- Home
- Public Sector
- Public Sector Blog
- November 2023 - Microsoft 365 US Public Sector Roadmap Newsletter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Newsworthy Highlights |
Elevating Government Productivity: Microsoft 365 Copilot at the Forefront
The digital transformation within government sectors is accelerating, and Artificial Intelligence (AI) is playing a pivotal role in this evolution. Microsoft is leading the charge, deploying innovative AI solutions tailored for public sector needs. At the heart of this transformation is Microsoft 365 Copilot, a groundbreaking tool set to redefine how government agencies work.
Microsoft 365 Government Community Call
Join Jay Leask and other members of the Government Community live on LinkedIn!
Where to Start with Microsoft Teams Apps in Gov Clouds
Customers in our Office 365 government clouds, GCC, GCCH, and DoD, are continuing to evolve how they do business in the hybrid workplace. As Microsoft Teams is the primary tool for communication and collaboration, customers are looking to improve productivity by integrating their business processes directly into Microsoft Teams via third-party party (3P) applications or line-of-business (LOB)/homegrown application integrations.
Microsoft 365 Government Adoption Resources
Empowering US public sector organizations to transition to Microsoft 365
What’s New in Microsoft Teams | October 2023
These features currently available to Microsoft’s commercial customers in multi-tenant cloud environments are now rolling out to customers in the US Government Community Cloud (GCC), US Government Community Cloud High (GCC-High), and/or the United States Department of Defense (DoD).
Release News |
SharePoint Online
Microsoft is announcing its plan to retire Business Connectivity Services (BCS) in Microsoft 365 and...
Teams
Shared Calling - GCC
End-to-end encryption for scheduled meetings - GCC October, GCCH & DoD November
New Teams chat experience in Microsoft Edge when opening web links
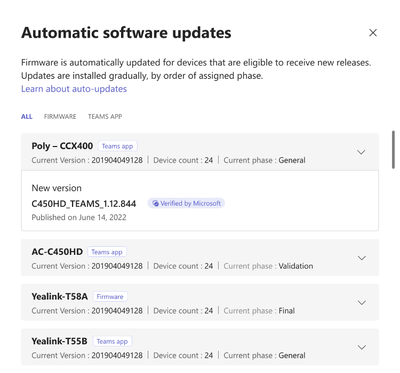
Automatic updates for the Teams app on Android-based Teams devices – GCC November 30 2023, GCCH & Do...
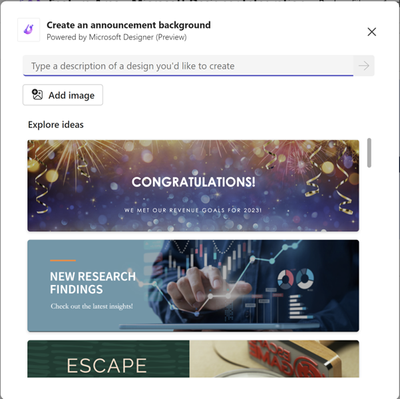
Custom announcement backgrounds in Channels with Designer - GCC & GCCH November, DoD December
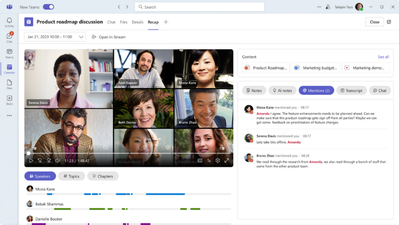
Meeting Recap tab helps users catch-up on past meetings. Teams Premium users will have access to AI-...
Bring-Your-Own-Device admin experience in Teams Pro Management Portal - GCC
Exchange Online
Outlook on the web: Replacing “Activity-Based Authentication Timeout” with “Idle Session Timeout for...
Purview
Ability to change retention period on labels set to start retention based on “When items were labele...
Data Loss Prevention - Matched items in audit logs
eDiscovery (Premium) – Data sources usability enhancements
Keyword highlight support for document trainable classifiers
DLP – Apply Protection at Time of Egress on Endpoints
Identity
Rollback of changes to the registration campaign feature in Microsoft Entra (previously Azure Active...
Microsoft 365
Retirement of the Translation feature in OneNote for Windows 10
Support for Office 2019 for Mac ended October 10, 2023
Office 2019 for Windows enters Extended Support on October 10, 2023
Office 2016 and 2019 Client Connectivity to Microsoft 365 Services support ended on October 10, 2023
References and Information Resources |
Microsoft 365 Public Roadmap
This link is filtered to show GCC, GCC High and DOD specific items. For more general information uncheck these boxes under “Cloud Instance”.
Stay on top of Microsoft 365 changes
Here are a few ways that you can stay on top of the Office 365 updates in your organization.
Microsoft Tech Community for Public Sector
Your community for discussion surrounding the public sector, local and state governments.
Microsoft 365 for US Government Service Descriptions
· Office 365 Platform (GCC, GCCH, DoD)
· Office 365 U.S. Government GCC High endpoints
· Office 365 U.S. Government DoD endpoints
· Microsoft Purview (GCC, GCCH, DoD)
· Enterprise Mobility & Security (GCC, GCCH, DoD)
· Microsoft Defender for Endpoint (GCC, GCCH, DoD)
· Microsoft Defender for Cloud Apps Security (GCC, GCCH, DoD)
· Microsoft Defender for Identity Security (GCC, GCCH, DoD)
· Azure Information Protection Premium
· Exchange Online (GCC, GCCH, DoD)
· Office 365 Government (GCC, GCCH, DoD)
· Power Automate US Government (GCC, GCCH, DoD)
· Outlook Mobile (GCC, GCCH, DoD)
Be a Learn-it-All |
|
Public Sector Center of Expertise We bring together thought leadership and research relating to digital transformation and innovation in the public sector. We highlight the stories of public servants around the globe, while fostering a community of decision makers. Join us as we discover and share the learnings and achievements of public sector communities. |

|
|
Microsoft Teams for US Government Adoption Guide
|

|
|

|
|
Message Center Highlights |
SharePoint Online / OneDrive for Business
MC686278 — SharePoint: Out-of-the-box document library templates
<30 Days
Microsoft 365 Roadmap ID 124879
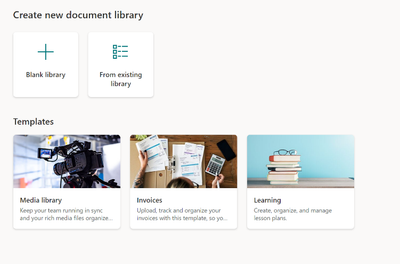
We are bringing the goodness of templates to SharePoint document libraries. Creating document libraries will now be a breeze with our ready-made templates with scenario relevant structure, metadata, and content types - all to save you time and maintain broader consistency across your content management organization.
When this will happen:
- Targeted Release: early November 2023
- Standard Release: mid-November 2023
How this will affect your organization:
We are rolling out a brand-new Document library creation experience that will be available in two locations:
- SharePoint Home > New > Document library
- SharePoint Site > Site contents > New > Document library
With the new experience you will be able to create Document libraries in different ways:
- Blank library: this experience will replicate the current library creation experience where a document library will be created with the basic columns of Name, Modified and Modified by.
- From existing library: this experience will allow you to choose any document library from a site you have access to, and replicate the structure, formatting, metadata and content types in a new document library. [please note that data will not copy over, only the structure will]
- From templates: we have three brand new templates for you: Media library, Invoices and Learning. Each template will come with a pre-defined schema, formatting, views etc. to kickstart your content management journey!
- Flows packaged into the out-of-the-box-templates: the Media Library and Invoices templates also come with pre-packages Flows that can be skipped or completed depending on the user's needs.
What you need to do to prepare:
Consider educating users that there are now more ways to create a Document Library.
MC684224 — Add Individual File Shortcuts in OneDrive Web
<30 Days
Microsoft 365 Roadmap ID 177873
You can create a shortcut to files stored in other people's OneDrives and document libraries to be able to easily find it within your OneDrive. These file shortcuts can be moved and renamed without impacting the source content and will show up in OneDrive Android, iOS & sync client endpoints.
When this will happen:
We will begin rolling out in early November and expect to complete by later November.
How this will affect your organization:
Users will see an Add Shortcut command in the command bar and context menu for a file. This command will be available across all OneDrive file lists (Home, My files, Shared, Favorites, etc.) as well as document libraries. It will also be available for document libraries browsed within SharePoint and Teams.
When a user selects a file and clicks Add Shortcut, they will see two options for where to add a shortcut to: My files and Other locations.
If the user selects My files, a .url file will be created within their My files list in OneDrive. If they select Other locations, a file picker will launch for users to choose a location for their file shortcut within their OneDrive as well as document libraries they have access to.
The default name of the shortcut will be the name of the source file appended with .url. For example, if you create a shortcut to IndividualFileShortcuts.docx, the name of the shortcut will be IndividualFileShortcuts.docx.url and will be differentiated with an arrow icon overlay.
The file shortcut is simply a pointer to a file. When a user renames, moves, deletes or shares a file shortcut, this only impacts the shortcut file and has no impact on the source file. A key implication of this behavior is that, if a user shares a shortcut file or moves a shortcut file to a shared location, it does not automatically grant access to the source file and users would need to share the source file directly to allow access. If the source file is renamed after the file shortcut was created, the file shortcut will not reflect the new source file name.
File shortcuts support the same commands as other .url files in OneDrive and SharePoint that were created through New > Link.
File shortcuts can only be added through OneDrive Web, SharePoint Web and Teams. File shortcuts can be accessed across OneDrive Web, SharePoint Web, OneDrive iOS & Android, OneDrive Sync Client and Teams. There is no meaningful distinction in file shortcut access behavior across endpoint.
What you need to do to prepare:
You may want to notify your users, update your user training, and prepare your help desk.
For your users: Add shortcuts to shared folders in OneDrive for work or school
- Users cannot create a file shortcut to non-file content within their OneDrive (e.g., Lists, Whiteboard, PowerBI dashboards, etc.). However, users can create a file shortcut to Loop components within OneDrive.
- Users cannot Favorite a file shortcut. Our expectation is that customers will Favorite the source file instead of a shortcut that points to the source file.
- When a user shares a file shortcut or moves it to a shared location, it does not share the source file.
- Users cannot preview file shortcuts since the shortcut file itself has no information to preview.
MC684222 — Video inline playback on Highlighted content web part
<30 Days
Microsoft 365 Roadmap ID 98091
This feature allows users to play the videos inline from Highlighted content web part. This functionality is enabled for web parts configured with Carousel or Filmstrip layouts and for 1-col and 2-col sections only.
When this will happen:
Standard Release: We will begin rolling out early November 2023 and expect to complete by mid-November 2023.
How this will affect your organization:
Videos configured in the above-mentioned layouts and sections for Highlighted content web part allows you to watch the videos inline within SharePoint itself. With in-context playback, you will be able to browse and scroll through other content on the Page while watching the video.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC683665 — Social ratings APIs are being retired.
>60 Days
This message is intended to notify all customers utilizing social ratings APIs that Microsoft will start retiring a number of these APIs starting January 2024. If your organization is not using the social ratings APIs, you can safely disregard this message.
For a comprehensive list of the APIs scheduled for retirement, please refer to the information provided below.
Microsoft has decided to retire the following APIs:
- CountRatingsOnUrl (string URL)
- GetRatingsOfUser (string userAccountName)
- GetRatingsOnUrl (string URL)
- GetRatingOnUrl (string URL)
- GetRatingOfUserOnUrl (string userAccountName, string URL)
- DeleteRating (string URL)
All of these APIs pertain to the social rating functionality ([MS-UPSDWS]: Glossary | Microsoft Learn).
The rationale behind this choice is that these APIs are superfluous and consistently yield empty results when called, leading to an inefficient utilization of customers' computing resources if they continue to make requests to them. Please be aware that in the event these APIs are invoked after they are retired, an exception with the message 'This API is deprecated; you should stop invoking the API and remove references.' will be returned.
When this will happen:
January 1, 2024.
How this will affect your organization:
Our telemetry data indicates that these APIs have almost no usage and should not have any impact on our customers. Nevertheless, we kindly request our customers to exercise due diligence and verify that they eliminate any reliance on the aforementioned APIs. As previously mentioned, these APIs do not provide any data and are therefore entirely superfluous.
What you can do to prepare:
If your organization has taken any dependency on the above-mentioned APIs, we ask you to please remove this dependency. Below, we have provided alternative existing social ratings APIs that can serve as replacements if required:
- SetRating (string URL, int rating, string title, FeedbackData analysisDataEntry)
- PropagateRating (string URL)
- GetRatingAverageOnUrl (string URL)
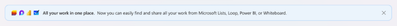
MC683663 — Access Microsoft Lists, PowerBI, Loop and Whiteboard Content in OneDrive Web
<30 Days
Microsoft 365 Roadmap ID 177877
You will be able to easily find your Microsoft Lists, Loops, Power BI dashboards and Whiteboard content within OneDrive Web. This content will be available in the Recent, Shared with You and Favorites list within OneDrive.
When this will happen:
Rollout will begin in early November 2023 and expect to be complete by late November 2023.
How this will affect your organization:
Users will see Microsoft Lists, PowerBI, Loop and Whiteboard content appear within their Recent, Shared with You, and Favorites list within OneDrive Web. When opened, this content will open in a new tab. This content will support a limited set of commands compared to other content types.
There is no additional preparation needed for this content to show up. As users open this content in the related apps, it will automatically appear in their Recent list. If this content is shared with them, it will appear in their Shared with You list. Users can Favorite this content from Recent and Shared with You with the same experience as other content types.
Users will see a banner in their OneDrive experience to announce the availability of these content types. This banner will only appear for customers who have these content types present in their Recent or Shared with You list. It will not appear for customers who have no usage of Lists, Loops, Power BI dashboards or Whiteboard.
What you need to do to prepare:
You may want to notify users, update your user training, and prepare your help desk.
MC679737 — Business Connectivity Services (BCS) retirement
>60 Days
SharePoint has a long history of helping users work with external data inside the SharePoint user experience. As SharePoint has evolved into a cloud-first service, so too have the options for customers that wish to integrate with external data sources. To simplify these options and provide the best experience for these scenarios going forward, Microsoft is announcing its plan to retire Business Connectivity Services (BCS) in Microsoft 365 and focus on Microsoft Power Apps as its replacement technology.
Key points:
- Major: Retirement
- Timeline:
- October 2, 2023: Retirement announcement and customers can proactively set a property to block Business Connectivity services features within their tenant.
- October 30, 2023: Microsoft will begin blocking Business Connectivity Services features based on the tenant property set by the customer.
- January 8, 2024: Microsoft will block Business Connectivity Services features in new Microsoft 365 tenants by default, as well as in tenants who haven’t used the feature since October 30, 2023.
- September 30, 2024: Business Connectivity Services is fully retired in Microsoft 365.
- Action: Review and assess impact.
How this will affect your organization:
If your organization uses Business Connectivity Services, it will no longer function after September 30, 2024. This includes features such as:
- External lists
- External columns
- External content types
- Business Connectivity Services hybrid solutions
What you need to do to prepare:
Microsoft encourages customers to explore using Power Apps to replace their Business Connectivity Services solutions. Although there's no direct migration from Business Connectivity Services to Power Apps, it supports a modern, cloud-first external data connectivity experience. Power Apps can integrate with a variety of Microsoft 365 services and external data sources through its extensible connector technology, including SharePoint, Dynamics 365, SQL Server, and others. It also supports integrating with on-premises data sources through the on-premises data gateway.
Learn more:
- Support update for Business Connectivity Services in Microsoft 365
- Support article with additional resources
MC666623 — (Updated) New Stream (on SharePoint) web part release
<30 Days
Microsoft 365 Roadmap ID 124800
Updated October 26, 2023: We have updated the rollout timeline below. Thank you for your patience.
This is an important message for customers who publish videos to SharePoint Pages and news posts. As noted in Message Center post MC561187, the Stream (Classic) webpart in SharePoint will be retired on August 15, 2023.
The Stream (on SharePoint) web part will support configuration of a single video and multiple videos for videos stored in OneDrive or SharePoint.
When this will happen:
The Stream (on SharePoint) webpart will begin its general availability roll out in mid-August 2023, and we expect the rollout to complete by late November 2023 (previously mid-October 2023).
How this will affect your organization:
Your organization will not be able to use Stream (Classic) webpart after August 15, 2023.
All existing SharePoint pages and news posts that were built using Stream (Classic) webpart will continue to function as usual. Please follow this documentation for detailed information for videos post migration: https://learn.microsoft.com/en-us/stream/streamnew/migration-details
Before availability of the new Stream (on SharePoint) web part, you can currently use video eligible webparts such as “File and Media”, “Hero”, “Highlighted content” and “List” webparts to publish videos/playlists from Stream (on SharePoint) to SharePoint Pages.
Post availability of this web part, we would recommend you use it for publishing single video and multiple videos from a folder and continue using “List” web part for publishing a playlist to SharePoint Pages.
What you need to do to prepare:
Please follow this documentation for detailed timelines and video publishing guidance on the new Stream.
MC600726 — (Updated) Microsoft Lists User Experience Update
TBD
Microsoft 365 Roadmap ID 124867
Update October 20, 2023: Thank you so much for the feedback on this feature rollout. We have listened to your feedback and are making changes to the feature as follows:
- Lists with the new experience will continue to open inside the Lists app when they are opened from Lists Home, a sharing link or a direct link.
- Any list navigation in a SharePoint context will now fall back to the old experience and will not get the feature updates as described in this blog post. We are working on a future rollout that will bring support to these Lists, in-line with the feedback we’ve gotten from customers so far.
- Rollout schedule has been updated below to reflect the above changes. Thank you for your patience.
This update improves the overall performance of Microsoft Lists and introduces new features, including the ability to add ratings to any list, drag and/or paste images directly into a list, see who is collaborating with you in real-time, switch views by clicking tabs, view date/time values in your preferred date settings and timezone, and more.
When this will happen:
Targeted Release: Roll-out complete for Lists opened from Lists Home, a sharing link or a direct link. Rollout stopped for Lists opened in SharePoint sites.
Standard Release: Roll-out complete for Lists opened from Lists Home, a sharing link or a direct link. Roll-out stopped for Lists opened in SharePoint sites.
Note: Some users may see this feature before others in your organization.
How this will affect your organization:
Users in affected tenants will see Lists feature updates as described in this blog post. These improvements will reach all Lists, except those that have been configured with the following features:
- SharePoint Framework extensions
- PowerApps forms
- Approvals
- The Playlist template
Lists that are using these features will not receive the new user experience with this feature rollout. Future rollouts will bring support for Lists that are using these features.
What you need to do to prepare:
You don’t need to do anything to prepare for this change.
Microsoft Planner
MC669735 — (Updated) Rosters in Microsoft Planner Supporting Container Sensitivity Labels
>60 Days
Microsoft 365 Roadmap ID 155837
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Customers will soon be able to apply container labels to rosters in Microsoft Planner. This is enabled directly in Planner by using Microsoft Graph APIs. When this feature is rolled out, the roster sensitivity labels can be set to respect the policy settings. If the tenant admin has made container labels mandatory and has set a default label, then the default label will be used for roster creation through Microsoft Loop client.
- On the Loop client, if the default label is provided, it will be used as the roster's lable when creating the roster. The roster system will not allow the user to create an unlabeled roster or to un-label a previously labeled roster.
- On the Microsoft Graph API, if a request is made and the label is not included, the request is rejected as the default label is not applied by the service. Users will need to ensure that a default label is provided when labels are mandatory so that roster creation does not fail.
Note: The container sensitivity label applied to a roster applies only to the information in Microsoft Planner and does not protect or encrypt the information when it syncs with the Loop client.
When this will happen:
We will begin rolling out in early January 2024 (previously late October) and is expected to complete by early February 2024 (previously late November).
How this will affect your organization:
Rosters can be configured with container labels being mandatory. When container labels are set to mandatory for rosters, ensure a default label is available otherwise rosters cannot be created unless a label is set. On the Microsoft Graph API, if a request is made and the label is not included, the request is rejected. (Note: default label is not applied by our service).
What you need to do to prepare:
By setting a container label to mandatory for an existing roster, there may be an impact to third parties used in your organization. For third parties using the labels Graph API, attempts to create a label-less roster will fail if labels are mandatory as the default label will not be applied by our service. To ensure roster creation does not fail when labels are mandatory, it is the client responsibility (third party responsibility) to apply the default label by either updating the apps (if under admin control) or modifying the dependency on such apps or by making labels not mandatory.
MC664477 — (Updated) See your Recent Microsoft Planner plans and Microsoft To Do Lists on Microsoft 365 Homepage
<30 Days
Microsoft 365 Roadmap ID 149272
Updated October 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
Currently, you cannot see your recently accessed Planner plans or Microsoft To Do lists in your Microsoft 365 homepage. With this update, you will be able to see and access all your recent plans and lists alongside your Microsoft Project for the web projects, Word documents, PowerPoint decks, and more on office.com.
When this will happen:
- This update will begin rolling out in early November 2023 (previously early October) and is expected to be completed by late November 2023 (previously mid-November).
How this will affect your organization:
With this update, your organization’s plans and lists will be visible from the office.com home page as opposed to solely from Planner and Microsoft To Do apps. This means you will be able to open your plans and lists directly from the Microsoft 365 homepage, just as you are able to open your Project projects, Word documents, Excel sheets, and all other Microsoft Office files.
What you need to do to prepare:
There is no action required to prepare for this change. Plans and lists for users in your tenant will begin to appear on the Microsoft 365 homepage as soon as the rollout reaches your tenant.
Microsoft Viva
MC682304 — New adoption health metrics dashboard available for Viva Topics
<30 Days
Microsoft 365 Roadmap ID 100028
Track the status of your adoption of Viva Topics with our new adoption health metrics dashboard!
When this will happen:
This feature is currently in Preview. We will begin rolling out to all Viva Topics tenants in late October and expect to complete by mid-November.
How this will affect your organization:
5 metrics will be available for knowledge managers to view in the Topic Center, under an 'Analytics' tab. These 5 metrics provide insight into how the AI is performing in your tenant with discovering topics, how topics are being surfaced in your end points, and how users are interacting with topics.
But not just that-- there are also actions for tenants to take that will improve your adoption. These recommended actions take the guess work out-- you will know exactly how to achieve a healthy knowledge base that is empowering learning across your user base. These are best practices that have been implemented by our most successful Viva Topics adopters that have now fully deployed and are recognizing immense value from Topics.
Please note-- there is a lack of data prior to August, so the monthly views will not be able to show anything prior to then. There were also intermittent data issues in August, which is why you may see a lack of data in that month. Those issues have since been resolved.
What you need to do to prepare:
There is nothing for your tenant to do to prepare. No admin controls are paired with this feature. Simply navigate to the 'Analytics' tab of the Topic Center and start driving your adoption like never before. End users will not have access to this dashboard. If admins want access, ensure they have been given knowledge manager permissions in the Viva Topics setup.
MC682303 — People Search Card in Viva Connections
<30 Days
Microsoft 365 Roadmap ID 173078
Viva Connections have a new card where admins now have the option to incorporate a new people search card for their organization. This card enables colleagues to effortlessly search for and communicate with one another within the organization using Teams chat and email.
When this will happen:
Standard Release: We will begin rolling out in late October and expect to complete by early November 2023.
How this will affect your organization:
This feature will not affect any existing functionality. It's an additional card which organizations can choose to use.
What you need to do to prepare:
No configuration needed. Just add the card and your organization should be able to use it in Viva Connections across all devices.
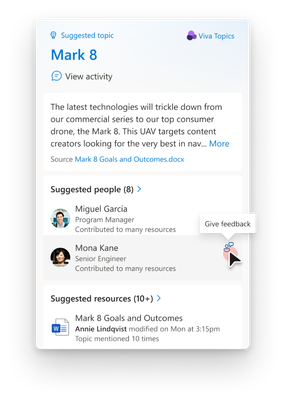
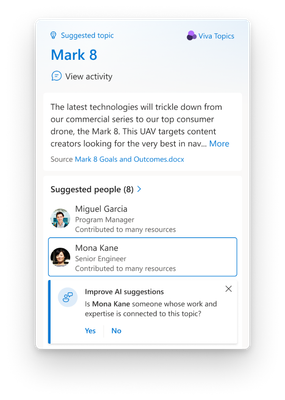
MC680657 — Microsoft Viva: Inline on Demand Feedback on Topic Cards Available
Rolled Out
Microsoft Viva users can soon provide feedback on AI suggested people and resources on a topic card by simply clicking the "Give Feedback" button to confirm or remove them.
When this will happen:
We will begin rollout in mid-October 2023 and expect rollout to be complete by late October 2023.
How this will affect your organization:
This is currently available on the hover topic cards only.
What you need to do to prepare:
There is nothing you need to do to prepare. You may want to notify users of this update.
MC666967 — (Updated) Microsoft Viva: Default Connections Experience on Desktop
>60 Days
Updated October 20, 2023: We have updated the rollout timeline below. Thank you for your patience.
A new default experience on desktop is being released for Viva Connections that’s easier and faster to set up and optimizes content to deliver a modern employee experience. The new experience focuses on essential job tasks, personalized content, easy access to other Viva experiences, and better alignment with the mobile experience. It uses existing assets from your organization’s home site and Viva Connection’s Dashboard, Feed, and Resources. If your organization already has Viva Connections set up, you’ll have the option to choose to keep the existing desktop experiences that features the home site or to use the new home experience. Learn more about the new Viva Connections home experience.
Microsoft 365 Roadmap ID 152560
When this will happen:
- GCC environment, rollout will begin in late September 2023 (previously early September) and is expected to be complete by late October 2023.
- GCC High environment, rollout will begin by March 2024 (previously late October 2023) and is expected to be complete by late March 2024 (previously late December 2023)
How this will affect your organization:
The default Connections desktop experience will automatically update in Microsoft Teams for customers who are currently using Viva Connections. When this feature is released, customers with existing home sites can choose to keep the existing desktop experience. With the new default desktop experience, admins and editors will be able to edit content and manage permissions from Microsoft Teams.
What you need to do to prepare:
To prepare for this change, help admins and editors for Viva Connections learn more about how to customize the default experience and how permissions work.
End users in your organization will use the same entry point in Teams as the previous desktop experience. When they view the new experience for the first time, visual prompts will walk them through the main functions of the design and how to interact with different elements. Share guidance with end users.
Microsoft Teams
MC687207 — Microsoft Teams: Files App Updating to OneDrive App Experience in Teams
30-60 Days
Microsoft 365 Roadmap ID 145798
The Files app accessed from the left side of the Teams desktop client will be updated with the new OneDrive app experience, bringing performance improvements, more views, and the latest features of OneDrive to both classic and new Teams. All existing features of the Files app will also be available via this new OneDrive app experience. For more details, please visit the blog page.
As part of this change, Files app on left side of the new Teams desktop client will also become OneDrive app. There is no change in the name of Files app in either classic Teams desktop client or Teams mobile client.
When this will happen:
Targeted Release: We will begin rolling out in mid-November 2023 and expect to complete rollout by late November 2023.
Standard Release: We will begin rolling out in late November 2023 and expect to complete rollout by mid-December 2023.
How this will affect your organization:
Additionally, for Teams desktop users, a one-time indication will be shown for awareness when Files app is updated to OneDrive app.
What you need to do to prepare:
There is no action required since any existing policies or settings done through Teams Admin Center for Files app will automatically be applicable.
MC687206 — Microsoft Teams: Private Line
>60 Days
Microsoft 365 Roadmap ID 181616
We are introducing a new calling feature. With private line, users will be able to have a private second phone number that they can make available to a select set of callers to call them directly, bypassing delegates, admins, or assistants. Inbound calls to the private line will be distinguished by a unique notification and ringtone. The private line will support incoming calls only.
When this will happen:
Standard Release and GCC: We will begin rolling out early December and expect to complete by mid-December.
GCCH and DoD: We will begin rolling out in early January and expect to complete by early February.
How this will affect your organization:
You will have the ability to designate a phone number as a private line for users to take private line calls.
What you need to do to prepare:
Nothing you need to do to prepare. Once the feature has rolled out, you will be able to set up private line for users.
MC686919 — Simplified Compose Experience for Teams
>60 Days
Microsoft 365 Roadmap ID 123486
Teams Compose is the heart of collaboration, where all Teams messages flow each month. It's also the gateway to a wealth of features, from Co-Pilot to Files, Loops, Video, and Platform Apps.
While Teams' capabilities have grown by leaps and bounds, the compose experience has remained largely unchanged. This update addresses usability, scalability, and information density challenges. We've simplified the compose experience, enhancing usability for various rich authoring scenarios, establishing scalable patterns for all compose actions, and optimizing it for your everyday needs. Get ready to enjoy a more seamless and efficient collaboration experience!
