect to complete by late October 2023.
How this affects your organization:
Users in your organization who are relying on PSTN (SMS and/or voice) for MFA will be prompted to use the Microsoft Authenticator app. Users can skip this prompt for a maximum of 3 times, after which registration of the app will be required by default. Note: admins can decide it they want to opt out of the “limited” 3 snooze configuration or give their end users the ability to snooze indefinitely.
What you can do to prepare:
We urge you to motivate your users to immediately stop using SMS and voice for MFA. You can take advantage of several new admin levers to achieve this such as system-preferred MFA and Microsoft Authenticator Lite, in addition to registration campaign. However, if some of your users require more time you can exempt them for now. Sign in as Global Administrator or Authentication Policy Administrator and go to Microsoft Entra > Identity > Protection > Authentication methods > Registration campaign and exclude these user groups.
Stay alert, stay secure!
Microsoft Identity & Network access (IDNA) product group
MC611686 — (Updated) Introducing Voice One Time Password (OTP)
<30 Days
Updated September 20, 2023: We have updated the rollout timeline below. Thank you for your patience.
Voice calls have proved to be the least secure authentication method; there are far better ways of performing multifactor authentication (MFA), including Microsoft Authenticator (which offers both MFA and Passwordless options), or more secure phishing-resistant methods like Windows Hello for Business and FIDO2 security keys. Although we have encouraged everyone to move away from traditional MFA methods (such as SMS and voice), we understand that some of you are dependent on these methods in order to use MFA. To address this need, we are making an improved version of our voice call method available - introducing “voice one-time password (OTP)”. This method will be combined with the SMS authentication method and as such have two delivery methods (SMS and voice OTP) to allow for delivery method optimization.
When this will happen:
Starting September 2023 and completing late October 2023.
How this affects your organization:
Users in your organization who rely on SMS will have this new optimized channel.
What you can do to prepare:
We encourage you to keep recommending users to use the Microsoft Authenticator app to get an even better user experience.
Microsoft Purview
MC679028 — Microsoft Purview Insider Risk Management: Public preview of SharePoint site selection enhancement
<30 Days
Microsoft 365 Roadmap ID 169880
Coming soon, Microsoft Purview Insider Risk Management will be rolling out public preview of SharePoint site selection enhancement.
When this will happen:
Preview: This is currently rolling out and expected to be complete by early October.
How this will affect your organization:
With this update, Insider Risk Management admins can add any SharePoint sites as priority content or exclude certain SharePoint sites in Insider Risk Management policies by searching the site names or using the exact URLs.
What you need to do to prepare:
You can add SharePoint sites to exclusion at insider risk settings > intelligent detections.
You can add SharePoint sites to priority content at Policies > create/ edit policy.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can access the Insider Risk Management solution in the Microsoft Purview compliance portal.
Learn more: Learn about insider risk management settings | Microsoft Learn
MC678065 — Microsoft Purview compliance portal: Information Protection - New cmdlet for Content Explorer
30-60 Days
Microsoft 365 Roadmap ID 117531
The Content explorer Export feature has a limitation of exporting data only after drill down to specific location. This feature is now available in Public Preview and allows admins to use a new cmdlet within the Security & Compliance PowerShell, Export-ContentExplorerData, to export all rows of data for the content that are scanned and shown on the Content Explorer.
When this will happen:
This feature will begin rolling out mid-October and expect to complete by mid-November.
How this will affect your organization:
This feature can be accessed through the Security & Compliance PowerShell, Export-ContentExplorerData.
What you need to do to prepare:
There are no additional settings needed for this feature.
Get started with content explorer | Microsoft Learn
MC677832 — Microsoft Information Protection: Microsoft Purview: EDM test function will return both the base SIT and EDM SIT results
<30 Days
Microsoft 365 Roadmap ID 169088
When using the test function in the Compliance portal or in PowerShell to test Exact Data Match (EDM) matches, the resulting EDM matches will be returned along with matches for the Sensitive Information Types (SITs) configured as EDM primary elements to help admins troubleshoot when EDM is not returning expected matches.
With this new capability, you can understand that:
- EDM won’t match if there is no base SIT detected (no EDM lookup occurs when no primary elements in the EDM SIT are detected in the content).
- EDM won’t match if the base SITs detected (and surfaced in the test cmdlet) in the content don’t match what was hashed and uploaded.
With this release, we are also adding the ability to test the EDM SIT from the EDM UI (New EDM experience only) – the test button will be accessible in the overlay that is displayed when clicking on the EDM SIT in the EDM UI.
When this will happen:
Rollout will begin in late September and is expected to be complete by late October.
How this will affect your organization:
Customers may find it easier to understand why an EDM SIT is not matching expected content.
What you need to do to prepare:
No advanced preparation is required – the test function will automatically recognize an EDM SIT from other SITs and display both the EDM SIT matches as well as the primary element(s) matches.
Test an exact data match sensitive information type | Microsoft Learn
MC677825 — Data Loss Prevention - Download File Evidence for DLP Investigations
30-60 Days
Microsoft 365 Roadmap ID 167340
We are announcing a new feature in GCC, GCC-H, DoD GA which provides DLP investigators the option to download the full file from SharePoint and/or OneDrive for Business that resulted in a DLP policy match as evidence for DLP Alerts in Microsoft Purview compliance portal and Microsoft 365 Defender portal.
When this will happen:
Rollout will begin in the end of October and is expected to be complete by early November.
How this will affect your organization:
To download the SharePoint or OneDrive for Business file that resulted in a DLP alert or incident for, Navigate to Alerts details tab in the Microsoft Purview compliance portal or Microsoft 365 Defender portal, select the alert, click on the Actions menu, and then click “Download.”
If you choose to not use this download feature, there is no impact to your organization.
What you need to do to prepare:
There is nothing you need to do prepare, the download option will be available in the DLP alerts experience in both Microsoft Purview compliance portal and Microsoft 365 Defender portal.
MC677514 — Microsoft Purview Endpoint Data Loss Prevention: Protect sensitive text when it is pasted through Web forms
<30 Days
Microsoft 365 Roadmap ID 169079
Microsoft Purview Data Loss Prevention that can help organizations create policies that prevent their users from pasting sensitive data to specific websites, including personal email, generative AI prompts, social media sites and more when accessed through a supported web browser.
When this will happen:
Rollout will begin in late September and is expected to be complete by early October.
How this will affect your organization:
With this new capability, Microsoft Purview DLP is now providing content-based protection, where no matter what the source of the sensitive data is (file, databases, or sensitive sites), when the user tries to paste sensitive data from the source to a website on a supported browser, the DLP engine is able to inspect the data, assess its sensitivity, and apply the appropriate restrictions.
What you need to do to prepare:
This feature will only work on onboarded machines with Antimalware Client Version is 4.18.23080 or higher.
Learn more: Stay informed about DLP.
MC677235 — Role Based Access Control (RBAC) Granular Scoping for Microsoft Purview Audit
<30 Days
Microsoft 365 Roadmap ID 163961
We are introducing role-based details to Microsoft Purview Audit search results to enable you to delegate granular permissions to users and analysts.
When this will happen:
Rollout will begin in early October and is expected to be complete by late October.
How this will affect your organization:
IT departments in large organizations are built in a way that some of the day-to-day tasks are delegated to specific people or roles in the organization following the industry standard of least privilege access. Admins have a need to delegate role-based permissions to users or analysts in a granular way. In some cases, this delegation is based on function, and in other cases it is based on geography or scope of work.
In this release, Audit will provide role-based information with Audit search results through the Microsoft Purview compliance portal user interface.
What you need to do to prepare:
No action is needed to enable this feature. To get started with the Audit solution in the Microsoft Purview compliance portal, please visit this....
Learn more: Microsoft Purview auditing solutions
MC676123 — Audit Activities - Operation Search Bar
Rolled Out
The Audit Custom Activities Search enables customers to search for specific operations in the audit log. Instead of having to use PowerShell queries to search for a specific activity or select from the events in the Activities drop-down menu, admins can use the custom search bar to search for several audit log events directly.
Microsoft 365 Roadmap ID 124913
When this will happen:
This is currently rolling out and is expected to be complete by late September 2023.
How this will affect your organization:
This update will enable a new search bar that admins can use when conducting searches in the audit log workflow to search specific operations. Operation names must be entered exactly as they are named to return results. Comma-separated values are accepted.
What you need to do to prepare:
More information on how to use this feature can be found in the documentation here: Audit New Search | Microsoft Learn
MC675959 — Microsoft Information Protection: Microsoft Purview: Exact Data Match to support multi-token corroborative evidence.
30-60 Days
Microsoft 365 Roadmap ID 124847
Updated September 27, 2023: We have updated the rollout timeline below. Thank you for your patience.
Exact Data Match (EDM) will support string match detection of multi-token (i.e., fields with multiple words separated by spaces or punctuation) corroborative evidence without requiring mapping Sensitive Information Types (SITs) to multi-token corroborative evidence fields.
When this will happen:
Rollout will begin in late October 2023 (previously late September) and is expected to be complete by mid-November 2023 (previously mid-October).
How this will affect your organization:
With this release, multi-token corroborative evidence can be detected as a string match, without requiring it to be mapped to a Sensitive Information Type (SIT) that is able to detect that content as a single entity, which may result in more accurate EDM detection.
In some cases, it may still make sense to map a SIT to a corroborative evidence field, both to reduce latency by limiting the amount of content that needs to be compared for each match, and to eliminate some potential false positives. For example, if you have indicated multiple characters as ignored delimiters using configurable match, but still want to only detect matches on strings which are formatted with some of the delimiters or where multiple delimiters match each other.
