- Home
- Public Sector
- Public Sector Blog
- July 2022 - Microsoft 365 US Public Sector Roadmap Newsletter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Newsworthy Highlights |
Help us shape our products for Government organizations
Microsoft is looking to understand employee experience sentiment in government organizations. Fill out our quick poll to help shape our products! Microsoft would love to hear from you!
What’s New in Microsoft Teams | June 2022 - Government
These features currently available to Microsoft’s commercial customers in multi-tenant cloud environments are rolling out to our customers in US Government Community Cloud (GCC), US Government Community Cloud High (GCC-High), and/or United States Department of Defense (DoD).
Release News |
Exchange Online
Consistently block delegates or shared mailbox members from accessing protected messages in Outlook
SharePoint / OneDrive for Business
Administrator ability to control Loop components through SharePoint Online PowerShell
We will soon be retiring the legacy Mover tool's ability to migrate from Google Drive, Dropbox, Box ...
Microsoft will soon retire Teams PowerShell Module versions below 4.x.x
With this new feature, users will be able to see due tasks assigned to them, connected to the ShareP...
This update includes improvements to the private channel site home page layout, the way site setting...
We are introducing First Run Experiences to help users learn about Topics in SharePoint - GCC
The SharePoint multilingual feature is expanding to include team sites
The Microsoft 365 Assessment tool will replace the relevant Modernization Scanner modules and ODSP S...
Teams
Empower end users to report inappropriate messages in Teams is now available
Show As in Teams meetings
Teams desktop client on VDI notification for unsupported versions
Call control via Bluetooth connected audio devices - GCC & GCCH
Microsoft Purview
Multiple Insider Risk Management features are available in public preview (US gov clouds)
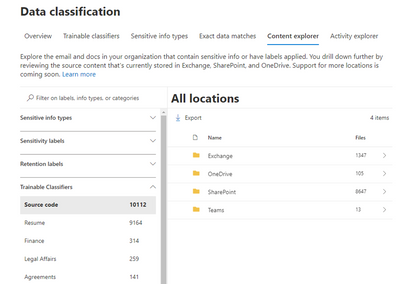
Data Discovery using Trainable Classifiers in Content Explorer
Security
Configurable impersonation protection and scope for preset security policies
Microsoft 365
Granular delegated Admin privileges in the Microsoft 365 Administration Center and Partner Center - ...
Microsoft 365 Apps for Windows reporting in Software Updates within the Microsoft 365 admin center
References and Information Resources |
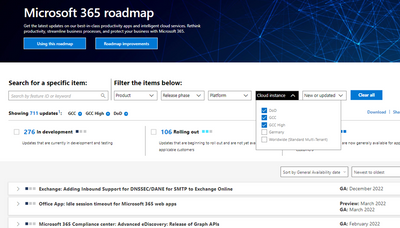
Microsoft 365 Public Roadmap
This link is filtered to show GCC, GCC High and DOD specific items. For more general information uncheck these boxes under “Cloud Instance”.
Stay on top of Microsoft 365 changes
Here are a few ways that you can stay on top of the Office 365 updates in your organization.
Microsoft Tech Community for Public Sector
Your community for discussion surrounding the public sector, local and state governments.
Microsoft 365 for US Government Service Descriptions
· Office 365 Platform (GCC, GCCH, DoD)
· Office 365 U.S. Government GCC High endpoints
· Office 365 U.S. Government DoD endpoints
· Microsoft Purview (GCC, GCCH, DoD)
· Enterprise Mobility & Security (GCC, GCCH, DoD)
· Microsoft Defender for Endpoint (GCC, GCCH, DoD)
· Microsoft Defender for Cloud Apps Security (GCC, GCCH, DoD)
· Microsoft Defender for Identity Security (GCC, GCCH, DoD)
· Azure Information Protection Premium
· Exchange Online (GCC, GCCH, DoD)
· Office 365 Government (GCC, GCCH, DoD)
· Power Automate US Government (GCC, GCCH, DoD)
· Outlook Mobile (GCC, GCCH, DoD)
Be a Learn-it-All |
|
Public Sector Center of Expertise We bring together thought leadership and research relating to digital transformation and innovation in the public sector. We highlight the stories of public servants around the globe, while fostering a community of decision makers. Join us as we discover and share the learnings and achievements of public sector communities. |

|
|
|
Microsoft Teams for Gov YouTube Video Series
The hub for teamwork in Office 365 GCC, GCC High, & DoD
Message Center Posts and Updates for Microsoft Teams in GCC |
Looking for what’s on the map for Microsoft Teams and only Teams in GCC?
Go right to the GCC Teams Feature Communications Guide
Message Center Highlights |
SharePoint Online / OneDrive for Business
MC394980 — SharePoint & OneDrive External Sharing One-Time Passcode mails will now come from no-reply@notify.microsoft.com
Updated June 27, 2022: We have updated the content below to show as intended.
In order to improve delivery reliability of the one-time passcode e-mails that are sent as part of the external sharing flow in OneDrive and SharePoint, we will be updating the sending address for these mails from no-reply@sharepointonline.com to no-reply@notify.microsoft.com. No other e-mails sent from OneDrive or SharePoint are being changed at this time.
When this will happen:
This change will begin rolling out late July and we expect rollout to be finished by late September.
How this will affect your organization:
This change should result in improved delivery reliability for all customers, and their partners, who use external sharing in OneDrive and SharePoint today.
What you need to do to prepare:
You may need to update your documentation or review your mailbox policies. Please ensure that the domain notify.microsoft.com is in the allow list for your mailbox policies
Please note, if your organization is using Azure B2B Integration with SPO, this change will not impact your organization.
MC394263 — Microsoft Lists calendar view conditional formatting
Microsoft 365 Roadmap ID 93360
The new feature, Microsoft Lists: Conditional formatting on calendar view, helps customize the calendar to meet specific requirements. Items in a list calendar view can be color coded based on conditions or rules specified on the fields available in the view. These rules can be managed using the 'Format current view' section of the Calendar view.
When this will happen:
Standard release: The feature rollout will begin in mid-June and is expected to complete by end of June.
How this will affect your organization:
Users will now be able to apply colors/highlights to the items appearing on the calendar canvas. This can be achieved using the ‘format current view’ option from the top right dropdown. Using the fields available in the view, the feature will introduce following capabilities:
- Add a new rule based on a field and select the color for corresponding items
- Modify, rearrange and delete existing rules
What you need to do to prepare:
No action is required to enable this feature. You may consider notifying users about this new capability and update your training and documentation as appropriate.
MC393823 — Improvements to SharePoint pages authoring - Column reflow and RSS connector web part
Microsoft 365 Roadmap ID 93243
These updates include changes to our reflow automation for two-column sections and the RSS Connector web part by giving more control to users around the number of publications shown at one time and the number of articles shown per publication.
When this will happen:
Targeted Release (select users and entire org): We will begin rolling these changes out in late June and we expect to complete rollout late June.
Standard: We will begin rolling this out in early July and we expect to complete rollout mid-July.
How this will affect your organization:
Changes to 2 columns reflow
To help with readability and better integration of pages in Teams, we will now be keeping the two-column layout intact for pages viewed on screens larger than 640px wide. Previously, we would collapse page content into a single column when viewed on screens exceeding this size.
Control vertical section reflow
Currently the vertical section in pages goes to the bottom of the page when viewed on smaller screens. We’re adding the ability for page authors to control this reflow and choose whether the vertical section goes to the top or bottom of the screen when the screen is condensed to a smaller size.
More room for page editing in Microsoft Teams
Last year, we enabled the ability to author SharePoint pages directly in Teams. With this latest change, when editing the page, users will get a full screen experience, making it easier for users to edit their pages.
Changes to RSS Connector web part
For pages currently using the RSS Connector web part, we will begin limiting the number of articles displayed per publication to 50. On new pages created after this change is rolled out, the limit will be 10. This will give users control over how many publications and how many articles can be displayed at one time.
What you need to do to prepare:
There is no work required to prepare for the updates listed for SharePoint Pages authoring, however you might want to notify your users about this change and update your training and documentation as needed.
Learn More:
· Use the Connector web part (microsoft.com)
· Add sections and columns on a SharePoint modern page (microsoft.com)
MC391952 — Microsoft 365 Assessment tool for SharePoint 2013 workflows available now!
SharePoint 2013 Workflows platform was introduced 10 years ago. Since the release of SharePoint workflows, Microsoft has evolved workflow orchestration to not only encompass SharePoint, but all the productivity services you use within Microsoft 365 and extend to 3rd parties. Power Automate is the Microsoft solution for workflow orchestration. It connects to all Microsoft 365 services and over 220 other services to let an enterprise build custom workflows. There are also many 3rd party solutions that can directly orchestrate SharePoint data via SharePoint’s open API platform.
SharePoint 2010 Workflows was retired as of November 1st, 2020 with the notice that we would also retire SharePoint Workflow 2013 in the future. Although we currently do not have a timeline to announce SharePoint 2013 Workflow retirement, it is strongly recommended to move 2013 workflows to the Power Automate platform or some other modern workflow orchestration solution.
To help, a new, open-source Microsoft 365 Assessment tool is available to help you identify and evaluate the usage of SharePoint 2013 workflows in your tenant.
When this will happen:
Available beginning in early June.
How this affects your organization:
The new, open source, Microsoft 365 Assessment Tool helps you identify and evaluate the SharePoint 2013 workflows on your tenant by providing you the usage data of SharePoint 2013 Workflows and generating a Power BI report to help plan migration of 2013 workflows to a modern workflow orchestration service.
What you can do to prepare:
Review the documentation and update internal documentation as appropriate.
· Modernize SharePoint 2013 workflows
· Guidance: Migrate from classic workflows to Power Automate flows in SharePoint
· Microsoft 365 Assessment tool
· Microsoft 365 Assessment tool blog post
MC390752 — SharePoint multilingual feature can be applied to team sites
Microsoft 365 Roadmap ID 93332
The SharePoint multilingual feature is expanding to include team sites. This new release includes other improvements to the navigation and site title editing experience for users whose preferred language differs from the site’s default language.
When this will happen:
We will begin rolling out early June and expect general availability of this feature by mid-September 2022.
How this will affect your organization:
Your organization will have more multilingual site options. There are also improvements to how site content for navigational labels, site descriptions, footers and titles are stored and saved. These changes prevent users from editing site content into the wrong language when the site’s default language is different from the user's preferred language.