When this will happen:
Targeted Release: We will begin rolling out early-December 2023 and expect to complete by mid-December 2023.
Standard Release: We will begin rolling out late Jan 2024 and expect to complete by early-February 2024.
GCC: We will begin rolling out mid-Feb 2024 and expect to complete by late February 2024.
GCCH: We will begin rolling out early March 2024 and expect to complete by mid-March 2024.
DoD: We will begin rolling out mid-March 2023 and expect to complete by late March 2024.
How this will affect your organization:
All Teams users will still be able to do everything they have previously done in Teams, but now, accessing these features will be easier and clearer.
What you need to do to prepare:
No changes are required to prepare for this change.
MC686915 — Microsoft Teams Admin Center: Permissions tab is available in GCCH and DOD tenants.
30-60 Days
App details page in the Teams admin center will now display permissions and information accessed by Teams apps and provide links for the admin to review the permissions and consent.
When this will happen:
We will begin rolling out late November 2023 and expect to complete by late December 2023.
How this will affect your organization:
App details page will display Permissions tab that contains details of permissions and information accessed by Teams applications, where applicable.
What you need to do to prepare:
No action needed to prepare for this change.
MC686911 — Preview the new Teams web client on Edge and Chrome
TBD
Today we’re starting to roll out the preview of the new Teams web client to Edge and Chrome browsers. Our new Teams web client is built on the same foundation as our new Teams desktop clients and brings Edge and Chrome web users new speed, performance, and flexibility when using Teams.
When this will happen:
We have begun rolling this out now.
How this affects your organization:
How will this benefit my organization:
Our goal for the new Teams web app is to bring a near-identical experience to our new Teams desktop app. Both the new Teams web client and desktop clients share the same underlying infrastructure built to improve load times, improve channel and chat switches, and reduce memory usage.
Web users will see the same Try the new Teams toggle as desktop users, except the web experience requires no additional download or installation.
Note: Not all customer segments (Education, Special Cloud, GCC, GCC-High and DoD) will receive this update at this time.
While the new Teams on web preview includes nearly all the same functionality as classic Teams on web, tenant switching is temporarily unavailable. This feature will become available shortly.
Visit this page to learn more about what’s currently available and what’s coming up.
What you need to do to prepare:
How will I preview the new Teams experience:
- If you are in the public preview program or Targeted release program, you will have access to the Try the new Teams toggle. Our preview roll out will on November 2, 2023 to Chrome and Edge browsers.
Note: Admins can choose individuals or the entire organization to receive updates in the Targeted release program.
- If you are in production, as an admin you will have the option to opt-in your users by using the Teams update management policy to select which users in your organization can see the toggle and get access to new Teams. Users can use the new Teams and switch back to classic Teams anytime. Our goal is to ensure you are fully empowered to try new Teams in a manner that’s right for you as early as possible.
Visit the support article or download resources to learn how to get started with the new Teams experience.
Additional information and support Blog
MC686281 — New Gallery in Teams Meetings
>60 Days
Microsoft 365 Roadmap ID 118467
We are introducing a revamped version of the gallery in Teams meetings and calls. The new gallery will be the default view when users join their meetings, so that they can use it without the need of taking an action.
When this will happen:
Targeted Release: We will begin rolling out early December 2023 and expect to complete by mid-December 2023.
Production and GCC: We will begin rolling out early January 2024 and expect to complete by mid-January 2024.
GCC High: We will begin rolling mid-January 2024 and expect to complete by late January 2024.
DoD: We will begin rolling out late January 2024 and expect to complete by early February 2024.
How this will affect your organization:
This new version introduces a series of changes to help users in their meetings:
- 16:9 aspect ratio participant tiles for more predictability. A consistent aspect ratio maintains a more predictable experience when users turn their videos on or off. It also provides more visibility into users' body language and hand gestures.
- An audio-video mixed gallery for a more inclusive representation. Audio and video users share now the same space by default.
- Meeting rooms are displayed larger than individual participants. In certain meeting sizes, we display Microsoft Teams Rooms video in a larger size than the rest of the participants to give an equivalent weight to participants joining from a meeting room. Non-Teams rooms joining Teams meeting via Direct Guest Join will remain the same tile size as today.
- You appear next to the rest of the participants. Your own tile will now be included next to the rest of the participants.
- Customization of the gallery. Users can adapt the gallery to their needs or preferences. The customization options include:
- Gallery size: Users can choose the maximum number of tiles that will be represented per page. The entry point for this action is available through the meeting toolbar: "View" > "Change gallery size".
- Placement of your own tile: For users who prefer to keep themselves separated from the rest of the participants. If chosen, the self-tile will be placed in an area separate from the rest of the participants. The entry point for this action is available through the meeting toolbar: "View" > "More options" > "Remove me from gallery".
- Prioritizing videos: For users who want to give a higher weight to participants with their video on. If chosen, video participants will be displayed more prominently than audio participants. The entry point for this action is available through the meeting toolbar: "View" > "Prioritize video".
- Meeting room tile size: Users can decide if they want to resize the meeting room tile to the same size as the rest of the participants. The entry point for this action is available in the contextual menu of the room tile.
What you need to do to prepare:
Please notify your users about this change and update any training documentation, as appropriate.
MC686279 — Stream App in Microsoft Teams will be updated to Stream (on SharePoint)
<30 Days
We are transitioning the Stream experience in the desktop client of Microsoft Teams from Stream (Classic) to Stream (on SharePoint). Once transitioned the Stream app in Microsoft Teams will display only Stream (on SharePoint) content--it will no longer display Stream (Classic) content. The new Stream (on SharePoint) app in Teams will feature similar content and features as found on the Stream start page.
The Stream app is currently accessible across multiple touchpoints on Teams, including the Stream app on Teams left rail, Stream on Teams message extension, and the Stream Tab on Chats/Channels. You can find the app by tapping the three dots on the Teams left rail and then search for Stream. As a first step, Stream app on Teams left rail will be updated to Stream (on Sharepoint). This updated version of Stream app will allow users to access the Stream start page within Teams, and quickly find and watch videos without switching apps. Users will have the option to pin the Stream app on the side panel for more convenient access in the future.
In the coming months, we will also transition the Stream app for Teams web and Teams mobile.
When this will happen:
Standard Release: We will begin rolling out early November and expect to complete by mid-November.
How this will affect your organization:
All users will see the Stream Start page when they access Stream App from Teams desktop client after this updated version is rolled out.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC686187 — Classic Teams Users Will be Automatically Updated to New Teams After March 31, 2024
>60 Days
On October 5, 2023, we announced general availability of the new Microsoft Teams app for Windows and Mac. Read the message center post MC679451 for details.
We mentioned in our GA announcement that classic Teams users will be automatically updated to new Teams in the coming months. Today, we want to inform you that after March 31, 2024, any classic Teams users who have not updated to new Teams, will be automatically updated to new Teams.
With just one click, you can join millions of users who are relying on new Teams to stay connected with colleagues, partners, and customers.
How will this affect your organization?
- New Teams is a performance-focused update. New Teams is up to 2x faster and use 50% less memory. There is no major impact to the user experience for new Teams. This means you don’t need to invest in any additional training.
- Between now and March 31, 2024, you can continue to use classic Teams without interruption.
We encourage you to review the service agreement that governs Teams app updates.
If you haven’t already updated to new Teams yet, review the prerequisites and policy updates for the update to new Teams.
How can I prepare for a seamless update to new Teams?
- Admins can enable new Teams in their organizations by leveraging robust IT admin policies and taking advantage of deployment options such as office update channels that allow them to enable users and groups within their organizations as needed.
- Admins who currently have the Teams update policy set to 'Not enabled' for the 'Use new Teams client' setting, we suggest setting the value as ‘New Teams only’ after selecting the Teams update policy to ‘Microsoft controlled’ in the Teams admin center.
Notes:
- We have not made the new Teams in the Virtual Desktop Infrastructure (VDI) environment generally available yet, so the VDI users will not be affected by the auto-update timeline of March 31, 2024.
- Microsoft Teams Rooms (MTR) and Surface Hub devices will also not be affected by the March 31, 2024, timeline.
- For our education users, the update option to new Teams is available now and they can be seamlessly updated at any time. Please visit this page for more information.
To learn more about this announcement, view this page.
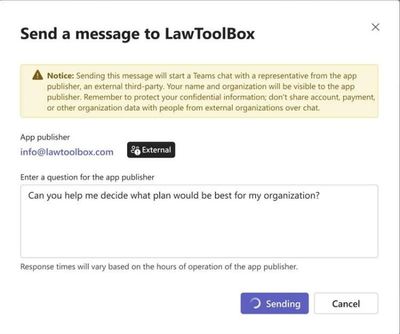
MC685934 — New Feature in Teams Admin Center to Communicate with Third-Party App Publishers via Teams
30-60 Days
Microsoft 365 Roadmap ID 182034
Microsoft Teams admins will soon be able to initiate private groups chats with a limited set of third-party Teams app publishers via a new 'Click-to-Chat' (C2C) feature being added to the Teams Admin Center (TAC).
When this will happen:
Standard Release: Rollout will begin late November and will complete by late December 2023.
How this will affect your organization:
As part of this feature, Teams admins will be able to quickly communicate directly with app publishers to assess whether an app will meet their business including questions regarding data compliance, pricing and deployment. If an app publisher supports this feature, admins will discover a C2C button in the app card in the manage apps tab of TAC (screenshot below).
Note: if an admin has disabled external communications in their tenant, C2C will also be disabled. While the C2C button will appear, attempts to initiate a chat will result in an dialog providing an email address to which the admin can submit their questions outside of Teams.
What you need to do to prepare:
No action if external communications are already enabled. If you have disabled external communications in your Teams tenant, consider whether to enable for ISVs that support this feature.
MC684868 — Analytics Insights for Virtual Appointments in Microsoft Teams
<30 Days
Microsoft 365 Roadmap ID 161629
Tenant admins can see updated virtual appointment analytics with new insights in Teams to help driving business outcomes, including average lobby wait times for scheduled vs. on-demand appointments, percentage of appointments completed after scheduled end time, and percentage of appointments with a late start.
When this will happen:
Targeted Release: We will begin rolling out early November and expect to complete by mid-November.
Standard Release: We will begin rolling out mid-November and expect to complete by late November.
How this will affect your organization:
Tenant Admins will be able to see insights of their organization's usage of Virtual Appointments tied to Bookings calendars. The insights will be visible in the Analytics tab inside the Virtual Appointments application in Teams.
What you need to do to prepare:
There is no pre-work needed. Simply navigate to Analytics tab to start seeing the insights. The current reports and controls continue to be available.
MC684867 — New Microsoft Teams Store now available in GCC High and DoD
<30 Days
Microsoft 365 Roadmap ID 174474
We are delighted to announce the launch of the new Teams app store experience in GCC High and DoD! Teams Store has been rebuilt and designed with our customers’ needs as the priority. It is centered around experiences that make discovering and installing apps into teams, chats, and meetings simple.
The first thing customers will experience as they enter the Teams Store is a sleek, redesigned landing page that brings relevant apps right to them. The new carousel at the top spotlights a set of apps that they may find interesting – which we’ll update frequently. We’ve created new categories, which makes it easier for users to find intelligent recommendations for apps based on what their colleagues and peers are using – making it easy for them to get started with apps popular in the organization.
The addition of “Manage your apps” in the store will allow users to update, remove, share or “get more apps”. Admins will be able to upload custom apps to their organizations from this page as well.
When this will happen:
Standard Release: We will begin rolling out mid-November and expect to complete by late November.
How this will affect your organization:
GCCH and DOD customers will now have access to the new Store experience. Users will find an updated app category bar on the left that breaks out apps into intuitive segments and apps built for your organization and/or colleagues. And new featured apps that spotlight the latest and greatest apps that are popular across all Teams users.
What you need to do to prepare:
Admins will be able to upload line-of-business/custom apps from:
- Teams store under “Manage your apps” page.
- Teams Admin Center under the “Manage apps” page.
Upload your app from Teams store.
You can sideload your app to a team, chat, meeting, or for personal use depending on how you configured your app's scope.
- Log in to the Teams client with your Microsoft 365 development account.
- Select Apps > Manage your apps and upload an app.
- Select Upload a custom app.
- Select your app package .zip file.
- Add your app to Teams as per your requirement:
- Select Add to add your personal app.
- Use the dropdown menu to add your app to a Team or chat.
Upload a custom app using Teams admin center.
To make the app available to users in your organization's app store, follow these steps:
- Access Teams admin center and go to Teams apps > Manage apps.
- Select Upload new app, select Upload, and select the app package that you received from the developer.
Admins can update existing custom apps, set up and manage app policies from Teams Admin Center.
Update a custom app using Teams admin center.
To update and existing custom app, follow these steps:
- Access Teams admin center and go to Teams apps > Manage apps.
- Select the name of the existing custom app to open its app details page.
- On the banner of the app, select Upload file, and provide the updated app package.
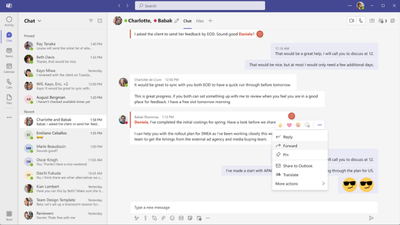
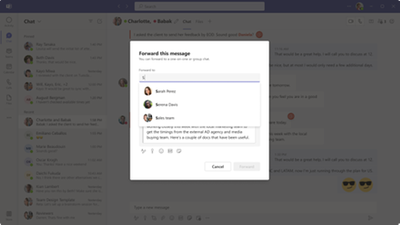
MC684532 — Microsoft Teams: Forward Messages in Teams Chats
>60 Days
Microsoft 365 Roadmap ID 90585
With the forward message feature, Microsoft Teams users will soon be able to send chat messages from one chat to another. Messages can be forwarded to 1:1 chats, group chats and meeting chats. This feature will also allow the sender to add additional content to the message in order to provide context and clarity to the recipient. This feature will be rolling out across Microsoft Teams Desktop, Web and Mobile.
When this will happen:
Rollout will begin in late November 2023 and is expected to be complete by mid-February 2024.
- Targeted release: Rollout will occur in late November 2023
- Standard release: Rollout will occur in mid-January 2024
- GCC, GCCH and DoD: Rollout will begin in late January 2024 and be complete by mid-February 2024
How this will affect your organization:
The entry point for the forward message feature will be in the overflow menu.
Upon clicking this button, the forward message compose dialog will populate the screen.
In the compose dialog, users will have the option to select from the people picker menu who the message will be forwarded to. A message can be forwarded to an existing named group chat, a new group chat, a meeting chat or a 1:1 chat. Currently, users will only be able to forward one message to one chat at a time.
In the compose dialog, the user can also add an additional message to accompany the forwarded message to provide context.
Once the message has been forwarded, the chat will bubble up to the top of the user’s chat list, and the message will appear in the chat in the format shown below.
What you need to do to prepare:
It is recommended that you notify your users about this new capability to forward messages and update your training and documentation as appropriate.
MC684220 — Creation of Default Notes tab in new standard channels in Teams
<30 Days
Microsoft 365 Roadmap ID 180484
As communicated in MC496248 (January '23) Microsoft Teams users will soon get a “Notes” tab, powered by OneNote, added by default on the tabs bar across the top on creation of new standard channels for note-taking capabilities. Earlier this capability was powered by Wiki, which is set to retire from Teams based on the announcement, MC496248, published in January.
When this will happen:
This will start rolling out by mid-November 2023 and expect to complete by late November 2023.
How this will affect your organization:
With this release, users will see a tab called “Notes” which is powered by OneNote, when they create a new standard channel in Teams. We’ll leverage the default OneNote notebook created at a team level for this purpose. When a new standard channel is created within the team, a new section will be created with the same as channel dedicated for notetaking within this channel.
OneNote is the Microsoft 365 app for notetaking that offers that offers:
- Easy collaboration across the team
- View all channel notes in a team in one place organized within a single notebook
- Rich editing with typing, ink annotations, highlighting, file attachments, etc.
- Easy recall & search for channel notes within OneNote on any platform
What you need to do to prepare:
If your organization has not enabled OneNote you can review this documentation: Deployment guide for OneNote
FAQs
How can I access the content captured for all channels in Notes tab?
All members in a team will be able to access the content captured in Notes tab across all standard channels within that team by clicking on the Show navigation
icon on left.
How can I add back Notes tab to a channel if it is accidentally removed?
Please note that Notes tab by default is only supported in standard channels at the moment. If your standard channel used to have a Notes tab, you can add it back.
- In Teams, go to the channel you want to add the Notes tab again.
- In the tabs bar across the top, select Add a tab
. The Add a tab window will open. - Select the OneNote tile. The OneNote window will open.
- Select the “Default team notebook” for your team, then select Save.
- A tab with the team notebook name will be added in the tabs bar across the top. Right-click the tab to rename it to “Notes”.
- Go to the Notes tab and select the show navigation icon. Create a new section in this notebook and give it the same name as the Teams channel.
Note: Having a dedicated section for each channel will help avoid confusion for others who access the notebook.
- In the section, create a page, name it, and start taking notes.
Why is Teams retiring wiki?
Please read the details on Wiki retirement in MC496248 (January '23).
Known limitation:
- OneNote notes only display in Default (Light) and High contrast mode.
MC683929 — Workflows within Microsoft Teams chats menu
<30 Days
Microsoft 365 Roadmap ID 180364
Microsoft Teams will be bringing workflows powered by Power Automate into the overflow menu for chats.
To make sure Microsoft Teams provides the best workflow experience for our users we are making it easier to configure workflows for chats. From the list of chats users will be able to go into the overflow menu for a specific chat (...) and select "Workflows". Here they will see a list of workflow templates specific to chats within Teams. Users can then configure these templates to their needs and deploy them to the chat.
When this will happen:
Standard Release: We will begin rolling out mid-November and expect to complete by late November 2023.
How this will affect your organization:
If the Power Automate app is disabled in Teams Admin Center, users will not see this option within the overflow menu.
This feature will only be available within the New Teams client.
What you need to do to prepare:
Consider bringing awareness to your users about this change if your users use workflows so they know where to find the new entry point.
MC683928 — Microsoft Teams: In-meeting Error Messaging
>60 Days
Microsoft 365 Roadmap ID 167211
Microsoft Teams Meeting users will be notified directly through the error message on meeting right pane for why they cannot access meeting chats when their chat access is limited by policy or due to system limitations and unexpected errors.
When this will happen:
Targeted Release: We will begin rolling out mid-November and expect to complete by late November.
Standard Release: We will begin rolling out early December and expect to complete by mid-December.
GCC: We will begin rolling out early January and expect to complete by mid-January.
GCCH: We will begin rolling out mid-January and expect to complete by late January.
DoD: We will begin rolling out early February and expect to complete by mid-February.
How this will affect your organization:
Once available, users will begin to understand why they cannot access certain chats during meetings.
What you need to do to prepare:
There is no action needed to prepare for this change.
MC683927 — (Updated) Microsoft Teams: Remote Setting for QR code on Teams Panels
30-60 Days
Updated November 2, 2023: We have updated this message to insure visibility for all customers. The content below has not changed.
With this update, admins can remotely turn the Teams Panel QR code setting on/off through Teams Admin Center. On the device, this setting is called 'Allow room reservations by QR code', and it controls whether there is a QR code shown in the top left of the home screen. In Teams Admin Center, it will be called 'People can scan a QR code to reserve a room.'
When this will happen:
Roll out is expected to begin in early November 2023 and complete by early December 2023.
What you need to do to prepare:
Please plan on updating all Microsoft Teams panels in your tenant to the latest version. You may want to update your training and documentation as appropriate.
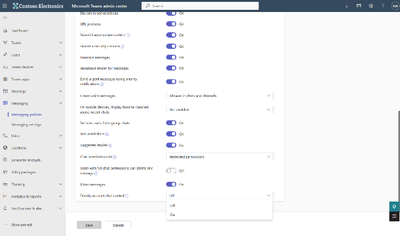
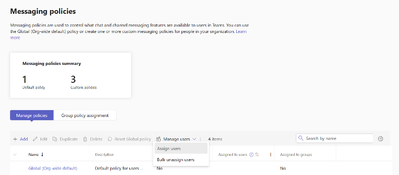
MC683926 — Priority Account Chat Controls General Availability
30-60 Days
Microsoft 365 Roadmap ID 144367
As part of the Teams Premium package, we are introducing a new management capability: Priority Account Chat Controls that empower users with decision making controls for unwanted internal communications via policies setting. Users are notified about chats from new contacts, giving them a choice to accept or block the conversations.
When this will happen:
Standard Release: We will begin rolling in late November 2023 and expect to complete by early December 2023.
How this will affect your organization:
For Admins:
You will need to setup a Policy in the Teams Admin center. Turn on the feature in Message Settings to be able to add this feature to either existing user policies or create new ones and assign them to individuals or groups in the Teams Admin Center.
Enable Priority Account Chat Control on the Messaging settings page.
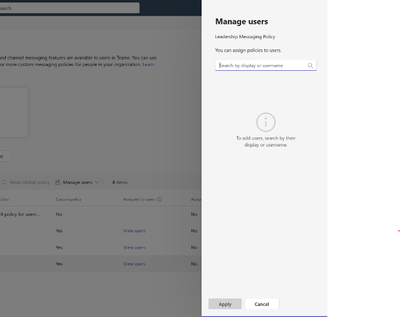
Navigate to the Messaging policies page, create a new policy or update an existing policy to set the value of Priority Account Chat Control to 'Yes'.
Assign users to the policy.
Search for the users you would like to assign the policy to.
Click Apply.
For End Users:
Users with priority account chat controls set up in their user policy will be able to accept or block new incoming in-org messages. If the conversation is accepted, they are able to chat regularly and if the conversation is blocked, no further communication will happen for that chat. A user with priority account chat controls can block and unblock all users in their organization at any given time.
What you need to do to prepare:
This feature is turned off by default and will require you to explicitly turn on the feature and assign it to users in your organization.
MC683662 — Microsoft Teams: Quickly Capture Content in Teams Mobile
<30 Days
Microsoft 365 Roadmap ID 171217
This feature enables you to quickly capture content shared in a Teams meeting on a mobile device and save it in your photo gallery or share in Teams and other apps. We’ll honor privacy choices set in the meeting.
When this will happen:
We will begin rolling out in early November 2023 and expect to complete rollout by late November 2023.
How this will affect your organization:
Most meetings involve some form of content that folks in the meeting might want to refer back to, or share with others – however, the only way to do this right now is through watching meeting recordings, or taking OS-level screenshots to share. Quick Capture will enable users to take screenshots and annotate/add text to content, to be saved and/or shared with Teams or outside of Teams, using sensitivity labels to ensure only content that is allowed to be saved/shared is done so.
What you need to do to prepare:
There is nothing you need to do to prepare. You may want to notify users of this feature.
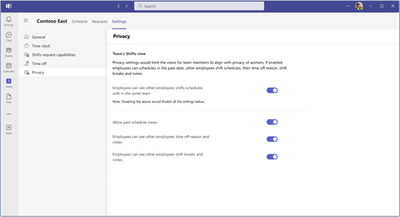
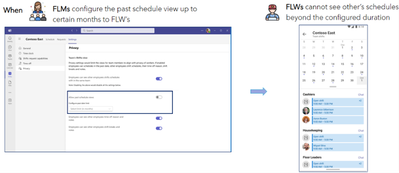
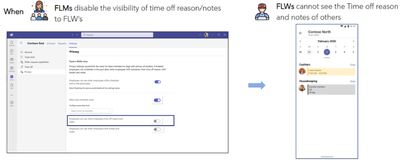
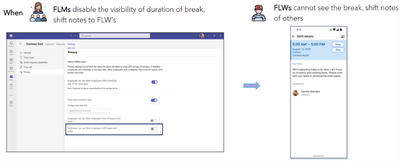
MC683659 — Microsoft Teams: Additional manager-controlled privacy settings in Shifts
<30 Days
Microsoft 365 Roadmap ID 152119
We are thrilled to announce exciting product enhancements on frontline managers-controlled privacy settings for frontline workers.
When this will happen:
We will roll out in November 2023.
How this will affect your organization:
Manager-Controlled Privacy Settings for Frontline workers
Frontline managers now have the power to manage shift information visibility for their employees through the newly available privacy controls in Shifts settings. Here's what this feature includes:
- Team Shifts View: Managers can enable or disable the Team Shifts View, giving frontline workers the ability (or not) to see their co-workers' shifts.
- Limited Past Views: Managers can restrict how far back frontline workers can view their co-workers' schedules, ensuring historical data privacy.
- Generic Time Off View: Frontline workers can see their co-workers' time off in a generic way, without viewing the specific reasons and notes.
- Limited Shift Details: Managers can limit the level of detail frontline workers can access about their co-workers' schedules, excluding sensitive information like Shift notes and break durations.
What you need to do to prepare:
There is nothing you need to do to prepare for these changes, besides you may want to notify your frontline managers about these updates.
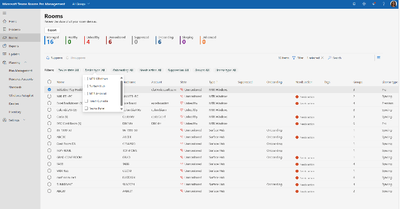
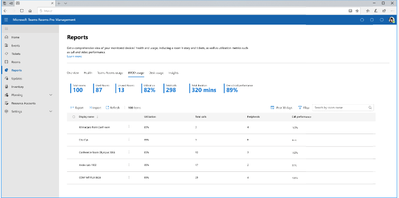
MC683041 — Microsoft Teams Rooms Pro Management Improved Search for rooms
30-60 Days
Microsoft 365 Roadmap ID 141821
In the Teams Rooms Pro Management Portal, the new "Search and Filters for Rooms" feature will be available in the Rooms tab and will allow IT admins to easily search specific rooms and utilize the filtering options to capture rooms data within small sets based on specific criteria.
When this will happen:
We will begin rolling out late November 2023 and expect to complete rollout by early December 2023.
How this will affect your organization:
The new “Search and Filters for Rooms” features will allow IT admins to efficiently locate specific rooms and capture rooms’ data within a small set based on specific criteria such as room type, states, licenses, groups
To utilize the search and filter functions, IT admins will need to follow these steps:
- Log in to the Pro Management Portal.
- Navigate to the Rooms Tab
- Below the headline metrics, the new search bar and filters will be shown.
Within the search bar, IT admins can enter the name, hostname, or account of the specific room they are looking at.
Below the search bar, there will be a list of filter options, each allowing users to select a category of rooms based on specific criteria.
What you need to do to prepare:
To have access to the Teams Rooms Pro Management Portal, admins will need to have at least one pro or premium license.
MC682302 — Microsoft Teams: Excel import enhancements in Shifts app
>60 Days
Microsoft 365 Roadmap ID 169705
We are thrilled to announce exciting product enhancements to our import and export Excel experiences in Shifts designed to empower frontline managers to achieve more.
When this will happen:
We will begin rolling out mid-November 2023 and expect to complete by late February 2024.
How this will affect your organization:
Import and export time offs and open shifts using Excel.
Until now, Frontline managers have only been able to import assigned shifts from Excel into Shifts. Now, we have expanded the supported entities by providing managers with more flexibility when creating schedules. This feature launch is being carried out in multiple phases.
Here’s what this feature includes:
Import a schedule includes time off and open shifts:
- Frontline managers can import assigned shifts, time offs and open shifts through the same Excel file into Shifts. There will be different worksheets for those 3 entities that managers will require to fill in according to what is wished to be imported.
- To respect Shifts settings, open shifts won’t be synced to Shifts calendar when imported through Excel whenever the open shift setting is disabled for a team.
Prevent duplication of groups:
Frontline managers can select groups in the import sample file from a pre-populated list with the existing available schedule groups in the team.
‘Export in a format that can be imported’ includes open shifts and time-offs:
Frontline managers can export, for a specific period, a schedule that might include assigned shifts, time offs and open shifts.
What you need to do to prepare:
There is nothing you need to do to prepare for these changes, besides you may want to notify your frontline manager about these updates.
MC682299 — Workflows Message Extension will be updated to include new pinned default actions
<30 Days
Microsoft 365 Roadmap ID 167324
The Workflows Message Extension in Microsoft Teams will include new default actions to assist user collaboration. These actions will help users quickly tackle common, multi-step activities within any conversation. The new default actions include capabilities for meetings, tasks, and status updates from others. Most workflows post an adaptive card to build transparency across the group.
When this will happen:
We will begin rolling out in early November and complete roll out by mid-November.