In general, if a SIT can be accurately matched to a corroborative evidence column, it is preferred to do so rather than to rely on automatic single-word or multi-token matching.
What you need to do to prepare:
To use this feature, you need to opt-in for multi-token support for each corroborative evidence field that you want enabled. You can do this either through the new EDM UI experience (see screenshot above) or through a schema XML file update. Before doing so, you will need to first uninstall your current version of the EDM Upload Agent and download / install the latest version from: https://learn.microsoft.com/en-us/purview/sit-get-started-exact-data-match-hash-upload#links-to-edm-....
Once this feature has been released, additional details will be found in our EDM public documentation:
Learn about exact data match based sensitive information types | Microsoft Learn
MC675502 — Microsoft Purview Insider Risk Management: General availability of static alert and case IDs
<30 Days
Microsoft 365 Roadmap ID 124777, 139455
Insider Risk Management will provide static alert and case IDs to help admins track and communicate investigation progress with colleagues more easily.
When this will happen:
Rollout will begin in late September and is expected to be complete by early October.
How this will affect your organization:
No impact
What you need to do to prepare:
No action is needed to enable these features. You can find the new features for alert and case on the alert and case pages in Insider Risk Management.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies to manage security and compliance. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
Admin link: You can access the Insider Risk Management solution in the Microsoft Purview compliance portal.
Other Links: Learn more: Learn about insider risk management | Microsoft Learn
MC674425 — eDiscovery (Premium): Enhancements for Teams meeting recordings
Rolled Out
Microsoft 365 Roadmap ID 117385
Coming soon to public preview, we're rolling out enhancements to Teams meeting recording and video files stored in OneDrive and SharePoint to improve management within eDiscovery workflows.
When this will happen:
Rollout will begin at the end of August and is expected to be complete by end of September 2023.
How this will affect your organization:
This update enables collection and review of metadata associated with Teams meeting recordings and video files stored in OneDrive and SharePoint including transcripts/captions, chapters, and custom thumbnails.
What you need to do to prepare:
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal.
Learn more: Conduct an eDiscovery investigation of content in Microsoft Teams
Conduct an eDiscovery investigation of content in Microsoft Teams
MC673976 — Label footers enhancement for emails
Rolled Out
Microsoft 365 Roadmap ID 124817
Coming soon to Microsoft Purview Information Protection, we're updating the configuration of email footers generated by sensitivity labels.
When this will happen:
Rollout will begin in early September and is expected to be complete by late September.
How this will affect your organization:
In Microsoft Purview compliance portal today, when an administrator configures content marking for Information Protection sensitivity labels to add a footer, the footer will accumulate at the very bottom of email chains. This is especially undesirable for long email threads, because the footer can be missed or not seen by end users. The new enhancement that we’re delivering will now add the footer at the bottom of the most recent email reply, instead of at the bottom of the whole email chain. Note that this feature only supports emails formatted as HTML or Plaintext. Unfortunately, support for Rich Text email formats is legacy and will not be improved. For emails formatted as Rich Text, the label footers will continue to accumulate at the bottom of email threads as before.
What you need to do to prepare:
No action is needed to enable this feature, besides using footers in sensitivity labels.
Get started with Information Protection in the Microsoft Purview compliance portal.
Learn more: Manage sensitivity labels in Office apps
MC672527 — Microsoft Purview Data Lifecycle and Records Management: New Graph APIs to apply
<30 Days
Microsoft 365 Roadmap ID 145118
Retention labels can be applied to items in SharePoint and OneDrive for Business programmatically today using CSOM and REST APIs. To offer more flexibility with our products and a more scalable solution, we’re excited to introduce these 4 new Microsoft Graph APIs:
- Set (apply) a retention label to items in SharePoint and OneDrive for Business
- Get metadata information for the retention label applied to an item
- Remove the retention label from the item
- Lock and unlock record labels (records versioning)
When this will happen:
Preview: We will begin rolling out these changes to Microsoft Graph API beta in early September and should be fully available to customers by mid-September.
Standard Release: We will begin rolling out to Microsoft Graph API v1 in early October and should be fully available to customers by mid-October.
How this will affect your organization:
If you are using CSOM or REST APIs to apply and manage retention labels, we recommend using these new Graph APIs instead.
What you need to do to prepare:
No action is needed; however, you may want to communicate this new feature to the team responsible for Data Lifecycle and Records Management at your organization.
MC670437 — (Updated) New default Microsoft Purview Data Loss Prevention policies
Rolled Out
Updated September 6, 2023: We have updated the rollout timeline details below.
We are creating default policies for Microsoft Purview Data Loss Prevention in your tenant to protect the most vulnerable sensitive information from accidental or malicious egress. The following default policies will be deployed along with the sensitive information they detect:
- Financial Information
- Healthcare Information
- HR and Privacy Information
- Source Code, Intellectual Property, and Trade Secrets
- Customer files
These changes are being made to your tenants as a precaution to help protect against potential data exfiltration.
When this will happen:
Timeline to opt-out: The rollout of the opt-out banner completed in late August. Once you see the banner, you will be able to opt-out until the 30 days is complete.
Timeline for Default policies: If opt-out is not selected, default policies will be rolled out in 30 days. The policies will be rolled out starting September 30th.
How this will affect your organization:
If you wish to opt-out of these policies, please visit your compliance portal and choose to opt out of the policies on the Policies page under Data Loss Prevention. The option to opt-out of these new default policies will be available for 30 days. After the roll out, these policies can be edited or deleted. For more information about editing a DLP policy see: Design a Data loss prevention policy | Microsoft Learn
What you need to do to prepare:
For more information about Microsoft Purview Data Loss Prevention please see:
MC669740 — (Updated) Microsoft Purview Information Protection Tracking and Revocation – End-User Tracking and Revocation
30-60 Days
Updated September 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
From the sensitivity menu, owners of Office files protected with a sensitivity label can access the Microsoft Purview compliance portal to view user access attempts and revoke access if needed.
When this will happen:
Preview: We have started rolling out and expect to complete by late August. - Complete
Registration will begin rolling out to production in mid-October 2023 (previously late August) and expect to complete by late October 2023 (previously mid-September).
Track & Revoke will begin rolling out to production will begin rolling out in late-October 2023 (previously late August) and expect to complete by mid-November 2023 (previously mid-September).
How this will affect your organization:
The Microsoft Purview Information Protection Tracking and Revocation feature will be turned on by default. To disable the feature, use the Disable-AipServiceDocumentTrackingFeature commandlet.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC669734 — (Updated) Admins are unable to manage Bing Chat Enterprise with MSB toggled off
TBD
Updated September 25, 2023: For Bing Chat Enterprise-eligible customers with Microsoft Search in Bing (MSB) toggled off, Bing Chat Enterprise will be turned on by default within the next 24 hours unless they previously opted-out.
Reminder: Organizations in government clouds are ineligible for Bing Chat Enterprise and can disregard the above.
Having Microsoft Search in Bing toggled on is no longer required to manage Bing Chat Enterprise. Please find more details on how to manage Bing Chat Enterprise here: Manage Bing Chat Enterprise | Microsoft Learn.
Updated September 14, 2023: We are providing additional information for clarification.
Due to an email list error, some ineligible customers were included in this communication. We apologize for the error and any confusion this caused.
If your organization is not licensed with a BCE-eligible Microsoft 365 SKU (Microsoft 365 E3 and E5; A3 and A5 (faculty only); or Business Standard and Business Premium licenses), it is not available to you and no action is required to turn it off. To clarify, organizations in government clouds are ineligible.
This message remains applicable to customers with eligible SKUs who have Microsoft Search in Bing (MSB) toggled off.
For customers who have Microsoft Search in Bing (MSB) toggled off, Bing Chat Enterprise will be turned on by default in mid-September instead of late August.
Please refer to MC649341 (July ’23) for more information on Bing Chat Enterprise and how to manage it for your organization.
To opt-out of Bing Chat Enterprise prior to mid-September, please follow the instructions in this communication. If you want to turn on Bing Chat Enterprise in your organization, you can do nothing and wait until it is turned on by default in mid-September.
When this will happen:
For customers who have Microsoft Search in Bing (MSB) toggled off, Bing Chat Enterprise will be turned on by default in mid-September instead of late August.
How this will affect your organization:
Bing Chat Enterprise will be turned on by default in mid-September. If you would like to opt-out of Bing Chat Enterprise prior to mid-September, you will need to take action.
What you need to do to prepare:
You will be able to opt-out of Bing Chat Enterprise after the end of August, as the Microsoft Search in Bing requirement will no longer be required to update your Bing Chat Enterprise settings using the links specified below.
To opt-out of Bing Chat Enterprise before it is turned on by default in mid-September:
- Use the link: https://aka.ms/TurnOffBCE
Note: You will not be able to access Bing Chat Enterprise sooner than mid-September.
If you take no action and allow Bing Chat Enterprise to be turned on by default in mid-September, your organization is thereby consenting to the Terms & Conditions.
For further details, please see our technical documentation: https://aka.ms/Bing-Docs
MC668524 — (Updated) Microsoft Purview Information Protection: Tracking and Revocation in Compliance Portal
Rolled Out
Microsoft 365 Roadmap ID 152126
Updated September 6, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can access the Microsoft Purview compliance portal to check who has tried accessing their sensitivity labeled and encrypted local Office files and revoke access when needed.
When this will happen:
Preview: We will begin rolling out late August 2023.
Standard Release: We will begin rolling out early November 2023 (previously mid-September) and expect to complete by mid-November 2023 (previously late September).