Summary of changes:
· Additional language information is provided when editors make changes to navigational labels, site descriptions, footers, and the site's name.
· The new language information will display even if multilingual settings have not been enabled for the site.
· When editors change site content that is not in their preferred language, it will modify the label instead of creating a translation.
· Additional information can be found in tool tips next to the content that’s being edited to confirm the language.
· Translations for site content can only be created when multilingual settings have been enabled.
What you need to do to prepare:
There will not be any changes to your existing instances of multilingual on SharePoint communication sites or how the multilingual feature functions overall. To prepare for this change, let site owners know that they will be able to create team sites in more than one language. Learn more about how to create multilingual SharePoint sites and editing site content.
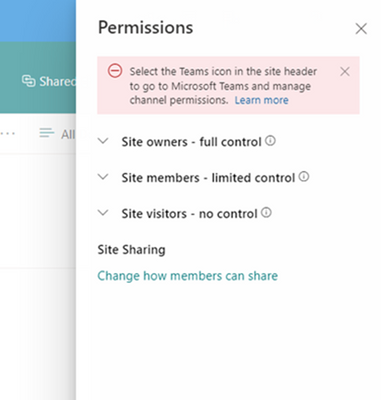
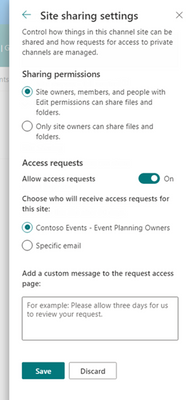
MC390004 — SharePoint: Updates to Channel Site to Display Site Permissions
Microsoft 365 Roadmap ID 93240
With this update, we're bringing back the Site Permissions panel to channel sites. You will now be able to display in read-only mode the site permissions for the channel sites. Also, as the site owner, you will be able to access and make changes to the site sharing or guest expiration options.
When this will happen:
Targeted Release: We will begin rolling out in mid-June.
Standard Release: We will begin rolling out to all customers in early July and expect to complete rollout by mid-July.
How this will affect your organization:
The site permissions panel is now available on channel sites and can be viewed by all users. However, this panel does not allow permissions to be edited, it is read-only. We have added a banner at the top of the panel to indicate that this is a Teams connected channel site and permissions should be managed in Teams.
For Private Channel sites, site owners will see both the Site Sharing and Guest expiration menu items below the permissions groups. Shared channel sites will only see Site Sharing as Guest Expiration does not apply to shared channel sites.
In the site sharing menu panel, we have made updates to accurately reflect what content you can control sharing access to. For channel sites, you have never been allowed to share the site. The menu now has just 2 sharing permissions options down from 3 on regular sites. Everything else remains the same.
What you need to do to prepare:
You may want to notify your users about this change and update your training and documentation as appropriate.
Learn More:
· Overview of Teams and SharePoint Integration
MC388539 — SharePoint: Updated Site Logo Management
Microsoft 365 Roadmap ID 93231
With this update, we're centralizing the management of your site logo. To update or manage your site logo, you will now exclusively visit the Header panel under the 'Change the Look' settings.
When this will happen:
We will begin rolling out early July and expect to complete rollout by mid-July.
How this will affect your organization:
Site owners will be able to navigate to the 'Header' panel from the 'Change the Look' settings, and then scroll to the bottom of the panel where the site logo options will be located.
What you need to do to prepare:
You may want to notify your users about this change and update your training and documentation as appropriate.
MC387641 — Planner cards now on SharePoint team site activity feed
Microsoft 365 Roadmap ID 93273
This new feature will allow members of Team sites to see tasks assigned to them by other team members on their home page.
When this will happen:
Targeted Release (select users and entire org): will begin rolling out in early June and expect to complete rollout late June.
Standard: will begin rolling this out in late June and expect to complete rollout early July.
How this will affect your organization:
This release will enable Planner task cards to show up on your team site activity feed when you are approaching the due date.
Now, when a team member assigns a task to you within a plan, a card will show up on your site activity feed if you are within two days of the due date.
What you need to do to prepare:
You do not need to do anything to prepare for this update, but you may want to let your users know about this improvement.
MC362284 — (Updated) OneDrive sync app will automatically configure accounts
Microsoft 365 Roadmap ID 93242
Updated June 14, 2022: We have updated the rollout timeline below. Thank you for your patience.
This release will enable the OneDrive sync app to sign into an account even quicker. Users will experience an improved single sign-on experience by automatically being able to see their OneDrive files within their file browser upon sign in or OneDrive app update.
· On Windows, users who are signed into the device with an Azure Active Directory (AAD) account will see their OneDrive folder start syncing without entering their account credentials.
· On macOS, users who are signed into another Microsoft app (i.e., Office, Teams, Edge, etc.) will see their OneDrive folder start syncing without entering their account credentials.
When this will happen:
We will begin rolling out in early July (previously mid-June) and expect to complete by late July.
How this will affect your organization:
If OneDrive is running in the background, it will periodically try to sign in with an existing AAD credential that is made available to Microsoft applications. This new capability will replace our existing Windows policy of SilentAccountConfig and is brand new for macOS. If you previously had SilentAccountConfig enabled, then you will see no difference in behavior. If you have never enabled this policy, then as long as OneDrive is configured to run in the background, you will have a more streamlined experience onboarding to OneDrive.
What you need to do to prepare:
Ensure that your OneDrive is set up to run in the background. On macOS you can confirm this by setting the "OpenAtLogin" plist. OneDrive already runs in the background on Windows.
If you would like to disable this, then there is a new policy and plist item in build 22.065 called "DisableAutoConfig". If you set this to 1, it will disable this new automatic account configuration.
MC361749 — (Updated) Section Templates now available in SharePoint Pages
Microsoft 365 Roadmap ID 88838
Updated June 10, 2022: We have updated the rollout timeline below. Thank you for your patience.
Section Templates curated for beautiful image and text combinations can now be added in the plus menu.
When this will happen:
Targeted Release (select users and entire org): We will begin rolling this out in late April and expect to complete rollout early May.
Standard: We will begin rolling this out in mid-May and expect to complete rollout mid-June (previously late May).
How this will affect your organization:
Authors of SharePoint Pages and News will be able to access section templates from the plus menu in a new tab next to the sections tab.
Section templates can be utilized when authoring SharePoint pages. Users will be able to choose and add templates at the section level instead of just at the page level. Although users will still have access to blank sections, we have implemented six templates to make section design easier.
These templates include fixed aspect ratios on the image webpart to automatically keep images within a template looking consistent with one another. However, this can be overridden when editing an image.
Once elements are added to the canvas, they can be added and deleted just like manually added section elements, but now users have a sleek and inspirational starting point.
What you need to do to prepare:
You do not need to do anything to prepare for this update but might want to notify your users about this change and update your training and documentation as appropriate.
MC350768 — (Updated) SharePoint: Create from the SharePoint app bar
Microsoft 365 Roadmap ID 82160
Updated June 2, 2022: Based on learnings from our early rings, we have made the decision to make additional changes before we proceed with the rollout. The create command in the app bar will be temporarily removed to address some stability issues with the Office document creation. We will add this experience back to the app bar starting in late July. We have updated the rollout timeline below. Thank you for your patience.
Apologies for the delayed release of this new feature. Resources in the SharePoint app bar are expanding to include the ability to create sites, files, and lists as an action.
Key points:
· Timing:
o Targeted Release (select users and entire org): will begin rolling out in late July (previously mid-April) and will complete by mid-August (previously late April)
o Standard: will begin rolling out in mid-August (previously mid-May) and will complete by late August (previously late May).
· Action: Action: review and assess
· Roll-out: tenant level
How this will affect your organization:
This new feature will allow users to create sites, files, and lists from within the SharePoint app bar. Users will be able to select the Create command (the plus sign) on the app bar and then select an option from SharePoint sites, Microsoft Lists, or Office files (Word, PowerPoint, Excel, and OneNote). As users create each of the different assets included in the panel, they will launch the create experience for each format.
· Note: The new create command cannot be disabled or customized. However, if you have previously disabled self-service site creation, the option to create a site will not appear on the create panel
· Site creation will launch the SharePoint site creation panel in the site you are in; if you are in a hub, the site will be associated with this hub when created
· List creation will open in a new tab and take you to the create experience in Microsoft Lists
· Office files will create the document in your OneDrive site until you save to a different location
What you need to do to prepare:
You do not need to do anything to prepare. The SharePoint app bar cannot be customized. If you have not already enabled and customized global navigation in the SharePoint app bar, it’s highly recommended that you do so to take advantage of the best navigational experience for end users.
Learn More:
· Use the new SharePoint app bar and set up global navigation
MC341151 — (Updated) Large Folder Delete on OneDrive and SharePoint Document Libraries on Web
Microsoft 365 Roadmap ID 88979
Updated June 10, 2022: We have updated the rollout timeline below. Thank you for your patience.
Currently large folders (>10k items) cannot be deleted from OneDrive and SharePoint Document Libraries on web. With this new feature we will allow users to delete them. The process of deleting a large folder will be the same as deleting any small folder on the web today.
When this will happen:
We will begin rolling out in mid-March and expect the rollout to be completed by mid-July (previously late May).
Note: Some users may see this feature before other users within your organization.
How this will affect your organization:
Users will now be able to delete large folders (>10k items) OneDrive and SharePoint Document Libraries on web. If a user tries to delete a shared folder that another user has already started deleting, they will see an error message, "This item is already being deleted." Deleted folders will still be available in the site Recycle Bin.
What you need to do to prepare:
No action is required.
MC336858 — (Updated) OneDrive and SharePoint: Access your Teams standard and private channel files
Microsoft 365 Roadmap ID 88911
Updated June 21, 2022: We have updated the content below for clarity. Thank you for your patience.
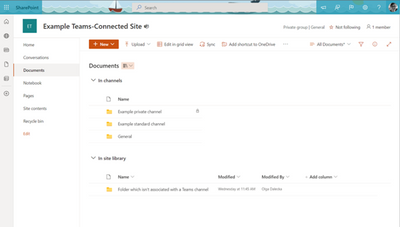
With this new feature, users that navigate to a site in SharePoint or OneDrive will be able to access the files stored in the Teams standard and private channels associated with that site. Users will see an “In channels” section when you navigate to the default document library of a Teams-connected site. This functionality will be available in OneDrive & SharePoint web, including experiences like the Move/Copy Picker.