How this will affect your organization:
The Workflows Message Extension will include new default actions that post cards to the active conversation.
Existing user-created actions will persist in the Workflows Message Extension and users will still be able to create new actions from within Workflows by browsing workflow templates or creating a custom workflow.
What you need to do to prepare:
Consider bringing awareness to your users about this change if your tenant uses the Workflows Message Extension.
If Admins have disabled the Updates Teams app, the updates default action will not be listed in the Workflows Message Extension.
MC682089 — Microsoft Teams: Teams Connect shared channels
<30 Days
Microsoft 365 Roadmap ID 180742
Teams Connect shared channels makes collaborating with those inside and outside your organization easier. Multiple organizations can work together in a shared space, have conversations, schedule a meeting, share, and co-author files, and collaborate on apps, without ever switching tenants in a secure, governable and compliant environment.
When this will happen:
GCCH Release: We will begin rolling out early November and expect to complete mid-November.
DoD Release: We will begin rolling out early November and expect to complete mid-November.
How this will affect your organization:
Shared channels is enabled by default in Teams. You can choose if people can create shared channels, if they can share them with people outside your organization, and if they can participate in external shared channels by creating a channel policy.
If you plan to share channels with people outside your organization, read Plan external collaboration for important planning considerations.
Sharing channels with people outside your organization also requires that you configure cross-tenant access settings in Azure AD. Each organization that you want to share channels with must also complete this configuration. See Collaborate with external participants in a channel for details.
What you need to do to prepare:
Read our documentation for shared channels to get started.
MC682086 — Addition of Chat button in Missed Call Activity
30-60 Days
Microsoft 365 Roadmap ID 176318
Teams users will have an option to chat with Teams users after receiving a missed call from them by simply clicking on an additional ‘chat’ button on the missed call activity.
When this will happen:
Targeted Release: We will begin rolling out early November and expect to complete by early November.
Standard Release: We will begin rolling out late November and expect to complete by early December.
How this will affect your organization:
There are no tenant level settings. Defaults will not change.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC681891 — New Call Shortcuts in New Teams
>60 Days
Microsoft 365 Roadmap ID 164200
We are changing the keyboard shortcuts used to initiate calls in Teams to create differentiation from other commonly used shortcuts and reduce accidental calls. The new shortcuts for Windows will be: Alt + Shift + A to initiate audio calls, Alt + Shift + V for video calls. For MacOs the new short cuts will be:Option + Shift + A to initiate audio calls, Option + Shift + V for video calls.
When this will happen:
General Availability: We will begin rolling out early November 2023 and expect to complete by mid-November 2023.
GCC, GCCHigh and DoD: We will begin rolling out early January 2024 and expect to complete by late January 2024.
How this will affect your organization:
There is no admin impact.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC681887 — Microsoft Teams | Front Row Enhancement: Active video speaker promotion for Teams Rooms on Windows
30-60 Days
Microsoft 365 Roadmap ID 161825
The latest version of Teams Rooms on Windows app 4.19 includes updates to Front Row experience to promote active video speakers to the spotlight area to improve space utilization and provide in-room users with immersive experience across single and dual display configurations.
When this will happen:
Standard Release: We will begin rolling out mid-November and expect to complete it by late-December.
How this will affect your organization:
The Front Row layout is improved to promote pinned or spotlighted participants to the center stage when there is no shared content in the meeting. This addresses customer feedback on empty space utilization and aligns pinned or spotlighted participants treatment across single and dual front of room displays. Additionally, active speaker video is promoted to the center stage to utilize display to create immersive experience for in room users. For single display configurations, when no one is pinned, spotlighted or sharing content, the most recent active speaker video will be promoted to the center. In dual display mode, when no one is pinned, spotlighted or sharing content, two most recent active speaker videos are promoted to the center on each screen. When someone is sharing content in the meeting, it’s displayed on one display while the other display shows the most recent active video speaker.
What you need to do to prepare:
Please notify your users about this new experience and update your training and documentation as appropriate.
MC681886 — Microsoft Teams | Support Joining a Teams Live Event as Attendee for Teams Rooms on Windows
30-60 Days
Microsoft 365 Roadmap ID 169881
The latest version of Teams Rooms on Windows app 4.19 update includes the support joining a Teams live event as an attendee.
When this will happen:
Standard Release: We will begin rolling out mid-November and expect to complete it by late December.
How this will affect your organization:
Teams Rooms on Windows can now join a Teams live event as an attendee and watch the streaming experience. Please follow the steps below:
- Create a meeting using your work account’s Teams Calendar or Outlook Calender on desktop or mobile.
- Add a conference room (a Microsoft Teams Rooms account) as an attendee directly to the meeting invite.
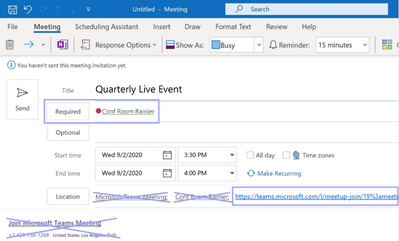
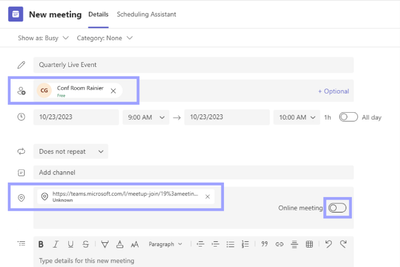
- Remove any values in the “Location” and "Body text” fields on the invite. Please make sure the invite does NOT attach any other Teams meeting link that can be automatically created depending on your setting.
- Copy and paste a Teams live event link for attendees into the “Location” field on your invite. Don’t paste it in the "Body text” field.
- Send the meeting invite.
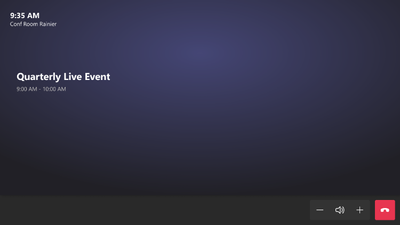
- The Microsoft Teams Rooms on Windows at the conference room you invited should get the invite and show the “Join” button.
- Click the “Join” button and enjoy the streaming experience for Teams live event attendees.
Outlook Example Image:
Teams Example Image:
Microsoft Teams Rooms Console during a Teams Live Event as an Attendee:
What you need to do to prepare:
Please notify your users about this new experience and update your training and documentation as appropriate.
MC681884 — macOS name change: Microsoft Teams to Microsoft Teams classic MDM Impact
Rolled Out
With the recent GA of New Teams on Mac, there are changes that impact the management of some tenants regarding new Teams and Microsoft Teams classic (formerly Microsoft Teams). New Teams, now with the app name Microsoft Teams (work or school), exists side by side on macOS with Microsoft Teams, now with the app name Microsoft Teams classic. Via an in-app toggle, users can seamlessly switch between New Teams and Microsoft Teams classic.
However, there are implications for tenant administration that have arisen that administrators should be aware of.
Bundle IDs for new and classic Teams remain the same:
- The bundle ID for Microsoft Teams classic remains the same:
com.microsoft.teams
- The bundle ID for Microsoft Teams (work or school) is:
com.microsoft.teams2
Note: this is the same bundle ID for the preview version which was named Microsoft Teams (work preview)
MacOS .app file name changes with the recent GA of new Teams:
- Microsoft Teams classic-- formerly Microsoft Teams:
Changed from:
Microsoft Teams.app
to
Microsoft Teams classic.app
- New Teams-- now officially Microsoft Teams (work or school):
Changed from:
Microsoft Teams (work preview).app
to
Microsoft Teams (work or school).app
Important MDM scenarios these changes can impact:
If you have an MDM implementation that periodically checks whether Microsoft Teams is installed on a given Mac device in your tenant based upon the .app name, and then installs a version of Teams if it isn’t present, then you may find that devices can have two version of Teams classic installed on the device: Microsoft Teams and Microsoft Teams classic.
If this happens, it should not require any action to remove the duplicate old Microsoft Teams version. When the old Microsoft Teams version next updates, the machine will be left with a single Microsoft Teams classic version on the device.
Prevention:
To prevent the above scenario from initially happening or repeating, admins should change the implementation to use the Teams bundle ID rather than the .app name when checking for the presence of Teams on a device. Alternatively, admins can update the .app name check to Microsoft Teams classic.
Important:
The new Teams currently has the .app name Microsoft Teams (work or school).app, but in the coming months it will change over to Microsoft Teams.app, so it is strongly recommended to use the bundle ID going forward in all cases to avoid a repetition of the above scenario.
Transition Timeline for Microsoft Teams Classic:
Daily users of the now Microsoft Teams classic, should have automatically received an update that changed the name of the app from Microsoft Teams to Microsoft Teams classic in September via built-in custom updater.
User who rarely open Teams should have recently received the update via Microsoft Auto-update which was released on 10/10/23
The latest Microsoft Teams classic build can be downloaded here: Teams_osx.pkg download.
Builds with the original "Microsoft Teams.app" naming convention - 626463 and earlier
Builds with the new "Microsoft Teams classic.app" naming convention - 627656 and later
Important! Ensure that any new MDM deployments that you may use include a build that uses the Microsoft Teams classic.app convention, meaning with a build 627656 and later.
For general information on upgrading and policies related to deployment of the new Teams, see:
Upgrade to the new Teams using policies
For specifics on New Teams for Mac, see:
New Teams for Mac – Overview and prerequisites
The download link for the latest new Teams GA build: MicrosoftTeams.pkg download.
For the remainder of calendar year 2023, the Microsoft 365 BusinessPro Suite installer will continue to include Teams classic. In early 2024, Teams classic will be replaced with the new Teams client BusinessPro Suite installer.
MC680963 — Bring-Your-Own-Device IT Admin Experience in Teams Pro Management Portal
30-60 Days
Microsoft 365 Roadmap ID 161728
BYOD (Bring Your Own Device) rooms are identified as rooms with no MTR (Microsoft Teams Rooms) but equipped with other peripherals such as camera, microphone.
In Teams Pro Management Portal, IT admins will finally have the capability to manage and track these specific BYOD rooms. They will get a comprehensive overview of their BYOD rooms and devices activities. With this new addition, they will gain valuable insights into how these spaces are being utilized and enabling them to make data driven decisions.
When this will happen:
We will begin rolling out in late November 2023 and expect to complete rollout by early December 2023.
How this will affect your organization:
IT admins will gain visibility of the BYOD rooms in the Teams Pro Management Portal upon logging in. To have access the portal, they will need at least one Pro, premium or Teams Shared Device license.
Under the Inventory tab, they will find a comprehensive list of all rooms within their organization, including information about BYOD rooms and devices.
Within the Inventory tab under the device page, IT admins will also have the capability to associate each device to its specific BYOD room. This association will be done in two different methods, with the "Import" function by importing the list of devices and adding the room information, or through auto discovery by selecting the specific room from list of available rooms.
In the Report tab, admins can finally see the BYOD rooms specific utilization metrics. However, an 8$ Teams Shared Device license will need to be assigned per room to have access to the BYOD usage report.
What you need to do to prepare:
To have access to the BYOD in Teams Pro Management Portal, at least one pro/premium or Teams Shared Device license is required on tenant level.
MC680960 — Reminder: Upcoming property changes in Microsoft Graph callRecord change notifications
Rolled Out
Earlier this year we announced an upcoming breaking change for developers using webhook change notifications for the callRecords Microsoft Graph API. This message provides a final notification and confirmation of the changes that will occur the week of October 30, 2023.
How this will affect your organization:
If you have automation or reporting using the "oDataId" and "oDataType" fields in Microsoft Graph API callRecord change notifications you will need to update to use the new "@odata.id" and "@odata.type" fields. As a part of this change, please note the content of the "@odata.type" field will be "#Microsoft.Graph.callRecord."
What you need to do to prepare:
Ensure you are now using the new field names and content in your webhook processing.
MC680662 — Microsoft Teams: Intelligent Recap Support for Additional Languages (Premium)
<30 Days
Intelligent recap leverages AI to automatically provide a comprehensive overview of your meeting, helping users save time catching up and coordinating next steps. We are bringing support for additional languages for Intelligent Recap experiences for Teams Premium users.
The additional languages include: Chinese Simplified, French, German, Italian, Japanese, Spanish, and Portuguese.
When this will happen:
We will begin rolling out in late October 2023 and expect to complete rollout by late November 2023.
How this will affect your organization:
Teams Premium users who have meetings conducted in the additional languages can now get a full Intelligent Recap experience. If the meeting is recorded and transcribed with the spoken language set to either of the supported languages (Chinese Simplified, French, German, Italian, Japanese, Spanish, and Portuguese), AI features will be available to Teams Premium users after the meeting ends. Users will receive a similar experience as below, but AI Notes/tasks will be provided in the languages of the meeting transcript.
What you need to do to prepare:
You may want to consider updating your training documentation or inform Teams Premium users about the new capability.
MC680353 — Saved items availability in New Teams
TBD
Currently New Teams does not have a Saved feature. This will continue to exist in Classic Teams. In the coming months we'll provide users with the option of downloading Classic Teams saved items to a doc with hyperlinks to open them. Additionally, a new and improved Saved feature is planned to come into New Teams next year.
When this will happen:
With New Teams availability.
How this will affect your organization:
Users who switch from Classic Teams to new Teams will not be able to view their Saved content. If users wish to see their Saved content, they can switch back to Classic Teams to see these items.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
MC680348 — Custom Backgrounds for Announcement Posts in Channels
>60 Days
Microsoft 365 Roadmap ID 123501
Microsoft Teams users will soon be able to create custom backgrounds for their Announcement posts with the generative AI power of Microsoft Designer. This release of Custom Backgrounds for Announcement Posts will be rolling out across Microsoft Teams Desktop and Web for Channels 2.0 in English – US markets only. In line with current announcement behavior, Mobile will only support the consumption of custom backgrounds. Feature is disabled for EDU tenants while the team implements a policy setting.
When this will happen:
Preview: We will begin rolling out mid-October and expect to complete by late October.
Targeted Release: We will begin rolling out mid-October and expect to complete by late October.
Standard Release/GCC: We will begin rolling out early November and expect to complete by mid-November.
GCC High/DoD: We will begin rolling out in late November and expect to complete by mid-January.
How this will affect your organization:
Before, in Channels 1.0, users struggled to "find the right picture," to "find images that work correctly with banner sizing, so it takes ages," etc.
Now, whether users have their own image or an idea in mind, or absolutely nothing at all, they can create rich, engaging backgrounds for their announcement posts through the generative AI power of Microsoft Designer. A few clicks is all it takes--let the imagination run wild!
You can find the entry point icon to the Designer integration at the bottom right corner of the announcement.
The Designer Mini Dialog is where all the magic happens. You can write a description, upload an image, or click one of the examples we have provided for you to start.
Once you have selected a background you like, you’ll see the option to press “Customize” or “Done.” “Done” inserts the background into your Announcement while “Customize” launches the Microsoft Designer App where you can further customize your background.
The Designer App provides flexibility and endless power for you to create exactly what you want
What you need to do to prepare:
You may want to notify your users about this new capability to better express themselves and engage their audience in their Announcements. Additionally, due to the inevitable generative AI learning curve, you may want to provide additional training/documentation as you see fit. You can also lead by example and show your users what’s possible.
While we work on making a policy setting available to tenants, this feature will be enabled by default (except in EDU). If there are concerns, please contact support.
We can't wait to see what announcement backgrounds you and your team come up with.
MC679738 — Microsoft Teams: Automatic Updates for the Teams app on Android-based Teams Devices
<30 Days
Microsoft 365 Roadmap ID 163598
Android-based Teams devices will start receiving automatic updates for Teams app, in addition to firmware.
When this will happen:
Rollout will begin in late October 2023 and is expected to be complete by early November 2023.
How this will affect your organization:
The Android-based Teams devices (Teams Rooms on Android, Teams Phones, Panels, and Displays) will start receiving automatic updates of the Teams app. The overall internal guardrails and features to manage the updates remain similar to those for automatic firmware updates. Administrators can find them on pages under Teams devices in Teams admin center.
The following capabilities can be used to manage these updates:
Update phases can be found after selecting the Update option after selecting a device.
- You can assign devices to these phases and the updates will rollout adhering to these. You can select multiple devices and assign a phase to them together as well.
- These phase timelines are different from those for Firmware auto-updates. Since the Teams app versions contain smaller changes and are released much more frequently, the rollout is much faster.
For Teams app automatic updates
- Validation phase - Updates start as soon as a new version is published.
- General phase - Updates start only 15 days after a new version is published.
- Final phase - Updates start only 45 days after a new version is published.
'Software auto-update' column in the device inventory table will indicate the phase assigned to the device. You can select the phase to quickly navigate to the Update section.
'Software auto-update' widget on device inventory pages shows any active updates that are going on and details for them.
Temporarily Pause (and Resume) auto-updates - under the Actions menu
- Selecting Pause stops all auto-updates for the tenants for 15 days. If an automatic update is already scheduled, it will be cancelled.
- If selected, the auto-updates are paused for all the Android-based devices in the tenant.
- Admin can also choose to resume the auto-updates before the 15 days elapse.
- Manual updates are not impacted by this.
Software versions released by Microsoft are marked as "Verified by Microsoft".
- Preview versions will be marked as 'Microsoft Preview'. Automatic updates do not update devices to these versions.
Refer to Update Microsoft Teams devices remotely for more details about auto-updates.
What you need to do to prepare:
Before this change takes effect, administrators should ensure that their devices are assigned the Update Phase of their choice. When this change takes effect, auto-updates will start happening following the configured update phases. In case you need to validate something on the devices, you can choose to pause the auto-updates temporarily.
MC679736 — (Updated) Microsoft Teams: Branded Meetings - Join Launcher Screen with Brand Image and Logo Support (Premium)
30-60 Days
Microsoft 365 Roadmap ID 164081
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
The Teams Join Launcher web page will now support the brand logo and brand image uploaded for branded meetings. This is a Teams Premium feature.
When this will happen:
Standard Release: We will begin rolling out early December 2023 (previously mid-November) and expect to complete by mid-December 2023 (previously late November).
What you need to do to prepare:
Please note - for tenants that have already uploaded and are using custom branded meetings, you may need to re-upload your images in order to support this new feature. Please see the Custom Meeting Branding support documentation for details.
MC679733 — Microsoft Teams Rooms on Windows- All-in-one experience
<30 Days
Microsoft 365 Roadmap ID 170740
With update 4.19 coming in November, Teams Rooms on Windows will support all-in-one and board device form factors, such as the Surface Hub 3.
When this will happen:
Standard Release: We will begin rolling out early November 2023 and expect to complete by late November 2023.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC678853 — (Updated) Microsoft Teams for VDI: New Microsoft Teams Desktop Client in Public Preview
Rolled Out
Updated November 2, 2023: We have updated the link to additional documentation. Thank you for your feedback.
VDI customers using Azure Virtual Desktops, Windows 365, Citrix and VMware can soon use the new Microsoft Teams client.
Optimized VDI users on the new Teams client will continue to enjoy the same feature set as in the classic Teams client, and more (like Channels 2.0).
The new desktop client has been redesigned from the ground up, focusing on better performance, simpler user experience and reduced resource consumption. With these pillars as a foundation, the new app adopts Fluent UI, transitions from Angular to React for building user interfaces, moves data processing out of the main thread to a client data layer worker, and lastly, replaces Electron to leverage WebView2 as the host.
The installer has also been redesigned as an MSIX package, with a new install folder location (C:\Program Files\WindowsApps) and new profile location (Appdata\Local\Packages\MSTeams_8wekyb3d8bbwe).
These improvements make the new Teams:
- More responsive (faster application launch time, faster meeting joins, faster chat and channel navigation and scrolling)
- Less resource intensive (reducing CPU, RAM and Storage on the virtual machine, allowing for higher user densities in VDI environments).
When this will happen:
Public Preview: We will begin rolling out in early October 2023 and expect to complete rollout by late October 2023.
How this will affect your organization:
In order to rollout the new Microsoft Teams client to your organization, you can either:
1) "Rip and Replace": uninstall the classic Teams client and install the new one (recommended method)
2) Install both apps 'side by side' and let the user switch between them by using the toggle on the top left of the UI. You can control who sees the toggle by configuring the Teams Admin Center policy "Teams update policy."
What you need to do to prepare:
Admin documentation and download link can be found here.
In order to support the new Microsoft Teams client, the following minimum VDI and OS software versions are required:
Windows Operative System for the virtual desktop:
- Windows 10.0.19041 or higher (single or multiuser)
- Windows Server 2019 (10.0.17763) -coming soon
- Windows Server 2022 (10.0.20348)
- Windows Server 2016 is NOT supported. Please plan upgrades.
AVD/W365:
- RD Client Windows 1.2.1755
- RD Client Mac 10.7.7
- WebRTC Redirector Service 1.1.2110.16001
Citrix:
- Workspace app Windows 2203 LTSR (and any CU), or 2302 CR
- Workspace app Linux 2207
- Workspace app Mac 2302
- Workspace app Chrome/HTML5 2301
- VDA 1912 CU6 or 2203 LTSR, or 2212 CR
RegKey to Add on VDAs:
HKLM\SOFTWARE\WOW6432Node\Citrix\WebSocketService
Key (Multi-SZ) : ProcessWhitelist
Value: msedgewebview2.exe
VMware:
- Horizon Agent 7.13.1, or 2103
MC678852 — (Updated) Out-of-box Controlled-content meeting template (Premium)
30-60 Days
Microsoft 365 Roadmap ID 91286
Updated October 26, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are launching an out-of-the box template for meetings with external participants. The controlled content access template has preset defaults for meeting options to provide tight controls over lobby bypass, who can present, allowing chat across meeting lifecycle/in-meeting, and who can record.
When this will happen:
Standard Release: We will begin rolling out in mid-October and complete by late October 2023.
GCC: We will begin rolling out early November and complete by mid-November 2023.
GCC High: We will begin rolling out mid-November 2023 (previously early October) and complete by late November 2023 (previously mid-October).
DoD: We will begin rolling out late November 2023 (previously mid-November) and complete by early December 2023 (previously late November).
How this will affect your organization:
The use of this out-of-box template is to remove the manual set-up needed for meeting with external participants. One can access this template by going to Teams Calendar > Schedule meeting > Controlled-content meeting template. This template is also available in Outlook. Please go to Teams Meeting drop down and select Controlled-content meeting template.
What you need to do to prepare:
Please share about this functionality with your users.
MC677231 — (Updated) Microsoft Teams: Engagement Information in Teams Attendance Report (Premium)
<30 Days
Microsoft 365 Roadmap ID 162171
Updated October 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
The new engagement information will enable organizers to view meeting engagement data such as total reactions, raised hands, cameras turned on, and more in the "Attendance" tab after a meeting or webinar.
When this will happen:
Targeted Release: We will begin rolling out in early October 2023 and expect to complete rollout by late October 2023 (previously mid-October).
Standard Release: We will begin rolling out in early November 2023 (previously late October) and expect to complete rollout by mid-November 2023 (previously early November).
How this will affect your organization:
If your tenant turns ON the Attendance Report, organizers will see engagement information in the "Attendance" tab in calendar or meeting chat. Information will include count of reactions, raised hands, unmutes and cameras turned on at meeting level and attendee level.
What you need to do to prepare:
If you need engagement information in Attendance Report, please make sure the "Attendance Report" policy is turned ON by both the admin and the organizer.
Note: If the end user opts out of the Attendance Report in Teams settings, then the user's engagement information will not be shown in the Attendance Report.
MC676296 — (Updated) Ratings and Reviews for Apps on Teams now Available
Rolled Out
Microsoft 365 Roadmap ID 122300
Updated October 16, 2023: We have determined that we will not be rolling this out to GCC organizations at this time. We will communicate via Message center when we are ready to proceed. We apologize for any inconvenience.
We are announcing the upcoming launch of the "Ratings and Reviews" feature for apps on Microsoft Teams. This new addition will empower users to view feedback from customers for apps from Microsoft and other third-party app publishers. Users can also provide feedback on apps they've installed, and by default these reviews will be marked as anonymous. Not only this, but app publishers will also have the capability to respond to these reviews via the Partner Center, thereby enabling a new mode of communication between partners and end users. Furthermore, this experience is powered by Microsoft AppSource's Ratings Service, hence ensuring the availability of reviews on the AppSource website as well as the Teams client experience. This feature is part of our continuous effort to enhance user experience and transparency within the Teams environment.
When this will happen:
Standard Release: We will begin rolling out in mid-October 2023 and expect to complete rolling out in late October 2023.
How this will affect your organization:
Users can now leverage customer sourced feedback for apps that they wish to install on Teams, thereby aiding their app discovery and installation experience.
What you need to do to prepare:
No action item is needed on behalf of the IT Admin for enabling this feature. This experience is controlled by the Optional Connected Experiences, and can be turned off by referring to this documentation.
MC675503 — (Updated) Meeting Protection Support and Improved View Switcher for Teams Rooms on Android
>60 Days
Updated November 2, 2023: We have updated the rollout timeline below as well as the content. Thank you for your patience.
The latest version of Teams Rooms on Android Update 3 (2023) includes the meeting protection support - End-to-end Encryption for meetings and Sensitivity labels.
When this will happen:
We will begin rolling out in mid-December 2023 (previously mid-November) and expect to complete rollout by mid-January 2024 (previously mid-December).
How this will affect your organization:
Teams Rooms on Android devices applies the Teams Premium meeting security features including end-to-end encryption and sensitivity labels if the meeting organizer has them turned ON.
Note: Features need to be activated through the Meeting options in Teams Calendar or Outlook on desktop or mobile devices. To enable the features a Teams premium license may be required.
If End-to-end Encryption is enabled, the Teams Rooms on Android will display a shield with a lock icon next to the view switcher. This icon includes a 20-digit group key that can be verified with other meeting participants. If a Teams meeting is set with a Sensitivity Label, room users will be informed that the label has been applied when clicking the shield with a lock icon.
Note: Together mode and Large Gallery are not available during End-to-end Encrypted Meetings, but meeting chat is permitted.
What you need to do to prepare:
Please notify your users about this new experience and update your training and documentation as appropriate.
MC675501 — (Updated) Microsoft Teams: Watermark support for recording playback (Premium)
>60 Days
Microsoft 365 Roadmap ID 137654
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Recording can now be enabled for watermarked meetings (Watermark feature requires a Teams Premium license). An email ID will be displayed as the watermark during the meeting recording playback. Once a meeting has concluded, users can access the recorded content on both web and mobile platforms to watch the recording with watermarking.
When this will happen:
- Targeted release: We will begin rolling out in early December 2023 and expect to complete by mid-December 2023.
- Standard release: We will begin rolling out in early January 2024 and expect to complete by mid-January 2024.
- GCC-H and DoD: We will begin rolling out in mid-February 2024 and expect to complete by late February 2024.
How this will affect your organization:
IT admins can now encourage meeting hosts to enable recording for watermarked meetings. The recording playback will be watermarked with the participants' email ID to avoid information leakage and add a layer of protection.
What you need to do to prepare:
You may need to update the documentation for your users to mention the existence of this feature.
- In a watermarked meeting, the meeting organizer and the co-organizer can now start recording by clicking on the "start recording" button.
- Once the meeting/recording has ended, participants can retrieve the link in the meeting chat and open the recording on the web.
- When the recording is opened on the web, they will see their individual email ID as the watermark on the meeting.
- When a meeting is recorded by the organizer, it will be saved onto their SharePoint and be able to download since they are the owner of the recording.
- The download option is only for the person who recorded the meeting (file owner). The owner can provide access to the other person.
- On the recording, it will add the email ID of the user who clicked on the recording file to watch the recording playback in the browser.
- The owner of the file will see their own email ID all over the recording.
- As a participant/other viewer of the file, if I watch the recording on the web, I would see my email ID all over the recording.
You can find more details about Watermark in Teams Premium in this documentation: Watermark for Teams meetings.
MC675498 — (Updated) Microsoft Teams: Extended Real-time Telemetry Retention Up To Seven Days
>60 Days
Microsoft 365 Roadmap ID 141108
Updated October 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
The Real-Time Analytics feature in the Teams admin center (TAC) allows IT admins to view their users' meetings and identify issues related to audio, video, content sharing, and network connectivity. As an admin, you can use this information to investigate and address any problems with the meeting experience while the meeting is ongoing.
In the current public preview, Real-time telemetry is only stored for users when administrators explicitly subscribe (go to user's meeting history and click on specific meeting) to it during ongoing meetings. This prevents admins from troubleshooting the issue if the meeting is already over and telemetry is not captured explicitly.
However, with this new update, Real-time telemetry will be captured and stored by default for all users with Teams premium licenses, even if admins do not explicitly subscribe to it in the Teams admin center.
