- Home
- Public Sector
- Public Sector Blog
- January 2023 - Microsoft 365 US Public Sector Roadmap Newsletter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Newsworthy Highlights |
What’s New in Microsoft Teams | December 2022
These features currently available to Microsoft’s commercial customers in multi-tenant cloud environments are now rolling out to our customers in US Government Community Cloud (GCC), US Government Community Cloud High (GCC-High), and/or United States Department of Defense (DoD).
Microsoft 365 Government Community Call
Join Jay Leask and other members of the Government Community live on LinkedIn!
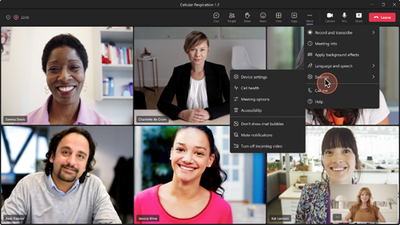
Where to Start with Microsoft Teams Apps in Gov Clouds
Customers in our Office 365 government clouds, GCC, GCCH, and DoD, are continuing to evolve how they do business in the hybrid workplace. As Microsoft Teams is the primary tool for communication and collaboration, customers are looking to improve productivity by integrating their business processes directly into Microsoft Teams via third-party party (3P) applications or line-of-business (LOB)/homegrown application integrations.
Microsoft 365 Government Adoption Resources
Empowering US public sector organizations to transition to Microsoft 365
Release News |
Users will be able to capture a short video and playback in-line in Teams desktop and mobile – GCC J...
Co-organizers will be able to create, manage and move between Breakout Rooms with equivalent capabil...
As one of the top asks from Poll users, Microsoft Forms will soon introduce multi-question poll to P...
DLP support for complex conditions
We will be updating the App protection status report and adding a new report, App configuration stat...
Microsoft Forms will enable images as choice options
References and Information Resources |
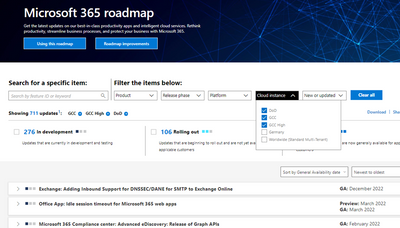
Microsoft 365 Public Roadmap
This link is filtered to show GCC, GCC High and DOD specific items. For more general information uncheck these boxes under “Cloud Instance”.
Stay on top of Microsoft 365 changes
Here are a few ways that you can stay on top of the Office 365 updates in your organization.
Microsoft Tech Community for Public Sector
Your community for discussion surrounding the public sector, local and state governments.
Microsoft 365 for US Government Service Descriptions
· Office 365 Platform (GCC, GCCH, DoD)
· Office 365 U.S. Government GCC High endpoints
· Office 365 U.S. Government DoD endpoints
· Microsoft Purview (GCC, GCCH, DoD)
· Enterprise Mobility & Security (GCC, GCCH, DoD)
· Microsoft Defender for Endpoint (GCC, GCCH, DoD)
· Microsoft Defender for Cloud Apps Security (GCC, GCCH, DoD)
· Microsoft Defender for Identity Security (GCC, GCCH, DoD)
· Azure Information Protection Premium
· Exchange Online (GCC, GCCH, DoD)
· Office 365 Government (GCC, GCCH, DoD)
· Power Automate US Government (GCC, GCCH, DoD)
· Outlook Mobile (GCC, GCCH, DoD)
Be a Learn-it-All |
|
Public Sector Center of Expertise We bring together thought leadership and research relating to digital transformation and innovation in the public sector. We highlight the stories of public servants around the globe, while fostering a community of decision makers. Join us as we discover and share the learnings and achievements of public sector communities. |

|
|

|
Microsoft Teams for Gov YouTube Video Series
The hub for teamwork in Office 365 GCC, GCC High, & DoD
Message Center Posts and Updates for Microsoft Teams in GCC |
Looking for what’s on the map for Microsoft Teams and only Teams in GCC?
Go right to the GCC Teams Feature Communications Guide
Message Center Highlights |
SharePoint Online / OneDrive for Business
MC481831 — OneDrive: Sharing Experience - Sensitivity Labels inside the Sharing Dialog
Microsoft 365 Roadmap ID 100714
We apologize that we did not communicate ahead of time for this feature release.
Sensitivity labels are used to classify and protect your organization's data. These labels are completely customizable, and admins can apply a label to a specific file based on the organization needs. We've now added sensitivity labels inside the Sharing dialog, to provide you the ability to see what labels have been applied to your files prior to sharing them.
When this will happen:
This feature is now available.
How this will affect your organization:
If the Admin chooses to set Sensitivity labels for the organization, users who interact with the OneDrive/SharePoint share control will be able to see these labels displayed inside the Sharing Dialog.
What you need to do to prepare:
You might want to notify your users about this new capability and update your training and documentation as appropriate.
Learn more about Sensitivity Labels here.
MC470136 — (Updated) Improved Upload experience and retirement of the ‘Get Data’ page in Power BI
Updated December 6, 2022: We have updated the timeline below. Thank you for your patience.
We will be retiring the ‘Get Data’ page in Power BI as well as the ability to connect to files from personal OneDrive accounts. Going forward, users can utilize a new streamlined Upload experience and we recommend connecting to files using OneDrive for Business or SharePoint for uploading local files.
When this will happen:
January 2, 2023 (previously December 8, 2022)
How this affects your organization:
Once this change is implemented, instead of going to the ‘Get Data’ page to upload files to a workspace, users can now use a streamlined Upload experience, found at the top of any workspace page. If users are looking to create datasets by importing Excel or CSV data, they'll be able to do this through the Dataset option under the New button at the top of any workspace page.
What you need to do to prepare:
We recommend updating any internal documentation related to uploading files or creating datasets within the Power BI service to direct users to start from the workspace they want to add the content into instead of going through the Get Data page
MC467233 — (Updated) OneDrive sync client will be blocked on virtualized machines configured with unsupported versions of FSLogix
Updated December 12, 2022: We have updated the timeline below. Thank you for your patience.
We have created a script which will allow customers to provide a list of VM names and remotely check to see if FSLogix is installed and if so, checks if the installed version greater is than the minimum version. It not only checks the version from the registry point of view, but also checks all the individual component versions as an extra measure. This script can be found here: GitHub
Note: If your organization does not utilize OneDrive on virtual machines, you can safely disregard this message.
OneDrive Sync client connections from a virtual machine using FSLogix releases older than FSLogix 2009 Hot Fix 1 are not supported and will get blocked starting March 2023. The hard block will show an error message, and the attempt to run the OneDrive Sync client on the machine will get blocked.
When will this happen:
The deployment will begin in March 2023 (previously January) and continue through April 2023 (previously February). Starting March 2023, any user connecting to OneDrive sync client with unsupported version of FSLogix will begin seeing error messages and OneDrive will not run on the machine. You can review the FSLogix release notes for more information.
How this will affect your organization:
Any enterprise that is using OneDrive in a virtual environment without a supported version of FSLogix is at risk of having OneDrive blocked for any users running on the virtual machine in an unsupported state. The OneDrive sync client will be blocked for any virtualized configuration using a FSLogix release older than FSLogix 2009 Hot Fix 1.
Users will see a dialog explaining that OneDrive cannot sync, and that they should contact their administrator. Once the user acknowledges this dialog, the OneDrive sync client will shut down.
What you need to do to prepare:
To avoid user impact, install the latest version of FSLogix on all virtualized machines using the OneDrive Sync client.
MC408994 — (Updated) Private drafts for SharePoint pages and news
Microsoft 365 Roadmap ID 85629
Updated December 22, 2022: We have updated the rollout timeline below. Thank you for your patience.
We’re adding the ability to create private drafts for pages and news posts. A private draft is visible only to the page author, the people the author chooses to share it with, and site admins. It's great for creating and editing content that’s not ready for others to see except the people you want to collaborate with.
When this will happen:
This update will roll out to Targeted Release customers starting early August and to all customers by late December (previously mid-November ).
How this will affect your organization:
Authors of SharePoint pages and news will be able to create private drafts. When a private draft is created, only the creator and site admins can see the page (including from within the Pages library). The creator can then share the private draft with other people to allow them to access and edit the page. They will also have access to the assets associated with the page which are stored in the site’s assets library.
Like all pages and news posts, only one person at a time can edit the draft. When the draft is published, its permissions are reset and everyone in your organization who has access to the site will be able to view it.
What you need to do to prepare:
You do not need to do anything to prepare for this update, but you may want to let your users know about these improvements.
More information available here: Create a private SharePoint page or news post
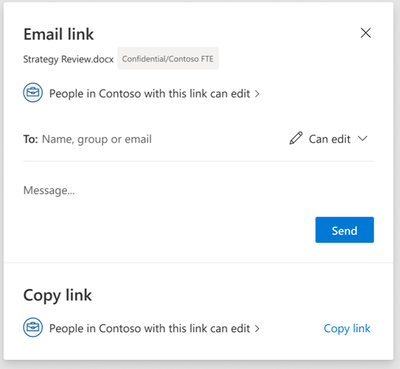
MC403644 — (Updated) OneDrive: Sharing Experience - Share Menu Dropdown
Microsoft 365 Roadmap ID 83727
Updated December 27, 2022: We have updated the rollout timeline below. Thank you for your patience.