When this will happen:
Targeted release (select users and entire org): will begin rolling out in mid-April (previously late March) and expect to complete rollout late April (previously early April). - Complete
Standard: will begin rolling out in late April (previously early April) and expect to complete rollout late July (previously late May).
How this will affect your organization:
When a user navigates to the document library of a SharePoint site associated with a team, the “In channels” section will be visible and collapsed by default. The “In channels” section will include all standard and private channels within the Team, and private channels will be distinguished with a specific icon. When shared channels become available, they will also appear in this section. The “In channels” section will only appear when a user navigates to the default document library of a SharePoint site that’s connected to a Team. The “In channels” section will not be visible if the SharePoint site is not connected to Teams.
· The impact of this work is that all Teams channels will be discoverable within a single SharePoint site, as opposed to navigating to the separate SharePoint site associated with each private or shared channel. This aligns with how end users currently work with channels in Teams.
· There will be no change to private channel disclosure as part of this change. For example, a user will only see the private channels that they explicitly have access to—regardless of whether they access them from OneDrive, SharePoint or Teams.
What you need to do to prepare:
This change will only impact SharePoint sites that are connected with a Team, and the “In channels” section will only be visible in the document library where Teams channels content is stored.
Standard channels will appear in both the “In channels” and “In site library” sections, while private channels will only appear in the "In channels" list.
· This was based on customer feedback that duplication of entries between the list was confusing and made the “In site library” list unnecessarily long. The impact of this decision is that, if an end user expects to find a folder within the document library, they will now need to look under the “In channels” section.
You might want to notify your end users, update your user training and prepare your help desk as part of this change.
MC329431 — (Updated) Microsoft Stream: in player Help experience
Updated June 28, 2022: We have updated the rollout timeline below. Thank you for your patience.
The web player for audio & video files that are stored in OneDrive and SharePoint (including when those files are embedded in Teams, Yammer, and SharePoint web parts) is updated with a new feature called Help. The Help feature provides links to public end user help documentation for the player.
When will this happen:
The feature will begin rolling out in early April and expect to complete by mid-July (previously end of May).
How this affects your organization:
Users will be able to see and interact with Help for all OneDrive for Business and SharePoint video and audio files.
What you can do to prepare:
You many consider updating your training and documentation as appropriate.
MC320460 — (Updated) Connected Templates with Microsoft Teams and SharePoint
Microsoft 365 Roadmap ID 84724
Updated June 21, 2022: We have updated the rollout timeline below. Thank you for your patience.
We determined that this notification did not go to the entire intended audience. We apologize for any inconvenience this delayed notification may have caused.
We are announcing the upcoming release of Connected Templates with Microsoft Teams and SharePoint. The connected templates will offer a new way of combining Microsoft Teams templates with SharePoint templates. Prior to this integration, clients needed to deploy Microsoft Teams or SharePoint-specific templates.
· Microsoft Team Templates allow administrators to easily deploy consistent teams across their organization using predefined or customized team templates across their organization.
· SharePoint templates offer a straightforward way for admins to build sites with pre-populated pages, page templates, news post templates, and web parts that can be customized to fit the needs of their organization.
Through this integration, Teams administrators can create templates that include SharePoint components, bringing together the capabilities of the Teams and SharePoint templates.
When this will happen:
We will begin rolling this out in mid-January and expect to complete rollout early July (previously early June).
How this will affect your organization:
Today, when you create a team through "create a team from templates' you get an automatically created SharePoint site that supports that template. We are adding SharePoint assets to the team you have just created with this new integration. In essence, all SharePoint applications that are associated with the new template will be automatically added, pinned, and displayed in this new team template.
· When you create a new team using a default template - for example, the “Manage a Project” template, the project management channels and apps, and the connected SharePoint template will get applied automatically. Now, the pages, lists, and Power Platform integrations from SharePoint will be automatically pinned as tabs in Teams and you can edit these pages and lists directly in Teams.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
MC267581 — (Updated) Microsoft Lists: Custom list templates
Microsoft 365 Roadmap ID 70753
Updated June 7, 2022: We have updated the rollout timeline below. Thank you for your patience.
This new feature will support the addition of custom list templates from your organization alongside the ready-made templates Microsoft provides to make it easy to get started tracking and managing information.
Key Points:
· Timing:
o Targeted release (entire org): Complete
o Standard release: will roll out in mid-September (previously mid-May) and be complete by early November (previously mid-June)
· Roll-out: tenant level
· Control type: user control / admin control
· Action: review, assess and educate
How this will affect your organization:
This feature will give organizations the ability to create their own custom list templates with custom formatting and schema. It will also empower organizations to create repeatable solutions within the same Microsoft Lists infrastructure (including list creation in SharePoint, Teams, and within the Lists app itself).
End-user impact:
Visual updates to the list creation dialog and the addition of a From your organization tab when creating a new list. This new tab is where your custom list templates appear alongside the ready-made templates from Microsoft.
Admin impact:
Custom list templates can only be uploaded by a SharePoint administrator for Microsoft 365 by using PowerShell cmdlets. For consistency, the process of defining and uploading custom list templates is like the custom site templates experience.
To define and upload custom list templates, admins will use the following site template PowerShell cmdlets:
· Use the Get-SPOSiteScriptFromList cmdlet to extract the site script from any list
· Run Add-SPOSiteScript and Add-SPOListDesign to add the custom list template to your organization.
· Scope who sees the template by using Grant-SPOSiteDesignRights (Optional).
The visual updates for this feature will be seen by end-users in the updated user interface (UI) when creating a list.
The From your organization tab will be empty until your organization defines and publishes custom list templates.
What you need to do to prepare:
You might want to notify your users about this new capability and update your training and documentation as appropriate.
Learn More:
· PowerShell Cmdlets documentation for custom list templates
· Creating custom list templates
Microsoft Teams
MC395422 — Cameo in PowerPoint Live
Microsoft 365 Roadmap ID 87725
With Cameo in PowerPoint Live, users will be able to integrate Teams camera feed into PowerPoint presentation and customize how and where they want to appear on slides.
Cameo supports all personalization properties like any other Office graphical object such as those offered by Pictures, Gifs and Shapes. This includes layering Cameo between content, adding motion effects such as morph, changing styles, shapes etc.
Limitation: - Cameo in PowerPoint Live will not be shown in the recording, web or mobile clients.
When this will happen:
Production and GCC will begin rolling out in early September and expect to complete by mid-September.
GCCHigh and DoD will begin rolling out early December and expect to complete by mid-December.
How this will affect your organization:
Cameo will allow users to insert and fully customize their camera feed directly within PowerPoint slide prior to joining a Teams meeting. Once joined in Teams meeting, users will be able to share PowerPoint Live and see their video integrated into slides.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
MC395226 — Calls App in Government Clouds
We are bringing the new and improved Modern Calls App to government clouds. We apologize for not communicating sooner about this change coming to your organization.
When this will happen:
Release for the calls app in government clouds has already begun and will complete by early July.
How this will affect your organization:
When your users update the Teams desktop app, they will see the new calling experience. A streamlined view shows contacts, voicemail, and calling history at once, making it easier to initiate or return a call with a single click.
Additional enhancements that are coming to Teams Calling:
· CarPlay support for Teams Calling
· Teams will identify potential spam calls and digitally attest to outgoing calls to prevent them from being rejected by external recipients.
What you need to do to prepare:
You might want to notify your users about this new capability and update your training and documentation as appropriate.
Learn More: Restore and maintain personal connections with new Microsoft Teams Calling features
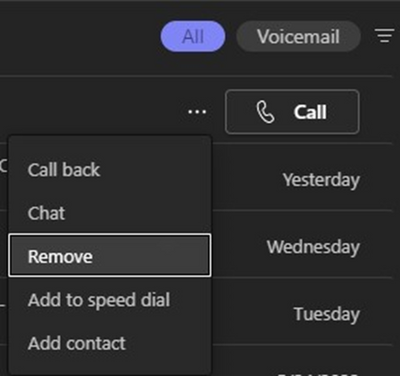
MC394845 — Remove from Call History View
Microsoft 365 Roadmap ID 94200
Users will now be able to remove a call history item from their view from the Calls App. Users will be able to do this across the desktop, web, and mobile application of Teams. Users should know that simply removing a call history from view still retains back-end logging of all calls available by user's IT Admin.
When this will happen:
We will begin rolling out late July and expect to complete by mid-September.
How this will affect your organization:
Once available users will be able to remove call history.
Note: removing call history does not impact back-end logging.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
MC394837 — Co-organizer Meeting Role
Microsoft 365 Roadmap ID 81676
Organizers will soon be able to assign the co-organizer meeting role to up to 10 specific people they invite to their meeting. Co-organizers will be granted most of the capabilities of the organizer in the meeting, including being able to access & modify the meeting options for the meeting.
Usage of the co-organizer role for a meeting will be optional. If users choose not to use the co-organizer feature, there will be no change.
When this will happen:
We expect this feature to begin rolling out in early-July and expect the rollout to be complete by late July.
How this will affect your organization:
Once this feature has been enabled, a “Choose co-organizers” meeting option will be available. The default value for this option is “None.” The option operates similarly to when “Specific people” are selected as presenters for the meeting. The meeting organizer can click on the selector box to open a dropdown menu where they can choose from the list of qualified people who have been invited to the meeting.
To qualify for the co-organizer role, an invitee must be using an account that is on the same tenant as the organizer’s account. Organizers will be able to assign the co-organizer role to up to 10 people.
Co-organizers will be displayed as additional organizers on the meeting roster, and they will have most of the capabilities of an organizer in the meeting. Co-organizers can do the following:
· Access and change meeting options
· Bypass the lobby
· Admit people from the lobby during a meeting
· Lock the meeting
· Present content
· Change another participant’s meeting role
· End the meeting for all
Co-organizers cannot do the following:
· Create & manage breakout rooms
· View & download attendance reports
· Manage the meeting recording
· Edit the meeting invitation
· Remove or change the Organizer role
The “Only me” selection for the “Who can present?” meeting option has been updated to reflect that this will apply to “Only me and co-organizers.”