What you need to do to prepare:
The Microsoft Purview Information Protection Tracking and Revocation feature will be turned on by default. To disable the feature, use the Disable-AipServiceDocumentTrackingFeature commandlet.
MC668252 — Microsoft Purview: Data Lifecycle and Records Management – Scope the administration of retention and label policies GCC
Rolled Out
Microsoft 365 Roadmap ID 117354
Updated September 12, 2023: We have updated the rollout timeline below. Thank you for your patience.
To assist in the implementation of security best practices, we are introducing new way to assign administrative privileges in the Microsoft Purview Data Lifecycle Management and Microsoft Purview Records Management solutions that will provide admins the least privilege access required for their job duties.
With this change, organizations can leverage Administrative Units in Azure Active Directory (AAD) to define who can configure and manage policies in Microsoft Purview. This update will include the ability to set up a Data Lifecycle Management or Records Management admin for a specific geography, department, or other unit, who can manage retention and label policies for their unit.
When this will happen:
Rollout to general availability will begin in mid-September 2023 (previously late August) and is expected to be complete by late September 2023 (previously early September).
How this will affect your organization:
Once this feature rolls out, Data Lifecycle Management and Records Management administrators in your organization will have the ability to use administrative units to granularly define access to who can manage retention policies and label policies for different parts of the organization.
Previously, you were only able to assign a tenant-wide admin for Data Lifecycle Management. These people would configure and administer retention and label policies for every part of the organization. Now, you can associate Data Lifecycle Management administrators to one or more admin units. This enables administrators who can view and manage policies for only part of an organization to do so confidently without affecting other units. For example, you can designate an administrator for the Finance Admin Unit. This person can then create polices that apply only to Finance users, groups, or sites.
What you need to do to prepare:
There is nothing you need to do to receive this feature.
You may consider updating any training or reference material for your Data Lifecycle Management and Records Management administrators and evaluate if you would like to use this new capability.
Get started with Data Lifecycle Management and Records Management in the Microsoft Purview compliance portal.
Learn more: Permissions in the Microsoft Purview compliance portal
MC667128 — Microsoft Purview Compliance Portal: Self-diagnostic tool for SharePoint and OneDrive DLP policies – Test-DlpPolicies
<30 Days
Microsoft 365 Roadmap ID 124833
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
Coming soon to general availability, we're introducing a new diagnostic tool to test the functionality of your Microsoft Data Loss Prevention (DLP) rules and policies configured for SharePoint Online and OneDrive for Business.
When this will happen:
Standard Release: Rollout will begin in late September 2023 (previously late August) and is expected to be complete by mid-October 2023 (previously mid-September).
How this will affect your organization:
With this update, admins can utilize a self-diagnostic tool via a new cmdlet (Test-DlpPolicies) to test DLP policies against SharePoint content and see if policies are working as expected. In test mode, the DLP policies are applied to the specified file in SharePoint, and an email containing the results is generated and sent to the admin.
What you need to do to prepare:
No action is needed to enable this feature. Refer to documentation for additional details on using the cmdlet.
Get started with the Data Loss Prevention solution in the Microsoft Purview compliance portal.
Learn more:
MC667126 — (Updated) Microsoft Purview DLP Endpoint: Most restrictive actions across multiple policies GA
<30 Days
Updated September 12, 2023: We have updated the timing below with additional information. Thank you for your patience.
We're enhancing the enforcement engine in Microsoft Purview Endpoint DLP (part of the Microsoft Purview Data Loss Prevention suite) to refine the restrictions enabled when multiple rules are matched. Note: This change is specific to Endpoint DLP for Windows only. Changes for MacOS will roll out separately.
When this will happen:
Starting in late August, we're rolling this enhanced behavior, which will apply the most restrictive policy-defined actions across multiple policies triggered by a given event. We expect to complete by early October.
How this will affect your organization:
You are receiving this message because your organization has licensing that entitles you to use Endpoint DLP.
Once this change is implemented, administrators may see an increase in Endpoint DLP alerts as more user activities are blocked by the more restrictive of multiple flagged policies.
Example: A user attempts to print a file containing both SSN & credit card numbers, triggering multiple policies. The SSN policy blocks users from printing, and the credit card policy blocks with override. The most restrictive policy (block) will be applied, ensuring there are no gaps in coverage.
What you need to do to prepare:
No action or policy reconfiguration is needed to enable this change.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Get started with Endpoint data loss prevention Data Loss Prevention policy reference.
MC666968 — Microsoft Purview Insider Risk Management – General availability of sequence starting with downloads from 3rd-party site
Rolled Out
Microsoft 365 Roadmap ID 153487
Coming soon, Microsoft Purview Insider Risk Management will be rolling out a new capability – sequence detection starting with downloads from third-party sites.
When this will happen:
Rollout will begin at the end of August and is expected to be complete by the end of September.
How this will affect your organization:
Admins with appropriate permissions can configure the new sequence feature to detect risky user activities that start with downloading data from third-party domains, such as box.com or dropbox.com. This can help security teams gain visibility into actions that take place in their multi-cloud environments that may lead to a data security incident.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
What you need to do to prepare:
To begin using this capability, admins with appropriate permissions can configure third-party domains at Insider risk settings > intelligent detections > third-party domains.
Get started with Insider Risk Management in the Microsoft Purview compliance portal.
MC660616 — (Updated) Microsoft Purview Information Protection: Require sensitivity label to restrict permissions
30-60 Days
Microsoft 365 Roadmap ID 109532
Updated September 15, 2023: We have updated the content below with additional information. Thank you for your patience.
Users with access to Microsoft Information Protection (MIP) are redirected from old protection mechanisms towards the modern sensitivity labeling experience.
When this will happen:
Preview: We will begin rolling out in mid-August 2023 (previously late July) and complete by early September 2023 (previously mid-August).
Standard Release: We will begin rolling out in late September 2023 (previously early September) and complete by late October (previously late September).
How this will affect your organization:
When restricting access to files using Information Rights Management (IRM), Office will redirect users to apply a sensitivity label instead (if available) to protect the file. Users will also be directed to use sensitivity labels to change the file’s protection rather than standalone IRM.
What you need to do to prepare:
Organizations with need for user-defined permissions should set-up sensitivity labels with user-defined permissions.
If you don't have any sensitivity labels or want to learn more, visit Get started with sensitivity labels.
MC635990 — (Updated) Microsoft Purview Information Protection: Unsaved default label indicator
<30 Days
Updated September 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
When default labeling of files is enabled in Word, Excel, and PowerPoint Microsoft 365 Apps for Windows, a default sensitivity label is applied to any unlabeled document when it is saved. To improve user confidence that default labeling is functioning, the sensitivity bar will now indicate that a label will be applied on next save when the user opens a new or previously unlabeled file.
When this will happen:
Standard Release: We will begin rolling out mid-September 2023 (previously mid-August) and expect to complete by late October 2023 (previously late September).
How this affects your organization:
When the change is rolled out, when a user opens a new or previously unlabeled file and default labeling is enabled, the sensitivity bar will indicate that a label will be applied on next save.
What you can do to prepare:
You may consider updating your training and documentation as appropriate.
MC609873 — Microsoft Purview Data Loss Prevention: Configure policy tips as pop-up dialog for emails with sensitivity labels
30-60 Days
Microsoft 365 Roadmap ID 139511
Updated October 3, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Purview Data Loss Prevention policies can be configured to display policy tips as a pop-up dialog for emails with sensitivity labels.
When this will happen:
Rollout will begin in mid-October 2023 (previously mid-September) and is expected to be complete by mid-November 2023 (previously mid-October).
How this will affect your organization:
Admins can configure DLP policies to show policy tips as a dialog to end users when they attempt to send email messages that include a sensitivity label on the email or attachment. With this capability, admins can set up rules to warn or block or request for an explicit acknowledgement or a business justification from users before sending emails. Furthermore, admins can customize a learn more URL in a DLP rule, ensuring that end users receive valuable guidance through the popup.
Note: Users included in these policies must hold E5/G5 or equivalent licenses.
What you need to do to prepare:
Configure policy tips for Data Loss Prevention in the Microsoft Purview compliance portal:
Learn more:
- Learn how to configure a DLP rule with oversharing popups: Create and Deploy data loss prevention policies
- View the AIP migration playbook: Migrate Oversharing Popups from AIP
MC598630 — (Updated) Microsoft Purview Data Loss Prevention - DLP Policy tips revamp for Outlook for Windows for E5/G5 users
<30 Days
Microsoft 365 Roadmap ID 138577
Updated September 15, 2023: We have updated the rollout timeline below. Thank you for your patience.
We’re rolling out new and improved DLP Policy tips in Outlook for Windows to support top DLP predicates and exceptions, all advanced classifiers, and override capabilities for E5/G5 users.
When this will happen:
Rollout will begin in late September 2023 (previously early August) and is expected to be complete by late October 2023 (previously late September).
How this will affect your organization:
You can now alert or restrict your users from unauthorized or accidental sharing of any sensitive information via email in Outlook win32 by leveraging new and improved DLP Policy tips in new or existing DLP policies. These real time alerts and recommendations empower your organization to accurately identify sensitive information being shared with unauthorized recipients or domains and take appropriate action.
DLP Policy tips now support a richer set of DLP conditions (and corresponding exceptions), including the following:
- Content Contains Sensitive Information
- Content contains Sensitivity label
- Content is shared internally/externally
- Sender is
- Sender domain is
- Sender is member of
- Recipient is
- Recipient domain is
- Recipient is a member of
- Subject contains words
Additionally, DLP Policy tips now support advanced classifiers like Trainable classifiers, Exact data match (EDM), Named Entities, and Credential scanning SITs, as well as an override feature that gives end users the ability to quickly and easily modify or override policies (if allowed in the DLP rule configuration), ensuring that the sensitive data is always protected, while still allowing end users to work efficiently.