We’re updating the Share button in Microsoft OneDrive to provide easy access to additional sharing options. When you select Share in OneDrive for Business on Web, you'll see a contextual menu with all choices available to you for sharing files or folders with your teammates.
When this will happen:
Targeted release: We will begin rolling this out in early October (previously mid-September) and expect to complete rollout by late October (previously late September).
Standard release: We will begin rolling this out in late October (previously late September) and expect to complete rollout by late January (previously mid-November).
How this will affect your organization:
Users who interact with the OneDrive/SharePoint share control will be able to see this new Menu.
· Share link, Email link or Send link: Email the file link directly to a one or more recipients.Note: users may see one of three different notations until finalized.
· Copy link: Copy a link to share with recipients directly.
· Manage Access: View and manage who has access to your files or documents.
Note: Some users may see this feature before others in your organization.
What you need to do to prepare:
There is no action needed from you at this time. You may want to notify your users about this new capability and update your training and documentation as appropriate.
Power Platform
MC489125 — Important information about Microsoft Power Automate emails
Microsoft Power Automate emails are moving to a new internal email provider. This change will result in emails from an additional Microsoft email account and IP addresses.
Description:
· As of Thursday, January 19, 2023, Microsoft Power Automate email notifications, such as approvals, flow alerts, and sharing notifications, will be sent from the following email addresses:maccount@microsoft.com
These emails will be sent from the IP addresses outlined here: Power Automate approval email delivery information.
Action Needed:
Please add these email addresses and IP addresses to your tenants' safe senders list so critical Microsoft Power Automate emails are not missed.
Please contact Microsoft Support and reference ticket number ICM347570815 if you have any questions.
MC482511 — Announcing Public preview of permanent deletion of users in Power Platform
We are pleased to announce that you can now delete and remove users with a disabled status in Power Platform. The rollout of this feature preview has already begun and is expected to be available globally by the end of December 2022.
How this will affect your organization
You may have deleted Microsoft Azure Active Directory (Azure AD) users who were created in your Power Platform environments. These deleted Azure AD users remain in Power Platform with a disabled status and can stay in the environments forever.
You may want to delete users with disabled status for the following reasons: Are no longer active in the tenant
· Have moved out of the environment's security group
· No longer has a license to use the application
· To comply with regulatory compliance
What you need to do to prepare:
This capability is available in all tenants for preview; however, it needs to be enabled in each environment where you want to delete users. To preview this capability, select a non-production environment on the Power Platform Admin Center and go to Settings/Product/Features and enable the "Delete disabled users (preview)" switch.
To learn more visit:
· Delete users from environments - Power Platform
· How to permanently delete your Power Platform users
MC481284 — Important Information about your Microsoft Power Automate service
Starting on January 10, 2023, support for the "Submit as a template" button will no longer be available. This functionality enables users to submit flow templates as candidates for Power Automate's public template gallery. As a result, users will no longer be able to submit their flows as templates using the "Submit as template" button.
How does this affect me?
Following deprecation of the "Submit as template" experience, we will be introducing an alternative submission process.
Action Needed:
No action is required at this time. Future updates to the submission process can be viewed here.
Please contact Microsoft Support if you need further assistance.
Microsoft Teams
MC494734 — Teams update: Expanded view of the profile card in Teams
Microsoft 365 Roadmap ID 109526
We’re adding a new feature to Teams.
Beginning in February, users in your organization will be able to use expanded views of the profile card in Teams. The expanded view is already available in Outlook and includes more information, like an overview of the profile, contact information, organizational chart, and LinkedIn tab.
When will this happen:
We will begin rolling out this feature in February and expect to complete the rollout in April.
What you need to do to prepare:
No preparation is needed for this change. For more information about what users can see on profile cards, see Profile cards in Microsoft 365.
MC492912 — Microsoft Teams Live Event Attendee Improvements
Microsoft 365 Roadmap ID 84960
In preparation for the new RTMP-In Support for Microsoft Teams Live Events, the Teams Live Event Attendee Experience will soon be updated to better support this scenario. This will include increased reliability for the attendee experience and include the ability for attendees to watch the Teams Live Events in a separate window, which users can do on the Web today.
When this will happen:
We will begin rolling out in mid-December 2022 and expect to complete rollout in late January 2023.
How this will affect your organization:
Attendees of Teams Live Events will receive a more optimal attendee experience including increased reliability and the ability for attendees to watch the Live Event in a separate window which they can do in the Web today.
What you need to do to prepare:
You do not have to do anything to receive this update.
MC492903 — Microsoft Teams: Presenter Window Improvements in Screen Sharing
Microsoft 365 Roadmap ID 100392
In Microsoft Teams, presenters will soon have the new Presenter window at their disposal while screen sharing.
When this will happen:
Preview: We will begin rolling out for preview in early January 2023 and expect to complete rollout in mid-January 2023.
Production and GCC: We will begin rolling out in early February 2023 and expect to complete rollout by late February 2023.
GCC-H: We will begin rolling out in late February 2023 and expect to complete rollout by mid-March 2023.
DoD: We will begin rolling out in early March 2023 and expect to complete rollout by mid-March 2023.
How this will affect your organization:
The new presenter window will give more awareness of meeting activity while users are sharing screen or multitasking away from the main meeting window.
In the new presenter window, controls are docked at the top, which makes active speakers' faces clearly visible. Raise hands and other important meeting notifications are surfaced for easier recognition.
Note: Presenter window updates are for desktop clients only.
What you need to do to prepare:
There is no action required from you at this time to enable this feature. You may want to consider updating your training and documentation as appropriate.
MC485792 — Fixing timestamp format in Teams meeting Transcripts files
We will be rolling out a fix to update the timestamp format in .docx and .vtt Teams meeting transcript files to follow the WebVTT timestamp standard. More specifically, the current timestamp, for example, 0:0:0.0 --> 0:0:1.890, will be updated to 00:00:0.0 --> 00:00:1.890 after this fix gets rolled out.
Note: If your organization does not have a dependency on the timestamp of .docx or .vtt transcript files you can safely disregard this message.
When this will happen:
We will begin rolling this out in mid-January and expect to complete by the end of January.
What you need to do to prepare:
If your organization takes any dependencies on the timestamp of .docx or .vtt transcript files for discovery, compliance, etc, you will need to update to accommodate the WebVTT timestamp standard.
MC485628 — Microsoft Teams: Mention Everyone in chat
Microsoft 365 Roadmap ID 101573
Similar to how users mention individuals in chat, users will now have the option for “Everyone” within their options for mentions. After typing @, users will see the same people results they see today, but a new option, “Everyone” will be available. By selecting Everyone and sending the message, a notification will be sent to all users in the group chat based on their selected notification settings. Users can adjust how they are notified within their Teams notification settings.
When this will happen:
We will begin rolling out in late January and expect to complete rollout to desktop, iOS and Android in late February 2023.
How this will affect your organization:
Users will now have a new type of mention within their group and meeting chats. This will automatically appear within chats with more than 2 users and any meeting chat. When used, recipients will receive a notification in their feed, which will show the user who has sent the message and that they have "mentioned Everyone". These notifications can be disabled or changed via chat notification settings. If a user sends a message where they mention an individual and use "Everyone", the prioritization will be given to the individual mention.
In group chats with more than 50 users, we will alert the sender that their message will notify a large number of users. This ensures that senders are fully aware of what will happen when they send a message with Everyone tagged.
What you need to do to prepare:
You may want to notify your users about this new mention type and give them awareness that they can adjust their preferences for notifications within the settings menu.
MC485096 — General availability - Receive all chats messages in all scopes
Microsoft 365 Roadmap ID 100883
The resource-specific consent (RSC) permissions model for receiving all message, originally developed for Microsoft Teams Graph APIs, is being extended to bot scenarios. This feature was available for the channel scope and now is being extended to chat scope. With RSC, conversation owners can consent for a bot to receive all user messages in standard channels and chats without being @mentioned.
When this will happen:
Available now
How this effects your organization:
When developing Teams apps, this feature will enable a bot defined in the app manifest to receive all conversations messages without being @mentioned in relevant contexts where the permissions apply.
What you can do to prepare:
For more details, review: Receive all conversation messages with RSC
This is for your information only and no action is needed.
MC482567 — Microsoft Teams: Meeting Toolbar Usability Improvements
Microsoft 365 Roadmap ID 102065
The updated Microsoft Teams meeting toolbar makes navigating meetings and discovering new features and capabilities easier than ever, including the ability to seamlessly switch between views and menu options.
When this will happen:
Preview: We will begin rolling out in early January.
GA and GCC: We will begin rolling out in mid-January and expect to complete rollout by late February.
GCC-H and DoD: We will begin rolling out in early February and expect to complete rollout by late March.
How this will affect your organization:
Users will be able to raise hands from the meeting toolbar with the dedicated raise hand button. Users can navigate the More menu easier from sub-menu groupings. Users can also switch their views seamlessly from the new View button with view options that include gallery, together mode, and other views.