The “Only me” selection for the “Who can bypass the lobby?” meeting option has been updated to reflect that this will apply to “Only me and co-organizers.”
Usage of the co-organizer role for a meeting is optional. If users choose not to use the co-organizer feature, there will be no change.
What you need to do to prepare:
There is nothing you need to do. The “Choose co-organizers” meeting option will appear automatically on the meeting options page when the feature has rolled out.
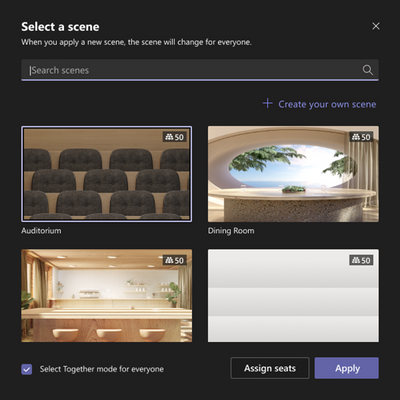
MC394833 — View Together Mode for Everyone
Microsoft 365 Roadmap ID 94390
Microsoft Teams users in a meeting will soon have the option to turn on Together Mode for all participants in a meeting.
While turning on Together Mode in a Teams meeting, the organizer and presenters will see a dialog box to select a scene. Additionally, the organizer and presenters will also see an option to "Select Together Mode for Everyone." This option will not be selected by default. After selecting and clicking on "Apply", the new scene will be selected for everyone and the Teams meeting view of all the participants will get changed to Together Mode.
Meeting participants, at all times will be able to switch the Meeting view from Together Mode to Gallery or Large Gallery view. Meeting participants will join in Together Mode view directly.
If this option is unselected, new participants will stop joining in Together Mode view.
Note: This will roll out on Teams Desktop (Windows and Mac) client.
When this will happen:
We will begin rolling this out in early August and expect to complete rollout mid-September.
How this will affect your organization:
What you need to do to prepare:
We suggest you notify your users about this change and update your training and documentation as appropriate.
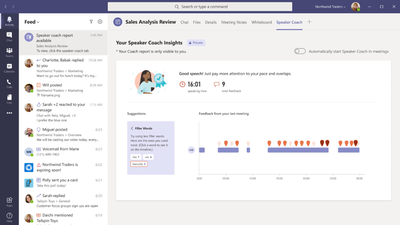
MC394785 — (Updated) Speaker Coach in Microsoft Teams Meetings
Microsoft 365 Roadmap ID 88253
Updated June 29, 2022: We have updated the content below to provide additional information. Thank you for your feedback.
Speaker Coach provides private, personalized feedback on your speaking and presentation skills in both real-time as well as post-meeting in a summary.
When this will happen:
We will begin rolling out in early July and expect to complete rollout by late July.
How this will affect your organization:
Tenant admins should ensure the policy for speaker coach is enabled in order for their users to be able to turn on speaker coach for themselves in meetings.
What you need to do to prepare:
You may want to notify your users about this new capability and update your training and documentation as appropriate.
Learn More:
· PowerPoint’s Presenter Coach Expands to Microsoft Teams and Takes on the New Name Speaker Coach
· Meeting policy settings - Speaker Coach
MC394264 — Remove Freehand by InVision from the ShareTray
The Meeting Share Tray will no longer allow you to share the Freehand by InVision app to collaborate on a Freehand board during a meeting. Instead, users will be able to use the Freehand app for Teams Meetings, as described here: Freehand whiteboard app for Microsoft Teams – InVision Support.
Note: If your organization is not using Freehand by InVision you can safely disregard this message.
When this will happen:
This feature change will start rolling out to all environments in early July 2022.
How this will affect your organization:
All users in your organization will have to add the Freehand app for Meetings to collaborate on a Freehand board instead of sharing a Freehand from the Teams Meeting Share Tray.
What you need to do to prepare:
Please inform your users about this functionality and point them to the user documentation so they are aware of the limitations.
MC392295 — Disable chat write access for anonymous or unauthenticated users
Microsoft 365 Roadmap ID 91142
Financial institutions consider chat messages as a form of data exfiltration, so it's imperative for IT admins to gain flexibility and control over chat access for anonymous or unauthenticated users. The latter may be expected to join Teams meetings, but they should be restricted from seeing and accessing any type of electronic communication on chat. This feature provides additional security by only disabling chat write access for non-federated users and unauthenticated users who join Teams meetings through a link, so it must be used in conjunction with disabled meeting chat policy applied to financial advisors to remain compliant.
When this will happen:
· Standard: early June through mid-July
· GCC: late July through mid-August
· GCC High: late August through early September
· DoD: mid-September through late September
How this affects your organization:
With this change IT admins can now disable chat write access at the policy level for non-federated users and unauthenticated users who join Teams meetings through a link.
What you can do to prepare:
There are two ways IT admins can disable chat write access for non-federated users and unauthenticated users who join Teams meetings through a link:
· PowerShell: Admins can run the syntax [-MeetingChatEnabledType <String>] with current supported values Enabled, Disabled, or EnabledExceptAnonymous.
· Teams Admin Portal: Admins can select the option, "Turn it on for everyone but anonymous users" in the "Chat in meetings" dropdown and apply this meeting policy to a subset or all tenant users.
Note: the scope of EnabledExceptAnonymous or "Turn it on for everyone but anonymous users" is limited to disabled write access. Once this meeting chat policy is applied to user/s, an organizer cannot override this policy through meeting options.
MC392294 — Media Logging Enabled by Default
We ask that you pardon us for not having provided advance communication of this release. To log diagnostic data for Teams meetings, users must have the option in the Teams client turned on. Up until recently Teams media logging was turned off by default for all machines. With this update, Media logging is enabled by default on high-end machines. Media logs contain diagnostic data about audio, video, and screen sharing in Teams meetings. They are required for support cases that are linked to call-related issues. The list of CPUs with media logging enabled by default is in the public documentation.
When will this happen:
The update is currently available.
How this will affect your organization:
When creating a support request with Microsoft Support, "Full Client Logs" are required to assist with any issue involving voice, video or screen sharing. In cases when “Enable logging for meeting diagnostics” has not been enabled prior to the incident, support team might suggest that the setting should be enabled, the issue reproduced, and the logs are collected to be shared with Microsoft Support.
Note: For machines where logging has been already enabled, the required logs can be collected right away and attached to the support request.
User experience:
For desktop clients running on machines affected by the change, the setting will be updated.
· The update will take place within the routine client update, no client restart is enforced.
What you need to do to prepare:
No specific action is required. In case the enabled logging is not expected, instruct the users to manually update Settings > General> Enable logging for meeting diagnostics to disabled.
Learn more about the list of CPUs with media logging enabled by default.
MC392289 — Reminder Installation of .Net 4.8 and WebView2 required for Teams Meeting Add-In in Outlook
As a reminder, .Net 4.8 and WebView2 are required for the Teams Meeting Add-In in Outlook.
How this affects your organization:
To avoid a degraded experience with the Teams Meeting Add-in in Outlook, ensure clients are updated to .Net 4.8 and WebView2.
How you can prepare:
Review the following resources and ensure .Net 4.8 and WebView2 are installed to run the Teams Meeting Add-in in Outlook:
· Use the Microsoft Teams Meeting add-in in Outlook - Microsoft Teams | Microsoft Docs
· Troubleshoot the Teams Meeting add-in in Outlook for Windows (microsoft.com)
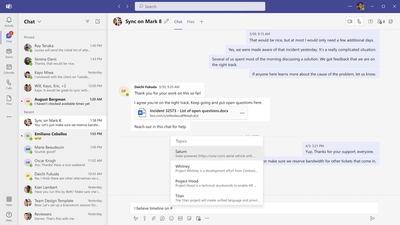
MC391950 — (Updated) Viva Topics in Teams
Microsoft 365 Roadmap ID 72189
Updated June 14, 2022: We have updated the content below to show as intended. Thank you for your patience.
Viva Topics in Teams allows users to mention topics in their chat conversations so that others in the conversation can easily learn more about a topic by hovering over the topic name and viewing the topic card. This feature requires users to have a Viva Topics license.
When this will happen:
· Public Preview: We began rolling out in April and will continue rolling out through June and expect complete rollout by late June.
· General Availability: We will continue rolling out through late June and expect complete rollout by late July.
· GCC: We will continue rolling out in early July and expect complete rollout by late August.
How this will affect your organization:
If your organization has users with Viva Topics licenses, those users will be able to mention topics by typing the # character and choosing a topic from the topic picker. The topic picker will narrow selections based on what the user types. Once a topic is selected, users can post the message.
Recipients with Viva Topics licenses will see the selected topic's name as highlighted text and will be able to hover over the highlight and see details of the topic in the topic card such as the alternate names for the topic, descriptions, associated people and resources.
What you need to do to prepare:
There is nothing you need to do to prepare for this change. The topics being displayed will be the same topics that are shown in Outlook Web and SharePoint.
MC391078 — Teams user/device usage report and Graph API data source change
We have made improvements to the underlying data source that powers the Teams User usage report and Teams Device usage report in the Microsoft 365 Admin Center and Teams Admin Center. We apologize for not meeting our communication commitments and communicating these changes prior to their roll out.
When will this happen:
These changes have been completed.
How this will affect your organization:
Moving forward the data source for Microsoft 365 admin center and Teams admin center will be same for all common Teams related usage reports –
1. Metrics reported in individual reports will have common naming practices and parity across usage reports in two admin center.
2. Individual metrics presented in each report will have same values.
3. Last Refresh frequency of each report across above two surfaces will be same (no more refresh duration lag between two admin center)
4. Common reporting duration – Besides M365 admin usage reports, 180 days of reporting usage data will be available for User activity report, Team usage report and Device usage report in Teams admin center as well.
This change is part of our ongoing commitment to offer reliable and accurate reporting for product usage.
How to prepare:
You may consider updating training and documentation as appropriate.
Documentation:
· Microsoft 365 usage reports: Microsoft 365 admin center activity reports - Microsoft 365 admin | Microsoft Docs
· Teams usage reports: Microsoft Teams analytics and reporting - Microsoft Teams | Microsoft Docs
MC390416 — Teams Chat with self
Microsoft 365 Roadmap ID 88066
Users will now be able to chat with themselves. All the same chat functionality that works for chatting with others will work for the individual chatting with themselves. They will be able to start a chat with themselves by typing their full name in the To: field when creating a new chat.