What you need to do to prepare:
You can create new DLP policies or leverage the existing ones to use DLP Policy tips as an additional layer of security for sensitive data.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal:
Learn more:
Microsoft Defender
MC675497 — New eBPF sensor for Microsoft Defender for Endpoint on Linux
Rolled Out
We are excited to announce the incoming of a new kernel-based sensor- eBPF (extended Berkeley Packet Filter) sensor for Microsoft Defender for Endpoints on Linux. eBPF sensor is an alternative technology to auditd. It is primarily an event provider which helps in dynamic and efficient tracing of system events such as network activities at packet and socket level, function calls, other system events providing deeper visibility into system behavior. It delivers additional system stability and performance optimizations in terms of improved CPU & memory utilization and reduced disk space usage for all supported Linux-based machines.
eBPF has shown significant improvements in performance, usability and stability for our customers using it in the preview stages. With eBPF, events previously obtained from the auditd event provider will now flow from the eBPF sensor. When eBPF is enabled, all auditd-related custom rules will be eliminated to help reduce the possibility of conflicts between applications. In addition, the eBPF sensor uses capabilities of the Linux kernel without requiring the use of a kernel module that helps increase system stability. With very low overhead, it becomes ideal for use in performance critical environments.
When this will happen:
eBPF sensor for Microsoft Defender for Endpoints on Linux will be generally available to all customers tentatively by the end of September with the release of our agent version '101.23082.0006'.
How this will affect your organization:
Starting MDE agent version '101.23082.0006' and onwards, eBPF will be enabled as the default supplementary event provider for all customers. This version is expected to hit production around end of September. Customers upgrading to version '101.23082.0006' will start seeing eBPF as the new default event provider. New deployments starting version '101.23082.0006' will start off with eBPF as the primary event provider. In case of any failures in enabling eBPF, there is a built-in fallback mechanism to auditD as the event provider automatically. Kernels that don't support eBPF will continue leveraging auditD. The 'supplementary_events_subsystem' field in the output of 'mdatp health' command can be used to verify that "ebpf" has been configured as the primary event provider.
What you need to do to prepare:
Customers upgrading to version '101.23082.0006' will start seeing eBPF as the new default event provider. You are recommended to test and plan your upgrade to the latest and greatest version accordingly. In case you observe any issues with this version '101.23082.0006', please raise a support case. New deployments will seamlessly get the benefits of eBPF.
Additional Information Link - Use eBPF-based sensor for Microsoft Defender for Endpoint on Linux
MC675279 — Reminder - Microsoft Defender for Identity: Classic portal automatic forced redirection
<30 Days
Beginning on September 30, 2023, access to Microsoft Defender for Identity legacy portal at portal.atp.azure.com will be unavailable for Gov environments (MC567494 June '23). Any request will be automatically redirected to Microsoft 365 Defender portal at security.microsoft.com. All new and existing tenants will be automatically redirected to the M365 Defender portal, and the option to opt-out will no longer be available.
When this will happen:
This will begin rollout on September 30, 2023, and is expected to be complete by mid-October 2023.
How this will affect your organization:
Once the forced redirection takes place, any requests to the standalone Defender for Identity portal (portal.atp.azure.com) will be redirected to Microsoft 365 Defender (securtiy.microsoft.com) along with any direct links to its functionality.
Organizations cannot manually opt-out and disable the setting.
What you need to do to prepare:
Ensure your security teams are familiar with Defender for Identity’s features and settings as they are represented in Microsoft 365 Defender. If your security teams need help, please direct them to the updated documentation available here.
MC673982 — Microsoft Secure Score is adding SSPM support
Rolled Out
We’re updating Microsoft Secure Score improvement actions to ensure a more accurate representation of security posture. The improvement actions listed below will be added to Microsoft Secure Score. Your score will be updated accordingly.
When this will happen:
This will begin rollout in mid-September 2023 and is expected to be complete by late September 2023.
How this will affect your organization:
The following new Microsoft Information Protection recommendations will be added as Microsoft Secure Score improvement action:
- Ensure Microsoft 365 audit log search is enabled.
- Ensure DLP policies are enabled for Microsoft Teams.
The following new Exchange Online recommendations will be added as Microsoft Secure Score improvement actions:
- Ensure that SPF records are published for all Exchange Domains
- Ensure modern authentication for Exchange Online is enabled.
- Ensure MailTips are enabled for end users.
- Ensure mailbox auditing for all users is enabled.
- Ensure additional storage providers are restricted in Outlook on the web.
The following new Microsoft Defender for Cloud Apps recommendation will be added as Microsoft Secure Score improvement actions:
- Ensure Microsoft Defender for Cloud Apps is enabled
The following new Microsoft Defender for Office recommendations will be added as Microsoft Secure Score improvement actions:
- Ensure Exchange Online Spam Policies are set to notify administrators.
- Ensure all forms of mail forwarding are blocked and/or disabled.
- Ensure Safe Links for Office Applications is enabled.
- Ensure Safe Attachments policy is enabled.
- Ensure that an anti-phishing policy has been created.
What you need to do to prepare:
There's no action needed to prepare for this change, your score will be updated accordingly. Microsoft recommends reviewing the improvement actions listed in Microsoft Secure Score. We will continue to add suggested security improvement actions on an ongoing basis.
MC519232 — (Updated) Attack Simulation and Training- Update to predicted compromise rate metric for tenant payloads
>60 Days
Updated October 3, 2023: We have updated the rollout timeline below. Thank you for your patience.
Attack Simulation Training under Microsoft Defender for Office is an intelligent phish risk reduction tool that measures behavior change and automates the deployment of an integrated security awareness training program across an organization. One of the most crucial elements in running a phishing simulation is the right selection of payload, to drive the right user behavior.
A core metric that can be used towards payload efficacy is predicted compromise rate (PCR) that predicts the percentage of people who will be compromised by this simulation (users compromised / total number of users who receive the simulation).
As part of this update, we are introducing an intelligent machine learning driven mechanism to predict a more accurate potential compromise rate if the payload was used within a simulation.
As part of this change, there will be 2 updates:
- Updates to the PCR values for global payloads available within Content library -> Global payloads:
- Introduction of an on-demand PCR calculation experience:
As part of the payload authoring experience, you can create your payload content and use the PCR machine learning model to determine the efficacy of your payload. This will be an addition to the existing experience and does not impact existing payload authoring experience.
When this will happen:
We plan to do a staggered rollout in following phases:
- Updates to global payloads will start to roll out from 3rd week of February, and are expected to complete by mid-April - Complete
- The on-demand PCR calculation for English language payloads will start to roll out from 1st week of March, and is expected to complete by end-April - Complete
- The on-demand PCR calculation for non-English language payloads will start to roll out from 2nd week of April, and is expected to complete by late January 2024 (previously late September 2023)
How this will affect your organization:
As part of this update, you will see minor changes in the PCR value for payloads. You will also see a mechanism to calculate PCR values as part of your payload authoring experience. There are no changes to your simulation, training workflows or content library.
There is no impact to the end users within your organizations, and only updates the experience for admins with access to Attack Simulation and Training experience.
Microsoft Defender for Office
MC678854 — Public Preview: Unified RBAC for Exchange Online (EXO) configurations in MDO
<30 Days
Unified Role Based Access Control (URBAC) provides an alternative to traditional Microsoft Defender for Office 365 (MDO) and Exchange Online (EXO) RBAC. By default, there are no changes to your security portal permissions. If you want to change to using Unified RBAC, then you must first configure the new URBAC roles for your organization. Once you have configured these roles, then you can enable use of URBAC for ‘Microsoft Defender for Office’ permissions and/or ‘Exchange Online permissions’. Doing so replaces your existing RBAC with the new roles. You can find more information over here - Microsoft 365 Defender Unified role-based access control (RBAC) | Microsoft Learn.
Unified RBAC will not migrate/replicate Exchange Online permissions – these will require manual configuration in URBAC role groups.
Due to the impact of RBAC on features within the Defender for Office 365 portal, if you are migrating to URBAC, you should configure URBAC roles in a test environment prior to enabling it for your organization. If you encounter access problems, you will need to check the permissions for the roles you have configured in URBAC.
When this will happen:
Unified RBAC for Exchange Online (EXO) configurations will be made available as a public preview starting on October 16th, 2023
How this will affect your organization:
Unified RBAC enables organizations to configure a single set of permissions for their security teams that work for Defender for Office, as well as the other Defender solutions.
What you need to do to prepare:
If you want to change to using Unified RBAC, then you must first configure the new URBAC roles for your organization. Once you have configured these roles, then you can enable use of URBAC for ‘Microsoft Defender for Office’ permissions and/or ‘Exchange Online permissions’. Doing so replaces your existing RBAC with the new roles.
MC676125 — Instructions to avoid opening safelinks to Office documents on SharePoint or OneDrive from Outlook email in read only
30-60 Days
The ability to click on Safe Links from an Outlook message and open Office files hosted in OneDrive or SharePoint Online directly into Microsoft 365 Apps for Windows will require Version 2108 (SEC) or later. Devices running versions older than Version 2108 (SEC) will open the document in the Microsoft 365 Apps in read only mode.
When this will happen:
This change will roll out in late October 2023 and complete by early November 2023.
How this affects your organization:
You are receiving this message because our reporting indicates one or more users in your organization are using safelinks and are on a version older than 2108 (SEC).