What you need to do to prepare:
No preparation is needed. You may want to update your training materials indicating the improvements in meeting toolbar.
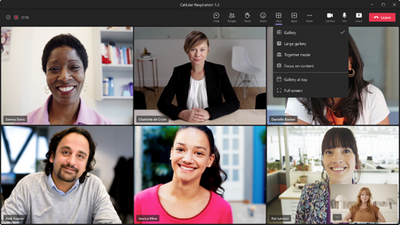
MC482564 — Microsoft Teams: Automatically View up to 49 Videos (7x7) in Teams Meetings
Microsoft 365 Roadmap ID 103612
Microsoft Teams Meetings is updating the number of videos a user can see at once in a meeting. With this update, users will be able to automatically see up to 49 videos (7x7) on their screen by default.
The actual number of videos seen by a user in Gallery will depend on:
· hardware/device capabilities
· internet bandwidth
· whether content is in a separate window or not
When this will happen:
We will begin rollout in early January and expect to complete rollout by mid-January.
How this will affect your organization:
Users will be able to automatically see up to 49 videos (7x7) on their screen by default in a meeting without an explicit action.
Before this update, Microsoft Teams Meetings supported a maximum of 9 videos (3x3) on the screen by default (in Gallery view). To see more than 9 videos on the screen, the user would need to manually select the Large Gallery view. Although with the new update users won't have to select this, Large Gallery view will still continue to exist as an option.
Note: This enhancement will be supported on devices that meet hardware requirements (CPU, memory, etc.)
What you need to do to prepare:
No explicit user action is needed to enable or use this feature. You may want to update your user documentation to inform users of this update.
MC481829 — Microsoft Teams Support for Co-organizer to Manage Breakout Rooms
Microsoft 365 Roadmap ID 105014
The Microsoft Teams Breakout Rooms feature enables co-organizers to create, manage and move between Breakout Rooms like meeting organizers. We will be updating this feature for co-organizers to have the ability to:
· Create rooms
· Configure room settings, including appointing additional Breakout Room managers
· Assign participants
· Add/Remove rooms
· Open/Close rooms
· Send announcements
· Rename/Delete rooms
When this will happen:
Preview: We will begin rollout in early-December and expect to complete rollout by mid December.
Standard Release: We will begin rollout in mid-January and expect to complete rollout by end January.
Government Clouds: We will begin rolling out in early March and expect to complete rollout by mid-March.
How this will affect your organization:
Users assigned as the co-organizer role in the main meeting will be able to create and manage Breakout Rooms on behalf of the organizer; they will also automatically be assigned the co-organizer role in Breakout Room meetings and will be able to access/modify meeting options for any Breakout Rooms too.
When rooms are opened, co-organizers will be treated like organizers with regards to the ability to join and move freely between Breakout Rooms.
Note: co-organizers won't be able to pre-create Rooms and pre-assign participants ahead of meeting start. Breakout Room Creation/Management will only be possible during live meeting for co-organizers.
What you need to do to prepare:
No preparation is needed. You may want to update your training materials indicating that the co-organizer role is now supported for managing Breakout Rooms.
MC481196 — Add people to a group chat from compose box via @ mention
Microsoft 365 Roadmap ID 97736
Teams Chat is for fast-paced communication, and we want to ensure nothing gets in the way. Pull in via @mention provides a short cut to the add-dialog saving you time from realizing the person isn’t already in the chat and navigating (2-clicks) to the add-dialog manually. Users can now add someone to a group chat directly from the compose box via @ mention.
When this will happen:
We will begin rolling this out in early December and the rollout will complete late December 2022.
What you need to do to prepare:
Users or admins do not need to do anything to prepare.
MC480719 — Microsoft Teams Rooms Companion Device Experience enhancement - Optimize video gallery for in-room participants
Microsoft 365 Roadmap ID 96212
When joining a meeting in a Microsoft Teams Rooms with a personal laptop running Microsoft Teams, the video galleries on both the Microsoft Teams Room and laptops will be optimized to display only remote attendees and will not display the room video or other in-room attendees' videos on the room gallery or the personal laptop. (Proximity Join with Microsoft Teams Rooms is required).
When this will happen:
This feature will begin to roll out in Teams desktop client (Windows/MacOS) in early December and complete in late December.
How this will affect your organization:
This feature will be available on all Teams desktop clients. To use the feature with Microsoft Teams Rooms, please ensure that the Bluetooth beaconing setting is enabled on all Microsoft Teams Rooms devices. Bluetooth must also be enabled on personal laptop devices that are joining a meeting in a Microsoft Teams Rooms.
When a user joins a meeting in a Microsoft Teams Room on their personal desktop device using Bluetooth proximity join, their in-room presence on the Teams gallery will not be shown on the Microsoft Teams Rooms device or other in-room personal desktop devices. In-room videos will only be shown to remote attendees and the in-room video gallery will be optimized for remote attendees only.
This in-room experience can be overridden on any in-room device including the Microsoft Teams Rooms by selecting on an in-room participant in the People panel and selecting either “Pin for me” or “Spotlight for everyone” command.

What you need to do to prepare:
There is nothing you need to do to prepare.
MC466199 — (Updated) Microsoft Teams: Users ability to delete chats
Microsoft 365 Roadmap ID 90723
Updated December 09, 2022: Due to an issue with admin controls in TAC that we are actively working on fixing, please refer to the PowerShell documentation to control the setting for enabling or disabling delete chat capability. Link: Set-CsTeamsMessagingPolicy
Users will be able to delete 1:1 chats, group chats, and meeting chats if they are a participant in Microsoft Teams. This permanently deletes the chat only for the user, other people in the chat and conversation history are not impacted.
When this will happen:
We will begin rolling out in early December and expect to complete rollout by mid-December.
How this will affect your organization:
Once available, users will be able to delete 1:1 chat threads or chat groups from the Teams desktop or mobile application. By selecting the ellipsis, users can select the Delete option to clear their chat list.
If Admins want to turn off this capability, they can do so from the admin portal under messaging policies. If turned off, users in the tenant will no longer see the delete option for their chats.
What you need to do to prepare:
This feature will be enabled automatically and there is no action required at this time.
MC439275 — (Updated) Microsoft Teams Detailed Call History Feature Update
Microsoft 365 Roadmap ID 98455
Updated December 15, 2022: We have updated the rollout timeline below. Thank you for your patience.
Users will now get a more comprehensive view into whether calls were transferred or forwarded in Microsoft Teams' call history.
When this will happen:
General Availability: We will begin rollout in mid-October (previously late September) and expect rollout to be completed by late October (previously mid-October).
Government Clouds: Rollout will begin in late October and is expected to be completed by mid-January 2023 (previously early December).
How this will affect your organization:
When users go into their call history in Teams, they will now see group calls, transferred calls, and forwarded calls. There will be no impact to user workflow when this feature rolls out.
What you need to do to prepare:
Please check for updates once feature has been released.
MC423128 — (Updated) Dynamic caller ID in Voice-enabled channels for government clouds: GCCH, DOD
Updated December 13, 2022: We have updated the rollout timeline below. Thank you for your patience.
Last year we enabled the capability where agents can use Dynamic Caller ID to call on behalf of a Call Queue or Auto Attendant from within Voice Enabled Channels. We are now bringing this capability to government clouds including GCCH and DOD.
We apologize for not meeting our commitment of providing notification prior to implementation and for any inconvenience.
When this will happen:
This has begun rolling out and will be complete by end of March (previously end of November).
How this affects your organization:
You can assign outbound caller ID numbers for the agents by specifying one or more resource accounts with a phone number. Agents can select which outbound caller ID number to use with each outbound call they make.
What you can do to prepare:
Review the Additional Information and consider updating your training and documentation as appropriate.
MC400565 — (Updated) Suggested Replies in Group Chats on Teams Desktop
Microsoft 365 Roadmap ID 95618
Updated December 7, 2022: We have updated the rollout timeline below. Thank you for your patience.
Suggested Replies are now available in group chats on Teams Desktop, allowing you to select a quick response when you are mentioned in a group chat or when you are having a 1:1 conversation within a group chat.
When this will happen:
· Standard: Early September 2022
· GCC: Early September 2022
· GCC-High: Mid-January 2023 (previously early October 2022)
· DoD: Late February 2023 (previously early November 2022)
How this will affect your organization:
Once available, users will be able to quickly reply to a given message by tapping on a suggested reply from within a group chat.
What you need to do to prepare:
This feature ships default on; review Manage messaging policies in Teams.
If you wish to disable this feature in your tenant, please disable the Suggested Replies setting that is found in Messaging Policies.
Users also have a setting within the app so they can disable the feature.
MC392295 — (Updated) Disable chat write access for anonymous or unauthenticated users
Microsoft 365 Roadmap ID 91142
Updated December 8, 2022: We have updated the rollout timeline below. Thank you for your patience.
Financial institutions consider chat messages as a form of data exfiltration, so it's imperative for IT admins to gain flexibility and control over chat access for anonymous or unauthenticated users. The latter may be expected to join Teams meetings, but they should be restricted from seeing and accessing any type of electronic communication on chat. This feature provides additional security by only disabling chat write access for non-federated users and unauthenticated users who join Teams meetings through a link, so it must be used in conjunction with disabled meeting chat policy applied to financial advisors to remain compliant.