When this will happen:
Rollout will begin in mid-January 2024 (previously late October 2023) and is expected to be complete by late January 2024 (previously mid-November 2023).
How this will affect your organization:
This feature is part of a Teams premium add-on SKU and only users with Teams premium licenses will have their Real-time telemetry stored for up to seven days.
What you need to do to prepare:
No action is required at this time from admins.
MC674737 — (Updated) Microsoft Teams: Emojis, GIFs and Stickers Unified in One Picker
>365 Days
Microsoft 365 Roadmap ID 84023
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can soon find all of their emojis, GIFs, and stickers in a combined picker in Microsoft Teams.
When this will happen:
Targeted Release: We will begin rolling out in late November 2023 (previously early November) and expect to complete rollout by early December 2023 (previously mid-November).
Standard Release: We will begin rolling out in late January 2023 (previously mid-November) and expect to complete rollout by early February 2023 (previously late November).
Gov Clouds: We will begin rolling out in mid-February (previously early December) and expect to complete rollout by late May 2024 (previously late January).
How this will affect your organization:
Users can find emojis, GIFs, and stickers combined in one menu under the smiley face icon. All the fun content will remain as normal for users to add in their messages.
What you need to do to prepare:
There is nothing you need to do to prepare.
MC674419 — (Updated) Retire Microsoft Teams Single-window UI in VDI for your organization
>60 Days
Updated October 20, 2023: We have updated the message to ensure visibility for all impacted organizations. The content below has not changed.
We will be retiring the Single Window UI feature from Microsoft Teams when optimized for VDI beginning January 31st 2024. Instead we recommend the utilization of Multi Window UI (also known as the new meeting experience), which is where we will continue to invest our development resources.
The Multi-window capability provides users with the option to pop out chats, meetings, calls, or documents into separate windows to help streamline their workflow while their call or meeting is in progress.
Accessing Teams and chats will be possible while keeping the popped-out call or meeting window visible - whether that's on the same screen as the main Teams client or on a secondary display.
It also brings new experiences to VDI such as ‘Call Me’, Background Blurring and Effects, Large Gallery, Together mode, Transcriptions and more.
Additionally, meeting and call controls such as mute, video, chat, leave, and more are now located at the top of the meeting window so that they are always available and never block the underlying content.
With Single-window, Microsoft Teams UI behaved like a ‘single pane of glass’, and if users tried to multi-task for example by clicking on a chat while there was a call in progress, this would trigger the appearance of a floating window in the UI (see picture below, bottom left).
In addition, the pre-join meeting experience would display the peripherals and audio options on the bottom, under the self-preview (see picture below, top left).
Once the user joins a meeting, the meeting and call controls bar is docked at the bottom/center of the UI (see picture below, middle left).
When this will happen:
January 31, 2024
How this will affect your organization:
You are receiving this message because our reporting indicates one or more users in your organization are using Single Window UI in Teams.
This mode is present when users are running old versions of the VDI stack, or the Teams client (older than 1.5.00.11865).
Minimum version requirement for Multi Window:
- Citrix:
- Citrix VDA 1912 CU6 LTSR
- Citrix VDA 2112 CR
- Citrix Workspace app for Windows 2203 CU1
- Linux and Mac 2209
- ChromeOS 2301
- VMware:
- VMware Horizon Agent 7.13.1 , or 2203
- Azure Virtual Desktops or Windows 365:
- RD Client Windows 1.2.1755
- RD Client Mac 10.7.7
- WebRTC Redirector Service 1.1.2110.16001
Recommended versions:
- Citrix: Latest Current Releases for Workspace app and VDA. Or latest CUs for LTSRs.
- VMware: Latest Horizon Agent
- AVD/W365: Latest RD Clients in Public release, and latest WebRTC Redirector Service.
Impact to users:
Users will no longer be able to use video or screensharing when they are using Microsoft Teams optimized for VDI when this change is implemented.
We'll be gradually rolling this deprecation out to customers in late January and complete this by January 31st 2024.
What you need to do to prepare:
To avoid work disruptions, we recommend you either:
- Update your VDI Infrastructure and Microsoft Teams versions to the minimum level supporting Multi-window
- Use Microsoft Teams in non-optimized mode (a.k.a server-side rendering, incurring higher VM resource consumption like CPU, RAM and Network traffic). For instructions on how to disable optimization, check your VDI Vendor’s documentation (AVD/W365, Citrix, VMware)
MC673714 — (Updated) Microsoft 365 admin center: New Premium Teams Usage Report
<30 Days
Microsoft 365 Roadmap ID 163426
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
A new product usage report will be available within Microsoft 365 admin center usage reports to help Admins understand how Microsoft Teams Premium is being used within their organization by daily active users, features, and by paid and trial license types.
Teams Premium usage reports will include daily active users, and three features in the first release: org-defined backgrounds, custom together mode, and live translation caption. Additional feature metrics coming in future iterations.
The report displays trends over the last 7/30/90/180 days, including a per-user view, and contains the user’s last active date and license information.
When this will happen:
Standard release. We will begin rolling out beginning late September 2023 (previously early September) with completion expected by mid-November (previously late October).
How this will affect your organization:
Admins with the correct permissions will soon have access to new usage reports for Teams Premium.
What you need to do to prepare:
To access the new reports, go to Reports -> Usage -> Teams Premium.
For more information regarding these reports, please review the following documentation.
MC673709 — (Updated) Microsoft Teams: New calendar views on Teams Rooms on Android
>60 Days
Microsoft 365 Roadmap ID 157123
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Teams Rooms on Android users will soon be able to get a refreshed look and feel of the room calendar along with expanded functionalities. The release of this calendar upgrade will be rolling out with Microsoft Teams Rooms on Android Update 3 2023. This feature enhancement will be available in all Teams Rooms licenses.
When this will happen:
Standard Release: We will begin rolling out in late January 2024 (previously early December) and will be completed by mid-February 2024 (previously mid-December).
Note: There can be a delay between when features are released by Microsoft and when they become available on a device model and make. You can reach out to your device manufacturer to confirm the exact timeline of when this app update will be available on your device.
How this will affect your organization:
Users can view the room calendar for the current and next day. There is a date separator to distinguish today vs. tomorrow's calendar items.
Like other Teams devices, a visual indicator in the form of green and purple vertical bar is added to each calendar slot so users can easily tell whether a room is booked or available at a glance. Any available 11-minute or more time slot is shown, allowing users who are searching for rooms in the office to easily determine whether a room can be used ad hoc.
Any meetings that are happening now or starting within the next 10 minutes are promoted to the top of the calendar as a focus tile with the same one touch join experience. Upcoming meetings that are happening later are shown as a non-focus tile, listed under the focus tile. Users can scroll trough the calendar to view the full list of room bookings and availabilities.
Users can tap anywhere on the non-focus tile to view the meeting details of upcoming meetings and access the Join button.
For better organization, when there are all day meetings scheduled, they are stacked together under the 'All day' page which can be accessed via the 'All day' bar found on top of the calendar. Non all day meetings remain on the first page of the calendar.
What you need to do to prepare:
Please plan on updating all Microsoft Teams Rooms on Android in your tenant to the latest version through the Teams Admin Center. Once devices are updated, you can notify your users about this change and update your training and documentation as appropriate.
MC662254 — (Updated) Microsoft Teams: Shared Device License on Mobile App for Android
Rolled Out
Microsoft 365 Roadmap ID 126706
Updated November 2, 2023: We are glad to announce that support for Teams Shared Device License on Android Mobile is generally available now on Teams mobile version >= 2023143401. Only Calls and Walkie Talkie apps are supported when the Android mobile app is signed into an account with Teams Shared Device license. To access other apps on Teams Android mobile including chats and channels, please assign eligible licenses to the account and remove the Teams Shared Device License.
Learn more on Set up an Android mobile phone as a common area phone - Microsoft Teams | Microsoft Learn
We are pleased to announce that we will soon support the Microsoft Teams Shared Device license on the Teams Android mobile application. The Teams Shared Device license offers a shared identity-based , common area phone experience, including basic and advanced calling, people search, voicemail and walkie talkie.
When this will happen:
- Standard Release: Rollout will begin in late August 2023 and is expected to be complete by early September 2023.
- GCC: Rollout will begin in late August 2023 and is expected to be complete by early September 2023.
How this will affect your organization:
This feature will enable Android phones to be set up as shared devices. Walkie Talkie, call queues, auto attendants, cloud voicemail, call park and all other calling features currently supported on common area phones will be available through the Teams Android app.
What you need to do to prepare:
We will share an update once we start rolling out the feature to all customers. Please ensure your Teams Android mobile application is updated with the latest version after the feature is released. No further action is required from your end currently. For more information, please visit this documentation.
MC662251 — (Updated) Configuration Change coming to Normalization rules (dial plan)
Rolled Out
Updated November 2, 2023: Based on customer feedback we will not be moving forward with this change at this time. You can safely disregard this message. Thank you for your feedback.
We're making some changes to dial-plan normalization rules.
Starting in October, we're stopping normalization on number that starts with plus sign (+).
Normalization in Microsoft Teams was not designed to do normalization when the phone number starts with plus sign (+) as documented, but we've never enforced this in the Teams desktop or Web client. We are planning to enforce this now and making this change to align with our Calling Service, other Teams services, Azure Communication Services SDKs, and other Microsoft services. Numbers that start with a plus sign (+) will not pass through any normalization rules.
How this will affect your organization:
You are receiving this message because our reporting indicates one or more users in your organization are using normalization rules that starts with a plus sign (+).
If you are relying on dial plan policies to translate numbers dialed starting with a +, those rules will no longer work. You will need to instruct your end users to either dial the correct number starting with a +, or dial numbers without a + to match dial plan policies.
What you need to do to prepare:
Prior to this change taking effect, you should ensure to review and modify normalization rules using plus sign (+), you should also notify your users about this change and update any relevant documentation as appropriate.
Please see Create and manage dial plans for more information.
MC649917 — (Updated) Microsoft Teams: Stream Preview and Playback in Teams Chat and Channels
<30 Days
Microsoft 365 Roadmap ID 127596
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can preview and play Stream videos directly in Teams Chat and Channel without having to open them in a browser and going to Stream.
When this will happen:
We will begin rolling out in late July 2023 and is expect to complete rollout by mid-November 2023 (previously late October 2023).
How this will affect your organization:
Stream videos that are saved in OneDrive and SharePoint are now embedded in chat and channels enabling users to preview and play them directly in Teams without the need to open a browser window.
What you need to do to prepare:
There is nothing required from you at this time. You may want to notify your users and update any relevant training documentation as appropriate.
MC642265 — (Updated) Cloud IntelliFrame: A New Way to See People in Teams Rooms
<30 Days
Microsoft 365 Roadmap ID 130219
Updated October 26, 2023: We have updated the rollout timeline below. Thank you for your patience.
Cloud IntelliFrame is a new experience that allows online meeting attendees to see people in Teams Rooms more clearly, enhancing the hybrid meeting experience by creating smart video feeds of in-room participants. The smart video feed is created by zooming into their faces and eliminating distractions. You can see the expressions and gestures of the people in the room more easily, which will help improve collaboration in hybrid meetings. It creates equity in hybrid meetings as everyone can be seen and heard.
Cloud IntelliFrame will be rolling out across Microsoft Teams Rooms on Windows with Pro license and can be viewed on Microsoft Teams Desktop (Windows & Mac) with any license.
When this will happen:
Standard Release and GCC: We will begin rolling out to commercial tenants in mid-August and expect to complete rollout by mid-November 2023 (previously mid-October).
GCC High will begin rollout by mid-November 2023 (previously mid-October).
How this will affect your organization:
All Microsoft Teams Rooms on Windows with a Pro license equipped with cameras in the supported camera list will automatically opt-in to Cloud IntelliFrame. Online participants on Microsoft Teams Desktop (Windows and Mac) will see the IntelliFrame video feed by default from Rooms with these cameras.
An icon on the top right of the Room video feed indicates that Cloud IntelliFrame is being displayed.
People in the Room can disable IntelliFrame by using in-meeting settings on the console. This turns off IntelliFrame and switches back to standard view for the Room. All online attendees would then see the standard view from the respective Room.
People on Teams Desktop can also toggle IntelliFrame on/off by right clicking on the Room video tile and selecting ‘Turn off IntelliFrame’. This switches off the IntelliFrame view just on their Teams client.
The following camera models when deployed in a Microsoft Teams Room on Windows with a Pro license will automatically use Cloud IntelliFrame:
- AVer CAM520 Pro
- AVer CAM520 Pro2
- BRIO 4K Stream Edition
- EagleEye Cube USB
- HD Pro Webcam C920
- Jabra PanaCast
- Logi Rally Camera
- Logitech BRIO
- Logitech ConferenceCam CC3000e
- Logitech MeetUp
- Logitech Webcam C925e
- Logitech Webcam C930e
- Microsoft® LifeCam Studio
- Polycom EagleEye IV USB Camera
- PTZ Pro 2
- PTZ Pro Camera
- ThinkSmart Cam
- Yealink UVC30
- Yealink UVC34
- Yealink UVC50
- Yealink UVC80
- Yealink UVC86
What you need to do to prepare:
You may want to notify your users about this capability. Cloud IntelliFrame shows the smart feed when there are 9 or less people in the room. It automatically switches between the standard room view and IntelliFrame view based on in-room activity. For example, if someone enters the meeting room, the view would automatically switch to standard room view until the individual settles down.
Cloud IntelliFrame is ideal for focus rooms and medium spaces. Large spaces may not be ideal as people furthest from the camera may appear blurry after digital zoom. You may also want to switch off Cloud IntelliFrame in Rooms with glass walls without any privacy filter.
To switch off Cloud IntelliFrame in a room:
- Follow this guide to create an XML configuration file
- Add the following element: <CloudIntelliFrame>False</CloudIntelliFrame>
- Restart the console to process the configuration changes.
MC617066 — (Updated) New Microsoft Teams rollout schedule, new controls, and direct deployment
Rolled Out
Updated October 16, 2023: Moving forward, please refer to the availability schedule here: The new Microsoft Teams desktop client.
The new Teams default app has started rolling out, and for more information, please visit Upgrade to the new Teams using policies.
Since March 2023, we have continued to add features such as third-party, line-of-business (LOB) applications, breakout rooms, and new scenarios such as multi-tenant organization (MTO) to the new Teams experience. Read MC533687 for details for our March announcement. Check The new Microsoft Teams (Preview) for details on upcoming features and support for Government Clouds and platforms such as Mac, VDI, and Web.
This announcement includes three upcoming changes for rolling out the new Microsoft Teams app:
Note: We will continue to honor the admin setting for UseNewTeamsClient under Teams update policies, where admins have already deployed the policy. This is to ensure administrators are fully empowered to manage the rollout of new Teams in a manner that’s right for them.
- We will begin displaying Try the new Teams toggle within the classic Microsoft Teams client where the admin policy setting of UseNewTeamsClient is set to Microsoft default value (Microsoft controlled in the Teams Admin Center (TAC) or Microsoft choice in PowerShell) based on our schedule details below.
- Administrators will be able to directly deploy the new Teams client to PCs in their organization.
- We will begin making new Teams as the default app for classic Teams users where the admin policy is set to Microsoft default (Microsoft controlled in TAC or Microsoft choice in PowerShell) based on our schedule details below. Administrators will be able to manage setting new Teams as the default app for their users.
When this will happen:
Starting mid-to late July 2023:
Microsoft will begin displaying the Try the new Teams toggle within the classic Microsoft Teams client starting in late July 2023. The planned rollout will be:
- Business plans (for example, Business Basic, Business Standard, Business Premium, and Teams Essentials (AAD), etc.): late July-early August 2023
- Enterprise plans (for example, E3, E5, F3, etc.): The new Microsoft Teams desktop client
- Note: Admins who have already deployed the policy to display the toggle or hide the toggle for their organizations will not see any change.
- Administrators can deploy the new Teams client directly to PCs in their organization starting mid-July 2023.
- Administrators can deploy a new setting value to make new Teams the default app for their users starting late July 2023
Starting September 2023:
Microsoft will start making the new Teams the default app starting in late September 2023. The planned rollout will be:
- Business plans (for example, Business Basic, Business Standard, Business Premium, and Teams Essentials (AAD), etc.): late September 2023
- Enterprise plans (for example, E3, E5, F3, etc.): The new Microsoft Teams desktop client
How this will affect your organization:
- Users will start seeing the Try the new Teams toggle in their classic Teams app. Organizations where admins have already deployed the policy to display the toggle or hide the toggle won’t see any changes.
- For bulk deployment, administrators will be able to safely deploy new Teams for their organization without needing to give admin privileges to the users. To learn more about this method, read our documentation here: Bulk deploy the new Microsoft Teams client.
- Administrators can also manage setting new Teams as the default app. To do this, administrators can manage "Use new Teams client" policy and configure "New Teams as default" for their users. To learn more, see our policy page here: Policy settings for deployment.
What you can do to prepare:
Review the resources and timeline and plan your organizations rollout plan for the new Microsoft Teams app.
MC602596 — (Updated) Microsoft Teams Panels Update
<30 Days
Microsoft 365 Roadmap ID 129366
Updated October 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
With this update, Teams Panels will support reserving a room using a QR code. This feature lets Microsoft Teams users book a room for meetings now, in the future, or add the room to an existing meeting by scanning a QR code on the scheduling panel and using the Teams app on their Android or iOS mobile phones.
All Teams Panels will have a QR code shown in the top left of the home screen. Panels users can either schedule a new meeting with the room pre-populated for them or easily see the room’s availability for their meetings and book the room with one click.
When this will happen:
Rollout is expected to begin in late August 2023 (previously early August) and is expected to be complete by mid-November 2023 (previously late October).
How this will affect your organization:
In order to access this feature, be sure to have the most up-to-date release of Teams Panels from Teams Admin Center, a Teams Rooms Pro or Teams Shared Devices license assigned to the account on the Panel, and check that your users have access to the latest version of the Teams app on their mobile phones.
Please note the following:
- External tenants are currently not able to use this feature.
- This feature will ship default "ON".
You can disable this feature on Teams Panels under Settings > Device settings > Teams Admin Settings > Meetings.
To reserve the room:
- Users need to scan the QR code using their mobile phone.
- In the Teams app on their mobile phone, users should select if they’d like to ‘Schedule a new meeting’ or ‘Reserve for existing meeting’.
- If the user schedules a new meeting, the room will be auto added as the location of the meeting. Users can then fill out the other meeting details.
- If the user selects to reserve the room for an existing meeting that is happening between now and midnight the next day, they will be able to see whether the room is available or booked at those times and can reserve with one click.
What you need to do to prepare:
To prepare for this incoming feature, we strongly recommend communicating this new feature to your users and share instructions if needed.
A recommended scanner for this feature is the mobile system/OS scanner on mobile phones. However, for Android, the scanning may not work if your users have both work and personal profiles on their Android phones. In this case, users will need to add mobile system/OS scanner in the work profile. To do that, follow the steps below:
- In Intune go to Apps -> Android and add
- Select Android enterprise system app
- Enter type of Android phone and Google and paste OS camera package name
- Assign to user / group of users
In order to use this feature, make sure Teams Panels is on 1449/1.0.97.2023080401. iOS mobile phones will need to be on 5.15.0 or higher, and Android mobile phones will need to be on 1416/1.0.0.2023153001 or higher.
For more information, please see: What's new in Microsoft Teams devices - Microsoft Support
MC600733 — (Updated) New Graph APIs for accessing Teams Meeting Recording
30-60 Days
Microsoft 365 Roadmap ID 95787
Updated October 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
New org-wide application permissions and RSC application permissions have been introduced to allow apps to access meeting recordings for a specific meeting. Resource specific consent (RSC) permissions, specifically enables admins to authorize users to provide consent to apps, so they get specific access to a Teams meeting’s recordings to which it is installed to, rather than providing them access across the entire tenant.
When this will happen:
Graph Beta We will begin rolling out in late August 2023 (previously late July) and expect to complete by mid-September 2023 (previously early August).
Standard Release: We will begin rollout in late November 2023 (previously mid-November) and expect to complete by late December 2023 (previously mid-December).
How this will affect your organization:
As a tenant admin, you will have separate org-wide application permissions to access meeting recordings across the organization. You can now switch to a more restrictive permission for apps to access only recordings. Alternatively, you could opt for a self-serve model wherein meeting organizers/presenters can authorize individual apps to access the recordings for specific meetings. This is possible via thew feature Resource-Specific Consent.
To enable the new meeting recordings-related org-wide application permissions:
You can review and accept org-wide application permissions for apps that require access to Teams meeting recordings in your organization through the Azure portal (Azure Active Directory > Enterprise applications > <App Name> > Permissions)
To enable the new meeting recordings-related meeting specific RSC application permissions:
As a tenant admin, you will have the ability to turn on/off resource-specific consent for apps in chats/meeting using a master switch. Once enabled, authorized users can now authorize a Teams app in a meeting, to access for that specific meeting using these permissions. More details can be found here.
What you need to do to prepare:
Org-wide Application permissions:
Review and accept permissions for apps that require access to Teams Meetings recordings in your organization (both app and delegated context) through the AAD portal through Enterprise Applications > App Name > Permissions.
Meeting specific RSC Application Permissions:
- Read this resource to understand how you can control whether you want to allow resource owners to grant RSC permission for apps in meetings directly.
- You can also view the list of RSC permissions for a Teams app in the Teams Admin Center (Team Apps ->Manage apps-> <App Name> -> Permissions tab).
Take into consideration whether to notify your users about this new capability and update your training and documentation as appropriate.
MC561186 — (Updated) Microsoft Teams: Block Meeting Chat Access in External, Non-Trusted Meeting Joins
<30 Days
Microsoft 365 Roadmap ID 123975
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Teams IT Admins will soon be able to block internal users from accessing chats when these users join meetings organized on external non-trusted tenants, including cross-cloud join. This release of Microsoft Teams' new meeting chat setting will be rolling out across MS Teams Desktop, Mobile and Web and will provide a new way for tenants to manage users' chat access in meetings hosted on external non-trusted tenants.
When will this happen:
Targeted Release: We will begin rollout in early July and expect to complete rollout by mid-July.
GA: We will begin rollout in mid-July and expect to complete rollout by late July.
GCC: We will begin rollout in early August and expect to complete rollout by mid-August.
GCCH: We will begin rollout in mid-August and expect to complete rollout by late August.
DoD: We will begin rollout in mid-September and expect to complete rollout by early November (previously late October).
How this will affect your organization:
IT Admins can modify this setting for internal users from the Teams Admin Center under External Meeting Chat or from PowerShell under AllowExternalNonTrustedMeetingChat. Internal users who have External Meeting Chat as OFF from the Admin Center or AllowExternalNonTrustedMeetingChat as False from the PowerShell will not have read or write chat access in meetings hosted on external non-trusted tenants on any Teams platforms.
What you need to do to prepare:
You may want to notify your users about this new setting and the potential effect on their chat access when joining external meetings.
MC554158 — (Updated) A new experience to search within chat and channels.
30-60 Days
Microsoft 365 Roadmap ID 122550
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are excited to introduce a new and improved experience to search within chats and channels.
When this will happen:
- Targeted release: We will begin rolling this out in mid-October 2023 and expect to complete rollout by late October 2023 (now completed)
- Standard release: We will begin rolling this out in mid-November 2023 and expect to complete rollout by late November 2023.
- GCC: We will begin rolling this out in mid- November 2023 and expect to complete rollout by late November 2023.
- GCC-H: We will begin rolling this out in early December 2023 and complete rollout by mid-December 2023.
- DoD: We will begin rolling this out in early December 2023 and complete rollout by mid-December 2023.
How this will affect your organization:
A few key enhancements include:
- The new in-chat and in-channel Search experience will now be available in the right handrail, making it possible to see your chat/channel list and your new search results in one single view. The initiation can be done using the keyboard shortcut Ctrl+F(win) or Cmd +F (Mac):
- Note: Search capability on the new Channels experience is currently available on the main view, and we will extend it to the conversation view very soon.
- In addition to the keyboard shortcut, a dedicated button ‘Find in Channel’, placed on the channel info pane can be used to initiate contextual search:
- We now have introduced enhanced captioning and keyword highlighting to aid the discernment of results in chat and channel:
- In-chat search will now also be available in pop-out chats.
What you need to do to prepare:
No preparation needed. The new search experience is set up by default, but you may want to draw attention to these new capabilities in Teams.
MC549348 — (Updated) Webinar Email feature updates -customize content and time to send reminders
30-60 Days
Microsoft 365 Roadmap ID 119391
Updated October 10, 2023: We have updated the rollout timeline below. Thank you for your patience.
Emails for Webinars are critical to engage with registrants and often organizers feel the need to customize the content. To enable this, we are rolling out two features.
- The content of the emails (i.e. all webinar related attendee emails) can be edited by the event organizers. This is reserved for Teams Premium licensed organizers.
- Time to send reminder emails can be configured by the event organizers. This is reserved for Teams Premium licensed organizers.
When this will happen:
Standard Release: rollout will start in mid-July and expected to be completed by end of July.
GCC: rollout will start in mid-November 2023 (previously mid-October) and expected to be completed by mid-December 2023 (previously late October).
How this will affect your organization:
Email customization is governed by IT admin policy to enable admins to restrict organizers with Teams Premium license from being able to edit the content of the emails. This setting is available in Teams Events policy. Set-CsTeamsEventsPolicy
What you need to do to prepare:
Both these features are reserved for users that have a Teams Premium license. The policy to customize content is enabled by default in commercial SKU.
MC546934 — (Updated) Microsoft Teams Rooms Licensing Policy Enforcement
Rolled Out
Updated October 10, 2023: We have updated this message to ensure visibility.
IMPORTANT! There are less than 30 days remaining before the Microsoft Teams Rooms licensing policy enforcement goes into effect. Please ensure all Microsoft Teams Rooms are properly licensed by September 30, 2023 to prevent any interruption in service.
Given the challenges that some of our customers are facing in migrating to the new licensing, we have elected to provide a 90-day grace period enforcement period that will begin on our July 1, 2023 enforcement date. We have made this decision with our commitment to customer satisfaction and seamless transition.
While we remain steadfast in our objective of ensuring a secure and compliant use of Microsoft Teams Rooms devices, we also acknowledge the need for adequate time to address migration issues. Therefore, we are granting additional time to allow you to complete your transitions smoothly.
We appreciate your understanding and flexibility as we navigate through these changes. Our aim remains to support you while ensuring adherence to our licensing policies. We are confident that this additional time will allow for a smoother transition, ultimately benefiting both our customers and our team.
Thank you for your unwavering commitment to our mission. Please feel free to reach out with any questions or concerns you may have.
Starting July 1, 2023, all Teams Rooms devices, including Microsoft Surface Hubs and Microsoft Teams Panels, using a user license will receive an error message and the device will fail to sign-in to the applicable service after the 90-day grace period expires on September 30, 2023. This means that if you have been using a user license (i.e., A, E, G) to enable your Microsoft Teams Rooms device, you will need to purchase and/or assign a new license. Please visit Microsoft Learn to understand more about the new Microsoft Teams Rooms Pro and Basic licensing options and how to update your user licenses.
When this will happen:
This policy enforcement will start on July 1, 2023. The 90-day grace period will end on September 30th, 2023.
How this will affect your organization:
Microsoft Teams Rooms, including Microsoft Surface Hubs and Microsoft Teams Panels, with a resource account that does NOT have one of the following licenses assigned will fail to sign-in after the 90-day grace period that starts on July 1, 2023 and ends on September 30, 2023.
- Teams Rooms Basic
- Teams Rooms Pro
- Teams Rooms Standard
- Teams Rooms Premium
- Teams Shared Device (Team Panels only)
Devices utilizing a resource account without the appropriate licensing will not have the ability to join meetings or access other features of Microsoft Team Rooms or Teams Panels.
What you need to do to prepare:
All Microsoft Teams Rooms resource accounts must have a valid Teams Rooms license assigned by July 1, 2023, to ensure no loss of service. Please visit Microsoft Learn for more information on Microsoft Teams Rooms licensing.
We recognize that updating licenses can be a time-consuming process for organizations. We've provided both a simple step-by-step process for checking small batches of devices and an automated script for checking licenses in bulk to help update your licenses to Pro or Basic, making the transition as smooth as possible.
To assist you further, we’ve produced a video on our Microsoft Helps YouTube channel. The video shows a step-by-step guide on how to audit your licenses and ensure that your Microsoft Teams Rooms devices continue to sign-in and run Teams meetings after the enforcement date. We highly recommend that you watch the video to learn more about the license update process and to make the transition as seamless as possible.