Impact to administrators
- Administrators who manage the deployment of Microsoft 365 Apps should ensure their user devices are updated to at least Version 2108 (SEC). To be fully supported, devices should be updated to the latest supported version for their chosen update channel as listed on Update history for Microsoft 365 Apps (listed by date).
- Current Channel: Version 2301 or later
- Monthly Enterprise Channel: 2211 or later
- Semi-Annual Enterprise Channel (Preview): Version 2202 or later
- Semi-Annual Enterprise Channel: Version 2108 or later
- For administrators that allow Microsoft to manage their devices through the Microsoft 365 Apps Installation options in the Microsoft 365 admin center, there is nothing to do.
Impact to users
- Users with older versions and have the Links Open Right setting enabled in Microsoft 365 apps, will end up in read-only mode when they click on a SafeLink URL contained within an email message in Outlook to open the document, workbook, or presentation.
The Links Open Right setting is available from File > Options > Advanced > Link Handling > Open supported hyperlinks to Office files in Office desktop apps.
When the user's device opens a document as read-only, the following workarounds are available if the user cannot immediately update their device to Version 2008 or later.
- Close and re-open the document from the recently used file list within Excel, Word, or PowerPoint.
- In their Outlook settings, uncheck Open supported hyperlinks to Office files in Office desktop apps.
- Right click on the URL in the Outlook message, copy the hyperlink and paste into a browser to open the document in the web app.
What you can do to prepare:
Ensure your organization is running Microsoft 365 Apps for Windows Version 2108 (SEC) or later.
MC678057 — Microsoft Defender for Office 365 Tenant Allow Block List limits
30-60 Days
Microsoft 365 Roadmap ID 98185
Soon, customers with Microsoft Defender for Office 365 plan 2 can create 10,000 block entries and 5,000 allow entries (via admin submissions) in the Tenant Allow Block List for each category (Domains & addresses, Files, and URLs). Customers with Microsoft Defender for Office 365 plan 1 can create 1,000 block entries and 1,000 allow entries (via admin submissions) in the Tenant Allow Block List for each category. Customers with Exchange Online Protection will remain at 500 block entries and 500 allow entries (via admin submissions) in Tenant Allow Block List for each category. The limit for spoofed senders will remain at 1,024 total entries (block entries and allow entries combined) for all service plans.
When this will happen:
This change will start rolling out in early October and should be completed by late November.
How this will affect your organization:
It would not affect any of your existing Tenant Allow Block List entries.
If you already have higher limits, then you will remain unaffected by this change.
If you have a mixture of licenses, we will consider the highest service plan as the service plan for the entire tenant and allocate Tenant Allow Block list limits.
What you need to do to prepare:
No changes are required. Your existing Tenant Allow Block List entries will not be affected. Once this change is made, you might be able to create more allow entries and block entries based on your service plan.
MC675960 — Microsoft Defender for Office 365: Tenant Allow Block List to Support URL Top-Level Domain Blocking
<30 Days
Microsoft 365 Roadmap ID 115506
Soon, you will be able to block URLs based on their top-level domain using block entries in the Tenant Allow Block List. You can create entries in the Microsoft 365 Defender portal or PowerShell, using the format “*.<TLD>/”, where <TLD> can be any top-level domain such as .net, .biz, .io, .movie, country codes (.in, .us, .ru) etc. The entry is not case sensitive, and can be in uppercase, lowercase, or mixed.
It is applicable to customers with Exchange Online Protection, Microsoft Defender for Office plan 1 or plan 2 service plans.
The top-level domain entry results in the blocking of all URLs that are related to “*.<TLD>/”, (subdomains, domains, or sub paths) both during mail flow (email is quarantined like other blocked URL entries) and at time of click across Microsoft Teams and Office apps, if Safe Links is enabled.
When this will happen:
Rollout will begin in late September 2023 and is expected to be complete by late October 2023.
How this will affect your organization:
This will not affect any of your existing Tenant Allow Block List entries.
What you need to do to prepare:
No changes are required. Once this change is rolled out, you can use it to block URL top-level domains.
MC674731 — Handling Malicious Intra-Organizational Messages by Default
<30 Days
We will be turning on intra-organizational protection by default for high-confidence phishing messages that contain a malicious or spam-based URLs in Microsoft Defender for Office 365. We are doing this along with the handling of intra-organizational messages (MC577356).
When this will happen:
Rollout will begin in late September 2023 and is expected to be complete by late October 2023.
How this will affect your organization:
The default behavior will be to quarantine intra-organizational messages that contain high confidence phishing URLs. If you want to opt-out of this behavior or opt-in to additional protection you can adjust your preferences within the anti-spam policy. More information can be found in this Configure spam filter policies documentation.
If you do nothing, the policy will default to act on messages containing high confidence phishing URLs after rollout.
What you need to do to prepare:
You don't need to do anything, however, if you don't want to act on intra-organizational messages, you can opt-out by changing the Anti-spam setting to NONE. If you prefer to opt-in to the new behavior now, you can select High Confidence Phishing or one of the other options from the drop down.
MC674418 — Required Configuration for Phishing Simulation emails
Rolled Out
Exchange online protection (EOP)/ Defender for Office 365 (MDO) customers who want to send phishing simulation emails, need to configure advance delivery policy for optimal behavior. This policy will ensure that emails that match your conditions are delivered unfiltered to the Inbox and that safe links time of click protection and post-delivery actions are disabled. Previously, EOP supported this scenario for some phishing simulation vendors by honoring admin configured Exchange transport rules stamping SCL -1 or the header (X-MS-ExchangeOrganizationPhishTraining). But this was a temporary solution and will be discontinued soon. We advise all customers who use phishing simulation products to configure advance delivery policy for a smooth product experience.
How this will affect your organization:
If you are using a 3rd party phishing simulation product and haven't configured advanced delivery policy, you might notice these emails getting quarantined.
What you need to do to prepare:
Instead of using mail flow transport rules, we recommend using Advance Delivery Policy
MC668798 — (Updated) Outlook on the web: Pre-Reporting and Post-Reporting Popups Integrated with Microsoft Defender for Office 365
30-60 Days
Microsoft 365 Roadmap ID 115508
Updated September 27, 2023: We have updated the rollout timeline below. Thank you for your patience.
The popups end-users see before and after reporting a message as phishing, junk, and not junk in Outlook on the web can soon be customized and localized in up to seven selected languages out of the full list of languages that Microsoft 365 supports.
Admins can customize the title and description of the popups. They can even add a custom URL along with custom URL link text which will be shown on the popups.
When this will happen:
Rollout will begin in mid-October 2023 (previously late September) and is expected to be complete by early November 2023 (previously mid-October).
How this will affect your organization:
To report a message in Outlook on the web, select Report in the simplified ribbon view.
Admins can customize and localize the popup messages on user reported settings using the "Customized messages" option.
Admins can add customized localized pre-reporting and post-reporting popup messages in up to seven different languages selected from the full list of languages supported.
If the reporting feature is turned OFF in the user reported settings page of the Microsoft 365 Defender portal, or if you're using a third-party add-in, you will not be affected by this change.
Other Outlook clients for Mac, Windows, and iOS and Android are unaffected by this change.
The Microsoft Report Message add-in will support the seven languages only for the pre-reporting popup (title and description). The link and URL aren't supported for the pre-reporting popups. The Microsoft Report Phish add-in will only support the report phish pre-reporting popup.
If you enable the popups and don't provide a custom message or set up a custom message for some of the notifications, the default notification which Outlook on the web shows today will be shown in the user's locale.
Unfortunately, the existing customized messages you have for pre-reporting and post-reporting popups inside user reported settings won't be carried over as part of this change.
What you need to do to prepare:
Once this change is rolled out, you can configure the new customized messages for pre-reporting and post-reporting popups in different languages using user reported settings.
MC649928 — (Updated) Introducing Microsoft Teams Post-Delivery Protection
Rolled Out
Microsoft 365 Roadmap ID 117595
Updated September 12, 2023: To give you more time to prepare, we are extending the opt-out period from August 18th, 2023 to August 22nd, 2023. We have also updated the UX to display the default policy as “On (default)” instead of previously appearing as “Off”. Remember to revisit the policy and verify that you have the right policy setting configured for your organization. If you want to opt-out, you will need to disable the policy in the UX or cmdlet.
If you would like to turn on ZAP prior to August 22nd, 2023 you can do so by turning off the policy, saving it, turning it on again and saving it.
We are introducing Zero-hour auto purge (ZAP) for Microsoft Teams. Internal messages containing potentially malicious content with Malware and High Confidence Phish verdicts will be automatically blocked for the end user and quarantined. Zero-hour auto purge will be ON by default once rolled out.
The blocked Teams messages can be reviewed in quarantine by the admin or end user (depending on the custom quarantine policy the admin has configured) and message details can be viewed on the Teams message entity panel. The Teams quarantine action can be configured in the Microsoft Teams protection policy under quarantine policies. If no custom quarantine policy is configured, the default will be set to admin only access policy.
These features will be available to P2 and E5 customers.
When this will happen:
We will begin rolling out in late July 2023 and expect to complete rollout by late September 2023 (previously late August).
After August 22, 2023, automated ZAP actions of blocking messages will occur unless you specify a different action. You will have until August 22, 2023 to opt-out.
How this will affect your organization:
Internal teams messages with Malware and High Confidence Phish verdicts will be blocked for end users on the Teams client. These messages can be reviewed in quarantine.
You can opt-out by running the cmdlet or disabling the Microsoft Teams protection policy. For more information, please visit:
What you need to do to prepare:
No additional action is required if you would like to enable ZAP in Microsoft Teams as the feature will be the cmdlet or disabling the Microsoft Teams Protection policy. For more information, please visit: Zero-hour auto purge in Microsoft Defender for Office 365.