When this will happen:
· Standard: early June through mid-July 2022
· GCC: late July through mid-August 2022
· GCC High: late August through late November 2022 (previously early September 2022)
· DoD: mid-September through late January 2023 (previously early December 2022)
How this affects your organization:
With this change IT admins can now disable chat write access at the policy level for non-federated users and unauthenticated users who join Teams meetings through a link.
What you can do to prepare:
There are two ways IT admins can disable chat write access for non-federated users and unauthenticated users who join Teams meetings through a link:
· PowerShell: Admins can run the syntax [-MeetingChatEnabledType <String>] with current supported values Enabled, Disabled, or EnabledExceptAnonymous.
· Teams Admin Portal: Admins can select the option, "Turn it on for everyone but anonymous users" in the "Chat in meetings" dropdown and apply this meeting policy to a subset or all tenant users.
Note: the scope of EnabledExceptAnonymous or "Turn it on for everyone but anonymous users" is limited to disabled write access. Once this meeting chat policy is applied to user/s, an organizer cannot override this policy through meeting options.
MC337332 — (Updated) Export feature in Teams Admin Center
Microsoft 365 Roadmap ID 85704
Updated December 12, 2022: We have updated the rollout timeline below. Thank you for your patience.
Teams admin center is adding support for downloading the data from the list pages like teams list page, members list page, channels list page and users list page. The downloaded data will be in the form of a CSV file. Admins can click on the “Export” icon placed on the table headers in these pages to generate the data and download the CSV from the downloads section in the header of the Teams admin center.
When this will happen:
We will begin rolling this out in early March and expect to complete the rollout by late January (previously late November).
How this will affect your organization:
Admins will now see a downloads icon in the header.
The downloads section will display the list of all entries that were generated in the last 24 hours. This section also is personalized for each admin in an organization but they cannot see exported files from other admins in their organization.
This new feature will enable admins to apply filters on these list pages and then export the filtered list of items instead of exporting the entire list.
What you need to do to prepare:
You might want to notify your Teams administrators about this new capability and update your training and documentation as appropriate.
Microsoft Viva
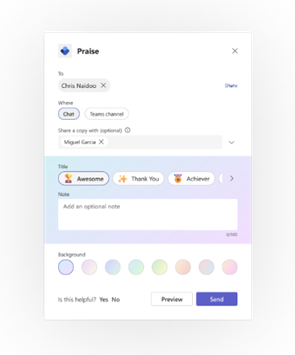
MC489162 — Sharing a copy of praise in Viva Insights app in Teams and Teams Messaging Extension
Microsoft 365 Roadmap ID 106122
Praise in Microsoft Teams is designed to appreciate the effort that goes into the wide-ranging, collaborative work that Teams users do. Users can send praise to their colleagues through the messaging extension pinned to the Teams messaging bar or through the Microsoft Viva Insights app in Teams. For both, admins can use the Microsoft Teams admin center to enable/disable Praise.
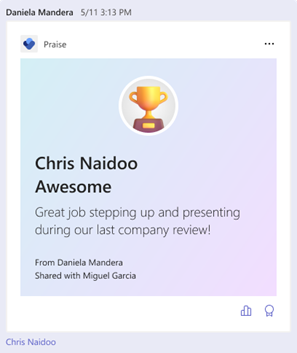
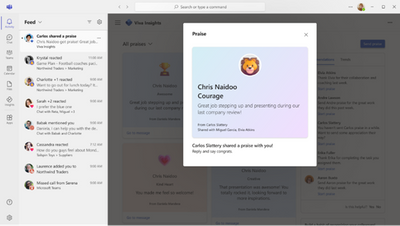
With the upcoming updates, users with Viva Insights subscriptions will have the ability to share a copy of praise they send. Shared recipients will be notified via Teams and can see praise details in the Microsoft Viva Insights app in Teams.
When this will happen:
We will begin rolling out in January 2023 and expect to complete rollout by early February 2023.
How this will affect your organization:
This feature is available for users with Viva Insights subscriptions. In the praise composer within Teams messaging extension and Microsoft Viva Insights app, the sender of praise can share a copy of the praise with a user or a distribution list. When praises are shared, the copied peoples’ names are displayed within the praise card below the sender’s name.
Shared recipients will be notified via Teams and can see the praise card with details including sender, praise title and message in the Microsoft Viva Insights app in Teams. Shared recipients can also see the history of praises shared with them in their praise history page.
What you need to do to prepare:
Refer to Praise with Viva Insights | Microsoft Docs which will be updated in sync with this roll out.
Exchange Online
MC488586 — Announcing Retirement of Remote PowerShell (RPS) protocol in Exchange Online PowerShell
You might already be aware that we made REST-based Exchange Online PowerShell v3 module generally available in September 2022 (read more here: Exchange Online PowerShell V3 Module General Availability). We will now be retiring RPS protocol from the beginning of June 2023. Instead, we recommend the utilization of the v3 module, which is where we will continue to invest our development resources.
When this will happen:
We'll be gradually rolling this out to customers in early June 2023, and the roll out will be completed by the end of June 2023.
How this will affect your organization:
You are receiving this message because our reporting indicates your organization may be using this RPS through New-PSSession or through Exchange Online PS v1 and v2 modules.
The users will no longer be able to use RPS protocol, when this change is implemented.
What you need to do to prepare:
If you are using RPS to establish an Exchange Online connection, you will not be able to do so after July 1, 2023. If you use the following, then you are using RPS:
· Connection using New-PSSession
· Exchange Online PowerShell v1 and v2 modules
· Any newer version of Exchange Online PowerShell module with the -UseRPSSession parameter
To switch to the v3 module and use REST cmdlets, take the following steps:
If you are using New-PSSession to establish an RPS connection:
1. Install the latest Exchange Online Management v3 module from here: ExchangeOnlineManagement 3.0.0.
2. Use Connect-ExchangeOnline instead of New-PSSession to establish connection.
If you have installed any module earlier than v3:
1. Uninstall previous versions of ExchangeOnlineManagement module by running "Uninstall-Module ExchangeOnlineManagement" from an elevated (admin) PowerShell command prompt.
2. Install the latest Exchange Online Management v3 module from here: ExchangeOnlineManagement 3.0.0.
3. Discontinue the use of -UseRPSSession parameter (if you are using it.)
We are excited about providing you with a more secure and performant environment, and we remain committed to our journey to empower you with the most modern features and tools. If you have questions/concerns, please leave comments here or email us directly at RPSdeprecation@service.microsoft.com
MC486289 — Pausing the Briefing emails from Microsoft Viva
Based on customer feedback we’re taking some time to improve the content of the Briefing emails from Microsoft Viva to be more personalized for each recipient. We will pause sending these emails in early 2023 and will share an updated Briefing email roadmap later in 2023.
When this will happen:
The pausing of the email service will roll out to end users no earlier than January 15th 2023 and will be done by February 1st, 2023
How this affects your organization:
The result of this change is end users within your organization will no longer receive the daily briefing email from Microsoft Viva.
Users who rely on the daily briefing email functionality like meeting prep and outstanding task reminders, booking focus time, and recommendations to improve work patterns can instead visit the Viva Insights Outlook add-in or the Viva Insights app in Teams and web.
What you need to do to prepare:
· For information on the Briefing email and the functionality that will be paused for your end users please see Briefing email overview | Microsoft Learn
· For information on the Viva Insights application in Teams and on the web – which includes functionality like outstanding task reminders, booking focus time, and recommendations to improve work patterns - please see: Viva Insights app | Microsoft Learn
· Review and assess the impact on your organization and end-users
MC485092 — Microsoft Bookings - Old web version will be retired on 01/31/2023
Microsoft Bookings is part of the Microsoft 365 suite of products and is available through most commercial SKUs. It is available on the Web - Microsoft Bookings. The new version of Bookings was launched last year and is the default experience for all new users. This version addresses issues and introduces many new features.
Currently users have an option to switch back to the old version. But, going forward, we are retiring old version of Bookings.
When this will happen:
January 31, 2023
How this will affect your organization:
If your organization has users who use the old version:
We initially communicated the migration date of 11/30 which we have extended by 2 months. All users will now be migrated to the new version post January 31, 2023. This will not impact any of your existing calendars and there will be no loss of data. We would recommend you ask users in your organization to switch to the new version ahead of the retirement date to familiarize themselves with it. Depending on the practices of your organization, you might also want to consider any requirements around training your staff.
If your organization does not have users who use the old version:
There is no impact or loss of data.
MC485091 — Microsoft Bookings - Mobile Apps will not be available on Google Playstore and Apple App Store from 01/31/2023
Microsoft Bookings is part of Microsoft 365 suite of products and is available through most commercial SKUs. It is currently available on the Web - Microsoft Bookings, as a Teams App and also on Mobile Apps on Google Playstore and Apple App store.
Bookings will continue to exist on the web and as an App on Teams and there won’t be any loss of data for existing users.