When this will happen:
We will begin rolling out mid June and expect to complete by late June.
How this will affect your organization:
The user will now be able to send themselves messages the same way they would with anyone else.
Previously, the user wasn't able to directly send themselves messages. There were workarounds, however, where a user could start a meeting with themselves and utilize the meeting chat as a self chat. Another workaround was if everyone in a group chat left, and the user was there alone. These will continue being part of the experience, but they are different from a chat with self.
A chat with self allows the user to type in their name in the To field when creating a new chat, and have a conversation with themselves. They can also access chatting with themselves from their people card.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
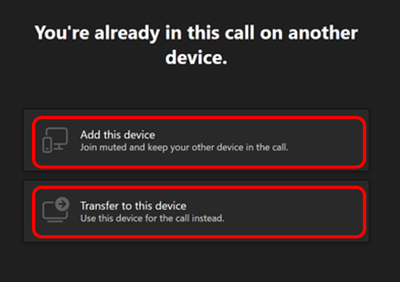
MC391070 — Transfer Calls or Meeting between Desktop and Mobile in GCC-High/DoD
This new Teams release will expand support and allow calling participants to transfer an ongoing VoIP, PSTN, Group call or Meeting between Teams devices. Users will be able to transfer a call or meeting from one device to another or even add a second device to the same call.
When this will happen:
· GCC-High: Available now.
· DoD: we will begin rolling out in late June and expect to complete by early July
How this will affect your organization:
After joining a Teams call or meeting on one device, users will be able to join the same call or meeting on a second device. For example, going from desktop to a mobile device or even to another desktop. Additionally, they will be able to transfer a call from one device to a second device, in the same call, if there is a need to share content from the second device.
Option to join Teams call from another device.
Teams will provide two options: Add this device, and Transfer to this device.
What you need to do to prepare:
You might want to notify your users about this new capability and update your training and documentation as appropriate.
MC390413 — Microsoft Teams Connect shared channels general availability
Microsoft 365 Roadmap ID 94820
Teams Connect Shared channels will be generally available in the coming weeks. Shared channels is a new channel type, in addition to the existing standard and private channel types. Shared channels enable users to collaborate seamlessly with internal and external partners beyond the boundaries of a team.
Invite individuals or entire teams to a shared channel. These can either be from your org or from an external Azure AD org. Once added to a shared channel external users can access the channel right from their Teams account without having to switch organizations.
Note: External collaboration is off by default.
When this will happen:
We will begin rolling this out in mid-July and expect to complete it by mid August.
Rollout to GCC cloud will begin early August and complete by late August.
How this will affect your organization:
Shared channels will be generally available in the coming weeks. Team owners will see shared channels as an additional channel type while creating a channel. They will be able to share the channel with anyone in the tenant.
Key callouts:
Each shared channel is backed by a dedicated SharePoint site collection. We have improved the SharePoint admin experience to help you manage sites collections associated with shared and private channels better.
· Shared channels support both meet now and scheduled meetings, making it easy to bring the team together.
· Shared channels support tabs, bots and message extensions.
· Graph APIs and PowerShell cmdlets have been updated to support shared channels.
· Shared channels support full range of Microsoft 365 Information Protection capabilities - eDiscovery, Legal Hold, Information Barriers, Retention, DLP, Audit Logs, & Communication compliance.
External collaboration in shared channels is powered by Azure AD B2B direct connect, a new way to collaborate with other Azure AD organizations. With B2B Direct connect, there's no need to add the external user as a guest in your organization. Cross-tenant access policies let admins manage B2B direct connect for their organization. A shared channel can be shared with as many organizations that can be specified in the Azure AD cross-tenant access policy. External collaboration is off by default.
What you need to do to prepare:
You may consider updating your user training; notifying your help desk; and updating your user level policy around shared channel creation.
You can manage shared channels and external collaboration for your organization via the policy managed through the Teams Admin Center or via PowerShell (New-CsTeamsChannelsPolicy).
· Who can create shared channels (-AllowSharedChannelCreation)
· Who can invite external users to a shared channel (-AllowChannelSharingToExternalUser)
· Who can participate in an external shared channel (-AllowUserToParticipateInExternalSharedChannel)
Note: Public preview customers - Once GA rollout is complete users will no longer need to opt-in to public preview to create shared channels. There will be no impact on existing shared channels.
Admin: Shared channels in Microsoft Teams | B2B direct connect overview
Users: What is a shared channel in Teams?
MC389614 — Join Meetings by a Meeting ID and Passcode
Microsoft 365 Roadmap ID 80668
Microsoft Teams users will soon be able to join meetings by Meeting ID. This release of Microsoft Teams Meeting ID will be rolling out across Microsoft Teams Desktop, Mobile and Web and will provide an additional way for users to join a Microsoft Teams meeting by entering a digital ID and Passcode.
When this will happen:
We will begin rolling out in early July and expect to complete rollout by mid July.
How this will affect your organization:
All meetings will have a Meeting ID and passcode that is automatically assigned to a Microsoft Teams user and added to the meeting invite under the meeting link. Meeting attendees can join the meeting by entering the Meeting ID. For all meeting attendees, the pre-join, lobby and security will remain the same.
To join a meeting by ID in Outlook, you can find the meeting details section in the meeting invite in Outlook in the details for Meeting ID and Passcode. You can enter this Meeting ID and Passcode on the Teams app or the Website to join the meeting.
To join a meeting by ID on Teams desktop, you can enter a Meeting ID and Passcode to join the meeting from the Calendar in the Teams app. You will see the option to join meeting by ID in the top right corner of the calendar.
To join a meeting by ID from a Web Page, we are introducing a public web page where users can enter the Meeting ID and Passcode for any meeting to initiate a meeting join.
To, join a meeting by ID on mobile for both iOS and Android, you can enter a Meeting ID and Passcode using the meet icon in the top right corner of the Calendar in the Teams app.
What you need to do to prepare:
You may want to notify your users about this new capability to join meetings and update your training and documentation as appropriate. Meeting ID and Passcode can be used on the app and Teams website link to join a meeting. There will continue to be individual separate sections for existing Video conferencing ID and Dial in by Phone, which are independent of Meeting ID.
MC387684 — (Updated) Upcoming feature release: Teams Button long press to Raise Hand during meeting
Microsoft 365 Roadmap ID 90738
Updated June 9, 2022: We have updated the rollout timeline below. Thank you for your patience.
We ask that you pardon us for not having honored out customer commitment to you by providing advance notice of this release. This new release enables users to invoke a Raise Hand reaction by long pressing their Teams Button on their Microsoft Teams certified peripheral.
When this will happen:
GCC-High: starting mid-July and expect to complete mid-August
How this will affect your organization:
While navigating remote working, users may be using a wireless headset and might be away from their mouse and keyboard when they want to raise or lower their hand. With this capability, users can easily create this reaction by pressing the Teams Button on their certified peripheral.
Note: Once the rollout is complete, users will be able to leverage this feature to Raise/Lower their Hand during meetings with their Teams Button on their Teams certified peripherals.
What you need to do to prepare:
There is no action required from the IT Admin or user to enable this feature. All of your Teams certified peripherals will automatically support this feature once the rollout is complete.
MC387640 — Dynamic Caller ID in Calls app for Call Queue Agents
Microsoft 365 Roadmap ID 86992
Call queue agents can now place calls from the Calls app using a call queue phone number, defined in resource account, as their caller ID. This ensures the call is properly identified by the recipient and that the call back number is the call queue number rather than the agent's personal line.
When this will happen:
We will begin rolling out in early June and complete rollout by late June.
How this will affect your organization:
You can assign outbound caller ID numbers for agents by specifying one or more resource accounts with a phone number. Agents can select which outbound caller ID number to use with each outbound call they make.
What you need to do to prepare:
The resource account used for calling ID purposes must have a Microsoft Teams Phone System Virtual User license and one of the following assigned:
· A Calling Plan license and a phone number assigned
· An Operator Connect phone number assigned
· An online voice routing policy (phone number assignment is optional when using Direct Routing)
Learn More:
MC387038 — (Updated) Call control with Bluetooth headsets and speakerphones
Microsoft 365 Roadmap ID 84309
Updated June 23, 2022: We have updated the timeline and provided additional details for clarity. Thank you for your patience.
This new feature allows users to use the buttons on Bluetooth headsets, speakerphones or certified devices that don't require a USB dongle to answer, end and even mute calls.
Note: This feature supports both Windows 10 and Windows 11. Mac support will be upcoming in first half of 2023.
When this will happen:
Public preview: began rolling out in mid-March but support was limited to Windows 10.
Standard and GCC: will begin rolling out in late July (previously late June) and be complete in mid-August (previously late July) with support for both Windows 10 and Windows 11.
GCC-H: will begin rolling out in late July and be complete in late August with support for both Windows 10 and Windows 11.
How this will affect your organization:
This feature uses industry standard communication protocol called Hands Free Protocol (HFP) and will work with most headsets that have an answer/end call button.
· If users can use the headset to answer cellular calls with their cell phone, then it indicates that the headset supports HFP and the user should be able to use it to answer calls with Teams.
· Mute control leverages industry standard mechanism so will also work for most devices that support a mute button.
Teams button support, which can be used for actions like meeting join, and raise/lower hands during meeting will only be available on certified models.
At this time, if a user has two or more audio devices connected to their PC, answering the call using device button is not supported (this is to avoid activating the wrong device). This limitation will be removed in upcoming updates to Windows that will allow Teams to know which device triggered the call answer action,but we do not have an estimated time at this time.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate. Watch for announcements soon about full certification for native Bluetooth headsets which will validate device performance for things like audio quality, and Teams button support.
MC387036 — (Updated) Teams Meeting Poll New Question Type - Rating
Microsoft 365 Roadmap ID 93991
Updated June 23, 2022: We have updated the rollout timeline below. Thank you for your patience.
The Rating question type is being added to the Polls app within Microsoft Teams. Meeting owners can easily create and launch Rating polls to increase engagement and collect input from their meeting attendees, as well as share the results live.
When this will happen:
We will begin rolling out in mid-July (previously late June) and expect to complete rollout by late July (previously mid-July).
How this will affect your organization:
Meeting owners within your organization will be able to create and launch this new Rating question if the Polls app is enabled.