Exchange Online
MC679319 — Microsoft 365: Translator for Outlook on the Web
30-60 Days
Microsoft Roadmap ID 164486
Translation email in Outlook on the Web is coming to your cloud. In Outlook, you can translate words, phrases, and full messages when you need them. You can also set Outlook to automatically translate messages you receive in other languages. When you receive an email message in another language, you'll see a prompt at the top of the message asking if you'd like Outlook to translate it into your preferred language.
When this will happen:
Rollout will begin in late October 2023 and is expected to be complete by early November 2023.
How this will affect your organization:
You may need to configure the experience in your tenant.
The new Translator feature provides several major benefits for most customers including:
- Source languages are detected automatically.
- Multilingual documents are supported.
- Users can look up translations for selected words, phrases, and other document selections.
- Users can insert translations back into the document with the formatting and fidelity preserved.
- Users can create on-demand translated copies of documents directly in the app.
What you need to do to prepare:
There is nothing you need to do to prepare for this change. For additional information, please visit this page.
MC679317 — Final Reminder Retirement of Remote Powershell in Exchange Online
<30 Days
As previously announced in MC488586 (December '22) we are in the process of retiring Remote PowerShell (RPS) in Exchange Online. Additionally we announced RPS retirement here in December ’22 and later gave an automatic 3-month extension here to all our sovereign cloud customers, in March ’23, which allowed them to use RPS until September 30th. As stated in the blog, we will be disabling RPS for organizations.
When this will happen:
Early October through mid-October
How this affects your organization:
If you are still using RPS to connect to EXO, we recommend you using Exchange Online PowerShell v3 module using Connect-ExchangeOnline without the UseRPSSession parameter.
What you can do to prepare:
If you are still using RPS to connect to EXO, we recommend you using Exchange Online PowerShell v3 module using Connect-ExchangeOnline without the UseRPSSession parameter. If not done, you will be unable to connect to EXO once RPS is disabled for your organization. In case of any concerns, please reach out to us on RPSDeprecation@service.microsoft.com
MC678855 — ExchangePowerShell: retirement of tenant admin cmdlets to Get, Set, and Remove UserPhotos
30-60 Days
We are working to ensure a coherent user profile image experience by retiring legacy profile photo services. This announcement covers the retirement of the ExchangePowerShell UserPhoto cmdlets for tenant admins to Get, Set, and Remove user profile photos:
When this will happen:
The retirement is scheduled for November 30, 2023.
How this affects your organization:
After this change the ExchangePowerShell UserPhoto cmdlets for tenant admins to Get, Set, and Remove user profile photos will no longer be usable.
Tenant admins can perform the same actions to Get, Set, and Remove user profile photos through the Microsoft Graph PowerShell SDK, or alternatively can administer the user photos through Azure Active Directory or through Microsoft 365 Admin Center, as described in this article.
What you can do to prepare:
You may consider updating training and documentation as appropriate.
MC678067 — Files Hub retiring from the new Outlook for Windows
30-60 Days
We will be retiring the Files Hub from the new Outlook for windows starting mid- October 2023. The Files Hub is a location where all attachments and files received by a user are aggregated and can be accessed through the paperclip icon from the leftmost vertical app bar in the new Outlook for windows.
When this will happen:
We will be gradually rolling this out to our enterprise users starting in mid-October 2023 and expect to complete by late November 2023.
How this will affect your organization:
Users will no longer be able to access the Files Hub when this change is implemented.
What you need to do to prepare:
Instead of using the Files Hub, we recommend using our other files centric experiences: the “Has files” filter in the message list or the upcoming “Files” tab within search results.
Differences to be aware of in the experience:
- In addition to supporting classic attachments like the file hub, the file tab shows up any file you have access to including cloudy and classic files and files shared on Teams.
- Unlike the file hub, you can only access the file tab once you have searched for something; there is no browse mode.
- The file tab currently will not support filtering the files, though we are actively working to add this feature.
- The file tab will not support photos.
MC676299 — Retirement of Exchange Web Services in Exchange Online
>365 Days
In 2018, we announced that we were no longer making feature updates to Exchange Web Services (EWS) in Exchange Online, and we advised developers to move to Microsoft Graph.
Today, we are announcing that on October 1, 2026, we will start blocking EWS requests from non-Microsoft apps to Exchange Online.
When this will happen:
October 1, 2026
How this affects your organization:
While the EWS components of the service will continue to receive security updates and certain non-security updates, product design and features will remain unchanged. This change also applies to the EWS SDKs for Java and .NET, as well.
Despite this announcement, EWS is still available and supported for use in production environments. But we strongly suggest migrating to Microsoft Graph to access Exchange Online data and gain access to the latest features and functionality.
Today’s announcement and the retirement of EWS apply only to Microsoft 365 and Exchange Online (all environments); there are no changes to EWS in Exchange Server. Further, the changes in Exchange Online do not affect Outlook for Windows or Mac, Teams, or any other Microsoft product.
Migrating Applications to Microsoft Graph
We know there are several feature gaps between EWS and Microsoft Graph, and though the list below is not exhaustive, these are the gaps most frequently reported to us by developers:
- Access to Archive Mailboxes – We are working on delivering access to archive mailboxes via Microsoft Graph and will provide an updated timeline in the coming months.
- Folder Associated Information / User Configuration – We are working on these features and will provide an updated timeline in the coming months.
- Exchange Online Management – We are investigating solutions for this and will provide an updated timeline in the coming months.
- Access to Public Folders – We are reviewing the need to provide third-party app access to Exchange Online public folders via the Graph API and are interested in hearing from customers and partners who build solutions that use public folders, other than backup and restore solutions. If you are willing to share details on how you use EWS with public folders, we’d love to hear from you, and you can reach us at EWSandPFfeedback@microsoft.com.
We know there are other gaps not listed above, and we continue to work on closing them, but it’s possible some functionality will not make it to Microsoft Graph. We encourage you to provide feedback to us, keep a close eye on the What’s new in Microsoft Graph page, and explore alternatives for functionality or features not available in Microsoft Graph.
Next Steps
The retirement of these APIs follows our Modern Lifecycle Policy. We understand changes like this may cause some inconvenience, but we are confident it will ensure more secure, reliable, and performant experiences.
We will publish regular communications as we progress towards this deadline to aid affected tenants in identifying EWS usage. We encourage all customers to monitor Message Center and this blog for related content.
Thank you in advance for updating and opening your apps to a wider range of useful and intelligent features on Microsoft Graph. We are extremely excited about the growing opportunities that Microsoft Graph offers to developers, and we remain fully committed to our journey to empower developers to access Microsoft 365 data with the most modern features and tools.
MC675499 — Outlook: Bookings With Me Available in GCC
30-60 Days
Microsoft 365 Roadmap ID: 171912
“Bookings with me” is coming in the GCC environment to help reduce the back and forth in scheduling while helping you maintain control of your calendar. You'll be able to create custom bookable slots to share with others so they can easily find a time to schedule a 1:1 meeting with you according to your availability and preferences. You will receive an email confirmation when someone books a slot with you using your personal booking page. Attendees can update or cancel scheduled meetings with you directly from your personal bookings page.
Bookings with me will be available in Outlook on Web and the new Outlook for Windows.
When this will happen:
Rollout will begin in late October 2023 and is expected to be complete by mid-November 2023.
How this will affect your organization:
Users will be able to access Bookings with me from the Outlook web calendar.
All users with the following subscriptions will have access to Booking slots in Outlook by default:
Office 365: A3, A5, E1, E3, E5, F1, F3
Microsoft 365: A3, A5, E1, E3, E5, F1, F3, Business Basic, Business Standard, Business Premium
What you need to do to prepare:
Bookings with me in Outlook will be enabled by default for users who meet the licensing requirements.
MC675144 — Outlook: MIP Label Support for Events on Android
>60 Days
Microsoft 365 Roadmap ID 163358
Tenants who have setup MIP sensitivity labels for use on events will now have support in Outlook for Android to both read and write labels to their meetings with enforcement of rules, such as encryption, as defined by tenant admins. This feature will also include support for other admin defined event label settings such as auto-label policies, do not forward, and cross-tenant events.
When this will happen:
Preview: We will begin rolling out mid-October and expect to complete by late October.
Standard Release: We will begin rolling out mid-November and expect to complete by early December.
How this will affect your organization:
Your organization will now have support of event labeling policies and their defined protections in Outlook Mobile, providing parity to the feature that exists in other Outlook apps for Windows, Mac, and Web. This will help to assure your organization has the ability to protect the meeting details and attachments of events while using Outlook Mobile.
What you need to do to prepare:
There is no specific action an admin needs to take so their organization has access to this feature. If your organization already uses event sensitivity labels, then they will begin to work seamlessly in Outlook Mobile once this feature is live. However, if you wish to learn more about what sensitivity labels are, how to create, use, and manage them, you may follow this link to our sensitivity label documentation.
MC675143 — Outlook: MIP Label Support for Events on iOS
>60 Days
Microsoft 365 Roadmap ID 163359
Tenants who have setup MIP sensitivity labels for use on events will now have support in Outlook for iOS to both read and write labels to their meetings with enforcement of rules, such as encryption, as defined by tenant admins. This feature will also include support for other admin defined event label settings such as auto-label policies, do not forward, and cross-tenant events.
When this will happen:
Preview: We will begin rolling out late October and expect to complete by early November.
Standard Release: We will begin rolling out mid/late November and expect to complete by mid-December.
How this will affect your organization:
Your organization will now have support of event labeling policies and their defined protections in Outlook Mobile, providing parity to the feature that exists in other Outlook apps for Windows, Mac, and Web. This will help to assure your organization has the ability to protect the meeting details and attachments of events while using Outlook Mobile.