MC545913 — (Updated) We will stop honoring Caller ID policies using Service calling line ID substitution
<30 Days
Updated October 26, 2023: We have updated the rollout timeline below. Thank you for your patience.
This is the second phase of the retirement of using Service calling line ID substitution in Caller ID policies. The first phase was announced in MC505122 at the end of January 2023.
We will stop honoring the use of Service calling line ID substitution in Caller ID policies when outbound calls are made. We will also remove using Service calling line ID substitution from the Teams admin center and in the New/Set-CsCallingLineIdentity cmdlet in the Teams PowerShell Module.
Customers are required to use the Resource calling line ID substitution.
When this will happen:
The change will be rolling out in late September 2023 and expect to complete by mid-November 2023 (previously mid-October).
How this will affect your organization:
You are receiving this message because our reporting indicates that your organization are using Caller ID policies using Service calling line ID substitution.
When this change is implemented, Caller ID policies using Service calling line ID substitution will no longer be honored and the outbound call will not have any caller ID substitution. We will still honor other settings on a Caller ID policy using Service calling line ID substitution. We will also remove using Service calling line ID substitution from the Teams admin center and in the New/Set-CsCallingLineIdentity cmdlet in the Teams PowerShell Module.
Your administrators will need to use the Resource calling line ID substitution. This type of substitution uses the phone number of a resource account associated to an Auto Attendant or Call Queue and it supports both Calling Plan, Direct Routing and Operator Connect phone numbers.
What you need to do to prepare:
You should change any existing caller ID policies using Service calling line ID substitution to using Resource calling line ID substitution.
Please review the following resources:
MC536885 — (Updated) Changes in Normalization
TBD
Updated November 2, 2023: Based on customer feedback we will not be moving forward with this change at this time. You can safely disregard this message. Thank you for your feedback.
Stopping normalization on number that starts with plus sign (+)
Normalization in Microsoft Teams was not designed to do normalization when the phone number starts with plus sign (+) as documented, but we've never enforced this in the Teams desktop or Web client. We are planning to enforce this in the future but for now we recommend avoiding this pattern.
We are making this change to align with our Calling Service, other Teams services, Azure Communication Services SDKs, and other Microsoft services. Numbers that start with a plus sign (+) will not pass through any normalization rules.
Translated numbers that do not start with a plus sign (+), will pass through normalization rules more than once. Please see Create and manage dial plans for more information.
When this will happen:
We will not be moving forward with this change at this time.
How this will affect your organization:
There is no immediate impact. We are letting you know, so you can prepare for this change. If you are relying on dial plan policies to translate numbers dialed starting with a +, those rules will no longer work. You will need to instruct your end users to either dial the correct E.164 number starting with a +, or dial numbers without a + to match dial plan policies.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC496629 — (Updated) Changes coming to how dialed phone numbers are matched to users
30-60 Days
Updated November 2, 2023: We have updated the timing of this change below. Thank you for your patience.
Microsoft will be changing how numbers dialed by Teams users or arriving from the PSTN match the number assigned to users. This process is often referred to as Reverse Number Lookup (RNL).
The change applies to users with an assigned phone number with an extension using the following formats:
- Where the last several digits of the base number are also added as the extension. For example, +14025557334;ext=334, where 334 is both included in the base number and as the extension.
- Where both the base number and extension are unique for each user. For example, +14025557253;ext=3111 and +14025556567;ext=3112
- Where the base number is common, and the extension is unique for each user. For example, +14025557000;ext=111 and +14025557000;ext=112
The users configured with this type of phone number are either Teams users or Skype for Business Server on-premises users.
This may be a breaking change if your Teams dial plans and Direct Routing Session Border Controllers are not configured to convert dialed numbers into the full number assigned to the user including the extension.
When this will happen:
We will begin rolling out this change in mid-September (previously early July) and will be complete by mid-December 2023 (previously late October).
How this will affect your organization:
You might be impacted by the change, if you have users configured with phone numbers with extensions.
Today, when a call is made to a phone number, the lookup to see if that number is assigned to a specific user works as follows:
- if a call is made to +14025557334;ext=334, we will find the user configured with the phone number +14025557334;ext=334
- if a call is made to +14025557334, and there is no user configured with +14025557334, we will find the user configured with the phone number +14025557334;ext=334.
This can be an issue in situations where the same base number is used for multiple users. For example:
- User Alice is assigned +14025557000;ext=111
- User John is assigned +14025557000;ext=112
If a call is made to +14025557000, and there is no user configured with +14025557000, we would match to the first user found with +14025557000 as a base number (Alice in this case).
Based on customer feedback, we are changing the matching logic to be an exact string match between the called number and the full phone number configured for a user.
After the change, in the above examples, we will not find a user configured with the phone number +14025557334, +14025557253 or +14025557000 and calls to those number will not match to a user instead of potentially being routed to the wrong person.
What you need to do to prepare:
If you have users configured with phone numbers with the extensions, to prevent calls not being matched to the intended user, please ensure that dialed numbers from Teams users and incoming PSTN calls are formatted to exactly match the full phone number configured on the user accounts.
Check that your tenant dial plans include normalization rules that can translate abbreviated dial strings to the full phone number configured on users. In example above, the following phone number normalization rule will translate a dialed 3-digit number to the full phone number configured on the users to ensure calls will succeed:
- Pattern ^(\d{3})$ and Translation +14025557$1;ext=$1
Check that any phone number manipulation/translation rules used on your Direct Routing Session Border Controller are capable of making the translation to the full phone number configured on your users.
For more information, see:
MC487014 — (Updated) Changes coming to how dialed phone numbers are matched to users
30-60 Days
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft will be changing how numbers dialed by Teams users or arriving from the PSTN match the number assigned to users. This process is often referred to as Reverse Number Lookup (RNL).
The change applies to users with an assigned phone number with an extension using the following formats:
- Where the last several digits of the base number are also added as the extension. For example, +14025557334;ext=334, where 334 is both included in the base number and as the extension.
- Where both the base number and extension are unique for each user. For example, +14025557253;ext=3111 and +14025556567;ext=3112
- Where the base number is common, and the extension is unique for each user. For example, +14025557000;ext=111 and +14025557000;ext=112
You are receiving this post, because our telemetry shows that you have users configured with phone numbers containing extensions.
The users configured with this type of phone number are either Teams users or Skype for Business Server on-premises users.
This may be a breaking change if your Teams dial plans and Direct Routing Session Border Controllers are not configured to convert dialed numbers into the full number assigned to the user including the extension.
When this will happen:
We will begin rolling out this change in mid-September (previously early July) and will be complete by mid-December (previously late October).
How this will affect your organization:
Today, when a call is made to a phone number, the lookup to see if that number is assigned to a specific user works as follows:
- if a call is made to +14025557334;ext=334, we will find the user configured with the phone number +14025557334;ext=334
- if a call is made to +14025557334, and there is no user configured with +14025557334, we will find the user configured with the phone number +14025557334;ext=334.
This can be an issue in situations where the same base number is used for multiple users. For example:
- User Alice is assigned +14025557000;ext=111
- User John is assigned +14025557000;ext=112
If a call is made to +14025557000, and there is no user configured with +14025557000, we would match to the first user found with +14025557000 as a base number (Alice in this case).
Based on customer feedback, we are changing the matching logic to be an exact string match between the called number and the full phone number configured for a user.
After the change, in the above examples, we will not find a user configured with the phone number +14025557334, +14025557253 or +14025557000 and calls to those number will not match to a user instead of potentially being routed to the wrong person.
Since your tenant has configured users with phone numbers with the extension, your users might be impacted by the change.
What you need to do to prepare:
To prevent calls not being matched to the intended user, please ensure that dialed numbers from Teams users and incoming PSTN calls are formatted to exactly match the full phone number configured on the user accounts.
Check that your tenant dial plans include normalization rules that can translate abbreviated dial strings to the full phone number configured on users. In example above, the following phone number normalization rule will translate a dialed 3-digit number to the full phone number configured on the users to ensure calls will succeed:
- Pattern ^(\d{3})$ and Translation +14025557$1;ext=$1
Check that any phone number manipulation/translation rules used on your Direct Routing Session Border Controller are capable of making the translation to the full phone number configured on your users.
For more information, see:
MC400569 — (Updated) Graph API for Teams Meetings Transcripts
30-60 Days
Microsoft 365 Roadmap ID 95788
Updated October 10, 2023: We have updated the rollout timeline below. Thank you for your patience.
New org-wide application permissions and RSC application permissions have been introduced to make sure that apps can access meeting transcripts for a specific meeting. Resource specific consent (RSC) permissions, specifically enables admins to authorize users to provide consent to apps, so they get specific access to a Teams meeting’s transcripts to which it is installed to, rather than providing them access across the entire tenant.
This message is specifically associated with post-meeting transcripts access for apps - that allows authorized apps to access Teams Meetings transcripts once the meeting is over.
When will this happen?
We will begin rolling this out in early October 2023 (previously mid-August) and expect to complete late December 2023 (previously late October).
How will this affect your organization?
As a tenant admin, you now have separate org-wide application permissions to access meeting transcripts across the organization. You can now switch to a more restrictive permission for apps to access only transcripts. Alternatively, you could opt for a self-serve model wherein meeting organizers/presenters can authorize individual apps to access the transcripts for specific meetings. This is possible via the feature Resource-Specific Consent.
To enable the new meeting transcripts-related org-wide application permissions:
You can review and accept org-wide application permissions for apps that require access to Teams meeting transcripts in your organization through the Azure portal (Azure Active Directory > Enterprise applications > <App Name > Permissions)
To enable the new meeting transcripts-related meeting specific RSC application permissions:
As a tenant admin, you will have the ability to turn on/off resource-specific consent for apps in chats/meeting using a master switch. Once enabled, authorized users can now authorize a Teams app in a meeting, to access for that specific meeting using these permissions. More details can be found here.
What do you need to do to prepare?
Org-wide Application permissions:
Review and accept permissions for apps that require access to Teams Meetings transcripts in your organization (both app and delegated context) through the AAD portal through Enterprise Applications > App Name > Permissions.
Meeting specific RSC Application Permissions:
- Read this to understand how you can control whether you want to allow resource owners to grant RSC permission for apps in meetings directly.
- You can also view the list of RSC permissions for a Teams app in the Teams Admin Center (Team Apps ->Manage apps-> <App Name> -> Permissions tab).
- Take into consideration whether to notify your users about this new capability and update your training and documentation as appropriate.
Microsoft Intune
MC683915 — Update to the latest Intune App SDK and Intune App Wrapper for Android 14 support
Rolled Out
We have recently released new versions of the Intune App SDK and Intune App Wrapping Tool for Android to support Android 14. We recommend that you upgrade your app to the latest versions to ensure applications stay secure and run smoothly.
How this will affect your organization:
If you have applications using the Intune App SDK or Intune App Wrapping Tool for Android, you will need to update to the latest version to support Android 14.
What you need to do to prepare:
If you choose to build apps targeting Android API 34, you will need to adopt the new version of the Intune App SDK for Android (v10.0.0). If you’ve wrapped your app and are targeting API 34 you will need to use the new version of the App wrapper (v1.0.4191.6).
Note: As a reminder, while apps must update to SDK 10+ if targeting Android 14, apps do not need to update the SDK to simply run on Android 14.
You should also plan to update your documentation or developer guidance if applicable to include this change in support for the SDK.
Here are the public repositories:
MC683653 — (Updated) Plan for Change: Update your iOS/iPadOS Company Portal minimum version to v5.2311.1
<30 Days
Updated October 31, 2023: Please note we have updated the version from v5.2310.1 to v5.2311.1.
We will soon release an updated Company Portal for iOS/iPadOS (v5.2311.1) to the Apple Store that is a required app update. Starting on November 6, 2023, or soon after, the minimum supported version of the iOS/iPadOS Company Portal will change to v5.2311.1.
How this will affect your organization:
User impact: Most users have app updates set to automatic, so they receive the updated Company Portal app without taking any action. Users that have an earlier app version will be prompted to update to the latest Company Portal app.
Note: If you have enabled the ‘Block installing apps using App Store’ device restriction setting, you may need to manually push an update to devices.
What you need to do to prepare:
If you have enabled the above device restriction setting you will likely need to push an update to devices. Otherwise, no action is needed, but if you have a helpdesk, you may want to make them aware of the prompt to update the Company Portal app.
MC683035 — Accept Apple’s new terms and conditions to ensure Intune can communicate with Apple as expected
Rolled Out
On October 24, 2023, Apple will release new Terms and Conditions for Apple Business Manager. An IT admin will need to accept these terms when using Apple School Manager, Apple Business Manager, Apple Volume Purchasing Program, or Automated Device Enrollment to ensure that the managed devices can continue communicating with Microsoft Intune.
How this will affect your organization:
This will only affect you if you use Apple Automated Device Enrollment, Apple School Manager, Apple Business Manager, or Apple Volume Purchase Program. You will need to accept the new terms and conditions to ensure your Intune service is not interrupted. If you do not accept the new terms and conditions the Intune service will receive the error – “T_C_NOT_Signed” from Apple.
What you need to do to prepare:
Simply login to the appropriate URL listed in the support article from Apple here: https://support.apple.com/HT203063. Once you have logged in and accepted the new terms and conditions, managed Apple devices will once again be able to communicate with Apple’s device management servers.
MC681236 — Plan for Change: Field Service Mobile for iOS and Android will soon not be supported for Intune app protection policies
Rolled Out
Dynamics 365 deprecated Field Service Mobile in June 2022. The app is no longer available in the Google Play Store and will soon be removed from the Apple App store. With Intune’s November (2311) service release, Intune app protection policies (APP, also known as MAM) will no longer support Field Service Mobile.
How this will affect your organization:
If you are using APP for Field Service Mobile, we recommend enabling a Conditional Access (CA) policy to prevent users from accessing your organization’s resources through this app.
User impact: Once you have enabled the CA policy, users attempting to sign-in with their organization’s email will receive an error message.
What you need to do to prepare:
Update your documentation and notify your helpdesk as needed. We recommend creating an app-based CA policy with Grant access > Require app protection policy selected, to ensure only managed apps can access your organizations resources. For more information, see Use app-based Conditional Access policies with Intune.
Related information
Field Service Mobile Xamarin end of life
Microsoft Purview
MC686920 — Microsoft Purview Information Protection - Discover and co-author documents labeled with user-defined permissions
30-60 Days
Microsoft 365 Roadmap ID 109570
Coming soon SharePoint and OneDrive will support discovery and coauthoring of files labeled with user-defined permissions.
When this will happen:
This is currently rolling out and is expected to be complete by late November.
How this will affect your organization:
With this feature, SharePoint and OneDrive can process labeled documents that are encrypted with custom permissions, also referred to as user-defined permissions. As a result they can also be opened, edited, seamlessly co-authored, and support AutoSave in Word, Excel, and PowerPoint apps on all platforms (including Office for the web).
Note: Support for user search and eDiscovery is coming soon by December 2024.
What you need to do to prepare:
No special action is needed to enable this feature. However, as this changes existing behavior for files labeled with user-defined permissions, we recommend educating your users and updating documentation as needed.
Review and define label policies and settings, and access Microsoft Purview Information Protection, Data Loss Prevention, and eDiscovery solutions in the Microsoft Purview compliance portal.
Learn more:
MC686912 — Microsoft Purview Data Lifecycle Management: Upcoming retirement of SharePoint Online Record Center site features
>365 Days
Microsoft Purview Data Lifecycle Management and Microsoft Purview Records Management features offer organizations flexibility and a scalable solution to proactively retain or delete content in Microsoft 365.
We have a long-term retirement plan for the older features used for records management in SharePoint Online that are not part of the Microsoft Purview Records Management or Purview Data Lifecycle Management. The first set of features that will be retired are:
- Record Center site template, used to create a new Record Center site.
- Configure systems to submit files to a site using the Record Center programmable interface (commonly referred to as “send to” location).
- Content Organizer
For more information on the retirement plan that starts with removing support for new configurations of these features, please see: Use Microsoft Purview risk and compliance solutions instead of the older information management and ...
The retirement plan does not apply to features for SharePoint Server (On-Premises).
When this will happen:
Retirement of these features will start to happen at the start of January 2025.
Additional reminders will be shared leading up to this date.
How this will affect your organization:
This retirement may impact your organization if you are using any of these features or feature behaviors.
Retirement of these Record Center features includes these outcomes:
- Feature may no longer be supported by Microsoft support.
- It may no longer be visible in the user interface.
- Configurations may not be available through the user interface or programmatically, including enable and disable actions.
What you need to do to prepare:
Microsoft won't automatically migrate your older information management and SharePoint records management features in SharePoint Online. If you choose not to migrate to supported features, the older features may no longer be supported.
Between now and the full retirement date of the feature, you have the flexibility to migrate your scenarios on your own schedule. For more information on migration strategies and modern features to use instead, please see Migration strategies for moving to Microsoft Purview risk and compliance solutions from older inform... management and records management for SharePoint.
We recommend communicating this change to the team responsible for Data Lifecycle and Records Management and SharePoint records management at your organization.
MC686594 — Migration of Audit permissions from Exchange Admin Center to Purview Compliance portal
>60 Days
To search or export the audit log, administrators or members of investigation teams must be assigned to at least one of the View-Only Audit Logs or Audit Logs roles. These roles can currently be assigned either through the Microsoft Purview Compliance portal or through the Exchange Admin Center. Starting February 2, 2024, Microsoft is simplifying Audit permissions management by ensuring you can manage access to Audit in accordance with your other Purview permissions controls directly from the Microsoft Purview Compliance portal. The ability to manage Audit permissions from Exchange Admin Center will cease to be available starting February 2, 2024. We recommend that you start using the Purview Compliance portal to manage Audit permissions and familiarize yourselves with the new permission controls. To minimize impact to your organization, all existing Audit permissions currently assigned in the Exchange Admin Center will be automatically configured in the Purview Compliance portal on February 2, 2024.
You can learn more about the new permission controls at Set up Audit (Standard) in Microsoft 365 | Microsoft Learn.
When this will happen:
Starting February 2, 2024, Microsoft is simplifying Audit permissions management by ensuring you can manage access to Audit within the Microsoft Purview Compliance portal. Starting February 2, 2024, you will no longer be able to manage Audit permissions using the Exchange Admin Center. Any Audit permissions assigned through the Exchange Admin Center on or before February 1, 2024 (existing or new permissions) will be automatically replicated into the permissions tab of the Microsoft Purview Compliance portal on February 2, 2024.
How this will affect your organization:
We recommend that you use the Purview Compliance portal to manage Audit permissions. Starting February 2, 2024, you will no longer be able to manage Audit permissions through the Exchange Admin Center.
You can learn more about the new permission controls at Set up Audit (Standard) in Microsoft 365 | Microsoft Learn.
What you need to do to prepare:
We recommend that you start using the Microsoft Purview Compliance portal to manage Audit permissions and familiarize yourselves with the permissions controls within the Microsoft Purview Compliance portal. You can start to manually reconfigure Audit permissions using the Microsoft Purview Compliance portal right away to get familiar with the new permission controls. Any existing Audit permissions assigned through the Exchange Admin Center on or before February 2, 2024, will be automatically configured into the permissions tab of the Microsoft Purview Compliance portal on February 2, 2024. You do not need to take any action towards the replication of these permissions.
Learn more about audit-related role groups here: Set up Audit (Standard) in Microsoft 365 | Microsoft Learn
Microsoft Purview Audit enables customers to centrally visualize cloud log data generated across their enterprise, thus helping them effectively respond to security events, forensic investigations, internal investigations and compliance obligations. Thousands of user and admin operations performed in dozens of Microsoft 365 services and solutions are captured, recorded and retained in customers unified Microsoft Purview Audit logs.
Learn more:
MC686283 — eDiscovery (Premium) – Data sources usability enhancements
<30 Days
Microsoft 365 Roadmap ID 164896
Several usability improvements in the Data Sources page will be introduced in Microsoft Purview eDiscovery (Premium) including list view updates, improvements to hold status and error messaging, error reports and quick hold retry.
When this will happen:
Rollout will begin in mid-November 2023 and is expected to be complete by late November 2023.
How this will affect your organization:
The Data Sources list page will show the count of locations added to a custodial data location. Updated hold statuses include - applying hold, releasing hold, on hold, not on hold, partial hold with errors, partial hold released, hold failed, and release failed.
Location flyout will show details of locations where hold action failed, suggest remediation actions, provide ability to download the error report for custodial locations and retry hold action for failed data sources.
List of custodial locations will show in a separate page within the flyout and can be searched.
Validation errors that occur during Import custodians will show in a separate page within the custodian location flyout.
Note – The detailed hold error messaging is only available when new sources are placed on hold or when hold action is retried for existing sources. For older sources where hold failed, a generic error message will be shown. User can retrieve the detailed error message by performing ‘Retry hold action’ for the failed sources.
To learn more about upcoming user experience and usability changes to eDiscovery (Premium), see Microsoft 365 Roadmap | Microsoft 365
What you need to do to prepare:
If your training and documentation contain screenshots of the current views, you might want to update the content with the updated views and notify your users about these usability experience changes.
Learn more about Microsoft Purview eDiscovery solutions - Microsoft Purview (compliance) | Microsoft Docs.
MC686274 — Microsoft Purview Data Loss Prevention – Extend DLP controls with Microsoft Purview Extension for Firefox
<30 Days
Microsoft 365 Roadmap ID 138590
The Microsoft Purview Extension for Firefox will enable you to extend Microsoft Purview Data Loss Prevention (DLP) controls to Firefox browsers.
When this will happen:
Rollout will begin in early November and is expected to be complete by late November 2023.
How this will affect your organization:
With this update, DLP Admins will be able to set policies to prevent exfiltration of sensitive information through the Firefox browser by preventing actions such as:
- Copying data from a sensitive document to another document using the Clipboard.
- Printing a sensitive document.
- Copying to USB Removeable Media.
- Copying to Network Share.
What you need to do to prepare:
To use this preview feature, admins can configure a policy to identify Firefox as part of the policy scope.
Within the Microsoft Purview compliance portal, admins can also apply the Firefox App Event Filter to list Firefox related events for review and investigation.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Learn about data loss prevention
Learn about the Microsoft Purview extension for Firefox
MC686273 — Data Loss Prevention - Matched items in audit logs
<30 Days
Microsoft 365 Roadmap ID 164489
Coming soon to general availability is Microsoft Purview Data Loss Prevention (DLP) capability that will show you the cause of a flagged DLP policy violation. We’ve extended our support to show matched conditions across workloads (Exchange, Teams, SharePoint, OneDrive, Endpoint), rules, and conditions.
When this will happen:
Rollout will begin in mid-November and is expected to be complete by late-November.
How this will affect your organization:
When a DLP rule match occurs, the configured action for that rule (e.g., Block, Audit) is enforced.
To view this event in the DLP Alerts dashboard, click on the Events tab and select the entry you want to investigate. Click on Details to view the exact condition and its corresponding matched value.
You can also view this information in Activity Explorer. Click on DLP rule matched event to investigate. Scroll to the bottom of the panel to find ‘Other conditions matched’, which will show you the condition and respective matched value.
What you need to do to prepare:
Verify that auditing is enabled for your tenant and turn on advanced classification for Endpoint DLP. Refer to advanced classification scanning and protection.
Configure and view alerts for DLP policies.
MC685929 — Microsoft Purview to expand role groups
30-60 Days
Microsoft 365 Roadmap ID 184899
Microsoft Purview built-in role groups are being extended to prepare for upcoming features and capabilities relevant to those role groups. Additional roles will be added to Microsoft Purview built-in role groups for Compliance Administrator, Information Protection related role groups, and Privacy Management related role groups.
When this will happen:
Standard Release: We will begin rolling out in early November and complete by early December 2023.
How this will affect your organization:
This change will not have an impact on standard end users. Admins will see new roles within specific built-in role groups, these roles will enable them to manage additional data types in the future.
What you need to do to prepare:
This change will be automatic for built-in Microsoft Purview role groups for Compliance Administrator, Information Protection related role groups, and Privacy Management related role groups.
Microsoft Purview has several built-in role groups which contain roles to help admins perform common functions for Microsoft Purview: you are encouraged to regularly review and adjust your role group memberships if needed. Microsoft Purview supports custom role groups as well: If built-in role groups don’t meet the specific needs of your organization, you can create custom role group(s) in Microsoft Purview and populate it with the desired roles and group members.
MC684530 — New Contextual Conditions in Service Side Auto-labeling
<30 Days
Microsoft 365 Roadmap ID 117537
Microsoft Purview Information Protection has historically focused on content-based classification. Large advances in this area have occurred over the past few years, including accuracy improvements for sensitive information types and the addition of new classifiers like Exact Data Match, Entity Match, Credential Scan and Trainable Classifiers.
Although customers consider content-based classification to be critical to the detection of sensitive data, especially for regulatory compliance reasons, they also want to extend the ability to classify sensitive information based on contextual attributes.
When this will happen:
Rollout will begin in late October and is expected to be complete by early November.
How this will affect your organization:
We are adding in the following conditions/exceptions that can be used in auto-labeling policy:
- File Extension
- Document size equals or is greater than
- Document name contains words or phrases
- Document created by (OneDrive and SharePoint locations only)
- Document property is
These can be used as standalone conditions.
What you need to do to prepare:
Auto-labeling requires the tenant to enable sensitivity labels for Office files: https://learn.microsoft.com/purview/sensitivity-labels-sharepoint-onedrive-files?view=o365-worldwide
“Document property is” predicate requires additional configuration before the policy can be effective if used on OneDrive or SharePoint locations. Please refer to this DLP documentation: https://learn.microsoft.com/purview/protect-documents-that-have-fci-or-other-properties?view=o365-wo... to learn how to create a managed property to use for “Document property is”.
Review our public documentation on auto-labeling
To include PDFs in auto-labeling be sure to enable PDF labeling
Be on the lookout for updates to our playbook
Admin link: https://learn.microsoft.com/en-us/purview/apply-sensitivity-label-automatically
Other Links: https://learn.microsoft.com/purview/sensitivity-labels-sharepoint-onedrive-files?view=o365-worldwide
MC684214 — Information Protection- Auto labeling (for files at rest in SharePoint Online) can now label PDF files
Rolled Out
Microsoft 365 Roadmap ID 168865
You can now enable support of PDF labeling in SharePoint and OneDrive. Once enabled, you can start automatically applying labels to PDFs stored in SharePoint and OneDrive locations.
When this will happen:
This is currently rolling out and is expected to be complete by late October.
How this will affect your organization:
Once the changes are rolled out to your tenant, the following are the changes you can expect:
- Admins can turn on labeling of PDFs: Enable sensitivity labels for Office files | Microsoft Learn or via Microsoft Purview Information Protection overview PDF protection card.
- Once PDF support is enabled, you can apply labels to PDF files at rest in SharePoint using Autolabeling. Auto-labeling policies will need to be restarted in simulation to label PDFs at rest. Newly uploaded PDFs will get automatically labeled with existing policies. Learn more: Automatically apply a sensitivity label in Microsoft 365 - Microsoft Purview (compliance) | Microsoft Learn. If you wish to exclude PDFs from being labeled in existing or new auto-labeling policies once PDF sensitivity labeling is enabled for your organization, you have the option to use the exception condition of Except if “File extension is” for .pdf.
- The sensitivity column will start showing the label names for newly uploaded or labeled PDF files.
- End users can view protected PDFs in SharePoint and OneDrive will be supported in the following clients on
Desktop:
- Edge in the browser to view directly on SharePoint and OneDrive (user must be signed in)
- Adobe for downloaded files *
- FoxIt for downloaded files *
- NitroPDF *
- AIP viewer for downloaded files*
Mobile:
- AIP viewer
- FoxIt
* Note that using a PDF reader that requires download may conflict with DLP policies that prevent download of files
If you want to remove labels with encryption from PDFs, then you can use this cmdlet: Unlock-SPOSensitivityLabelEncryptedFile.
What you need to do to prepare:
- With this release you can expect more PDF files to be protected via sensitivity labels and encryption. You should prepare to train your users on methods to view protected PDFs both in browser and apps as described above.
- Note that this functionality is default turned OFF. If your organization is ready for consumption of sensitivity label encrypted PDF files, you can enable this functionality via SharePoint Admin PowerShell cmdlet:
- Set-SPOTenant -EnableSensitivityLabelforPDF $true
- To turn on support from the Microsoft Purview compliance portal, go to Information protection > Auto-labeling. If you see a message to Protect PDFs with Auto-labeling, click on the banner to confirm Turn on PDF protection for files in SharePoint and OneDrive. If you don't immediately see this message, try again in a few days, or use the PowerShell option.