When this will happen:
January 31, 2023
How this will affect your organization:
If your organization has users who use the Bookings Mobile Apps:
We initially communicated the app removal date of 11/30, which we have extended by 2 months. After January 31, the Bookings Mobile Apps on Google Playstore and Apple App store will no longer be available for download. Any new user who is searching for the Bookings App will not be able to find or install the Apps.
Any existing user (who already has the App installed), will be able to continue to use the App but will not receive any support or updates.
Users who want to access Bookings on their mobile devices are recommended to access Bookings web page (https://book.ms) through their mobile browser from 02/01 onwards.
If your organization does not have users who use the Mobile Apps:
There is no impact or loss of data.
MC485090 — Microsoft Bookings - Custom domain support
You can now specify which domain will be used from the domain list for Bookings using OWA mailbox policy. Once default domain policy is configured and deployed, any new booking calendars created will have the configured domain in the SMTP address.
For example: Booking pages can get created with a domain “contoso.com” instead of “contoso.onmicrosoft.com”.
You are also allowed to Configure domain for specific users. When users with the custom OWA policy create a Booking calendar, it would get created with the custom domain and not the default domain
When this will happen:
Custom domain support is now available to all tenants worldwide.
How this will affect your organization:
Your admin will now have the option to add custom domains and define domain to be used for Bookings calendars. They can now also configure a domain for specific users.
This change will not impact Bookings calendars that have already been created. Only new calendars will be created using the configured domain.
What you need to do to prepare:
This is a great new feature which can benefit your organization. You may wish to inform your users to utilize this feature and share the documentation Custom domain support in Bookings
MC484251 — Outlook: S/MIME sensitivity label support natively on Outlook for Windows
Microsoft 365 Roadmap ID 100062
Outlook for Windows will support S/MIME (Secure/Multipurpose Internet Mail Extensions) sign and encryption as sensitivity label outcome. If admins define the label to have S/MIME sign, encryption, or both and emails with those labels will enforce S/MIME accordingly.
When this will happen:
Current Channel Preview: We have started rolling this out and expect to complete by mid-December 2022.
Current Channel: We will begin rolling mid-Dec 2022 and expect to complete by early Jan 2023.
How this will affect your organization:
If you are using Outlook for Win32 built-in labeling, and you have S/MIME label enabled, you will see those S/MIME label shows up in your Outlook for windows Sensitivity dropdown menu, and you could apply those labels with S/MIME certificate to enforce S/MIME sign or encryption, or both.
What you need to do to prepare:
If you do not use S/MIME on emails, this will not impact you.
If you do want to use S/MIME on emails, please refer https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-office-apps?view=o365-... to how to set that up on labels.
MC466195 — Outlook for the web - End user Reporting integrated with Microsoft Defender for Office 365 (Exchange Online Protection)
Updated November 15, 2022: We have updated the content below with additional information. Thank you for your patience.
New built-in report buttons will be added to Outlook on the web (OWA) starting the end of November 2022. Admins can control the appearance and behavior of these buttons that allow users to report emails as phishing/ junk / not junk from the User Reported setting page in the Microsoft 365 Defender portal (security.microsoft.com). Admins can also customize where messages get reported to (custom mailbox, Microsoft, or both) and what the user sees when they report a message from these buttons.
Information to keep in mind:
· Other Outlook clients such as Mac, Windows 32, Mobile (iPhone and android) will remain unaffected by this change. The reporting buttons in other Outlook clients are still being worked upon.
· If you have the reporting feature turned off in the Microsoft 365 Defender user reported settings page or are using a third-party add-in, the report buttons in OWA won't be visible.
· The Microsoft reporting add-in (the Microsoft report message add-in & Microsoft phishing add-in) will be supported till further notice. It will exist alongside the built-in reporting buttons for the time being, but the goal is to have a consistent button reporting experience across all the Outlook clients in the future.
· The selections you make on the user reported settings page will determine the reporting experience for your users whether they choose the add-in or built-in reporting option in Outlook. Either option will report to the same place (Microsoft, custom mailbox or both) based on the settings selected.
· The built-in reporting buttons in OWA will not include the customizable pre and post reporting pop-ups like the Microsoft reporting add-in currently does. We are working to include the pop-ups in 2023.
· The settings for enabling/disabling the popup's during reporting won't be honored during this migration. So, you need to disable the popups if it has been enabled again.
Microsoft 365 Roadmap ID 101515
When this will happen:
We will begin rolling out the change for Outlook for the web by the late November 2022 with the goal of having it completed late December 2022.
How this will affect your organization:
If you are using Microsoft reporting add-ins in Outlook for web, your users will see two reporting surfaces - one from the built-in Outlook buttons (added by this change) and one from the add-in. Both options will behave the same for the users (except for the customized pop-ups) and the reported messages will end up in the same place, causing minimal disruption.
What you need to do to prepare:
No changes are required from your end as your current settings in the user reported settings page will not be changed.
If you have any feedback, please provide it from this Message center post using the text box after you do thumbs up or thumbs down as it will directly reach the responsible team
MC373880 — (Updated) Migrating the Safe Links Block List to Tenant Allow Block List
Updated December 13, 2022: As a reminder Tenants will have until January 2023 to review and take action on any entries in the Safe Links Block List that were unable to be migrated. Any entries that are unable to be migrated will be marked as such and organizations will have the ability to resolve that entry and run the migration again. In January 2023 the Safe Links Global Block List will be retired.
We have stopped the automated migration efforts to migrate all entries from your Safe Links Block List to the Tenant Allow Block List. Organizations will have the ability to review and take action on the entries that were unable to be migrated. Any entries that are unable to be migrated will be marked as such and organizations will have the ability to resolve that entry and run the migration again. Tenants will have until January 2023 to complete this activity, at which point the Safe Links Global Block List will be retired.
Note: Any entry migrated from the Safe Links Block List to the Tenant Allow/Block List will adopt the behavior of TABL. This means that any message with the URL present will be moved to Quarantine. If deleting an already migrated entry from TABL, it needs to be removed from BlockURLS to avoid migration.
As a reminder beginning in June tenants will no longer have the ability to add to the Safe Links Block List in the Global Setting menu. Then we will attempt to migrate the Safe Links Block List to the Tenant Allow Block List (TABL) on behalf of the organization. Any entries that are unable to be successfully migrated, they will be marked as such in the Block List and organizations will have the ability to take action as needed beginning in July.
Another update will be sent closer to July as a reminder for tenants to review the migration status of the Block List. Beginning in June organizations will no longer have the ability to add to the Safe Links Block List in the Global Setting menu. Following this, we will attempt to migrate the Safe Links Block List to the Tenant Allow Block List (TABL) on behalf of the organization. For any entries that we are unable to migrate, they will be marked as such in the Block List and organizations will have the ability to take action as needed.
When this will happen:
· Early June: Organizations will no longer have the ability to add to the URL/Domain entries to the Safe Links Block List in the Global Settings flyout and we will attempt to migrate all the entries in an organization's Safe Links Block List to TABL on their behalf
· Mid-June through December: Organizations will have the ability review entries that were not able to be migrated and resolve the issue(s)
· January: The Safe Links Block List will be retired
How this will affect your organization:
Organizations who are utilizing the Safe Links Block List will need to review the list to ensure all entries were migrated successfully. Any entries that are unable to be migrated will be marked as such and organizations will have the ability to resolve that entry, at which point migration will run again.
Organizations will use the Tenant Allow Block List to manage URL/Domain blocks moving forward.
What you need to do to prepare:
In June an update to this Message center post will be sent notifying organizations that the first migration has been completed and they will need to review their Safe Links Block Lists for potential actions.
Microsoft Purview
MC489169 — Microsoft Purview | Data Loss Prevention: Support for complex conditions (preview)
Microsoft 365 Roadmap ID 103620
Coming soon to public preview for Microsoft Purview Data Loss Prevention (DLP), we're introducing support for complex conditions as part of a new DLP rule authoring experience.
When this will happen:
Rollout to preview will begin in early January and is expected to be complete by end of January.
How this will affect your organization:
With this new DLP rule authoring experience, you will be able to create complex conditions while configuring your Microsoft Purview Data Loss Prevention policies. You will be able to create conditions with AND/OR combinations with the ability to create groups to achieve condition combinations like A AND (B OR C).
What you need to do to prepare:
To start using the new DLP authoring experience (preview), opt in using the toggle in Data Loss Prevention > Settings.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal:
· Microsoft Purview compliance portal for GCC cloud environments
· Microsoft Purview compliance portal for GCC-High cloud environments
· Microsoft Purview compliance portal for DoD cloud environments
Learn more: Learn about data loss prevention
MC442111 — (Updated) Microsoft Purview Information Protection: User-defined permissions support domain name restrictions
Microsoft 365 Roadmap ID 98131
Updated December 12, 2022: We have updated the rollout timeline below. Thank you for your patience.
Coming soon to public preview and general availability, we're updating the options for custom permissions, also referred to as user-defined permissions, to support domain name restrictions.
When this will happen:
Rollout to public preview will begin in early December (previously mid-November) and is expected to be complete by late December (previously late November).