What you need to do to prepare:
You may want to update internal documentation and/or training material to let people know about the new feature and how to use it.
MC384783 — (Updated) Microsoft Teams: Multi-language meeting invite control for government clouds
Microsoft 365 Roadmap ID 81521
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
Multi-language Teams meeting invite control enables administrators to configure the join information languages in meeting invitations. Controlled by a new policy parameter, this feature allows the administrator to set up to two languages to replace the user preferred language when creating new Teams meeting invitations across all email platforms.
When this will happen:
· GCC-High rollout targeting mid-July and complete by end of July
· DOD rollout targeting early August and complete by mid-August
How this will affect your organization:
Administrators will soon be able to use the new -MeetingInviteLanguages parameter in CsTeamsMeetingPolicy to set the join information language used in the meeting invite. Administrators can choose to set this at the user or group level, or for the entire organization.
This parameter will allow administrators to set up to two languages to replace the user preferred language when creating a new Teams meeting invite across all platforms including Outlook desktop client, Outlook for the web, Outlook mobile app, and the Teams desktop/mobile apps.
Impact to users:
· If an administrator specifies a language override using the -MeetingInviteLanguages parameter, users will not have control over the language used for the join link in meeting invitations they create.
· Using the below multiple languages example, the screenshot above illustrates how the meeting invitation will look.
What you need to do to prepare:
To set one language
· In the below example, the administrator is setting the meeting invite language to English (en-US). If the meeting policy is updated with a single language and the same meeting policy is applied to all users in the organization, all users will create the meeting invite details in the specified single language - regardless of their preferred language.
· Set-CsTeamsMeetingPolicy
-Identity Global -MeetingInviteLanguages "en-US"
To set multiple languages
· In the below example, the administrator is setting the meeting invite language to English (en-US) and French (fr-FR).
· Set-CsTeamsMeetingPolicy
-Identity Global -MeetingInviteLanguages "en-US,fr-FR"
Notes:
· The order of the languages displayed in the meeting invite follows the order of the languages specified in the PowerShell cmdlet.
· If -MeetingInviteLanguages was not set on the policy (default), there will be no impact to the user and the preferred user language will take effect.
MC384329 — (Updated) Multitasking Panel for Meetings on iPad
Microsoft 365 Roadmap ID 86923
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
The Teams Mobile meeting experience is being updated for the iPad. Users will now see a collapsible right panel during meetings, which enables richer multitasking experiences such as chat or viewing participant list alongside the ongoing meeting.
When this will happen:
This feature will begin rollout in early June (previously late May) and will complete rollout by mid-June (previously early June).
How this will affect your organization:
Users will now see a collapsible right panel during meetings, when chat or participant list is accessed.
What you need to do to prepare:
No action is required from you as this is an UI change.
MC378419 — (Updated) Automatic groupings available in Teams for channel posts
Microsoft 365 Roadmap ID 94118
Updated June 1, 2022: We have updated the content below for clarity. Thank you for your feedback.
A new Automatic Grouping will be available in Teams as a suggestion to use in channel posts. Users will be able to use "@Team Owners" in a channel posting and all Team Owners will be notified. This functionality will be available in both Desktop (including Web) and Mobile.
When this will happen:
· Standard Release: We expect this rollout to begin in early May and expect the rollout to be completed by late June.
· GCC: We expect this rollout to begin in late May and expect the rollout to be completed in early July.
· GCC-H: We expect this rollout to begin in late May and expect the rollout to be completed in early July.
· DoD: We expect this rollout to begin in late May and expect the rollout to be completed in early July.
What do I need to do to prepare:
No action required; you may want to update your documentation accordingly.
MC376244 — (Updated) Retiring Call Quality Dashboard (CQD) v2 -- Get ready for CQD v3 today
Updated June 28, 2022: We have updated the timeline below. Thank you for your patience.
We will be retiring Call Quality Dashboard (CQD) v2 beginning on July 29th, 2022 (previously June 30th). On that day, we will cut over to Call Quality Dashboard v3, which is where we will continue to invest our development resources.
You are receiving this message as this change will impact all GCC-H and DoD tenants using the Microsoft Teams Call Quality Dashboard v2. Accessing the CQD v3 is the same as you currently access CQD v2 today.
Note: We request that you perform the below steps (1 and 2) prior to July 29th (previously June 30th) as Microsoft support staff will not be able to assist in retrieving these files after this date.
How this will affect your organization:
Once this change takes place, you will no longer be able to access any custom reports you have created in CQD v2, and any building data files uploaded to CQD v2 will not be available.
What you need to do to prepare:
Before July 29th, 2022 (previously June 30th), you need to:
1. Download any custom reports created in CQD v2. We recommend each administrator using CQD v2 should perform this if they wish to keep their custom reports. If desired, a designated administrator may also perform this by visiting https://cqd.dod.teams.microsoft.us/cqd/#/Users (DoD) or https://cqd.gov.teams.microsoft.us/cqd/#/Users (GCC-H) and downloading each user's custom reports manually.
2. Download your current building data files. Where you have multiple building data files, please ensure you capture the date range for which each file applies. These data files are tenant-wide, so only one administrator with the 'Upload building data' permission must perform this step. See this page for information on which admin roles have the appropriate permissions.
What you need to do once the change is complete:
Once the cutover to CQD v3 has completed:
1. Add your building data files to CQD v3 using an administrator account with the 'Upload building data' permission. Only one administrator needs to perform this step. Verify that the correct date ranges are applied to each data file to ensure your building mapping is accurate in your reports.
2. Administrators can import their custom reports back into CQD v3 if they desire.
MC358529 — (Updated) Microsoft Teams: Roaming bandwidth control for GCC-H and DoD
Microsoft 365 Roadmap ID 89064
Updated June 7, 2022: We have updated the rollout timeline below. Thank you for your patience.
Roaming bandwidth control is a new capability that allows admins to set dynamic bandwidth policies which are based upon the geographic location of users’ Teams clients. This allows admins to set more limited bandwidth controls for when users travel to remote or bandwidth constrained locations, and then relax limitations when they travel to a location with higher bandwidth capacity. Initially two settings from the Teams Meeting Policy will be included - AllowIPVideo, andMediaBitRateKb.
When this will happen:
We will begin rolling out in late April and expect to be completed by late June (previously mid-May).
How this will affect your organization:
The network roaming policy is not enabled by default, admin will need to configure the policy via PowerShell or Teams admin center to implement it.
What you need to do to prepare:
Review your network roaming policy needs and configure as appropriate for your organization.
MC346913 — (Updated) Adding a restore option to the Manage Tags Tab
Microsoft 365 Roadmap ID 88318
Updated June 10, 2022: We have updated the rollout timeline below. Thank you for your patience.
In the near future, we will be adding a restore option on the Manage Tags tab (Manage Team > Manage Tags). This update will make it so that when tags are deleted, they will be kept in a deleted section in the Tags tab and can be restored for up to 30 days from the date of deletion.
Note: This is similar to the lifecycle management for Teams Channels.
When this will happen:
Standard: We will begin rolling this out in mid-August (previously mid-May) and expect to complete rollout late August (previously early June).
Government: We will begin rolling this out in early September (previously mid-June) and expect to complete rollout late September (previously early July).
How this will affect your organization:
If the tag setting at the manage team level for "Tags are managed by" is set so to "Team owners and members," then all team members will be able to see and restore deleted tags.
If the tag setting at the manage team level for "Tags are managed by" is set so to "Team owners," then only team owners will be able to see and restore deleted tags.
What you need to do to prepare:
You might want to notify your users (especially your Team Owners) about this change and update your training and documentation as appropriate.
MC341572 — (Updated) Microsoft Teams: Text Predictions for Teams Mobile (Android)
Microsoft 365 Roadmap ID 81573
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
Text predictions is coming to Teams for Android.
When you compose or reply to a message in Teams, Editor Text Predictions anticipates your writing and suggests a suitable word or phrase inline. This saves time and helps to reduce typos.
When this will happen:
We expect the rollout to begin in early April and expect the rollout to be completed by late June (previously late May).
How this will affect your organization:
This feature will be enabled on by default via a tenant and user setting. The feature can be disabled through messaging policies or users can disable for themselves via an in app setting.
What you need to do to prepare:
Review your messaging policies and the policy setting for this feature.
MC341571 — (Updated) Microsoft Teams: Casting from Teams desktop client to Microsoft Teams Rooms
Microsoft 365 Roadmap ID 88027
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
For quick ad-hoc sessions that don’t require setting up a formal meeting, people can use Teams casting to wirelessly connect to a Teams Room and display content from the Teams desktop client (Windows and Mac). Users can share their screen and cast content stored locally on their computer or accessible via Office 365.
When this will happen:
We expect this rollout to begin in mid-March and expect to complete the rollout by late June (previously late May).
How this will affect your organization:
This feature will be available on all Teams clients. To use the feature with Microsoft Teams Rooms, please ensure that the Bluetooth beaconing setting is enabled on all Microsoft Teams Rooms devices.
The Teams Cast menu option can be found in the top menu of Teams when selecting “…”, as shown in the figure below.
What you need to do to prepare:
This feature will be available on both Windows and MacOS clients. It will require that Bluetooth is enabled on the personal device. To use the feature with Microsoft Teams Rooms, please ensure that the Bluetooth beaconing setting is enabled on all Microsoft Teams Rooms devices.
MC333941 — (Updated) New Fluent Emoji style coming to Teams emojis and reactions
Microsoft 365 Roadmap ID 88277
Updated June 7, 2022: We have updated the rollout timeline below. Thank you for your patience.
This update will have Teams joining Microsoft 365 and Windows in updating all emojis and reactions to the new Microsoft Fluent emoji style, bringing users a more vibrant and expressive emoji experience.
When this will happen:
We will begin rolling this out in late February and expect to complete rollout late June (previously late May).
How this will affect your organization:
This update will only change the styling of the emojis and reactions in Teams. There is no functional change to the features.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
Learn More:
MC320165 — (Updated) Microsoft Teams: Chat density
Microsoft 365 Roadmap ID 88064
Updated June 7, 2022: We have updated the rollout timeline below. Thank you for your patience.
Customize the number of chat messages you see on the screen. Use the compact setting to fit 50 percent more messages on the screen. Comfortable setting keeps the chat display as it is in Teams today.
This will be rolling out on Teams desktop.