- Please note that it may take around 15 minutes after this setting is enabled for labeling of PDFs to occur. Enabling this setting will enable all PDF labeling in SharePoint and OneDrive not just through automatic labeling.
MC683661 — Announcing GA of Admin units in Microsoft Purview Information Protection and Data Loss Prevention
<30 Days
Microsoft 365 Roadmap ID 165027
We’re rolling out a new capability in GCC, GCC-H, DoD that enables admins to delegate management and remediation authority for different people in different regions or organization units with role-based access control (RBAC) via Azure Active Directory Administrative Units. For example, German Admin Unit investigators would be able to investigate alerts and audit events for only German users.
When this will happen:
GCC, GCC-H, DoD GA rollout will begin in late October and is expected to be complete by mid-November 2023.
How this will affect your organization:
If you choose to not use this Admin Units feature, there is no impact to your organization. If your organization requires delegations of tasks based on users in specific regions or organization units, please follow the steps to set up this capability:
- Set up Administrative Units (AU) in Azure Portal
- Ring-fence Purview Admin Permissions to Administrative Unit scopes
- Create and manage Admin Unit scoped MIP/DLP policies
- Investigate user scoped DLP Alerts, Incidents, and Logs in Purview
- Investigate user scoped Activities and events in Activity Explorer
Note- This Admin Units capability will be extended to Data Loss Prevention alerts in the Microsoft 365 Defender portal and can be tracked as part of the roadmap ID here: 162292
What you need to do to prepare:
Get started with Information Protection and Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Permissions in the Microsoft Purview compliance portal
MC683657 — Information Protection - Configure labels independently on files and emails
<30 Days
Microsoft 365 Roadmap ID 124889
We're introducing a new capability to enable admins to scope sensitivity labels independently on files and emails.
When this will happen:
Standard Release: We will begin rolling out in U.S. Government clouds mid-November and expect to complete rolling out by the end of November.
How this will affect your organization:
With this update, admins can use the Microsoft Purview compliance portal to configure labels scoped to files or emails only.
What you need to do to prepare:
No action is needed to enable this feature.
Get started with Information Protection in the Microsoft Purview compliance portal.
Learn more: Get started with sensitivity labels
MC683656 — (Updated) Data Loss Prevention - Advanced classification scanning and protection for Endpoints running on Mac OS
<30 Days
Microsoft 365 Roadmap ID 162667
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Currently available in GA for Microsoft Purview Data Loss Prevention, we're introducing the ability for admins to extend Advanced classification support to macOS Endpoints for Government Clouds.
When this will happen:
This is currently rolling out and is expected to be completed by late November 2023 (previously late October).
How this will affect your organization:
With this capability, customers can extend enhanced protection to Endpoints running on Mac OS,
With classification techniques like fingerprinting, exact data matches, machine learning based Trainable Based Classifiers, and named entities in their DLP policies.
What you need to do to prepare:
As part of Endpoint DLP settings, Advanced Classification Scanning and Protection must be turned on for the tenant.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Configure endpoint DLP settings
MC683034 — Microsoft Purview: Moving from Audit Classic experience to New Search experience
<30 Days
In our ongoing efforts to enhance your search experience and provide you with the best possible service, we are replacing the Audit Classic Search with our improved Audit New Search feature, as customers have had since October 2022 to adopt the more robust experience. We want to ensure all affected customers are aware that the Classic Search experience will be retired and no longer accessible from the Compliance Portal starting in late November 2023. Customers are encouraged to adopt the new more robust experience now,
When this will happen:
November 30, 2023
How this will affect your organization:
This improved Audit search has been meticulously designed and engineered to be more efficient, powerful, and user-friendly, enabling you to find the information you need with even greater speed and accuracy. We have listened to your feedback and incorporated many of your suggestions into this updated search functionality. During this period, we encourage you to familiarize yourself with the new search and take advantage of its advanced capabilities.
What you can do to prepare:
You may consider updating your training and documentation as appropriate.
We appreciate your understanding and cooperation during this transitional period. Our goal is to continuously improve our services to better serve your needs, and we firmly believe that the new search will exceed your expectations.
For additional information on the Audit New Search feature, see: Audit New Search.
MC682085 — Microsoft Purview compliance portal: eDiscovery Premium – Guest reviewer
<30 Days
Microsoft 365 Roadmap ID 165487
We are releasing a feature that enables secure and convenient reviewer access to external collaborators to review sets within an eDiscovery (Premium) case. This feature empowers eDiscovery Premium admins and managers to follow more traditional collaboration practices that will boost confidence and workflow defensibility by allowing an outside expert to collaborate in-place to help reduce costs and risks associated with exporting a large amount of sensitive content to external parties.
When this will happen:
Rollout will begin in late October 2023 and is expected to be complete by mid-November 2023.
How this will affect your organization:
An eDiscovery Administrator can turn on the ability to allow guest access within eDiscovery from Premium settings.
Once this feature is turned on, eDiscovery Managers will be able to invite a Guest user to a specific eDiscovery case through Case settings > Access & permissions page.
An eDiscovery Administrator can then review and approve access to the Guest reviewer through the Premium Settings page.
On approval of access by the eDiscovery Administrator, the guest user will receive an email inviting them to access the case within eDiscovery (Premium). The guest must click on the link provided in the email to access the case.
What you need to do to prepare:
Assess if this feature will change your organization’s eDiscovery workflow. If so, provide training to all eDiscovery users in your organization and update relevant documentation if needed.
Ensure that the correct B2B external collaboration settings are in place to allow eDiscovery Administrator to approve a guest user.
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal.
Guest access in eDiscovery (Premium) | Microsoft Learn
MC682084 — Microsoft Purview Insider Risk Management: Public preview of administrative units support
30-60 Days
Microsoft 365 Roadmap ID 171717
Coming soon, Microsoft Purview Insider Risk Management will be rolling out public preview of administrative units support.
When this will happen:
Rollout will begin late November and is expected to be completed by late December 2023.
How this will affect your organization:
Administrative units allow admins with appropriate permissions to subdivide the organization into smaller units, and then assign specific admins or role groups that can manage only the members of those units. For example, German administrators can only create/manage policies for only German users, and German investigators can only investigate alerts and activities from only German users.
What you need to do to prepare:
Admins can configure administrative units in Azure by adding users and groups to new or existing administrative units. Admins can then assign these administrative units to solution admins or members of Insider Risk Management role groups from the permissions area of Microsoft Purview compliance portal. After the configuration, when these restricted administrators create or edit policies that support administrative units, they can select only the users in those administrative units as part of the policy.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can access the Insider Risk Management solution in the Microsoft Purview compliance portal.
Learn more: Permissions in the Microsoft Purview compliance portal | Microsoft Learn
MC681889 — Microsoft Purview eDiscovery (Premium): Identify, add and preserve Teams channels as non-custodial data locations
<30 Days
Microsoft 365 Roadmap ID 93270
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
eDiscovery (Premium) will have the capability to pick relevant Teams channels (standard, private, and shared) as non-custodial data locations. This will intelligently identify associated custodian/group mailboxes and SharePoint sites related to the channel.
When this will happen:
Rollout will begin in mid-November 2023 (previously late October) and is expected to be complete by late November 2023 (previously early November).
How this will affect your organization:
The ability to search for Teams and for select Teams channels to be added as non-custodial data sources will be available under the Data Sources > Add data locations > Teams option.
You can search for and add up to 10 Teams at a time. You can select the Standard, Shared and Private channels under each Team to add as a data source.
You can also select which associated locations you want to place on Hold.
eDiscovery users with the permissions to add locations in the Data sources page will be able to add mailboxes and sites associated with Teams channel (including standard, shared and private channels) as non-custodial data sources and preserve them.
What you need to do to prepare:
Assess if the changes will change your organization’s eDiscovery workflow. If so, update internal documentation. Provide training to all eDiscovery users in your organization and update relevant documentation if needed.
MC681880 — New connectors for Salesforce and Zoom coming to Microsoft Purview Compliance Manager
>60 Days
We're introducing new functionality to Microsoft Purview Compliance Manager to enable connectors for Salesforce and Zoom to enable increased visibility across your data estate.
Microsoft 365 Roadmap ID 124884
When this will happen:
Rollout will begin in mid-December 2023 and is expected to be complete by mid-January 2024.
How this will affect your organization:
Your current assessments will not be affected by this update. However, this update will allow you to add automated, resource-level testing across Salesforce, and Zoom to our existing Microsoft 365 assessments. This will help you assess your compliance posture more comprehensively across your data estate.
What you need to do to prepare:
To use the Microsoft Purview Compliance Manager integration with Microsoft Defender for Cloud, you will need to enable either the Foundational CSPM or Defender CSPM plan and assign the standards you wish to assess to your Azure subscriptions.
Get started with Compliance Manager in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Microsoft Purview Compliance Manager
MC680964 — Microsoft Purview Insider Risk Management: General availability of new sequence indicators
Rolled Out
Microsoft 365 Roadmap ID 168841
Coming soon, Microsoft Purview Insider Risk Management will be rolling out general availability of new sequence indicators.
When this will happen:
This feature is currently rolling out and is expected to be completed by late October 2023.
How this will affect your organization:
With this update, Insider Risk Management will provide new sequence indicators that start with activities on devices that may lead to a data security incident, including downgrading/removing file labels, archiving files, and downloading files from unallowed sites.
What you need to do to prepare:
You can opt in the new sequence indicators at insider risk settings > policy indicators.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can access the Insider Risk Management solution in the Microsoft Purview compliance portal.
MC675959 — Microsoft Information Protection: Microsoft Purview: Exact Data Match to support multi-token corroborative evidence.
30-60 Days
Microsoft 365 Roadmap ID 124847
Updated October 26, 2023: We have updated the rollout timeline below. Thank you for your patience.
Exact Data Match (EDM) will support string match detection of multi-token (i.e., fields with multiple words separated by spaces or punctuation) corroborative evidence without requiring mapping Sensitive Information Types (SITs) to multi-token corroborative evidence fields.
When this will happen:
Rollout will begin in mid-November 2023 (previously late October) and is expected to be complete by mid-December 2023 (previously mid-November).
How this will affect your organization:
With this release, multi-token corroborative evidence can be detected as a string match, without requiring it to be mapped to a Sensitive Information Type (SIT) that is able to detect that content as a single entity, which may result in more accurate EDM detection.
In some cases, it may still make sense to map a SIT to a corroborative evidence field, both to reduce latency by limiting the amount of content that needs to be compared for each match, and to eliminate some potential false positives. For example, if you have indicated multiple characters as ignored delimiters using configurable match, but still want to only detect matches on strings which are formatted with some of the delimiters or where multiple delimiters match each other.
In general, if a SIT can be accurately matched to a corroborative evidence column, it is preferred to do so rather than to rely on automatic single-word or multi-token matching.
What you need to do to prepare:
To use this feature, you need to opt-in for multi-token support for each corroborative evidence field that you want enabled. You can do this either through the new EDM UI experience (see screenshot above) or through a schema XML file update. Before doing so, you will need to first uninstall your current version of the EDM Upload Agent and download / install the latest version from: https://learn.microsoft.com/en-us/purview/sit-get-started-exact-data-match-hash-upload#links-to-edm-....
Once this feature has been released, additional details will be found in our EDM public documentation:
Learn about exact data match based sensitive information types | Microsoft Learn
MC672525 — (Updated) Microsoft Purview Compliance Portal: License Enforcement for Fingerprint-Based Sensitive Information Types
<30 Days
Microsoft 365 Roadmap ID 153080 and 164203
Updated November 2, 2023: We have updated the content with additional details. Thank you for your patience.
Document fingerprinting is a Microsoft Purview Data Loss Prevention (DLP) feature that converts a standard form into a sensitive information type (SIT), which you can use in the rules of your DLP policies.
To use Fingerprinting in your policies one of the below licenses is required:
- Microsoft 365 E5/A5/G5
- E5 Compliance
- Microsoft 365 E5/A5/G5 Information Protection and Governance
- Office 365 E5/A5/G5
You are receiving this message as a reminder to ensure your admins users who are covered with Data Loss Prevention have the required licenses before September 30, 2023. If you already have the license mentioned above, this message is not relevant to you, so please ignore.
Note: that these policies will be created by Microsoft Engineering and will appear as such in your audit logs. These policies are designed to not block any sensitive documents from being shared, they aim to only give admins the visibility to audit these activities in Activity Explorer. Further enforcement can then be taken by editing the policies. Should you choose to remove these policies after the Opt-Out period, simply disable or delete them from the DLP policies page.
When this will happen:
Current organizations with Microsoft 365 E3 and licenses assigned to their admins listed above can create fingerprinting-based sensitive information types and policies, but only for Exchange workloads.
In late November 2023 (previously late October), organizations will require one of the licenses listed above (or equivalent) to fully utilize all the features of fingerprinting.
How this will affect your organization:
If your admins do not have the required licenses post September 30, 2023, they will no longer be able to create, edit, or delete these existing fingerprint based sensitive information types and policies. Existing policies will still continue to function as they are today.
We recommend you assign the admins and users the appropriate licenses to continue to benefit from the feature set.
What you need to do to prepare:
Learn more about Document Fingerprinting here.
MC670437 — (Updated) New default Microsoft Purview Data Loss Prevention policies
<30 Days
Updated October 20, 2023: Please note that the 3 policies in the below (Financial Information, Healthcare Information, HR and Privacy Information) will be created but disabled and turned OFF by default. There is no change in the other 2 policies. Also, please note that Policy Tips will be turned OFF for all 5 policies. These policies are designed to not block any sensitive documents from being shared, they aim to only give admins the visibility to audit these activities in Activity Explorer. Further enhancements can then be taken by editing the policies. Should you choose to remove these policies after the Opt-Out period, simply disable or delete them from the DLP policies page.
We are creating default policies for Microsoft Purview Data Loss Prevention in your tenant to protect the most vulnerable sensitive information from accidental or malicious egress. The following default policies will be deployed along with the sensitive information they detect:
- Financial Information
- Healthcare Information
- HR and Privacy Information
- Source Code, Intellectual Property, and Trade Secrets
- Customer files
These changes are being made to your tenants as a precaution to help protect against potential data exfiltration.
When this will happen:
Timeline to opt-out: The rollout of the opt-out banner completed in late August. Once you see the banner, you will be able to opt-out until the 30 days is complete.
Timeline for Default policies: If opt-out is not selected, default policies will be rolled out in 30 days. The policies will be rolled out starting September 30th.
How this will affect your organization:
If you wish to opt-out of these policies, please visit your compliance portal and choose to opt out of the policies on the Policies page under Data Loss Prevention. The option to opt-out of these new default policies will be available for 30 days. After the roll out, these policies can be edited or deleted. For more information about editing a DLP policy see: Design a Data loss prevention policy | Microsoft Learn
What you need to do to prepare:
For more information about Microsoft Purview Data Loss Prevention please see:
MC669740 — (Updated) Microsoft Purview Information Protection Tracking and Revocation – End-User Tracking and Revocation
<30 Days
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
From the sensitivity menu, owners of Office files protected with a sensitivity label can access the Microsoft Purview compliance portal to view user access attempts and revoke access if needed.
When this will happen:
Preview: We have started rolling out and expect to complete by late August. - Complete
Registration will begin rolling out to production in mid-October 2023 (previously late August) and expect to complete by mid-November 2023 (previously late October).
Track & Revoke will begin rolling out to production will begin rolling out in late-October 2023 (previously late August) and expect to complete by mid-November 2023 (previously mid-September).
How this will affect your organization:
The Microsoft Purview Information Protection Tracking and Revocation feature will be turned on by default. To disable the feature, use the Disable-AipServiceDocumentTrackingFeature commandlet.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC668524 — (Updated) Microsoft Purview Information Protection: Tracking and Revocation in Compliance Portal
<30 Days
Microsoft 365 Roadmap ID 152126
Updated October 20, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can access the Microsoft Purview compliance portal to check who has tried accessing their sensitivity labeled and encrypted local Office files and revoke access when needed.
When this will happen:
Preview: We will begin rolling out late August 2023.
Standard Release: We will begin rolling out late October 2023 (previously early November) and expect to complete by late November 2023 (previously mid-November).
What you need to do to prepare:
The Microsoft Purview Information Protection Tracking and Revocation feature will be turned on by default. To disable the feature, use the Disable-AipServiceDocumentTrackingFeature commandlet.
MC667126 — (Updated) Microsoft Purview DLP Endpoint: Most restrictive actions across multiple policies GA
<30 Days
Updated October 10, 2023: We have updated the timing below. Thank you for your patience.
We're enhancing the enforcement engine in Microsoft Purview Endpoint DLP (part of the Microsoft Purview Data Loss Prevention suite) to refine the restrictions enabled when multiple rules are matched. Note: This change is specific to Endpoint DLP for Windows only. Changes for MacOS will roll out separately.
When this will happen:
Starting in late August, we're rolling this enhanced behavior, which will apply the most restrictive policy-defined actions across multiple policies triggered by a given event. We expect to complete by early November 2023 (previously early October).
How this will affect your organization:
You are receiving this message because your organization has licensing that entitles you to use Endpoint DLP.
Once this change is implemented, administrators may see an increase in Endpoint DLP alerts as more user activities are blocked by the more restrictive of multiple flagged policies.
Example: A user attempts to print a file containing both SSN & credit card numbers, triggering multiple policies. The SSN policy blocks users from printing, and the credit card policy blocks with override. The most restrictive policy (block) will be applied, ensuring there are no gaps in coverage.
What you need to do to prepare:
No action or policy reconfiguration is needed to enable this change.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Get started with Endpoint data loss prevention Data Loss Prevention policy reference.
MC663629 — (Updated) Microsoft Purview: General Availability of Microsoft Purview Insider Risk Management forensic evidence add-on
>60 Days
Microsoft 365 Roadmap ID 117565
Updated October 20, 2023: We have updated the timing of this change, below. Thank you for your patience.
Microsoft Purview Insider Risk Management forensic evidence add-on is an optional, additional capacity feature in Microsoft Purview Insider Risk Management that gives security teams visual insights into potential insider data security incidents, with user privacy built in.
Organizations with Microsoft 365 E5/G5, Microsoft 365 E5/G5 Compliance, or Microsoft 365 E5/G5 Insider Risk Management are eligible to purchase Insider Risk Management Forensic Evidence 100GB Add-on.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
When this will happen:
This new SKU, Insider Risk Management Forensic Evidence 100GB add-on, will be available starting mid-January 2024 (previously October 1, 2023).
What you need to do to prepare:
Starting September 1, 2023, organizations can purchase Insider Risk Management Forensic Evidence 100GB add-on.
MC660616 — (Updated) Microsoft Purview Information Protection: Require sensitivity label to restrict permissions
>60 Days
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users with access to Microsoft Information Protection (MIP) are redirected from old protection mechanisms towards the modern sensitivity labeling experience.
Microsoft 365 Roadmap ID 109532
When this will happen:
Preview: We will begin rolling out in mid-August 2023 (previously late July) and complete by early September 2023 (previously mid-August).
Standard Release: We will begin rolling out in late September 2023 (previously early September) and complete by early February 2024 (previously late October).
How this will affect your organization:
Users will no longer be able to apply IRM protection to new or existing documents and instead will be directed to apply MIP labels.
What you need to do to prepare:
Users with access to MIP that require the old IRM protection mechanisms will need to either need transition towards MIP labels or request a registry key capable of reverting to the old behavior.
MC609873 — Microsoft Purview Data Loss Prevention: Configure policy tips as pop-up dialog for emails with sensitivity labels
30-60 Days
Microsoft 365 Roadmap ID 139511
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Data Loss Prevention policies can be configured to display policy tips as a pop-up dialog for emails with sensitivity labels.
When this will happen:
Rollout will begin in early December 2023 (previously mid-October) and is expected to be complete by mid-December 2023 (previously mid-November).
How this will affect your organization:
Admins can configure DLP policies to show policy tips as a dialog to end users when they attempt to send email messages that include a sensitivity label on the email or attachment. With this capability, admins can set up rules to warn or block or request for an explicit acknowledgement or a business justification from users before sending emails. Furthermore, admins can customize a learn more URL in a DLP rule, ensuring that end users receive valuable guidance through the popup.
Note: Users included in these policies must hold E5/G5 or equivalent licenses.
What you need to do to prepare:
Configure policy tips for Data Loss Prevention in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- Learn how to configure a DLP rule with oversharing popups: Create and Deploy data loss prevention policies
- View the AIP migration playbook: Migrate Oversharing Popups from AIP
MC515536 — (Updated) Microsoft Purview | Data Lifecycle Management and Records Management – Microsoft Graph APIs for extensibility
<30 Days
Microsoft 365 Roadmap ID 88276
Updated October 10, 2023: We have updated the rollout timeline below. Thank you for your patience.
As a part of our extensibility vision and first release to Microsoft Graph, we are introducing three new APIs for retention labels, events, and event types in the Microsoft Graph beta environment. These APIs will enable you to customize and extend on what we have built in the product so far.
These APIs can be used by compliance admins and developers to manage retention labels in Data Lifecycle and Records Management solutions.
When this will happen:
Rollout will begin in late March 2023 (previously late February) and is expected to be complete by mid-November 2023 (previously mid-October).
How this will affect your organization:
If your organization needs to automate any operation related to retention labels or events, we recommend you achieve this by using the new Graph APIs instead of using PowerShell cmdlets. With Graph, we use REST APIs that support better security, extensibility, and app authentication features.
The three APIs are available under the security node and the endpoints to access them are as follows:
What you need to do to prepare:
Permissions
Currently, these APIs are supported through delegated permissions only, which are managed through the Graph interface. We are introducing two new permissions which you will need to access these APIs:
- recordsmanagement.read.all
- recordsmanagement.readwrite.all
Licensing
Access to Data Lifecycle Management and Records Management features varies based on your Microsoft 365 license level. See Microsoft 365 guidance for security & compliance - Service Descriptions for licensing requirement details.
Get started with Data Lifecycle Management and Records Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- Use the Microsoft Graph records management API
- Create retention labels for exceptions
- Start retention when an event occurs
Microsoft Defender
MC685930 — Microsoft Secure Score - New Microsoft Defender for Identity recommendations
30-60 Days
We’re updating Microsoft Secure Score improvement actions to ensure a more accurate representation of security posture.
The improvement actions listed below will be added to Microsoft Secure Score. Your score will be updated accordingly.
When this will happen:
This will begin rollout in mid-November 2023 and is expected to be complete by mid-December 2023.
How this will affect your organization:
The following new Microsoft Defender for Identity recommendations will be added as Microsoft Secure Score improvement actions:
- Prevent users to request a certificate valid for arbitrary users based on the certificate template (ESC1)
- Edit overly permissive Certificate Template with privileged EKU (Any purpose EKU or No EKU) (ESC2)
- Edit misconfigured enrollment agent certificate template (ESC3)
- Edit misconfigured certificate templates ACL (ESC4)
- Edit misconfigured certificate templates owner (ESC4)
- Edit vulnerable Certificate Authority setting (ESC6)
- Edit misconfigured Certificate Authority ACL (ESC7)
- Enforce encryption for RPC certificate enrollment interface (ESC8)
These are new security posture reports related to Active Directory Certificate Services (AD CS) that analyze the configurations of different AD CS components and guide remediation, if necessary.
What you need to do to prepare:
There's no action needed to prepare for this change, your score will be updated accordingly. Microsoft recommends reviewing the improvement actions listed in Microsoft Secure Score. We will continue to add suggested security improvement actions on an ongoing basis.
MC683044 — Retiring “MDE Settings” and “New version” options from Threat Explorer
30-60 Days
We will be retiring the “MDE Settings” and “New version” options from Threat Explorer as we work to clean up and streamline the user experience.
When this will happen:
We will be rolling out this change beginning in early November 2023 and expect to complete by late December 2023.
How this will affect your organization:
Users and Administrators will no longer see the “MDE Settings” and “New version” options from Threat Explorer, when this change is implemented.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
MC681893 — (Updated) Microsoft Secure Score - Changes in SSPM support
<30 Days
Updated October 26, 2023: We have updated the content below to show as intended. Thank you for your patience.
We’re updating Microsoft Secure Score improvement actions to ensure a more accurate representation of security posture.
The improvement actions listed below will be added to Microsoft Secure Score. Your score will be updated accordingly.
When this will happen:
This will begin rollout in mid-October 2023 and is expected to be complete by mid-November 2023.
How this will affect your organization:
The following new Microsoft Entra (AAD) recommendations will be added as Microsoft Secure Score improvement actions:
- Ensure 'Phishing-resistant MFA strength' is required for administrators.
- Ensure custom banned passwords lists are used.
The following new Microsoft Sway recommendations will be added as Microsoft Secure Score improvement actions:
- Ensure that Sways cannot be shared with people outside of your organization
The following new Atlassian recommendations will be added as Microsoft Secure Score improvement actions:
- Enable multi-factor authentication (MFA).
- Enable Single Sing On (SSO).
- Enable strong Password Policies.
- Enable session timeout for web users.
- Enable Password expiration policies.
- Atlassian mobile app security - Users that are affected by policies.
- Atlassian mobile app security - App data protection.
- Atlassian mobile app security - App access requirement.
The following new Zendesk recommendations will be added as Microsoft Secure Score improvement actions:
- Enable and adopt two-factor authentication (2FA).
- Send a notification on password change for admins, agents, and end users.
- Enable IP restrictions.
- Block customers to bypass IP restrictions.
- Admins and agents can use the Zendesk Support mobile app.
- Enable Zendesk authentication.
- Enable session timeout for users.
- Block account assumption.
- Block admins to set passwords.
The names, functionality and compliance conditions for Okta and DocuSign security recommendation were updated as Microsoft Secure Score improvement action.
The name of this control "Ensure Sign-in frequency is enabled and browser sessions are not persistent for Administrative users" is changed to "Ensure Sign-in frequency is enabled and browser sessions are not persistent for Administrative users".
What you need to do to prepare:
There's no action needed to prepare for this change, your score will be updated accordingly. Microsoft recommends reviewing the improvement actions listed in Microsoft Secure Score. We will continue to add suggested security improvement actions on an ongoing basis.
Microsoft Purview
MC686920 — Microsoft Purview Information Protection - Discover and co-author documents labeled with user-defined permissions
30-60 Days
Microsoft 365 Roadmap ID 109570
Coming soon SharePoint and OneDrive will support discovery and coauthoring of files labeled with user-defined permissions.
When this will happen:
This is currently rolling out and is expected to be complete by late November.
How this will affect your organization:
With this feature, SharePoint and OneDrive can process labeled documents that are encrypted with custom permissions, also referred to as user-defined permissions. As a result they can also be opened, edited, seamlessly co-authored, and support AutoSave in Word, Excel, and PowerPoint apps on all platforms (including Office for the web).
Note: Support for user search and eDiscovery is coming soon by December 2024.
What you need to do to prepare:
No special action is needed to enable this feature. However, as this changes existing behavior for files labeled with user-defined permissions, we recommend educating your users and updating documentation as needed.
Review and define label policies and settings, and access Microsoft Purview Information Protection, Data Loss Prevention, and eDiscovery solutions in the Microsoft Purview compliance portal.
Learn more:
MC686912 — Microsoft Purview Data Lifecycle Management: Upcoming retirement of SharePoint Online Record Center site features
>365 Days
Microsoft Purview Data Lifecycle Management and Microsoft Purview Records Management features offer organizations flexibility and a scalable solution to proactively retain or delete content in Microsoft 365.
We have a long-term retirement plan for the older features used for records management in SharePoint Online that are not part of the Microsoft Purview Records Management or Purview Data Lifecycle Management. The first set of features that will be retired are:
- Record Center site template, used to create a new Record Center site.
- Configure systems to submit files to a site using the Record Center programmable interface (commonly referred to as “send to” location).
- Content Organizer
For more information on the retirement plan that starts with removing support for new configurations of these features, please see: Use Microsoft Purview risk and compliance solutions instead of the older information management and ...
The retirement plan does not apply to features for SharePoint Server (On-Premises).
When this will happen:
Retirement of these features will start to happen at the start of January 2025.
Additional reminders will be shared leading up to this date.
How this will affect your organization:
This retirement may impact your organization if you are using any of these features or feature behaviors.
Retirement of these Record Center features includes these outcomes:
- Feature may no longer be supported by Microsoft support.
- It may no longer be visible in the user interface.
- Configurations may not be available through the user interface or programmatically, including enable and disable actions.
What you need to do to prepare:
Microsoft won't automatically migrate your older information management and SharePoint records management features in SharePoint Online. If you choose not to migrate to supported features, the older features may no longer be supported.
Between now and the full retirement date of the feature, you have the flexibility to migrate your scenarios on your own schedule. For more information on migration strategies and modern features to use instead, please see Migration strategies for moving to Microsoft Purview risk and compliance solutions from older inform... management and records management for SharePoint.