Rollout to general availability will begin in early February (previously early December) and is expected to be complete by late February (previously late December).
How this will affect your organization:
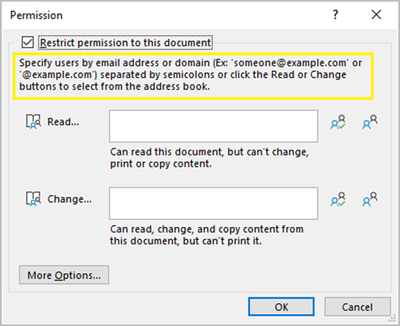
Within Microsoft Office files (Word, Excel, PowerPoint), when you choose a sensitivity label configured for user-defined permissions, you can now use domain names to restrict file access to specific individuals, or to all individuals from that domain. For example, you can specify "someone@example.com" or "@example.com" and permissions will be restricted based on those parameters.
What you need to do to prepare:
If you have previously configured user-defined permissions for your organization, no further action is needed to enable this feature.
Configure and manage sensitivity labels in the Microsoft Purview compliance portal.
Learn more:
· Let users assign permissions
· Support for organization-wide custom permissions
MC301684 — (Updated) General availability of AIP client and scanner audit logs in Microsoft 365 Audit and Activity explorer
Updated December 22, 2022: We have updated the rollout timeline below. Thank you for your patience.
Azure Information Protection (AIP) administrators will soon be able to access data in Microsoft 365 compliance center Audit logs and Activity explorer, in addition to the AIP Analytics (Preview) portal.
Microsoft 365 Roadmap ID 89777.
When this will happen:
Rollout will begin in early December 2021 and is expected to be complete by late January 2023 (previously mid-November 2022).
How this will affect your organization:
As part of our unified labeling and analytics experience across the Microsoft Information Protection (MIP) solution, we are expanding your ability to access and review data logged by AIP client, scanner, and MIP SDK beyond the existing AIP Analytics (Preview) portal.
· With this update, audit logs reported by the AIP client, the AIP scanner, and MIP SDK flowing today into the Log Analytics workspace will also be available in Microsoft 365 Audit logs.
· Additionally, you can use the Activity explorer screen for additional insights into labeling activity and history.
What you need to do to prepare:
Your data will be available in Activity Explorer, and you will be able to explore your AIP audit logs in Microsoft 365 portal. No action is needed as audit log data will flow into Activity Explorer by default. If you wish to opt-out, please follow the procedure explained here.
Administrators will be able to continue exploring AIP Audit logs in the Log analytics workspace in the AIP Analytics (Preview) portal. This is a supplemental access point.
You might want to notify your administrators about this new capability and update your training and documentation as appropriate.
Get started with Activity explorer in the Microsoft 365 compliance center:
· Microsoft 365 compliance center for GCC
· Microsoft 365 compliance center for GCC-H
· Microsoft 365 compliance center for DoD
Learn more:
· Azure Information Protection unified labeling client - Version release history and support policy
· Get started with Activity explorer
· Search the Audit log in the Microsoft 365 compliance center
Microsoft Defender
MC492896 — Updated opt-in setting for Microsoft Defender for Identity
Over the last few months, the experiences and functions of Microsoft Defender for Identity have been made available in Microsoft’s extended detection and response (XDR) platform, Microsoft 365 Defender. Merging identity data and functions into this XDR experience is a valuable addition to a security teams capabilities, with identity providing important context to detection logic and investigation potential.
Since all major Microsoft Defender for Identity features have now been made available in Microsoft 365 Defender portal, the portal redirection setting will be automatically enabled for each tenant starting January 31, 2023.
How will this affect your organization:
· Once the redirection setting is enabled, any requests to the standalone Defender for Identity portal (portal.atp.azure.com) will be redirected to Microsoft 365 Defender (securtiy.microsoft.com) along with any direct links to its functionality.
· Organizations can still manually opt-out by switching it back and disable the setting (navigating from the Microsoft 365 Defender homepage (security.microsoft.com) to Settings -> Identities -> General -> Portal redirection)
What you need to do to prepare:
Ensure your security teams are familiar with Defender for Identity’s features and settings as they are represented in Microsoft 365 Defender. If your security teams need help, please direct them to the updated documentation available here.
MC481830 — Announcing Permanent Redirection and Retirement of ‘Office 365 Security and Compliance Center’ – GCCH & DoD
We are announcing the final step in the transition from the legacy ‘Office 365 Security and Compliance Center’ to the new portals, and the retirement of ‘Office 365 Security and Compliance Center’.
Due to the broad reception and adoption from you, our customers, to the new portals, we feel confident to complete the journey and make Microsoft 365 Defender portal, Microsoft Compliance center and the Modern Exchange Admin portal - the homes for Office 365 Security and Compliance management. This is a continuation of our migration to our new portals: the Microsoft 365 Defender portal, Microsoft Purview compliance portal, and modern Exchange admin center, as announced in August 2022 (MC408693).
Until now, all customers were using the new portals, either via direct access or via automatic redirection from the Office 365 Security and Compliance Center. Now, as we move to the final step of permanent redirection and retirement of the Office 365 Security and Compliance Center, we will stop all redirection to the new portals.
If you still go to Office 365 Security and Compliance Center, please update any internal links or bookmarks you have to the old portal.
GCC-High Environment:
· Office 365 Security & Compliance Center old URL: scc.office365.us
· Microsoft 365 Defender new URL: security.microsoft.us
· Microsoft Purview compliance new URL: compliance.microsoft.us
DoD Environment:
· Office 365 Security & Compliance Center old URL: scc.protection.apps.mil
· Microsoft 365 Defender new URL: security.apps.mil
· Microsoft Purview compliance new URL: compliance.apps.mil
Please note that we have already updated all portals, email notifications and APIs. At this point – beyond using internally stored links – you should not be landing in the Office 365 Security and Compliance Center anymore.
How this will affect your organization:
Users accessing the old Office 365 Security and Compliance Center and being redirected to the new portals will need to update their internal links or bookmarks and move to the new portals for all of their workflows. Users accessing the new portals (Microsoft 365 Defender portal, Microsoft Purview compliance portal and the modern Exchange admin center) will not be impacted.
This change impacts all users who log in to the Office 365 Security and Compliance Center, including security teams as well as end-users who access the email quarantine experience at security.microsoft.us/quarantine (GCC-High) or security.apps.mil/quarantine (DoD).
We'll be gradually rolling this out in early December 2022, and the roll out will be completed by the end of January 2022.
What you need to do to prepare:
Please ensure awareness of resources who may be going to the old Office 365 Security and Compliance Center and being redirected to the new portals to update their internal links or bookmarks and move to the new portals for all of their workflows.
MC467232 — (Updated) Changes to Cloud App Catalog and Risk score calculation
Updated December 15, 2022: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Defender for Cloud Apps are making some changes to the Cloud App Catalog as part of improving the scoring of Apps.
1) As part of the changes, the following non-relevant/redundant indicators are being removed from the catalog:
· Consumer Popularity Index
· Safe Harbor
· Jericho Forum Commandments
· Heartbleed patched
· Protected against DROWN
2) The following indicators are being removed from the score calculation; however, they will continue to be presented in the catalog for information and will also continue to be available in Filters.
· Founded
· Holding
· Domain Registration
· FedRAMP level
· FISMA
3) Indicator “Disaster Recovery Plan” is being moved from “General” to “Security” section
4) Indicator “SSAE 16” is being replaced with “SSAE 18”.
When this will happen:
Standard Release: We will begin rolling out mid-January 2023 (previously mid-December 2022) and expect to complete it by late January 2023 (previously late December 2022).
How this will affect your organization:
Due to the above changes, the risk score of some applications might change and new alerts might trigger if customers have created discovery policies based on total score of apps or removed indicators. Also, any existing policies that were created based on the removed indicators will also be removed
What you need to do to prepare:
Therefore, please review your existing discovery policies and modify them or create new policies as needed.
MC362283 — (Updated) Updates to the Zero-hour auto purge (ZAP) alerts
Microsoft 365 Roadmap ID 93206
Updated December 27, 2022: We have updated the rollout timeline below. Thank you for your patience.
We will be updating the current zero-hour auto purge (ZAP) alerts and introduce a new ZAP alert that will notify you if a message has not been removed by ZAP.
Updates to the ZAP alerts will include:
· Scoping the success ZAP alerts for only ZAP related scenarios. You will no longer be alerted as part of the ZAP alert for Dynamic Delivery scenarios.
· A new failure ZAP alert is being introduced. You will receive an alert when a message was not successfully removed from the mailbox. Manual action will be required to remediate the message. The alert will be correlated and linked to both Automated Investigation and Response (AIR) and Incidents. The alert will be on by default and can be configured in alert policies.
When this will happen:
We expect these updates to roll out in early November (previously mid-October) and expect to be complete by mid-January (previously early December).
How this will affect your organization:
Due to these new changes, you can expect a change in the volume of the successful ZAP alerts. The new ZAP failure alert will be on by default and can be configured in the alert policy settings. You can review both default alerts in the portal. However, if you’re exporting these alerts into external systems, you will need to include the new alert generated by the new policy.