When this will happen:
Standard: will begin rolling this out in mid-February and expect to complete rollout late February. - Complete
GCC: will begin rolling this out in mid-March (previously mid-February) and expect to complete rollout late March (previously late February). - Complete
GCC-High: will begin rolling this out in mid-April (previously mid-March) and expect to complete rollout late April (previously late March). - Complete
DoD: will begin rolling this out in mid-May (previously mid-April) and expect to complete rollout mid-June (previously late May).
How this will affect your organization:
This feature introduces a new, optional setting for users to increase the density of viewable content on Teams Chat via "Compact" mode. Compact mode allows the user to see more content given the same screen size vs. the existing layout.
Note: This mode only increases the density of the Teams Chat message pane and has no impact on Teams and Channel experiences.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
MC320163 — (Updated) Updating default tenant-level tag management settings
Microsoft 365 Roadmap ID 88318
Updated June 10, 2022: We have updated the rollout timelines below. Thank you for your patience.
We’re updating the default tag management settings based on customer feedback. The new defaults eliminate the need for team members to ask owners to create or edit tags on their behalf.
Key points:
· Timing: This change will start to rollout in mid-August (previously late May), and we expect to complete the rollout by late September (previously early July).
· Roll-out: tenant level
· Control type: Team owner and team member control
· Action: review and assess for appropriate experience
How this will affect your organization:
The Teams admin center default for who can manage tags will be updated from "Team owners" to "Team owners and members." Tenant admins still can override the default and limit Tag Create/Edit to Team Owners only. If you have already made any changes to any option in the Tagging settings in the Teams admin center, your settings will not be updated, and this change will not affect your tenant.
This tenant-level setting will be inherited by existing Teams, unless the Tags Settings in Manage Team has been updated. For example, if the “Tags are managed” by setting at the team level value has been changed, this change will not affect that team.
These changes simplify the Tags permissions model and makes it consistent with other Teams concepts like Channels.
For new teams created after this change is implemented, all team members will be able to create and manage tags by default, similar to the defaults for create and edit channels. The team owner will still have the option to override this management setting if "Let team owners override who can manage tags" is set to "On" in your Tagging settings in the Teams admin center.
What you need to do to prepare:
No specific action is required but you will want to review your settings and update your documentation as necessary.
MC296205 — (Updated) Multi-language Teams meeting invite control
Microsoft 365 Roadmap ID 81521
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
Multi-language Teams meeting invite control enables administrators to configure the join information languages in meeting invitations. Controlled by a new policy parameter, this feature allows the administrator to set up to two languages to replace the user preferred language when creating new Teams meeting invitations across all email platforms.
When this will happen:
· Standard rollout targeting mid-June and complete by end of June.
· GCC rollout targeting early July and complete by mid-July.
How this will affect your organization:
Administrators will soon be able to use the new -MeetingInviteLanguages parameter in CsTeamsMeetingPolicy to set the join information language used in the meeting invite. Administrators can choose to set this at the user or group level, or for the entire organization.
This parameter will allow administrators to set up to two languages to replace the user preferred language when creating a new Teams meeting invite across all platforms including Outlook desktop client, Outlook for the web, Outlook mobile app, and the Teams desktop/mobile apps.
Impact to users:
· If an administrator specifies a language override using the -MeetingInviteLanguages parameter, users will not have control over the language used for the join link in meeting invitations they create.
· Using the below multiple languages example, the screenshot above illustrates how the meeting invitation will look.
What you need to do to prepare:
To set one language
- In the above example, the administrator is setting the meeting invite language to English (en-US). If the meeting policy is updated with a single language and the same meeting policy is applied to all users in the organization, all users will create the meeting invite details in the specified single language - regardless of their preferred language.
- Set-CsTeamsMeetingPolicy -Identity Global -MeetingInviteLanguages "en-US"
To set multiple languages
- In the above example, the administrator is setting the meeting invite language to English (en-US) and French (fr-FR).
- Set-CsTeamsMeetingPolicy -Identity Global -MeetingInviteLanguages "en-US,fr-FR"
Notes:
- The order of the languages displayed in the meeting invite follows the order of the languages specified in the PowerShell cmdlet.
- If -MeetingInviteLanguages was not set on the policy (default), there will be no impact to the user and the preferred user language will take effect.
MC292796 — (Updated) Co-organizer Meeting Role
Microsoft 365 Roadmap ID 81391
Updated June 23, 2022: We have updated the rollout timeline below. Thank you for your patience.
Organizers will soon be able to assign the co-organizer meeting role to up to 10 specific people they invite to their meeting. Co-organizers will be granted most of the capabilities of the organizer in the meeting, including being able to access & modify the meeting options for the meeting.
Usage of the co-organizer role for a meeting will be optional. If users choose not to use the co-organizer feature, there will be no change.
When this will happen:
We expect this feature to begin rolling out in mid-June (previously late May) and expect the rollout to be complete by mid-July (previously late June).
How this will affect your organization:
Once this feature has been enabled, a “Choose co-organizers” meeting option will be available. The default value for this option is “None.” The option operates similarly to when “Specific people” are selected as presenters for the meeting. The meeting organizer can click on the selector box to open a dropdown menu where they can choose from the list of qualified people who have been invited to the meeting.
To qualify for the co-organizer role, an invitee must be using an account that is on the same tenant as the organizer’s account. Organizers will be able to assign the co-organizer role to up to 10 people.
Co-organizers will be displayed as additional organizers on the meeting roster, and they will have most of the capabilities of an organizer in the meeting. Co-organizers can do the following:
· Access and change meeting options
· Bypass the lobby
· Admit people from the lobby during a meeting
· Lock the meeting
· Present content
· Change another participant’s meeting role
· End the meeting for all
Co-organizers cannot do the following:
· Create & manage breakout rooms
· View & download attendance reports
· Manage the meeting recording
· Edit the meeting invitation
· Remove or change the Organizer role
The “Only me” selection for the “Who can present?” meeting option has been updated to reflect that this will apply to “Only me and co-organizers.”
The “Only me” selection for the “Who can bypass the lobby?” meeting option has been updated to reflect that this will apply to “Only me and co-organizers.”
Usage of the co-organizer role for a meeting is optional. If users choose not to use the co-organizer feature, there will be no change.
What you need to do to prepare:
There is nothing you need to do. The “Choose co-organizers” meeting option will appear automatically on the meeting options page when the feature has rolled out.
Microsoft Purview
MC394983 — Microsoft Purview compliance portal: Default classification for content matching trainable classifiers (GA)
Microsoft 365 Roadmap ID 93266
We're introducing default classification for content matching trainable classifiers. This enables admins to view items that match trainable classifiers within Content explorer without first needing to create a policy.
When this will happen:
Rollout will begin in late July and is expected to be complete by end of August.
How this will affect your organization:
Content explorer, part of the data classification analytics capabilities in the Microsoft Purview compliance portal, shows a current snapshot of the items that have a sensitivity label, a retention label, or have been classified as a sensitive information type in your organization.
This feature adds default classification for content that matches the scope of any machine learning-based pre-trained or custom trainable classifiers that you have set up in your organization. In this way, admins with appropriate permissions will be able to identify which content aligns to which classifiers without needing to first set up a policy.
What you need to do to prepare:
Access trainable classifiers and Content explorer in the Microsoft Purview compliance portal:
· Microsoft Purview compliance portal for GCC cloud environments
· Microsoft Purview compliance portal for GCC-High cloud environments
· Microsoft Purview compliance portal for DoD cloud environments
Learn More:
Learn about trainable classifiers
· Get started with Content explorer
MC394842 — Microsoft Purview: Exact Data Match support for eDiscovery and Insider Risk Management
Microsoft 365 Roadmap ID 93286 and 93287
Microsoft Purview eDiscovery search queries and Microsoft Purview Insider Risk Management policy configuration will now support Exact Data Match (EDM) classification capabilities.
When this will happen:
Rollout will begin in mid-June and is expected to be complete by late June.
How this will affect your organization:
EDM-based classification enables organizations to create custom sensitive information types (SITs) that refer to exact values in a database of sensitive information. With this update, organizations will be able to include EDM SITs when searching for sensitive data using the Microsoft Purview eDiscovery search tools.
Additionally, organizations will be able to configure new or existing Insider Risk Management policies using EDM SITs, enabling more assertive control in specifying policies to identify risk indicators. The precise nature of EDM reduces risk of false positives, thus signals detected using EDM-based classification may be considered stronger indicators of risk. For example, a user gathering what appears to be customer personally identifiable information (PII) in a local drive may be considered a stronger signal of risky activity if the data is detected through EDM since it is far more likely to be customer PII than non-relevant PII or false positives.
What you need to do to prepare:
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, security and policy violations, and more. Insider Risk Management enables customers to create policies based on their own internal policies, governance, and organizational requirements. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can access the eDiscovery and Insider Risk Management solutions here:
· Microsoft Purview compliance portal for WW and GCC cloud environments
· Microsoft Purview compliance portal for GCC-High cloud environments
· Microsoft Purview compliance portal for DoD cloud environments
Learn More:
· Learn about exact data match based sensitive information types
· Microsoft Purview eDiscovery solutions
· Learn about insider risk management
MC393822 — Microsoft Purview Information Protection: Sensitivity labels now apply to modified documents (WXP on PC and Mac)
Microsoft 365 Roadmap ID 93209
Coming soon to public preview, default labeling policies can be applied to any supported document that a user edits, not just a new document. This update applies to Word, Excel, and PowerPoint documents on PC and Mac platforms.
When this will happen:
Rollout to public preview will begin in mid-June and is expected to be complete by late June.
How this will affect your organization:
If you’ve configured users for a default sensitivity label policy for Office documents, the label you chose will automatically be applied to Word, Excel, and PowerPoint documents that users create or modify. Previously, this only applied to new documents only.
Note: This functionality is now generally available for Word, Excel, and PowerPoint documents on the Web (MC305436), and with this update will extend to Word, Excel, and PowerPoint on PC and Mac.