We recommend communicating this change to the team responsible for Data Lifecycle and Records Management and SharePoint records management at your organization.
MC686594 — Migration of Audit permissions from Exchange Admin Center to Purview Compliance portal
>60 Days
To search or export the audit log, administrators or members of investigation teams must be assigned to at least one of the View-Only Audit Logs or Audit Logs roles. These roles can currently be assigned either through the Microsoft Purview Compliance portal or through the Exchange Admin Center. Starting February 2, 2024, Microsoft is simplifying Audit permissions management by ensuring you can manage access to Audit in accordance with your other Purview permissions controls directly from the Microsoft Purview Compliance portal. The ability to manage Audit permissions from Exchange Admin Center will cease to be available starting February 2, 2024. We recommend that you start using the Purview Compliance portal to manage Audit permissions and familiarize yourselves with the new permission controls. To minimize impact to your organization, all existing Audit permissions currently assigned in the Exchange Admin Center will be automatically configured in the Purview Compliance portal on February 2, 2024.
You can learn more about the new permission controls at Set up Audit (Standard) in Microsoft 365 | Microsoft Learn.
When this will happen:
Starting February 2, 2024, Microsoft is simplifying Audit permissions management by ensuring you can manage access to Audit within the Microsoft Purview Compliance portal. Starting February 2, 2024, you will no longer be able to manage Audit permissions using the Exchange Admin Center. Any Audit permissions assigned through the Exchange Admin Center on or before February 1, 2024 (existing or new permissions) will be automatically replicated into the permissions tab of the Microsoft Purview Compliance portal on February 2, 2024.
How this will affect your organization:
We recommend that you use the Purview Compliance portal to manage Audit permissions. Starting February 2, 2024, you will no longer be able to manage Audit permissions through the Exchange Admin Center.
You can learn more about the new permission controls at Set up Audit (Standard) in Microsoft 365 | Microsoft Learn.
What you need to do to prepare:
We recommend that you start using the Microsoft Purview Compliance portal to manage Audit permissions and familiarize yourselves with the permissions controls within the Microsoft Purview Compliance portal. You can start to manually reconfigure Audit permissions using the Microsoft Purview Compliance portal right away to get familiar with the new permission controls. Any existing Audit permissions assigned through the Exchange Admin Center on or before February 2, 2024, will be automatically configured into the permissions tab of the Microsoft Purview Compliance portal on February 2, 2024. You do not need to take any action towards the replication of these permissions.
Learn more about audit-related role groups here: Set up Audit (Standard) in Microsoft 365 | Microsoft Learn
Microsoft Purview Audit enables customers to centrally visualize cloud log data generated across their enterprise, thus helping them effectively respond to security events, forensic investigations, internal investigations and compliance obligations. Thousands of user and admin operations performed in dozens of Microsoft 365 services and solutions are captured, recorded and retained in customers unified Microsoft Purview Audit logs.
Learn more:
MC686283 — eDiscovery (Premium) – Data sources usability enhancements
<30 Days
Microsoft 365 Roadmap ID 164896
Several usability improvements in the Data Sources page will be introduced in Microsoft Purview eDiscovery (Premium) including list view updates, improvements to hold status and error messaging, error reports and quick hold retry.
When this will happen:
Rollout will begin in mid-November 2023 and is expected to be complete by late November 2023.
How this will affect your organization:
The Data Sources list page will show the count of locations added to a custodial data location. Updated hold statuses include - applying hold, releasing hold, on hold, not on hold, partial hold with errors, partial hold released, hold failed, and release failed.
Location flyout will show details of locations where hold action failed, suggest remediation actions, provide ability to download the error report for custodial locations and retry hold action for failed data sources.
List of custodial locations will show in a separate page within the flyout and can be searched.
Validation errors that occur during Import custodians will show in a separate page within the custodian location flyout.
Note – The detailed hold error messaging is only available when new sources are placed on hold or when hold action is retried for existing sources. For older sources where hold failed, a generic error message will be shown. User can retrieve the detailed error message by performing ‘Retry hold action’ for the failed sources.
To learn more about upcoming user experience and usability changes to eDiscovery (Premium), see Microsoft 365 Roadmap | Microsoft 365
What you need to do to prepare:
If your training and documentation contain screenshots of the current views, you might want to update the content with the updated views and notify your users about these usability experience changes.
Learn more about Microsoft Purview eDiscovery solutions - Microsoft Purview (compliance) | Microsoft Docs.
MC686274 — Microsoft Purview Data Loss Prevention – Extend DLP controls with Microsoft Purview Extension for Firefox
<30 Days
Microsoft 365 Roadmap ID 138590
The Microsoft Purview Extension for Firefox will enable you to extend Microsoft Purview Data Loss Prevention (DLP) controls to Firefox browsers.
When this will happen:
Rollout will begin in early November and is expected to be complete by late November 2023.
How this will affect your organization:
With this update, DLP Admins will be able to set policies to prevent exfiltration of sensitive information through the Firefox browser by preventing actions such as:
- Copying data from a sensitive document to another document using the Clipboard.
- Printing a sensitive document.
- Copying to USB Removeable Media.
- Copying to Network Share.
What you need to do to prepare:
To use this preview feature, admins can configure a policy to identify Firefox as part of the policy scope.
Within the Microsoft Purview compliance portal, admins can also apply the Firefox App Event Filter to list Firefox related events for review and investigation.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Learn about data loss prevention
Learn about the Microsoft Purview extension for Firefox
MC686273 — Data Loss Prevention - Matched items in audit logs
<30 Days
Microsoft 365 Roadmap ID 164489
Coming soon to general availability is Microsoft Purview Data Loss Prevention (DLP) capability that will show you the cause of a flagged DLP policy violation. We’ve extended our support to show matched conditions across workloads (Exchange, Teams, SharePoint, OneDrive, Endpoint), rules, and conditions.
When this will happen:
Rollout will begin in mid-November and is expected to be complete by late-November.
How this will affect your organization:
When a DLP rule match occurs, the configured action for that rule (e.g., Block, Audit) is enforced.
To view this event in the DLP Alerts dashboard, click on the Events tab and select the entry you want to investigate. Click on Details to view the exact condition and its corresponding matched value.
You can also view this information in Activity Explorer. Click on DLP rule matched event to investigate. Scroll to the bottom of the panel to find ‘Other conditions matched’, which will show you the condition and respective matched value.
What you need to do to prepare:
Verify that auditing is enabled for your tenant and turn on advanced classification for Endpoint DLP. Refer to advanced classification scanning and protection.
Configure and view alerts for DLP policies.
MC685929 — Microsoft Purview to expand role groups
30-60 Days
Microsoft 365 Roadmap ID 184899
Microsoft Purview built-in role groups are being extended to prepare for upcoming features and capabilities relevant to those role groups. Additional roles will be added to Microsoft Purview built-in role groups for Compliance Administrator, Information Protection related role groups, and Privacy Management related role groups.
When this will happen:
Standard Release: We will begin rolling out in early November and complete by early December 2023.
How this will affect your organization:
This change will not have an impact on standard end users. Admins will see new roles within specific built-in role groups, these roles will enable them to manage additional data types in the future.
What you need to do to prepare:
This change will be automatic for built-in Microsoft Purview role groups for Compliance Administrator, Information Protection related role groups, and Privacy Management related role groups.
Microsoft Purview has several built-in role groups which contain roles to help admins perform common functions for Microsoft Purview: you are encouraged to regularly review and adjust your role group memberships if needed. Microsoft Purview supports custom role groups as well: If built-in role groups don’t meet the specific needs of your organization, you can create custom role group(s) in Microsoft Purview and populate it with the desired roles and group members.
MC684530 — New Contextual Conditions in Service Side Auto-labeling
<30 Days
Microsoft 365 Roadmap ID 117537
Microsoft Purview Information Protection has historically focused on content-based classification. Large advances in this area have occurred over the past few years, including accuracy improvements for sensitive information types and the addition of new classifiers like Exact Data Match, Entity Match, Credential Scan and Trainable Classifiers.
Although customers consider content-based classification to be critical to the detection of sensitive data, especially for regulatory compliance reasons, they also want to extend the ability to classify sensitive information based on contextual attributes.
When this will happen:
Rollout will begin in late October and is expected to be complete by early November.
How this will affect your organization:
We are adding in the following conditions/exceptions that can be used in auto-labeling policy:
- File Extension
- Document size equals or is greater than
- Document name contains words or phrases
- Document created by (OneDrive and SharePoint locations only)
- Document property is
These can be used as standalone conditions.
What you need to do to prepare:
Auto-labeling requires the tenant to enable sensitivity labels for Office files: https://learn.microsoft.com/purview/sensitivity-labels-sharepoint-onedrive-files?view=o365-worldwide
“Document property is” predicate requires additional configuration before the policy can be effective if used on OneDrive or SharePoint locations. Please refer to this DLP documentation: https://learn.microsoft.com/purview/protect-documents-that-have-fci-or-other-properties?view=o365-wo... to learn how to create a managed property to use for “Document property is”.
Review our public documentation on auto-labeling
To include PDFs in auto-labeling be sure to enable PDF labeling
Be on the lookout for updates to our playbook
Admin link: https://learn.microsoft.com/en-us/purview/apply-sensitivity-label-automatically
Other Links: https://learn.microsoft.com/purview/sensitivity-labels-sharepoint-onedrive-files?view=o365-worldwide
MC684214 — Information Protection- Auto labeling (for files at rest in SharePoint Online) can now label PDF files
Rolled Out
Microsoft 365 Roadmap ID 168865
You can now enable support of PDF labeling in SharePoint and OneDrive. Once enabled, you can start automatically applying labels to PDFs stored in SharePoint and OneDrive locations.
When this will happen:
This is currently rolling out and is expected to be complete by late October.
How this will affect your organization:
Once the changes are rolled out to your tenant, the following are the changes you can expect:
- Admins can turn on labeling of PDFs: Enable sensitivity labels for Office files | Microsoft Learn or via Microsoft Purview Information Protection overview PDF protection card.
- Once PDF support is enabled, you can apply labels to PDF files at rest in SharePoint using Autolabeling. Auto-labeling policies will need to be restarted in simulation to label PDFs at rest. Newly uploaded PDFs will get automatically labeled with existing policies. Learn more: Automatically apply a sensitivity label in Microsoft 365 - Microsoft Purview (compliance) | Microsoft Learn. If you wish to exclude PDFs from being labeled in existing or new auto-labeling policies once PDF sensitivity labeling is enabled for your organization, you have the option to use the exception condition of Except if “File extension is” for .pdf.
- The sensitivity column will start showing the label names for newly uploaded or labeled PDF files.
- End users can view protected PDFs in SharePoint and OneDrive will be supported in the following clients on
Desktop:
- Edge in the browser to view directly on SharePoint and OneDrive (user must be signed in)
- Adobe for downloaded files *
- FoxIt for downloaded files *
- NitroPDF *
- AIP viewer for downloaded files*
Mobile:
- AIP viewer
- FoxIt
* Note that using a PDF reader that requires download may conflict with DLP policies that prevent download of files
If you want to remove labels with encryption from PDFs, then you can use this cmdlet: Unlock-SPOSensitivityLabelEncryptedFile.
What you need to do to prepare:
- With this release you can expect more PDF files to be protected via sensitivity labels and encryption. You should prepare to train your users on methods to view protected PDFs both in browser and apps as described above.
- Note that this functionality is default turned OFF. If your organization is ready for consumption of sensitivity label encrypted PDF files, you can enable this functionality via SharePoint Admin PowerShell cmdlet:
- Set-SPOTenant -EnableSensitivityLabelforPDF $true
- To turn on support from the Microsoft Purview compliance portal, go to Information protection > Auto-labeling. If you see a message to Protect PDFs with Auto-labeling, click on the banner to confirm Turn on PDF protection for files in SharePoint and OneDrive. If you don't immediately see this message, try again in a few days, or use the PowerShell option.
- Please note that it may take around 15 minutes after this setting is enabled for labeling of PDFs to occur. Enabling this setting will enable all PDF labeling in SharePoint and OneDrive not just through automatic labeling.
MC683661 — Announcing GA of Admin units in Microsoft Purview Information Protection and Data Loss Prevention
<30 Days
Microsoft 365 Roadmap ID 165027
We’re rolling out a new capability in GCC, GCC-H, DoD that enables admins to delegate management and remediation authority for different people in different regions or organization units with role-based access control (RBAC) via Azure Active Directory Administrative Units. For example, German Admin Unit investigators would be able to investigate alerts and audit events for only German users.
When this will happen:
GCC, GCC-H, DoD GA rollout will begin in late October and is expected to be complete by mid-November 2023.
How this will affect your organization:
If you choose to not use this Admin Units feature, there is no impact to your organization. If your organization requires delegations of tasks based on users in specific regions or organization units, please follow the steps to set up this capability:
- Set up Administrative Units (AU) in Azure Portal
- Ring-fence Purview Admin Permissions to Administrative Unit scopes
- Create and manage Admin Unit scoped MIP/DLP policies
- Investigate user scoped DLP Alerts, Incidents, and Logs in Purview
- Investigate user scoped Activities and events in Activity Explorer
Note- This Admin Units capability will be extended to Data Loss Prevention alerts in the Microsoft 365 Defender portal and can be tracked as part of the roadmap ID here: 162292
What you need to do to prepare:
Get started with Information Protection and Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Permissions in the Microsoft Purview compliance portal
MC683657 — Information Protection - Configure labels independently on files and emails
<30 Days
Microsoft 365 Roadmap ID 124889
We're introducing a new capability to enable admins to scope sensitivity labels independently on files and emails.
When this will happen:
Standard Release: We will begin rolling out in U.S. Government clouds mid-November and expect to complete rolling out by the end of November.
How this will affect your organization:
With this update, admins can use the Microsoft Purview compliance portal to configure labels scoped to files or emails only.
What you need to do to prepare:
No action is needed to enable this feature.
Get started with Information Protection in the Microsoft Purview compliance portal.
Learn more: Get started with sensitivity labels
MC683656 — (Updated) Data Loss Prevention - Advanced classification scanning and protection for Endpoints running on Mac OS
<30 Days
Microsoft 365 Roadmap ID 162667
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Currently available in GA for Microsoft Purview Data Loss Prevention, we're introducing the ability for admins to extend Advanced classification support to macOS Endpoints for Government Clouds.
When this will happen:
This is currently rolling out and is expected to be completed by late November 2023 (previously late October).
How this will affect your organization:
With this capability, customers can extend enhanced protection to Endpoints running on Mac OS,
With classification techniques like fingerprinting, exact data matches, machine learning based Trainable Based Classifiers, and named entities in their DLP policies.
What you need to do to prepare:
As part of Endpoint DLP settings, Advanced Classification Scanning and Protection must be turned on for the tenant.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Configure endpoint DLP settings
MC683034 — Microsoft Purview: Moving from Audit Classic experience to New Search experience
<30 Days
In our ongoing efforts to enhance your search experience and provide you with the best possible service, we are replacing the Audit Classic Search with our improved Audit New Search feature, as customers have had since October 2022 to adopt the more robust experience. We want to ensure all affected customers are aware that the Classic Search experience will be retired and no longer accessible from the Compliance Portal starting in late November 2023. Customers are encouraged to adopt the new more robust experience now,
When this will happen:
November 30, 2023
How this will affect your organization:
This improved Audit search has been meticulously designed and engineered to be more efficient, powerful, and user-friendly, enabling you to find the information you need with even greater speed and accuracy. We have listened to your feedback and incorporated many of your suggestions into this updated search functionality. During this period, we encourage you to familiarize yourself with the new search and take advantage of its advanced capabilities.
What you can do to prepare:
You may consider updating your training and documentation as appropriate.
We appreciate your understanding and cooperation during this transitional period. Our goal is to continuously improve our services to better serve your needs, and we firmly believe that the new search will exceed your expectations.
For additional information on the Audit New Search feature, see: Audit New Search.
MC682085 — Microsoft Purview compliance portal: eDiscovery Premium – Guest reviewer
<30 Days
Microsoft 365 Roadmap ID 165487
We are releasing a feature that enables secure and convenient reviewer access to external collaborators to review sets within an eDiscovery (Premium) case. This feature empowers eDiscovery Premium admins and managers to follow more traditional collaboration practices that will boost confidence and workflow defensibility by allowing an outside expert to collaborate in-place to help reduce costs and risks associated with exporting a large amount of sensitive content to external parties.
When this will happen:
Rollout will begin in late October 2023 and is expected to be complete by mid-November 2023.
How this will affect your organization:
An eDiscovery Administrator can turn on the ability to allow guest access within eDiscovery from Premium settings.
Once this feature is turned on, eDiscovery Managers will be able to invite a Guest user to a specific eDiscovery case through Case settings > Access & permissions page.
An eDiscovery Administrator can then review and approve access to the Guest reviewer through the Premium Settings page.
On approval of access by the eDiscovery Administrator, the guest user will receive an email inviting them to access the case within eDiscovery (Premium). The guest must click on the link provided in the email to access the case.
What you need to do to prepare:
Assess if this feature will change your organization’s eDiscovery workflow. If so, provide training to all eDiscovery users in your organization and update relevant documentation if needed.
Ensure that the correct B2B external collaboration settings are in place to allow eDiscovery Administrator to approve a guest user.
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal.
Guest access in eDiscovery (Premium) | Microsoft Learn
MC682084 — Microsoft Purview Insider Risk Management: Public preview of administrative units support
30-60 Days
Microsoft 365 Roadmap ID 171717
Coming soon, Microsoft Purview Insider Risk Management will be rolling out public preview of administrative units support.
When this will happen:
Rollout will begin late November and is expected to be completed by late December 2023.
How this will affect your organization:
Administrative units allow admins with appropriate permissions to subdivide the organization into smaller units, and then assign specific admins or role groups that can manage only the members of those units. For example, German administrators can only create/manage policies for only German users, and German investigators can only investigate alerts and activities from only German users.
What you need to do to prepare:
Admins can configure administrative units in Azure by adding users and groups to new or existing administrative units. Admins can then assign these administrative units to solution admins or members of Insider Risk Management role groups from the permissions area of Microsoft Purview compliance portal. After the configuration, when these restricted administrators create or edit policies that support administrative units, they can select only the users in those administrative units as part of the policy.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can access the Insider Risk Management solution in the Microsoft Purview compliance portal.
Learn more: Permissions in the Microsoft Purview compliance portal | Microsoft Learn
MC681889 — Microsoft Purview eDiscovery (Premium): Identify, add and preserve Teams channels as non-custodial data locations
<30 Days
Microsoft 365 Roadmap ID 93270
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
eDiscovery (Premium) will have the capability to pick relevant Teams channels (standard, private, and shared) as non-custodial data locations. This will intelligently identify associated custodian/group mailboxes and SharePoint sites related to the channel.
When this will happen:
Rollout will begin in mid-November 2023 (previously late October) and is expected to be complete by late November 2023 (previously early November).
How this will affect your organization:
The ability to search for Teams and for select Teams channels to be added as non-custodial data sources will be available under the Data Sources > Add data locations > Teams option.
You can search for and add up to 10 Teams at a time. You can select the Standard, Shared and Private channels under each Team to add as a data source.
You can also select which associated locations you want to place on Hold.
eDiscovery users with the permissions to add locations in the Data sources page will be able to add mailboxes and sites associated with Teams channel (including standard, shared and private channels) as non-custodial data sources and preserve them.
What you need to do to prepare:
Assess if the changes will change your organization’s eDiscovery workflow. If so, update internal documentation. Provide training to all eDiscovery users in your organization and update relevant documentation if needed.
MC681880 — New connectors for Salesforce and Zoom coming to Microsoft Purview Compliance Manager
>60 Days
We're introducing new functionality to Microsoft Purview Compliance Manager to enable connectors for Salesforce and Zoom to enable increased visibility across your data estate.
Microsoft 365 Roadmap ID 124884
When this will happen:
Rollout will begin in mid-December 2023 and is expected to be complete by mid-January 2024.
How this will affect your organization:
Your current assessments will not be affected by this update. However, this update will allow you to add automated, resource-level testing across Salesforce, and Zoom to our existing Microsoft 365 assessments. This will help you assess your compliance posture more comprehensively across your data estate.
What you need to do to prepare:
To use the Microsoft Purview Compliance Manager integration with Microsoft Defender for Cloud, you will need to enable either the Foundational CSPM or Defender CSPM plan and assign the standards you wish to assess to your Azure subscriptions.
Get started with Compliance Manager in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Microsoft Purview Compliance Manager
MC680964 — Microsoft Purview Insider Risk Management: General availability of new sequence indicators
Rolled Out
Microsoft 365 Roadmap ID 168841
Coming soon, Microsoft Purview Insider Risk Management will be rolling out general availability of new sequence indicators.
When this will happen:
This feature is currently rolling out and is expected to be completed by late October 2023.
How this will affect your organization:
With this update, Insider Risk Management will provide new sequence indicators that start with activities on devices that may lead to a data security incident, including downgrading/removing file labels, archiving files, and downloading files from unallowed sites.
What you need to do to prepare:
You can opt in the new sequence indicators at insider risk settings > policy indicators.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can access the Insider Risk Management solution in the Microsoft Purview compliance portal.
MC675959 — Microsoft Information Protection: Microsoft Purview: Exact Data Match to support multi-token corroborative evidence.
30-60 Days
Microsoft 365 Roadmap ID 124847
Updated October 26, 2023: We have updated the rollout timeline below. Thank you for your patience.
Exact Data Match (EDM) will support string match detection of multi-token (i.e., fields with multiple words separated by spaces or punctuation) corroborative evidence without requiring mapping Sensitive Information Types (SITs) to multi-token corroborative evidence fields.
When this will happen:
Rollout will begin in mid-November 2023 (previously late October) and is expected to be complete by mid-December 2023 (previously mid-November).
How this will affect your organization:
With this release, multi-token corroborative evidence can be detected as a string match, without requiring it to be mapped to a Sensitive Information Type (SIT) that is able to detect that content as a single entity, which may result in more accurate EDM detection.
In some cases, it may still make sense to map a SIT to a corroborative evidence field, both to reduce latency by limiting the amount of content that needs to be compared for each match, and to eliminate some potential false positives. For example, if you have indicated multiple characters as ignored delimiters using configurable match, but still want to only detect matches on strings which are formatted with some of the delimiters or where multiple delimiters match each other.
In general, if a SIT can be accurately matched to a corroborative evidence column, it is preferred to do so rather than to rely on automatic single-word or multi-token matching.
What you need to do to prepare:
To use this feature, you need to opt-in for multi-token support for each corroborative evidence field that you want enabled. You can do this either through the new EDM UI experience (see screenshot above) or through a schema XML file update. Before doing so, you will need to first uninstall your current version of the EDM Upload Agent and download / install the latest version from: https://learn.microsoft.com/en-us/purview/sit-get-started-exact-data-match-hash-upload#links-to-edm-....
Once this feature has been released, additional details will be found in our EDM public documentation:
Learn about exact data match based sensitive information types | Microsoft Learn
MC672525 — (Updated) Microsoft Purview Compliance Portal: License Enforcement for Fingerprint-Based Sensitive Information Types
<30 Days
Microsoft 365 Roadmap ID 153080 and 164203
Updated November 2, 2023: We have updated the content with additional details. Thank you for your patience.
Document fingerprinting is a Microsoft Purview Data Loss Prevention (DLP) feature that converts a standard form into a sensitive information type (SIT), which you can use in the rules of your DLP policies.
To use Fingerprinting in your policies one of the below licenses is required:
- Microsoft 365 E5/A5/G5
- E5 Compliance
- Microsoft 365 E5/A5/G5 Information Protection and Governance
- Office 365 E5/A5/G5
You are receiving this message as a reminder to ensure your admins users who are covered with Data Loss Prevention have the required licenses before September 30, 2023. If you already have the license mentioned above, this message is not relevant to you, so please ignore.
Note: that these policies will be created by Microsoft Engineering and will appear as such in your audit logs. These policies are designed to not block any sensitive documents from being shared, they aim to only give admins the visibility to audit these activities in Activity Explorer. Further enforcement can then be taken by editing the policies. Should you choose to remove these policies after the Opt-Out period, simply disable or delete them from the DLP policies page.
When this will happen:
Current organizations with Microsoft 365 E3 and licenses assigned to their admins listed above can create fingerprinting-based sensitive information types and policies, but only for Exchange workloads.
In late November 2023 (previously late October), organizations will require one of the licenses listed above (or equivalent) to fully utilize all the features of fingerprinting.
How this will affect your organization:
If your admins do not have the required licenses post September 30, 2023, they will no longer be able to create, edit, or delete these existing fingerprint based sensitive information types and policies. Existing policies will still continue to function as they are today.
We recommend you assign the admins and users the appropriate licenses to continue to benefit from the feature set.
What you need to do to prepare:
Learn more about Document Fingerprinting here.
MC670437 — (Updated) New default Microsoft Purview Data Loss Prevention policies
<30 Days
Updated October 20, 2023: Please note that the 3 policies in the below (Financial Information, Healthcare Information, HR and Privacy Information) will be created but disabled and turned OFF by default. There is no change in the other 2 policies. Also, please note that Policy Tips will be turned OFF for all 5 policies. These policies are designed to not block any sensitive documents from being shared, they aim to only give admins the visibility to audit these activities in Activity Explorer. Further enhancements can then be taken by editing the policies. Should you choose to remove these policies after the Opt-Out period, simply disable or delete them from the DLP policies page.
We are creating default policies for Microsoft Purview Data Loss Prevention in your tenant to protect the most vulnerable sensitive information from accidental or malicious egress. The following default policies will be deployed along with the sensitive information they detect:
- Financial Information
- Healthcare Information
- HR and Privacy Information
- Source Code, Intellectual Property, and Trade Secrets
- Customer files
These changes are being made to your tenants as a precaution to help protect against potential data exfiltration.
When this will happen:
Timeline to opt-out: The rollout of the opt-out banner completed in late August. Once you see the banner, you will be able to opt-out until the 30 days is complete.
Timeline for Default policies: If opt-out is not selected, default policies will be rolled out in 30 days. The policies will be rolled out starting September 30th.
How this will affect your organization:
If you wish to opt-out of these policies, please visit your compliance portal and choose to opt out of the policies on the Policies page under Data Loss Prevention. The option to opt-out of these new default policies will be available for 30 days. After the roll out, these policies can be edited or deleted. For more information about editing a DLP policy see: Design a Data loss prevention policy | Microsoft Learn
What you need to do to prepare:
For more information about Microsoft Purview Data Loss Prevention please see:
MC669740 — (Updated) Microsoft Purview Information Protection Tracking and Revocation – End-User Tracking and Revocation
<30 Days
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
From the sensitivity menu, owners of Office files protected with a sensitivity label can access the Microsoft Purview compliance portal to view user access attempts and revoke access if needed.
When this will happen:
Preview: We have started rolling out and expect to complete by late August. - Complete
Registration will begin rolling out to production in mid-October 2023 (previously late August) and expect to complete by mid-November 2023 (previously late October).
Track & Revoke will begin rolling out to production will begin rolling out in late-October 2023 (previously late August) and expect to complete by mid-November 2023 (previously mid-September).
How this will affect your organization:
The Microsoft Purview Information Protection Tracking and Revocation feature will be turned on by default. To disable the feature, use the Disable-AipServiceDocumentTrackingFeature commandlet.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC668524 — (Updated) Microsoft Purview Information Protection: Tracking and Revocation in Compliance Portal
<30 Days
Microsoft 365 Roadmap ID 152126
Updated October 20, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users can access the Microsoft Purview compliance portal to check who has tried accessing their sensitivity labeled and encrypted local Office files and revoke access when needed.
When this will happen:
Preview: We will begin rolling out late August 2023.
Standard Release: We will begin rolling out late October 2023 (previously early November) and expect to complete by late November 2023 (previously mid-November).
What you need to do to prepare:
The Microsoft Purview Information Protection Tracking and Revocation feature will be turned on by default. To disable the feature, use the Disable-AipServiceDocumentTrackingFeature commandlet.
MC667126 — (Updated) Microsoft Purview DLP Endpoint: Most restrictive actions across multiple policies GA
<30 Days
Updated October 10, 2023: We have updated the timing below. Thank you for your patience.
We're enhancing the enforcement engine in Microsoft Purview Endpoint DLP (part of the Microsoft Purview Data Loss Prevention suite) to refine the restrictions enabled when multiple rules are matched. Note: This change is specific to Endpoint DLP for Windows only. Changes for MacOS will roll out separately.