What you need to do to prepare:
There is no specific action an admin needs to take so their organization has access to this feature. If your organization already uses event sensitivity labels, then they will begin to work seamlessly in Outlook Mobile once this feature is live. However, if you wish to learn more about what sensitivity labels are, how to create, use, and manage them, you may follow this link to our sensitivity label documentation.
MC670444 — (Updated) Outlook: Disallow Reactions on Specific Emails
<30 Days
Microsoft 365 Roadmap ID 117433
Updated September 19, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are developing a suite of improvements that support the Reactions in Outlook feature, including methods for a sender to disallow reactions on an email they are about to send, or methods for an admin to control which emails in their tenant should disallow reactions.
Different Outlook endpoints will differ in terms of timing of full support for the feature (i.e., UI entry point to Disallow Reactions and UI-disablement when reactions are disallowed). Server-side support will roll out in advance (i.e., attempts to react on emails that have reactions disallowed will not result in a Reaction signal).
When this will happen:
We will begin rolling out the server-side support in late September 2023 (previously mid-September) and expect to complete rollout by mid-October 2023 (previously late September).
How this will affect your organization:
You will have new capabilities at hand to fine-tune whether emails coming in from outside your tenant should not allow reactions, whether all emails in your organization should not allow reactions or use a myriad of other conditionals.
Your users will also have more agency to decide if a certain email they are about to send should not allow reactions.
What you need to do to prepare:
We will be publishing some documentation soon that describes the full extent of this feature.
For important information about how to use the new capabilities of Disallow Reactions, check out:
Reactions in Outlook: Public usability update September 2023 - Microsoft Community Hub
MC666166 — (Updated) Outlook: Reactions Feature in Outlook for GCC Moderate
Rolled Out
Microsoft 365 Roadmap ID 155836
Updated September 19, 2023: For additional information, refer to: Reactions in Outlook: Public usability update September 2023
With reactions in Outlook, you can now react to an email message sent from someone in the same tenant without having to send a reply email. Show your appreciation and empathy with one click or tap.
Users will see a reactions icon (a face) in a message for any messages sent from someone inside the same tenant. They can hover over or tap it to see all of the possible reactions to select from.
Reactions will also send a digest email to a user who received any reactions.
When this will happen:
We will begin rolling out in late August 2023 and expect to complete rollout by mid-September 2023.
How this will affect your organization:
Reactions in Outlook allows you to react with one of six possible ways: Thumbs up, Heart, Celebrate, Laugh, Surprise, Sad. When you click on a reaction, everyone in the email thread who received the email will be able to see the reaction as long as they are part of the same tenant. The sender of the email will receive a notification of any reaction in their Notifications feed giving them a quick view of all the reactions their emails have elicited from other people.
Reactions will send a digest email once a day to users that may have missed any reaction notifications in the past 24 hours.
Note: Users can only react and see reactions to messages sent from people in the same tenant. Emails received from an external sender may not show the "reaction icon" (face).
Users can also choose from different thumbs up reactions to choose the one that better represents them, and Outlook will remember their choice the next time.
What you need to do to prepare:
There is nothing you need to do to prepare for this change.
MC649482 — (Updated) Sender Rewriting Scheme (SRS) Expanding to SMTP/Mailbox Forwarding
<30 Days
Updated September 27, 2023: We have updated the content below to address customer feedback.
We're constantly working on making our service better and more efficient. As part of that, we are making changes to forwarding in Exchange Online that we have been working towards for some time. This will result in all forwarded messages being rewritten with Sender Rewriting Scheme (SRS).
Starting in mid-August, we will be further consolidating our rewriting feature for messages that are automatically forwarded outside of Exchange Online. Not all forwarded messages are rewritten using SRS today. For example, messages forwarded with SMTP or mailbox forwarding have their P1 Mail From address replaced with the forwarding mailbox address today. This will be changing, and SRS rewriting will be used instead. The change will be rolled out slowly and it may take time to reach your organization.
When this will happen:
We will begin rolling out in mid-August and expect to complete rollout by late October.
How this will affect your organization:
This behavior change may impact systems relying on the P1 Mail From address. All messages that are forwarded externally from Exchange Online to the internet will be subject to SRS rewriting. Messages that will see a change in behaviour include those forwarded externally by SMTP or mailbox forwarding, or by Mail Contacts or Mail Users with external addresses. The risk of mail flow impact by changing from the current rewriting method to SRS depends on a few factors including your tenant configuration. Here are a few factors in more detail:
Firstly, any rules that have been set up in your tenant that are dependent on the P1 Mail from address, SRS introduces a rewritten address that will neither be a user in your tenant nor use one of your own domains. If you need a rule to act on the mailbox responsible for the forwarding, you should use the Resent-From header. Any mail servers or devices that have been configured to rely on the P1 Mail From address could also be affected.
Secondly, SRS is not always used to rewrite all forwarded messages. As mentioned in the SRS documentation, the new Relay Pool feature decides whether a message should be rewritten or not. One scenario this applies to is when the incoming message did not pass our SPF check in the first place. The list of conditions that skip SRS rewriting can be found in the Relay Pool documentation: Outbound delivery pools
Lastly, SRS does not act on traffic leaving Exchange Online using an on-premises mail flow connector. There is a risk of disruption for customers who route traffic from Exchange Online out to the internet via their on-premises servers (EXO -> On-Prem -> Internet). Forwarded messages will go out without being rewritten and could result in them being rejected by the recipients' mail servers. This disruption would already be occurring for messages forwarded via other means such as Inbox Rules. This scenario can be addressed by following the instructions below about the new SenderRewritingEnabled setting.
Messages rewritten by SRS that are successfully delivered will have the same P2 From address of the original sender that shows up in email clients. Documentation on how SRS works here: Sender Rewriting Scheme (SRS) in Microsoft 365.
What you need to do to prepare:
Before this change takes effect, customers who route traffic to the internet from their on-premises environment should enable the new parameter SenderRewritingEnabled on their outbound on-premises mail flow connector to avoid any disruptions.
Please click Additional Information to learn more. Sender Rewriting Scheme Upcoming Changes
MC579609 — (Updated) S/MIME sensitivity label support natively on Outlook for Windows
30-60 Days
This change is associated with Microsoft 365 Roadmap ID: 139450
Updated September 20, 2023: We have updated the rollout timeline below. Thank you for your patience.
Outlook desktop will support S/MIME (Secure/Multipurpose Internet Mail Extensions) sign and encryption as sensitivity label outcome. Customer admins could use set-label advanced setting to define the label to have S/MIME sign or encryption or both, and emails with those labels applied will enforce S/MIME sign and encrypt accordingly, and also it will support content marking of the label.
When this will happen:
Standard Release: We will begin rolling out in mid-October 2023 (previously early September) and expect to complete by mid-November 2023 (previously late September).
How this will affect your organization:
If you have defined S/MIME email labels for your organization, you will see that S/MIME label also available in Outlook on the web to apply. If you do not have any S/MIME labels today, then it will not impact your organization.
What you need to do to prepare:
If you would like to start using S/MIME labels, please refer the admin instructions how to enable S/MIME labels via set-Label cmdlets advanced setting.
MC556159 — (Updated) Message List Selection UI updates for Outlook on the Web and New Outlook for Windows
<30 Days
Microsoft 365 Roadmap ID 125905
Updated October 3, 2023: We have updated the rollout timeline below. Thank you for your patience.
In order to save space on the message list in Outlook, we are making an UI update: From "selection circles on the left side of each row" to "Select mode that you have to get into before checkboxes appear", using a button in the top-right corner of the Message List. Users may have to acclimate themselves to the new Selection user experience.
In addition, mouse+keyboard multi-selection where users hold down Ctrl or Shift will continue to work as before.
When this will happen:
We will begin rolling out in mid-May 2023 and expect to complete rollout by late October 2023 (previously late September).
How this will affect your organization:
This will affect users who do not have "Sender Images" enabled in the Message List. If you have "Sender Images" turned on, hovering over the images will still show the checkboxes, even if you did not get yourself into "Select Mode". To review if you have "Send image" enabled, go to Settings > Mail > Layout and scroll to "Sender image".
What you need to do to prepare:
There is nothing to prepare for this change.
Microsoft 365
MC678062 — Important Notice: End of Support for Office 2013 and Recommended Upgrade
Rolled Out
Note: This message only applies to you if members of your organization are still running Office 2013.
Introduction
As of six months ago, support for Microsoft Office 2013 has officially ended. This means that security updates, non-security updates, free or paid assisted support options, or online technical content updates from Microsoft have ended for this version of the product.
How this will affect your organization:
If your organization is still running this version of the product, we strongly recommend that you upgrade to a newer version as soon as possible. Continuing to use Office 2013 could expose your system to potential security vulnerabilities and compatibility issues with new software and updates.
To ensure continuous support and access to the latest features, we recommend migrating to Microsoft 365 E3, which includes the Microsoft 365 Apps. This product is continuously supported and updated by Microsoft, providing you with the most secure and efficient tools for your needs.
Please take a moment to review this article that provides recommendations, information, and links to help organizations plan their upgrades from older versions of Office to Microsoft 365 Apps. If you haven't already begun to upgrade from these older versions of Office, we recommend you start now.
MC678059 — Banner message to appear for Stream (Classic) users on migrated videos
<30 Days
This is an important message for customers who have migrated or plan to migrate videos from Stream (Classic) to Stream (on SharePoint).