What can you do to prepare:
Review the following resources below to learn more:
· Microsoft 365 alert policies
· Zero-hour auto purge in Microsoft Defender for Office 365
Identity
MC485089 — Azure AD Tenant Creation Control
This new capability will provide admins with the ability to lock down tenant creation to decide whether they want their users to create more tenants.
The ability for users to create tenants from the Manage Tenant overview has been present in Azure AD since almost the beginning of the Azure portal. The Tenant Creation Lockdown capability (Restrict non-admin users from creating tenants) will provide admins with the ability to restrict tenant creation to decide whether they want their users to create more tenants. We have also created the Tenant Creator role, which will allow users assigned to this role to create new tenants.
Microsoft 365 Roadmap ID 109541
When this will happen:
Preview: We began rolling out mid-November and expect to complete by mid-December.
How this will affect your organization:
The feature gives tenant administrators the ability to lock down tenant creation by their users and restrict it to only users with Tenant Creator or Global administrator role.
What you need to do to prepare:
Tenant administrators can choose to restrict non-admin users to create more tenants, once the feature is available in their tenant.
Microsoft 365
MC494735 — Group Policy for LookUp and Translate in Visio 2021 LTSC
Note: This change only impacts Visio 2021 LTSC. If your organization is not using this version, you can disregard this message.
Microsoft Visio is announcing the retirement of the Translate and LookUp features for Visio 2021 LTSC.
With this group policy update we will give admins the ability to turn off these features.
The policy was rolled out on October 11, 2022, with the build number 16.0.14332.20387 and above.
You are receiving this message because your organization may be using the LookUp and Translate feature.
Admins will have the capability to turn off these features with the help of a group policy update.
Installation Steps for Admins:
1. The policy should be located at 'User Configuration > Administrative Templates > Microsoft Visio 2016 >Visio Options > Proofing > Turn off Research and Translation features in Visio. If the policy is not found here, you can download the ADMX/ADML file from here
2. Click the Download button and choose whether you want to download the 32-bit (x86) or 64-bit (x64) files, or both. For example, if you’re using the Office Customization Tool (OCT) to customize installations of the 64-bit version of Office, download the 64-bit (x64) files. If you just need the ADMX/AMDL files, you can download either the 32-bit (x86) or 64-bit (x64) files. The ADMX/ADML files are the same for both.
3. Click Next and choose where to save the files.
4. Go to the location where you saved the downloaded files and double-click the admintemplates executable (.exe) file and follow the instructions to extract the files to a location of your choosing.
5. Next, copy the Visio16.admx file to the C:\Windows\PolicyDefinitions folder and the Visio16.adml files to the corresponding locale folder (for example: Visio16.adml from the en-US folder to C:\Windows\PolicyDefinitons\en-US folder).
Steps to Run the Policy for Admins:
1. Using the Windows key + R, run the ‘gpedit.msc’ command.
2. The policy will be located under 'User Configuration > Administrative Templates > Microsoft Visio 2016 >Visio Options > Proofing > Turn off Research and Translation features in Visio.
3. Set the policy to enable/disable.
4. Run 'gpupdate/force' on the command line to force group policy to update.
MC486729 — [UPDATE] New details on IE11 desktop application permanent disablement scheduled for February 14, 2023
The out-of-support Internet Explorer 11 (IE11) desktop application is scheduled to be permanently disabled on certain versions of Windows 10 devices on February 14, 2023, through a Microsoft Edge update, not a Windows update as previously communicated. All remaining devices that have not already been redirected from IE11 to Microsoft Edge are scheduled to be redirected with the Microsoft Edge update scheduled for February 14, 2023. Similar to how Windows updates work, redirection from IE11 to Microsoft Edge will be included in all future Microsoft Edge updates and will impact all devices within your organization at the same time with no ability for users to reverse the change. Therefore, if your organization still has dependencies on IE11, you must take steps now to complete your transition before February 14, 2023, or risk business disruption at scale when users lose access to IE11-dependent applications. As a reminder, IE11 has been out of support since June 15, 2022.
The change to use Microsoft Edge update to disable IE is intended to provide a better user experience and help organizations transition their last remaining IE11 users to Microsoft Edge. Users will see a dialogue box when they are transitioned to Microsoft Edge. When they try to click any IE11 icons or other entry points, they will be redirected to Microsoft Edge. Users’ browsing data will be automatically brought over to Microsoft Edge from IE11 so they can seamlessly continue browsing.
IE11 visual references, such as the IE11 icons on the Start Menu and taskbar, will be removed by the June 2023 Windows security update (“B” release) scheduled for June 13, 2023. They will also be removed by the non-security preview “C” release on certain Windows 10 versions scheduled for May 23, 2023.
When this will happen:
· All in-scope devices are scheduled to be permanently redirected from IE11 to Microsoft Edge on February 14, 2023, through a Microsoft Edge update
· The Windows update that removes visual references to IE11 is scheduled to be available in the following releases:
· May non-security preview (“C”) release scheduled for May 23, 2023
· June security (“B”) release scheduled for June 13, 2023
· Removal of IE11 visual references will be included in all subsequent Windows updates after the May non-security preview release
How this will affect your organization:
· Organizations that have already transitioned from IE11 to Microsoft Edge with IE mode will not be impacted when the IE11 desktop application is scheduled to be permanently disabled on February 14, 2023. Note: If you would like to remove the IE visual references such as on the taskbar or Start Menu, you will need to use the Disable IE policy before February 14, 2023.
· Organizations that have not transitioned from IE11 to Microsoft Edge with IE mode may face business disruption at scale when the out-of-support IE11 desktop application is permanently disabled, currently scheduled for February 14, 2023.
· When a user tries to open IE11 after receiving the Microsoft Edge update, they will see a dialogue box informing them that they are being redirected to Microsoft Edge. Clicking "Continue" will launch Microsoft Edge. This is an example of a message a user might see:
What you need to do to prepare:
Complete your transition from IE11 to Microsoft Edge with IE mode before February 14, 2023. Failing to transition before this date may cause your organization to experience business disruption at scale when IE11 is scheduled to be permanently disabled on February 14, 2023. If you would like to remove all IE11 visuals/entry points, set the Disable IE policy before February 14, 2023.
If you need help transitioning from IE11 to Microsoft Edge with IE mode, please reach out to Microsoft as soon as possible through one of the following pathways:
1. Open a support ticket for help with technical issues
2. Request help from the App Assure team for app compatibility issues
The majority of customers have already moved to Microsoft Edge and are experiencing the performance and productivity benefits of a faster, more secure, and more modern web experience than Internet Explorer (learn more). Microsoft Edge is the only browser with built-in compatibility for legacy IE-based sites and apps with IE mode.
Additional Information
· Read the FAQ to help answer your questions.
We always value feedback from our customers.
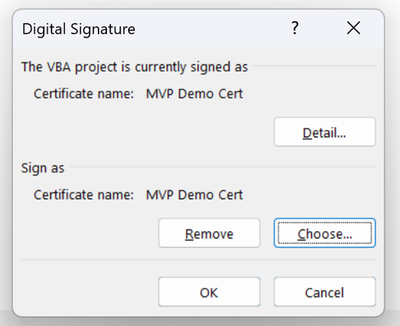
MC482182 — Announcing Ability to Digitally Sign VBA Projects in Microsoft Access Databases
When creating a Microsoft Access database, authors will be able to use a code signing certificate to digitally sign the database. The signature will cover VBA code and other elements of the database such as Access macros and action queries. This will enable databases to execute VBA code and other active elements when the Trust Center Macro Settings are set to only enable digitally signed VBA macros to run.
When this will happen:
Preview: This feature is available in Beta and Current Channel (Preview) now, for Office version 2211 and subsequent versions.
Standard Release: This feature will be available in Current Channel starting with Office Version 2211 in late November and will be available in Semi-Annual channel in July 2023.
How this will affect your organization:
This feature will have no impact on users or tenants, unless your organization chooses to use it. However, if you organization has set Trust Center Macro Settings to enable only digitally signed VBA macros, by using this feature, users will be able to run active content in databases without putting the database into a Trusted Location, if it is signed (either by the author, or by your organization), with a digital signature from a publisher that is trusted by your organization.
What you need to do to prepare:
If your organization does not yet enable the setting to run only digitally signed VBA macros, you can prepare to do so by ensuring that for any databases that you wish to run with active content are signed with a certificate from a trusted publisher.
MC478686 — (Updated) Whiteboard application for Windows and Surface Hub - (GCC-High)
Microsoft 365 Roadmap ID 85624
Updated December 16, 2022: We have updated the content below for clarity. Thank you for your patience.
The Whiteboard application for Windows and Surface Hub is now available for your tenant.
When this will happen:
This functionality is now available.
How this will affect your organization:
In addition to Whiteboard on the web and in Teams desktop, the Whiteboard application for Windows and Surface Hub can now be made available to your users.
Note: Whiteboard will not appear in the app picker at this time and will be added in the future. Please access Whiteboard directly via the direct GCCH Whiteboard URL https://whiteboard.office365.us, or the entry points listed above.
What you need to do to prepare:
We are providing an environment-specific version of Whiteboard for Windows and Surface Hub for your tenant, which means you should not use the version in the Microsoft Store.