When this will happen:
Starting in late August, we're rolling this enhanced behavior, which will apply the most restrictive policy-defined actions across multiple policies triggered by a given event. We expect to complete by early November 2023 (previously early October).
How this will affect your organization:
You are receiving this message because your organization has licensing that entitles you to use Endpoint DLP.
Once this change is implemented, administrators may see an increase in Endpoint DLP alerts as more user activities are blocked by the more restrictive of multiple flagged policies.
Example: A user attempts to print a file containing both SSN & credit card numbers, triggering multiple policies. The SSN policy blocks users from printing, and the credit card policy blocks with override. The most restrictive policy (block) will be applied, ensuring there are no gaps in coverage.
What you need to do to prepare:
No action or policy reconfiguration is needed to enable this change.
Get started with Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more: Get started with Endpoint data loss prevention Data Loss Prevention policy reference.
MC663629 — (Updated) Microsoft Purview: General Availability of Microsoft Purview Insider Risk Management forensic evidence add-on
>60 Days
Microsoft 365 Roadmap ID 117565
Updated October 20, 2023: We have updated the timing of this change, below. Thank you for your patience.
Microsoft Purview Insider Risk Management forensic evidence add-on is an optional, additional capacity feature in Microsoft Purview Insider Risk Management that gives security teams visual insights into potential insider data security incidents, with user privacy built in.
Organizations with Microsoft 365 E5/G5, Microsoft 365 E5/G5 Compliance, or Microsoft 365 E5/G5 Insider Risk Management are eligible to purchase Insider Risk Management Forensic Evidence 100GB Add-on.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
When this will happen:
This new SKU, Insider Risk Management Forensic Evidence 100GB add-on, will be available starting mid-January 2024 (previously October 1, 2023).
What you need to do to prepare:
Starting September 1, 2023, organizations can purchase Insider Risk Management Forensic Evidence 100GB add-on.
MC660616 — (Updated) Microsoft Purview Information Protection: Require sensitivity label to restrict permissions
>60 Days
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Users with access to Microsoft Information Protection (MIP) are redirected from old protection mechanisms towards the modern sensitivity labeling experience.
Microsoft 365 Roadmap ID 109532
When this will happen:
Preview: We will begin rolling out in mid-August 2023 (previously late July) and complete by early September 2023 (previously mid-August).
Standard Release: We will begin rolling out in late September 2023 (previously early September) and complete by early February 2024 (previously late October).
How this will affect your organization:
Users will no longer be able to apply IRM protection to new or existing documents and instead will be directed to apply MIP labels.
What you need to do to prepare:
Users with access to MIP that require the old IRM protection mechanisms will need to either need transition towards MIP labels or request a registry key capable of reverting to the old behavior.
MC609873 — Microsoft Purview Data Loss Prevention: Configure policy tips as pop-up dialog for emails with sensitivity labels
30-60 Days
Microsoft 365 Roadmap ID 139511
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
Data Loss Prevention policies can be configured to display policy tips as a pop-up dialog for emails with sensitivity labels.
When this will happen:
Rollout will begin in early December 2023 (previously mid-October) and is expected to be complete by mid-December 2023 (previously mid-November).
How this will affect your organization:
Admins can configure DLP policies to show policy tips as a dialog to end users when they attempt to send email messages that include a sensitivity label on the email or attachment. With this capability, admins can set up rules to warn or block or request for an explicit acknowledgement or a business justification from users before sending emails. Furthermore, admins can customize a learn more URL in a DLP rule, ensuring that end users receive valuable guidance through the popup.
Note: Users included in these policies must hold E5/G5 or equivalent licenses.
What you need to do to prepare:
Configure policy tips for Data Loss Prevention in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- Learn how to configure a DLP rule with oversharing popups: Create and Deploy data loss prevention policies
- View the AIP migration playbook: Migrate Oversharing Popups from AIP
MC515536 — (Updated) Microsoft Purview | Data Lifecycle Management and Records Management – Microsoft Graph APIs for extensibility
<30 Days
Microsoft 365 Roadmap ID 88276
Updated October 10, 2023: We have updated the rollout timeline below. Thank you for your patience.
As a part of our extensibility vision and first release to Microsoft Graph, we are introducing three new APIs for retention labels, events, and event types in the Microsoft Graph beta environment. These APIs will enable you to customize and extend on what we have built in the product so far.
These APIs can be used by compliance admins and developers to manage retention labels in Data Lifecycle and Records Management solutions.
When this will happen:
Rollout will begin in late March 2023 (previously late February) and is expected to be complete by mid-November 2023 (previously mid-October).
How this will affect your organization:
If your organization needs to automate any operation related to retention labels or events, we recommend you achieve this by using the new Graph APIs instead of using PowerShell cmdlets. With Graph, we use REST APIs that support better security, extensibility, and app authentication features.
The three APIs are available under the security node and the endpoints to access them are as follows:
What you need to do to prepare:
Permissions
Currently, these APIs are supported through delegated permissions only, which are managed through the Graph interface. We are introducing two new permissions which you will need to access these APIs:
- recordsmanagement.read.all
- recordsmanagement.readwrite.all
Licensing
Access to Data Lifecycle Management and Records Management features varies based on your Microsoft 365 license level. See Microsoft 365 guidance for security & compliance - Service Descriptions for licensing requirement details.
Get started with Data Lifecycle Management and Records Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- Use the Microsoft Graph records management API
- Create retention labels for exceptions
- Start retention when an event occurs
Microsoft Defender
MC685930 — Microsoft Secure Score - New Microsoft Defender for Identity recommendations
30-60 Days
We’re updating Microsoft Secure Score improvement actions to ensure a more accurate representation of security posture.
The improvement actions listed below will be added to Microsoft Secure Score. Your score will be updated accordingly.
When this will happen:
This will begin rollout in mid-November 2023 and is expected to be complete by mid-December 2023.
How this will affect your organization:
The following new Microsoft Defender for Identity recommendations will be added as Microsoft Secure Score improvement actions:
- Prevent users to request a certificate valid for arbitrary users based on the certificate template (ESC1)
- Edit overly permissive Certificate Template with privileged EKU (Any purpose EKU or No EKU) (ESC2)
- Edit misconfigured enrollment agent certificate template (ESC3)
- Edit misconfigured certificate templates ACL (ESC4)
- Edit misconfigured certificate templates owner (ESC4)
- Edit vulnerable Certificate Authority setting (ESC6)
- Edit misconfigured Certificate Authority ACL (ESC7)
- Enforce encryption for RPC certificate enrollment interface (ESC8)
These are new security posture reports related to Active Directory Certificate Services (AD CS) that analyze the configurations of different AD CS components and guide remediation, if necessary.
What you need to do to prepare:
There's no action needed to prepare for this change, your score will be updated accordingly. Microsoft recommends reviewing the improvement actions listed in Microsoft Secure Score. We will continue to add suggested security improvement actions on an ongoing basis.
MC683044 — Retiring “MDE Settings” and “New version” options from Threat Explorer
30-60 Days
We will be retiring the “MDE Settings” and “New version” options from Threat Explorer as we work to clean up and streamline the user experience.
When this will happen:
We will be rolling out this change beginning in early November 2023 and expect to complete by late December 2023.
How this will affect your organization:
Users and Administrators will no longer see the “MDE Settings” and “New version” options from Threat Explorer, when this change is implemented.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
MC681893 — (Updated) Microsoft Secure Score - Changes in SSPM support
<30 Days
Updated October 26, 2023: We have updated the content below to show as intended. Thank you for your patience.
We’re updating Microsoft Secure Score improvement actions to ensure a more accurate representation of security posture.
The improvement actions listed below will be added to Microsoft Secure Score. Your score will be updated accordingly.
When this will happen:
This will begin rollout in mid-October 2023 and is expected to be complete by mid-November 2023.
How this will affect your organization:
The following new Microsoft Entra (AAD) recommendations will be added as Microsoft Secure Score improvement actions:
- Ensure 'Phishing-resistant MFA strength' is required for administrators.
- Ensure custom banned passwords lists are used.
The following new Microsoft Sway recommendations will be added as Microsoft Secure Score improvement actions:
- Ensure that Sways cannot be shared with people outside of your organization
The following new Atlassian recommendations will be added as Microsoft Secure Score improvement actions:
- Enable multi-factor authentication (MFA).
- Enable Single Sing On (SSO).
- Enable strong Password Policies.
- Enable session timeout for web users.
- Enable Password expiration policies.
- Atlassian mobile app security - Users that are affected by policies.
- Atlassian mobile app security - App data protection.
- Atlassian mobile app security - App access requirement.
The following new Zendesk recommendations will be added as Microsoft Secure Score improvement actions:
- Enable and adopt two-factor authentication (2FA).
- Send a notification on password change for admins, agents, and end users.
- Enable IP restrictions.
- Block customers to bypass IP restrictions.
- Admins and agents can use the Zendesk Support mobile app.
- Enable Zendesk authentication.
- Enable session timeout for users.
- Block account assumption.
- Block admins to set passwords.
The names, functionality and compliance conditions for Okta and DocuSign security recommendation were updated as Microsoft Secure Score improvement action.
The name of this control "Ensure Sign-in frequency is enabled and browser sessions are not persistent for Administrative users" is changed to "Ensure Sign-in frequency is enabled and browser sessions are not persistent for Administrative users".
What you need to do to prepare:
There's no action needed to prepare for this change, your score will be updated accordingly. Microsoft recommends reviewing the improvement actions listed in Microsoft Secure Score. We will continue to add suggested security improvement actions on an ongoing basis.
Exchange Online and Microsoft Defender for Office 365
MC686270 — Microsoft 365 Icon Update
<30 Days
The Office 365 logo will be replaced throughout Outlook Mobile for Android with the Microsoft 365 logo, as will references to the account type.
When this will happen:
Standard Release: We will begin rolling out early November and expect to complete by mid-November 2023.
How this will affect your organization:
When this update rolls out, users may see their account represented with the updated icon in their accounts list.
What you need to do to prepare:
You may want to notify your users about this change and update any training documentation as appropriate.
MC684892 — Control Inbox and Calendar Sharing Options in Outlook on the Web and in the New Outlook for Windows
<30 Days
Microsoft 365 Roadmap ID 182261
Outlook on the Web and the new Outlook for Windows provides users with the ability to share mail and calendar with other users at different permission levels.
Starting in November 2023, tenant admins will be able to turn off the ability for users to share inbox and calendar folders by utilizing the new Office Cloud Policy Service “Turn off folder sharing.”
When will this happen:
The rollout for this feature will begin in early November 2023 and we expect to complete by late November 2023.
How this affects your organization:
This feature matches the existing capabilities available in Outlook for Windows (Win32).
When this policy is turned on, users will be able to block future sharing of inbox and calendar folders in OWA.
Existing users that have been granted permissions to the inbox and calendar will not be affected.
If admins wish to continue to allow users to delegate their inboxes and calendars, no action is necessary.
This capability is only active when the policy is turned on.
What you can do to prepare:
You may consider updating your training and documentation as appropriate.
For more information on applying Cloud policy, please visit: Overview of Cloud Policy
For more information on sharing policies in Exchange Online, please visit: Sharing Policies in Exchange Online
MC682560 — Final reminder: Retiring Remote PowerShell use through Connect-IPPSession
Rolled Out
As communicated in MC541649 (April 2023) and MC586563 (June 2023), the legacy Remote PowerShell (RPS) protocol will be retired on Thursday October 26th, 2023.
How this affects your organization:
On October 26, SCC customers will access EOP using REST-based APIs instead of RPS. Please click Additional Information to learn more.
You are receiving this message because our reporting indicates your organization may be using RPS to connect to EOP.
What you need to do:
Steps to switch to REST-based cmdlets:
Install the EXO module version 3.4.0 (current GA version) from here.
Use Connect-IPPPSession to establish connection.
What you can do to prepare:
REST-based cmdlets are available now in the latest GA version - we recommend customers install the latest EXO module version 3.4.0 as soon as possible (steps above).
Why this is happening:
In line with our vision to enhance the security of our cloud, the SCC admin experience will move to REST-based APIs.
In releasing the REST interface, RPS-based cmdlets will run as REST API calls instead of running via an RPS session. The REST API has the same cmdlets available and feature parity with RPS v1 cmdlets, so existing scripts and processes don't need to be updated. Simply using the new module will ensure REST is used rather than RPS.
MC682307 — Reactions in Outlook for GCC High and DoD
<30 Days
With reactions in Outlook, you can now react to an email message sent from someone in the same tenant without having to send a reply email. Show your appreciation and empathy with one click or tap.
Users will see a reactions icon (a face) in a message for any messages sent from someone inside the same tenant. They can hover over or tap it to see all of the possible reactions to select from.
Reactions will also send a digest email to a user who received any reactions.
When this will happen:
We will begin rolling out in late October 2023 and expect to complete rollout by late November 2023.
How this will affect your organization:
Reactions in Outlook allows you to react with one of six possible ways: Thumbs up, Heart, Celebrate, Laugh, Surprise, Sad. When you click on a reaction, everyone in the email thread who received the email will be able to see the reaction as long as they are part of the same tenant. The sender of the email will receive a notification of any reaction in their Notifications feed giving them a quick view of all the reactions their emails have elicited from other people.
Reactions will send a digest email once a day to users that may have missed any reaction notifications in the past 24 hours.
Users can also choose from different thumbs up reactions to choose the one that better represents them, and Outlook will remember their choice the next time.
What you need to do to prepare:
The September 2023 update outlines some ways for tenant admins and end users to disallow reactions on emails: Reactions in Outlook: Public usability update September 2023
MC681888 — S/MIME sensitivity label support on Outlook for Web
Rolled Out
Microsoft 365 Roadmap ID 180732
Outlook Web will support S/MIME (Secure/Multipurpose Internet Mail Extensions) sign and encryption as sensitivity label outcome. Customer admins could use set-label advanced setting to define the label to have S/MIME sign or encryption or both, and emails with those labels applied will enforce S/MIME sign and encrypt accordingly, and also it will support content marking of the label.
When this will happen:
Standard Release: We will begin rolling out in mid-October 2023 and expect to complete by end of October 2023
How this will affect your organization:
If you have defined S/MIME email labels for your organization, you will see that S/MIME label also available in Outlook on the web to apply. If you do not have any S/MIME labels today, then it will not impact your organization.
What you need to do to prepare:
If you would like to start using S/MIME labels, please refer the admin instructions how to enable S/MIME labels via set-Label cmdlets advanced setting.
MC680661 — Expand and Collapse Folders in Outlook Mobile
Rolled Out
Microsoft 365 Roadmap IDs 171602 and 171603
We're adding the ability to expand and collapse mail folders to Outlook Mobile.
When this will happen:
We will begin rolling out in early October 2023 and expect to complete rollout by late October 2023.
How this will affect your organization:
When viewing folders in the Outlook Mobile sidebar users will now see a ">" button that expands or collapses the current row, revealing any subfolders it may contain.
What you need to do to prepare:
The feature will automatically be enabled and will only appear for users who have a nested folder structure in Mail. For those who don't use subfolders there is no change in functionality.
MC680660 — Feature Update: Notifications for @mentions in Mail and Documents in Outlook Mobile
Rolled Out
Microsoft 365 Roadmap ID 171606 and 171607
We're adding @mention notifications to the Outlook Mobile Notifications Pane.
When this will happen:
We will begin rolling out early October 2023 and expect to complete by late October 2023.
How this will affect your organization:
In addition to the notifications they already receive for reactions, Outlook Mobile users will start to see notifications in the Notifications Pane when they are mentioned in an email, a Microsoft 365 document, or a Loop. Currently there are no push notifications associated with these in-app notifications.
What you need to do to prepare:
This feature works with no user or tenant intervention necessary.
MC678854 — (Updated) Public Preview: Unified RBAC for Exchange Online (EXO) configurations in MDO
TBD
Updated October 20, 2023: We are evaluating the rollout of this feature and will communicate a new timeline once it is determined.
Unified Role Based Access Control (URBAC) provides an alternative to traditional Microsoft Defender for Office 365 (MDO) and Exchange Online (EXO) RBAC. By default, there are no changes to your security portal permissions. If you want to change to using Unified RBAC, then you must first configure the new URBAC roles for your organization. Once you have configured these roles, then you can enable use of URBAC for ‘Microsoft Defender for Office’ permissions and/or ‘Exchange Online permissions’. Doing so replaces your existing RBAC with the new roles. You can find more information over here - Microsoft 365 Defender Unified role-based access control (RBAC) | Microsoft Learn.
Unified RBAC will not migrate/replicate Exchange Online permissions – these will require manual configuration in URBAC role groups.
Due to the impact of RBAC on features within the Defender for Office 365 portal, if you are migrating to URBAC, you should configure URBAC roles in a test environment prior to enabling it for your organization. If you encounter access problems, you will need to check the permissions for the roles you have configured in URBAC.
When this will happen:
We will communicate a new timeline when determined.
How this will affect your organization:
Unified RBAC enables organizations to configure a single set of permissions for their security teams that work for Defender for Office, as well as the other Defender solutions.
What you need to do to prepare:
If you want to change to using Unified RBAC, then you must first configure the new URBAC roles for your organization. Once you have configured these roles, then you can enable use of URBAC for ‘Microsoft Defender for Office’ permissions and/or ‘Exchange Online permissions’. Doing so replaces your existing RBAC with the new roles.
MC678057 — (Updated) Microsoft Defender for Office 365 Tenant Allow Block List limits
30-60 Days
Microsoft 365 Roadmap ID 98185
Updated October 20, 2023: We have updated the rollout timeline below. Thank you for your patience.
Soon, customers with Microsoft Defender for Office 365 plan 2 can create 10,000 block entries and 5,000 allow entries (via admin submissions) in the Tenant Allow Block List for each category (Domains & addresses, Files, and URLs). Customers with Microsoft Defender for Office 365 plan 1 can create 1,000 block entries and 1,000 allow entries (via admin submissions) in the Tenant Allow Block List for each category. Customers with Exchange Online Protection will remain at 500 block entries and 500 allow entries (via admin submissions) in Tenant Allow Block List for each category. The limit for spoofed senders will remain at 1,024 total entries (block entries and allow entries combined) for all service plans.
When this will happen:
This change will start rolling out in late October 2023 (previously early October) and should be completed by late December 2023 (previously late November).
How this will affect your organization:
It would not affect any of your existing Tenant Allow Block List entries.
If you already have higher limits, then you will remain unaffected by this change.
If you have a mixture of licenses, we will consider the highest service plan as the service plan for the entire tenant and allocate Tenant Allow Block list limits.
What you need to do to prepare:
No changes are required. Your existing Tenant Allow Block List entries will not be affected. Once this change is made, you might be able to create more allow entries and block entries based on your service plan.
MC675960 — (Updated) Microsoft Defender for Office 365: Tenant Allow Block List to Support URL Top-Level Domain Blocking
Rolled Out
Updated November 2, 2023: We have updated the content below to show as intended. Thank you for your patience.
Soon, you will be able to block URLs based on their top-level domain using block entries in the Tenant Allow Block List. You can create entries in the Microsoft 365 Defender portal or PowerShell, using the format “*.<TLD>/*”, where <TLD> can be any top-level domain such as .net, .biz, .io, .movie, country codes (.in, .us, .ru) etc. The entry is not case sensitive, and can be in uppercase, lowercase, or mixed.
It is applicable to customers with Exchange Online Protection, Microsoft Defender for Office plan 1 or plan 2 service plans.
The top-level domain entry results in the blocking of all URLs that are related to “*.<TLD>/*”, (subdomains, domains, or sub paths) both during mail flow (email is quarantined like other blocked URL entries) and at time of click across Microsoft Teams and Office apps, if Safe Links is enabled.
Microsoft 365 Roadmap ID 115506
When this will happen:
Rollout will begin in late September 2023 and is expected to be complete by late October 2023.
How this will affect your organization:
This will not affect any of your existing Tenant Allow Block List entries.
What you need to do to prepare:
No changes are required. Once this change is rolled out, you can use it to block URL top-level domains.
MC678855 — (Updated) ExchangePowerShell: retirement of tenant admin cmdlets to Get, Set, and Remove UserPhotos
>60 Days
Updated October 10, 2023: To ensure organizations have enough time to prepare we have updated the implementation timing below. Thank you for your patience.
We are working to ensure a coherent user profile image experience by retiring legacy profile photo services. This announcement covers the retirement of the ExchangePowerShell UserPhoto cmdlets for tenant admins to Get, Set, and Remove user profile photos:
When this will happen:
The retirement is scheduled for late March 2024 (previously November 30, 2023).
How this affects your organization:
After this change the ExchangePowerShell UserPhoto cmdlets for tenant admins to Get, Set, and Remove user profile photos will no longer be usable.
Tenant admins can perform the same actions to Get, Set, and Remove user profile photos through the Microsoft Graph PowerShell SDK, or alternatively can administer the user photos through Azure Active Directory or through Microsoft 365 Admin Center, as described in this article.
What you can do to prepare:
You may consider updating training and documentation as appropriate.
MC670895 — (Updated) Exchange Transport Rules (ETRs) stopping support for DLP scenarios
<30 Days
Updated October 20, 2023: We have updated this message as a reminder of this upcoming change. Review and take action as appropriate for your organization.
Last year, the Exchange Online data loss prevention (DLP) experience was retired from the classic Exchange admin center (EAC) (MC278896, August '21 & MC400953, July '22). We recommend customers use Microsoft Purview Unified DLP, which extends DLP protection to SharePoint Online, OneDrive for Business, Teams chats, devices, and more. The Microsoft Purview compliance portal provides access to advanced classification capabilities like EDM, ML, etc., along with rich alerts, incident management features, and more.
We are notifying you now that we are removing support for Exchange Online DLP in mail flow rules.
When this will happen:
mid-November 2023
How this will affect your organization:
Beginning mid-November, the ability to use the following Exchange DLP-related actions and conditions/exceptions (predicates) will be removed from mail flow rules:
- Actions: NotifySender
- Conditions/Predicates: MessageContainsDataClassifications (message contains sensitive information), ExceptIfMessageContainsDataClassifications, HasSenderOverride (sender has overridden the Policy Tip), ExceptIfHasSenderOverride
You will no longer be able to create new mail flow rules with these actions/predicates and any existing rules that use them will no longer be evaluated or run. If you’ve already migrated to Unified DLP, we recommend that you delete any affected mail flow rules. Otherwise, migrate and then delete any existing, affected mail flow rules before mid-November .
When the rollout reaches your tenant, you’ll see additional mail flow rule properties in the EAC and in Exchange Online PowerShell to show you which rules are no longer supported (Configuration Support and Unsupported Reason).
What you need to do to prepare:
Use the Get-TransportRule cmdlet to see if your organization has any existing mail flow rules that use these DLP actions or predicates. If you’ve already migrated to Unified DLP, verify that any mail flow rules that use the Exchange DLP conditions/predicates have been removed from the EAC or Exchange Online PowerShell. If you haven’t migrated to Unified DLP, migrate before mid-November, and then delete the Exchange DLP mail flow rules.
To learn more about creating rules in DLP, see Create and deploy a data loss prevention policy.
MC556159 — (Updated) Message List Selection UI updates for Outlook on the Web and New Outlook for Windows
<30 Days
Microsoft 365 Roadmap ID 125905
Updated November 2, 2023: We have updated the rollout timeline below. Thank you for your patience.
In order to save space on the message list in Outlook, we are making an UI update: From "selection circles on the left side of each row" to "Select mode that you have to get into before checkboxes appear", using a button in the top-right corner of the Message List. Users may have to acclimate themselves to the new Selection user experience.
In addition, mouse+keyboard multi-selection where users hold down Ctrl or Shift will continue to work as before.
When this will happen:
We will begin rolling out in mid-May 2023 and expect to complete rollout by late November 2023 (previously late October).
How this will affect your organization:
This will affect users who do not have "Sender Images" enabled in the Message List. If you have "Sender Images" turned on, hovering over the images will still show the checkboxes, even if you did not get yourself into "Select Mode". To review if you have "Send image" enabled, go to Settings > Mail > Layout and scroll to "Sender image".
What you need to do to prepare:
There is nothing to prepare for this change.
Microsoft 365
MC687205 — Manage Surface Hub 3 devices in Teams admin center and Teams Rooms Pro Management portal
30-60 Days
Microsoft 365 Roadmap ID 168347
Surface Hub 3 is now officially joining the Microsoft Teams Rooms family as an all-in-one Teams Rooms board running Teams Rooms on Windows.
This integration brings a unified experience to all your meeting spaces, allowing your team to seamlessly transition from one room to another. Whether you are using the streamlined, touch-first interface on Surface Hub 3 or the traditional console-based Teams Rooms setup, the experience remains consistent.
As Admins, you will be delighted to know that you can now manage Surface Hub 3 in the Teams Admin Center, right alongside your Teams rooms on Windows devices. Surface Hub 2S devices running the legacy Windows 10 Team edition experience will continue to show in the “Surface Hubs” tab.
For those with Teams Rooms Pro licenses, you can effortlessly monitor and manage your Surface Hub 3 devices through the Teams Rooms Pro Management portal.
When this will happen:
Standard Release: We will begin rolling out in early December and expect to complete in mid-December.
How this will affect your organization:
This integration brings with it some important changes for administrators using Teams Admin Center (TAC)/ Teams Rooms Pro Management portal (PMP) to manage their Teams Rooms on Windows devices:
- TAC - The new Surface Hub 3 devices and the software-migrated Surface hub 2S devices, upon enrollment, will be shown as part of the Teams Rooms on Windows inventory under the Teams devices section within Teams Admin Center. Only the Surface hub 2S devices running the legacy Windows 10 Team edition will be shown in the Surface hubs inventory.
- PMP – Surface Hub 3 devices and the software-migrated Surface hub 2S devices, upon enrollment will display as MTR on Windows device type in the Rooms dashboard.
What you need to do to prepare:
This is for your awareness; no action is required from you. If you have any questions or require further assistance regarding this change, please reach out to our support team.
MC682305 — Whiteboard: "Specific people” Share Link Fallback
Rolled Out
Microsoft Whiteboard now automatically utilizes Specific People Share Links (PSL) for participants of a Teams meeting when a whiteboard is shared and the tenant has Company-wide Share Links disabled (CSL).
When this will happen:
We will begin rolling out in mid-October and complete rolling out in late October 2023.
How this will affect your organization:
Whiteboards are stored in the OneDrive of the user who starts Whiteboard in the Teams meeting. If your tenant does not have CSLs enabled, previously when trying to share a whiteboard in a Teams meeting users would receive an error message and would not be able to access and collaborate on the whiteboard during and after the meeting.
Now, in the case that CSLs are disabled in your tenant, Whiteboard will fallback to utilizing PSLs and provide access directly to the participants of that Teams meeting. They will be able to access and collaborate on that whiteboard during and after the meeting.
Scenarios where PSL Fallback Apply:
- Teams meetings Whiteboard flow
- Teams Screen sharing Annotations flow
- Teams Whiteboard Tab App in channels (private, shared, public)
Note: participants that join a meeting or annotation session after a whiteboard has been shared will need to have the whiteboard manually shared with them. For private and shared Tab channel, the whiteboard will need to be manually shared with participants.
Note: PSL Fallback will only apply to in-tenant users, not external users.
What you need to do to prepare:
No change will be required, this will happen automatically based on your tenant settings.
MC681244 — Microsoft 365 Apps licensing will support 12 months offline – GCCH and DoD
Rolled Out
Microsoft 365 tenants within the GCC High and DoD clouds will support offline licenses for 365 days from the activated date. This will empower your users/devices to be offline for up to 12 months. If there is connectivity and an application is launched it will true up from that time for 12 months
When this will happen:
We will begin rolling out mid-October 2023 and expect to complete once the devices check in and receive the new licensing enablement.
How this will affect your organization:
This will enable your devices to be offline for up to 12 months. Although, we don't recommend this we understand that you could benefit from an extended offline period for specific scenarios.
What you need to do to prepare:
The IT Admin will not have to do anything as this will be a license file change from the service.
MC680788 — Pin based verification process for support callers
Rolled Out
In 2020, we added a PIN-based verification step to our existing phone-based verification process, to better protect your organization. If you call support, the Microsoft support representative will send a verification code to your registered email or phone in your Admin Center profile. Provide this code to the support representative to grant them access to your organization’s account.
How this will affect your organization:
This change will be enforced as of November 1, 2023
How this affects your organization:
Starting November 1, 2023, this enhanced verification will be required to open and manage a phone-initiated case with Support.
What you need to do to prepare:
To help ensure an expedited Support experience, users with appropriate permissions can update their profile contact information in Admin center->Users->Active users->Admin Name->Manage contact information.
Microsoft 365 IP and URL Endpoint Updates |
Documentation - Office 365 IP Address and URL web service
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.