Beginning on October 15, 2023 your users will see a banner message on top of all migrated Stream (Classic) videos. The banner will say, "This video has been migrated to Stream (on SharePoint). You accessed this video from the Stream (Classic) link, which will expire on Feb 15, 2025. If you own the content containing the Stream (Classic) link, you will need to update it with the new Stream (on SharePoint) link. Learn more
When this will happen:
October 15, 2023
How this will affect your organization:
Your end users will see a banner message. End users who are owners of migrated videos will need to update the links associated with the migrated videos if they want those links to continue working after Feb 15, 2025. See this article for information on updating links: Migration details - Microsoft Stream
What you can do to prepare:
You should consider updating training and documentation as appropriate.
For more information and timelines on the retirement of Stream (Classic) see:
Overview of migrating from Microsoft Stream (Classic) to Stream (on SharePoint)
MC674414 — New servicing profiles and Inventory experience in Microsoft 365 Apps admin center
Rolled Out
New improvements are coming to Microsoft 365 Apps admin center's servicing profile and inventory to reduce admin burden and help build confidence to move to Monthly Updates. This will include changes to some of your Settings, and retirement of some device selection criteria. Below is an overview of changes and potential actions you can do to prepare for change.
Overview of the upcoming changes
- Servicing profiles (https://config.office.com/officeSettings/serviceprofile) will be renamed to Cloud Updates
- New Updates Overview page in the Servicing section which provides a comprehensive snapshot of the update progress.
- Settings like 'Exclude Groups' and 'Exclusion Windows' will be moved from the settings tab to 'Tenant Settings' Tab in Updates Overview Page
- Several device selection criteria controls will be deprecated i.e., Exclusion of devices by macros and add-ins, and Inclusion of devices by groups. All of Exclusion will be supported by 'Exclude Groups' capability which will enable admins to select AAD groups which they do not want to be managed via Cloud updates.
- For customers using Rollout Waves, Deployment Validation feature will provide high-confidence validation of new Microsoft 365 builds in monthly updates through statistical validation of health signals on Wave 1.
- Inventory (https://config.office.com/officeSettings/inventory) will get an additional column:
- Cloud update status: representing if this device is currently updated by profiles.
When this will happen:
We will begin rolling out these changes in September 2023.
How this will affect your organization:
The transition to the new release of servicing profiles and inventory will happen automatically. Depending on your current Device Selection Criteria, the scope of devices managed by Cloud Updates might change compared to Servicing Profiles. Additionally for Tenants with Rollout waves configured, Deployment Validation will be enabled.
What you need to do to prepare:
- If you are using Rollout Waves and want to benefit from Deployment Validation (https://learn.microsoft.com/deployoffice/overview-deployment-validation), ensure the following:
- Diagnostic data is turned on for your devices (at required level).
- You have good representation of our various departments and usage scenarios including add-ins. within your wave 1 devices. This will ensure early detection of issues and enable you to take action (and reduce risk).
- If you have configured Custom Waves under the Setting 'Rollout Waves', the duration between wave 1 and wave 2 will be adjusted to 7 days. The duration between all other waves will remain unchanged based on your original selection.
- If you are using any of the Device Selection Criteria among 'Inclusion into profiles based on Azure AD groups', 'Exclude devices based on Addin presence, disc space limitation or macros presence':
- Cloud Update profile will include devices based on their channel i.e., all Monthly Enterprise Channel Devices will be managed via Monthly Enterprise Channel profile - unless the devices are excluded via the 'Exclude Groups' setting. See Change the Microsoft 365 Apps update channel for devices in your organization for options on changing update channels.
- Azure AD groups-based filtering, Disk space selector, Macros selector and Add-in selector will be deprecated i.e. if you have set a value to exclude devices based on any of these settings, those devices will be included in their respective channel profile (currently support for only Monthly Enterprise Channel is launched so this applies to only Monthly Enterprise Channel Devices), unless you put those devices behind 'Excluded Groups' setting.
FAQs:
- Will devices change their assigned Microsoft 365 Apps update channels?
- No, this will not affect your update channel configuration.
- What are the goals of Deployment Validation?
- To give the customers a high-confidence validation process, reduce the app compatibility risk and effort needed for testing, and provide more visibility & control over build rollout.
- When should I use deployment validation?
- If you are concerned about App-compatibility, deployment Validation provides the best-in-class solution to identifying any add-in impact due to updates early in the rollout without disrupting your critical devices. This is an extension of the existing feature - Rollout waves. It will be automatically enabled when you create Custom Waves. It will give you a high fidelity quantitative and qualitative analysis of performance and reliability signals.
- When should I not use deployment validation?
- This feature is not for you if you don't have application compatibility concerns and presently, don't carry out manual validation of Microsoft 365 app builds before rollout.
- What are the requirements for getting Deployment Validation results?
- There need to be at least 10 devices with at least 1 session each in the 7 days preceding and following a patch Tuesday respectively. Also, Wave 1 needs to be representative of the wider tenant (incl. usage scenarios, app and add-in coverage).
- Can I turn off Deployment Validation?
- You can turn it off by removing/turning off Rollout Waves feature.
Learn More: New Improvements to Microsoft 365 Apps admin center coming soon!
Introducing Deployment Validation
Please share your feedback on the changes via the 'Give Feedback' button in Microsoft 365 Apps Admin Center at https://config.office.com/
MC674249 — Universal Print for GCC and GCC High organizations – coming soon
<30 Days
Microsoft 365 Roadmap ID 93404
Universal Print will soon be available in GCC and GCC High and offers full feature parity with what exists in the commercial cloud today, while remaining compliant with certifications that are required for U.S. government organizations.
When this will happen:
Universal Print will be available in GCC and GCC High beginning in early October.
How this affects your organization:
Existing Microsoft 365 E3/E5 GCC/GCC High tenants will be backfilled in early October 2023 with these new service plans accordingly: Universal Print for GCC and Universal Print for GCC HIGH.
These changes will impact Microsoft 365 Government G3 and G5 (GCC Compatible) customers, as they will now have access to Universal Print for GCC.
These changes will also impact Microsoft 365 Enterprise E3 and E5 in GCC High customers, as they will now have access to Universal Print for GCC High.
What you can do to prepare:
To learn more about Universal Print visit the Learn pages at License Universal Print. The content will be updated with information for GCC and GCC High in early October.
MC668795 — (Updated) Conditional access policy enforcement for Office Scripts
Rolled Out
Updated September 12, 2023: We have updated the content below with additional information.
SharePoint and OneDrive conditional access policies for unmanaged devices will start to be enforced for Office Scripts files. This means that users on unmanaged devices will have their access to Office Scripts functionality restricted based on policies you have enabled in your tenant.
When this will happen:
We will be turning enforcement on in late September and start rolling out an updated error message for Excel clients. The rollout of the error message will complete based on the deployment schedule for each update channel.
How this will affect your organization:
Users on unmanaged devices may start encountering errors if they attempt to use Office Scripts in Excel or Power Automate. In older versions of Excel, they may see the generic error: "We can't find this script. It may have been deleted by another user."
Eventually, this error message will be updated to: "Due to organizational policies, you can't access this script from this untrusted device."
Additionally, because Office Script files will be treated like text files, users on unmanaged devices may not able to access Office Scripts from the browser even under a policy that allows web-only access.
What you need to do to prepare:
If there are users in your tenant who are currently using Office Scripts on an unmanaged device, let them know that their access to Office Scripts may be disrupted and they should switch to a managed device to avoid disruption.
MC513601 — (Updated) Stream live events replacement service
>60 Days
Updated September 12, 2023: To ensure organizations have time to make necessary changes we are updating the timing of this change from September 15, 2023, to January 31, 2024.
This is an important message for customers who use Stream (Classic) or Yammer to create and host Stream live events. Microsoft will retire the Stream live events service on January 31, 2024. Microsoft Teams live events, with encoder support, will become your new platform to host and run live events.
For several years Microsoft has offered two venues for hosting live events -- Stream and Teams. While both services allow you to create live events, each had a slightly different set of capabilities and limitations. Our goal is to provide you with a single, simple, robust solution for hosting live events.
Teams live events with encoder support is the replacement service to Stream live events. Teams live events is now rolling out the general availability of encoder support (see Roadmap ID 84960), which will allow you to create, host and produce live events with the same functionality that you get with Stream. Teams live events will support 10,000 simultaneous event attendees and Real-Time Messaging Protocol input (RTMP-In). RTMP-in lets you create highly polished events that feature combined live streams, screen overlays, on-screen data and more.
Users will also get two other benefits from using Teams live events:
- The option to allow public anonymous attendees to attend Teams encoder live events.
- Transcription (RTMP transcript only) and recording are available for both public and in-tenant encoder events. With in-tenant encoder events, the organizer will have ability to edit the video recording and upload it to SharePoint so that attendees who missed the event can view it.
If you use Yammer to create and host live events you will be able to continue using Stream Live Events in Yammer until September 15, 2023. Additionally, you’ll soon be able to select Teams within Yammer to run your event.
When this will happen:
- Teams live events with encoder support began its general availability roll out on February 1, 2023, and we expect the rollout to complete by February 15, 2023.
- The Stream live events service will be retired on January 31, 2024.
How this will affect your organization:
We recommend that you begin using the Teams live events to schedule and host live events.
If your organization has Stream live events scheduled beyond January 31, 2024, please reschedule those events. Any Stream live events scheduled after January 31, 2024 will be automatically removed.
For more information see the links below:
- Stream live events replacement service FAQs
- How to set up a Teams live event
- How to produce a Teams live event
- Teams live events capabilities and limitations
Microsoft 365 IP and URL Endpoint Updates |
|
Documentation - Office 365 IP Address and URL web service
|
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.