How to install and update Whiteboard for your environment:
· Uninstall any prior versions of Whiteboard on the device using an endpoint manager, such as Intune (Apps for GCC High and DoD environments - Microsoft Intune | Microsoft Learn).
· Download the application (.appxbundle) from App Center at https://go.microsoft.com/fwlink/?linkid=2216206.
· Deploy the package through an endpoint manager onto your users’ devices. Ensure that the application is not set to automatic updates, they should be updated only through controlled distribution via your endpoint manager.
When you get an MC post update informing you of a newer version, you will follow the steps to download and deploy the package, but you don’t need to uninstall the version.
In the future, we'll bring an automatic update solution so that the app only needs to be deployed utilizing the above instruction the first time.
The process is the same for Windows and Surface Hub devices.
MC470781 — (Updated) Microsoft 365 admin center: New ways to find advanced deployment guides
Microsoft 365 Roadmap ID 102402
Updated December 16, 2022: We have updated the content below with additional details. Thank you for your patience.
The Advanced deployment guides & assistance page in the Microsoft 365 admin center and the setup.microsoft.com website are both getting new looks and additional features. We’re updating the search tools, recommendations, and layout of both locations so it’ll be easier to find guides for the product you’re deploying. Included in the new layout are views that highlight guides for Secure Score, Compliance Score, and Adoption Score improvement. You’ll also see new guides on setup.microsoft.com that are currently available only within the Microsoft 365 admin center.
When this will happen:
Updates to the search tools, recommendations, and layout for both locations will be available in mid-December. Secure Score, Compliance Score, and Adoption score views on the Advanced deployment guides & assistance page will also be available mid-December, with a visual representation of each score coming at a later date.
How this will affect your organization:
Advanced deployment guides give admins tailored guidance and resources for planning and deploying tenant settings, apps, and services in step-by-step instructions. They include automated configuration tools, scripts, and best practices from Microsoft FastTrack deployment specialists.
In the Microsoft 365 admin center, the Advanced deployment guides & assistance page hosts more than 40 guides that cover Microsoft products, such as Microsoft Teams, Microsoft Purview, Microsoft Defender, Microsoft Viva, and Exchange. We’ll remove the All guides and Overview sections and replace them with a combined view that has improved search and filtering features. There will be new pages to highlight guides that help with improving your security, compliance, and adoption scores.
The Secure Score view on the Advanced deployment guides & assistance page.
Other key features include:
· Share your deployment journey with key stakeholders by exporting your progress to an Excel workbook.
· See the most important actions front and center in the Suggested guides section. In future updates, these suggestions will be tailored to your configuration and licenses.
· Tags to notify you when a new or updated guide has been released since your last visit to the page.
The Suggested guides view on the Advanced deployment guides & assistance page.
Setup.microsoft.com is the home for Advanced deployment guides outside the Microsoft 365 admin center. You can’t use guides on this site to directly configure your tenant, but they still offer step-by-step deployment tips for users who can’t directly sign in to the Microsoft 365 admin center, or who only have permissions to access other admin centers. This site also hosts guides to help you discover and try Microsoft 365 services before making a purchase.
Key updates to this site include:
· New child pages for each product so you can find more details about the product along with the related deployment guide.
· Find guides for specific products or for deployment scenarios with our updated search functionality.
· Guides currently only available in the Microsoft 365 admin center will be added to this site by January.
The updated design of the setup.microsoft.com site with new areas to find guides by product or scenario.
What you need to do to prepare:
If you’ve bookmarked sections of the Advanced deployment guides & assistance page, those links will redirect to the new Deployment guides section. You might need to make IT staff in your org aware of the new navigation. You don’t need to do anything to prepare for the changes on setup.microsoft.com.
MC467624 — (Updated) Text Formatting Support for Microsoft Whiteboard
Microsoft 365 Roadmap ID 100497
Updated December 15, 2022: We have updated the rollout timeline below. Thank you for your patience.
The ability to format all or a portion of text in text boxes, notes and shapes is coming soon to Whiteboard web, Teams and the Windows app (mobile users will be able to view formatted text but not format it).
When this will happen:
Roll out will begin in mid-November and is expected to be completed by early January 2023 (previously late November 2022).
How this will affect your organization:
Users will be able to apply Bold, Italics and/or Underline formatting to all or a portion of text in text boxes, notes & shapes. They can also choose to format the color of text in text boxes. Moreover, each new text box that will be added will have Segoe UI font for higher legibility & also coherence with text in notes & shapes.
Note: The font of existing text boxes will not be changed.
What you need to do to prepare:
The feature will be rolled out automatically on Whiteboard web, Teams and the Windows app to all customers.
To learn more, visit the Microsoft Whiteboard Help Hub page.
MC343441 — (Updated) Announcing Public Preview of Idle Session Timeout for Microsoft 365 Web Apps
Microsoft 365 Roadmap ID 55183
Updated December 13, 2022: We have updated the rollout timeline below. Thank you for your patience.
Today's release of Idle session timeout will allow IT admins to configure a tenant-wide timeout policy to automatically sign out users after a period of inactivity on Microsoft 365 web apps. This will help protect sensitive company data from unauthorized access while providing peace of mind for end users while working on unmanaged and/or shared devices. This feature is an improvement over, and will eventually replace, current app-specific idle timeout settings in Outlook Web App (OWA) and SharePoint Online (SPO).
When this will happen:
Preview: Began rolling out today and is expected to be complete in late March. - Complete
Standard: We will begin rolling this out in late June and expect to complete rollout late August.
GCC/GCC-High/DoD: We will roll out in the first half or 2023 and will update the post with additional details.
How this will affect your organization:
With this update, admins will have the ability to control how long a user can remain inactive on a Microsoft 365 web app before they get signed out automatically. By default, Idle session timeout feature is turned off for an organization. You can opt in via UX in Microsoft 365 Admin Center using the steps described here.
Once this feature is turned on for your organization, users who access Microsoft 365 web apps from an unmanaged device and do not select 'Stay signed in?' option at the time of sign-in might start seeing more sign-in prompts. Other users will not get impacted by this change.
Idle Session Timeout Setting
Idle Session Timeout Prompt
What you need to do to prepare:
As you try out the Idle session timeout feature, you might want to notify your users about this change and update your training and documentation as appropriate.
Note: If you have already configured idle timeout policies for OWA and SPO, then turning on the new Idle session timeout feature will override existing OWA/SPO timeout behavior.
· Please note that we are not yet retiring the existing functionalities in OWA and SPO. But in order to better prepare your organization for this change, we recommend you trying out the new feature now and migrate to it once it becomes generally available.
Learn more:
· Manage idle session timeout web apps
We always value feedback and questions from our customers. Please feel free to submit either feedback or questions here.
MC295027 — (Updated) Rich text and images in Planner task notes
Microsoft 365 Roadmap ID 85688.
Updated December 27, 2022: We have updated the rollout timeline below. Thank you for your patience.
We are adding support for rich text (bold, italics, underline, etc.) in the Planner task notes field. Support for images is coming in the future.
NOTE: We will update this post once we have Microsoft Graph documentation for the new rich text task notes field available.
When this will happen:
We expect to begin rolling out the new rich text task notes field in mid-January (previously early December) and we expect to complete the rollout by late January (previously mid-December).
How this will affect your organization:
To support this capability, we are introducing a new rich text enabled task notes field in the Planner Microsoft Graph API. This will result in two task notes fields in our API – the new “rich text task notes field” and the existing “plain text task notes field.” When this feature launches, Planner for the Web and for Teams (Tasks app) will support rich text in task notes. Other Planner experiences in iOS, Android, SharePoint, and Power Automate will only support plain text task notes, but we plan to update these apps to support rich text at a later date.
When this feature update is deployed, all existing task notes content will be preserved in the new rich text enabled task notes field, so users will be able to continue viewing and editing notes without interruption.
We will maintain compatibility between the rich text task notes field and plain text task notes field by ensuring both fields’ contents stay in sync.
If a user edits the rich text task notes field, all content is synced to the plain text task notes field automatically. Any rich content is converted to plain text and synced to the plain text task notes field.
If a user edits the plain text task notes field via the Microsoft Graph API or via a client which only supports the plain text field, the contents in the plain text task notes field is synced to the rich text task notes field without modification. Therefore edits to the plain text task notes field will result in the removal of any pre-existing rich text, or text formatting in the rich text notes field.
What you need to do to prepare:
If your organization has custom applications interacting with our Microsoft Graph Planner API, make sure to update the apps to support the rich text task notes field as soon as it is available to take advantage of the new notes capabilities. We will maintain support for the existing plain text task notes field in our Microsoft Graph Planner API for at least 36 months.
If your organization has applications or workflows which parse the task notes to trigger logic based off contents in the notes field, we recommend users continue to input only plain text in task notes and not apply text formatting into task notes. Such apps should also be updated to avoid parsing task notes or applying logic to contents in the task notes as these are not recommended uses of the task notes field in our API.
Microsoft 365 IP and URL Endpoint Updates |
Documentation - Office 365 IP Address and URL web service
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.