What you need to do to prepare:
View sensitivity labels and their policies and settings in the Microsoft Purview compliance portal:
· Microsoft Purview compliance portal for WW and GCC cloud environments
· Microsoft Purview compliance portal for GCC-High cloud environments
· Microsoft Purview compliance portal for DoD cloud environments
Learn More:
· Get started with sensitivity labels
· Learn about the default labels and policies to protect your data
MC393184 — Records Management – Configure a record label to start unlocked for user-driven records declaration
Microsoft 365 Roadmap ID 88509
Coming soon to general availability, we are introducing a new capability to better manage the lifecycle of documents labeled as a record. This feature enables Records Management administrators to create retention labels that will mark contents in SharePoint and OneDrive as records but will not be “locked” (restricted for edits) until a user manually locks it. This will help customers who use automatic or default labeling of content which includes documents in a draft state which are not yet final and will need to become a locked record until they reach this stage of their lifecycle.
When this will happen:
Rollout will begin in late July and is expected to be complete by mid-August.
How this will affect your organization:
Records Management administrators can still choose to create record labels that start as a locked record, as has been the case until now. This new configuration of a record label can be set from the retention label creation experience that currently exists in the Records Management solution of the Microsoft Purview compliance portal.
Currently, items marked as a record in SharePoint or OneDrive are locked by default and users must unlock them to generate a new version before editing it. With this update, users can assign this new type of record label to content that will classify it with the appropriate retention label but will provide the flexibility to edit the content until they manually lock it (when the document is deemed to be finalized).
This change does not impact the restrictions applied to the file while the record is unlocked, and all behaviors documented as to what actions are allowed or blocked still apply.
What you need to do to prepare:
There is nothing you need to do to receive this feature and it will not affect your existing record labels. You may consider updating any training or reference material for your Records Management administrators and evaluate if you would like to use this new capability.
You can access the Records Management solution here:
· Microsoft Purview compliance portal for WW and GCC cloud environments
· Microsoft Purview compliance portal for GCC-High cloud environments
· Microsoft Purview compliance portal for DoD cloud environments
MC375741 — (Updated) Microsoft Purview compliance portal: Announcing data purge capabilities for Microsoft Teams content (preview)
Microsoft 365 Roadmap ID 88975
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
Coming to preview, this new feature extends data purge functionality to Microsoft Teams content to facilitate the purge of sensitive or misplaced data.
When this will happen:
Rollout to public preview will begin in mid-July (previously early May) and is expected to be complete by mid-August (previously early June).
How this will affect your organization:
Data spillage occurs when a confidential document is released into an untrusted environment. An eDiscovery case provides an effective way to manage data spillage investigations, so you can quickly assess the size and locations of the spillage, examine user activities around it, and then permanently purge the spilled data from the system.
With this update, you will be able to include Teams content in the scope of the data purge.
Note: Data purge can't delete items in a review set in eDiscovery (Premium) because the review set contains copies of items in the live service that are stored in an Azure Storage location. To delete items in a review set, you have to delete the eDiscovery (Premium) case that contains the review set. The purge signal will be available via the eDiscovery (Premium) Graph APIs, currently in public preview. For more information, see Close or delete an eDiscovery (Premium) case.
What you need to do to prepare:
Access the eDiscovery solution in the Microsoft Purview compliance portal:
· Microsoft Purview compliance portal for GCC cloud environments
· Microsoft Purview compliance portal for GCC-H cloud environments
· Microsoft Purview compliance portal for DoD cloud environments
Learn More:
· Search for and delete chat messages in Teams
MC321240 — Advanced eDiscovery: Updated timing for rollout of hold optimizations for U.S. gov clouds
Microsoft 365 Roadmap ID 70586
Updated June 14, 2022: We have updated the rollout timeline below. Thank you for your patience.
Timing update: We ask that you pardon our delay of this earlier planned feature release. We are now ready to proceed rolling out to Government environment. As previously announced in (MC256277 - Aug 2021), we're rolling out various service optimizations for Advanced eDiscovery, including service improvements for hold.
· Pre rollout (current): users see an error message when placing more than 1,000 mailboxes or 100 sites on hold which is the limit for eDiscovery holds.
· Post rollout: when placing more than 1,000 mailboxes or 100 sites on hold, the system will automatically scale the eDiscovery legal hold as needed.
Note: This is achieved as the system automatically adds data locations to multiple holds, instead of adding them to a single hold.
When this will happen:
Rollout will begin in early March and is expected to be complete by late July (previously early June).
How this will affect your organization:
The system will automatically scale eDiscovery legal holds as needed when you use the following Advanced eDiscovery custodian workflows:
· Advanced eDiscovery > Case > Data
o Add new custodians
o Import custodians
o Data source > Edit
o Data source > Release
· Microsoft Graph eDiscovery API (beta)
o Custodian resource type
Not all locations associated with a single custodian are guaranteed to be added to the same hold.
This release only impacts custodian workflows within an Advanced eDiscovery case.
· Creating query-based holds (Advanced eDiscovery > Hold > Create) will not automatically scale and will return same error as before due to hitting the limit.
· Adding non-custodial data locations (Advanced eDiscovery > Data sources > Add data locations) will not automatically scale and will return same error as before due to hitting the limit.
· This change does not affect holds in Core eDiscovery or the corresponding PowerShell cmdlets and will not impact any existing automation scripts that use PowerShell cmdlets.
All existing eDiscovery hold limits remain unchanged.
We are also changing naming schema in Advanced eDiscovery for auto-created legal holds:
· Existing naming convention for legal holds created by the system is: CustodianHold-{Case id}, for example, CustodianHold-b3d6b416-234f-47f8-b446-930df275be4e
· New naming convention for legal holds created by the system is: CustodianHold-{truncated case id}-{policy creation time in ticks}; for example, CustodianHold-b3d6b416234f47f8-0637541049083233486
What you need to do to prepare:
You might want to notify your users about this new capability and update your training and documentation as appropriate.
Access the Advanced eDiscovery solution in the Microsoft 365 compliance center:
· Microsoft 365 compliance center for GCC
· Microsoft 365 compliance center for GCC-High
· Microsoft 365 compliance center for DoD
Learn More:
· Advanced eDiscovery hold limits
· Importing custodians to an Advanced eDiscovery case
· Automate Advanced eDiscovery legal hold workflows that involve large scale cases using Microsoft Graph eDiscovery API
Security
MC395210 — Microsoft Defender for Office 365: Recipient Block Using Tenant Allow/Block List Senders
Microsoft 365 Roadmap ID 93363
Today, the Tenant Allow/block List is used to prevent users from receiving email from selected senders using the sender block. However, users are still able to send email to that email address or domain as recipient. With this update, the Tenant Allow/block List will be extended to prevent users from sending emails to these email addresses and domains that are added or part of the sender block list.
When this will happen:
The rollout should start around mid-July and should be completed by mid-August.
How this will affect your organization:
This won't apply to intra-organizational sender email addresses. It will apply to existing sender blocks and any new sender blocks which are added to the Tenant Allow/Block List.
If a user tries to send an email to these blocked senders, they will get the following NDR:
"- 5.7.1 Your message can't be delivered because one or more recipients are blocked by your organization’s tenant allow/block list policy"
What you need to do to prepare:
We advise you to cross check the existing sender block in Tenant Allow/Block list to ensure that it does not affect any sender that you want your users to send emails to, but can't because of this change.
MC394261 — Option to automatically allow Spoofing and Impersonation related message directly using Admin Submissions
Microsoft 365 Roadmap ID 93366
Today security administrators can use the Submissions page in the Microsoft 365 Defender portal to submit email messages, URLs, and attachments to Microsoft for scanning
We are enhancing the email submission capability with an option to automatically allow Spoofing and Impersonation related emails from senders/infrastructure that were classified as legitimate by the admin, despite being initially blocked by the system. This will help mitigate false positives while the system continues to learn.
When this will happen:
This feature has started rolling out and the rollout will complete by late June 2022
How this will affect your organization:
This enhances your ability to mitigate spoofing and impersonation related messages that you determine as False Positives.
You can tackle such False Positives easily while making admin submission by toggling "Allow emails with similar attributes."
The allowed spoof sender domain pair entries will be created under Tenant allow block list - spoofing found at https://security.microsoft.com/tenantAllowBlockList.
The allowed impersonated domains or user entries will be created under the respective Anti Phishing Policy under https://security.microsoft.com/antiphishing.
Note: Expiry date and notes won't apply to spoof and impersonation allows created from this process.
What you need to do to prepare:
You need to be informed of this change so that you can leverage this capability.
MC387682 — New opt-in setting for Microsoft Defender for Identity
Over the last few months, the experiences and functions of Microsoft Defender for Identity have been made available in Microsoft’s extended detection and response (XDR) platform, Microsoft 365 Defender. Merging identity data and functions into this XDR experience is a valuable addition to a security teams capabilities, with identity providing important context to detection logic and investigation potential.
Since all major Microsoft Defender for Identity features have now been made available in Microsoft 365 Defender portal; we are introducing a portal redirection setting which will be available by navigating from the Microsoft 365 Defender homepage (security.microsoft.com) to Settings -> Identities -> General -> Portal redirection
Enabling this option will automatically redirect any requests to the standalone Defender for Identity portal (portal.atp.azure.com) to Microsoft 365 Defender along with any direct links to its functionality.
If your organization does not use Microsoft Defender for Identity, you may disregard the below message.
Key Points:
· Timing: Starting from June 1st, 2022, Microsoft will make the settings available in tenants globally. The setting may take a few days to appear in your console after this date.
· Action: Start using the Microsoft 365 Defender portal for Microsoft Defender for Identity. Microsoft recommends enabling redirection and to begin using Microsoft 365 Defender as the single place for operating and administering Defender for Identity.
· Next steps: Starting from January 2023, we will enable this opt-in settings automatically for every tenant, however, organizations can still manually opt-out by switching it back.
How will this affect your organization
By enabling this redirection experience, any requests to the standalone Defender for Identity portal (portal.atp.azure.com) will be automatically redirected to Microsoft 365 Defender (security.microsoft.com). This includes any requests originating from alerting emails or notifications.
What do you need to do to prepare
Ensure your security teams are familiar with Defender for Identity’s features and settings as they are represented in Microsoft 365 Defender. If your security teams need help, please direct them to the updated documentation available here.
MC362283 — (Updated) Updates to the Zero-hour auto purge (ZAP) alerts
Microsoft 365 Roadmap ID 93206
Updated June 23, 2022: We have updated the rollout timeline below. Thank you for your patience.
We will be updating the current zero-hour auto purge (ZAP) alerts and introduce a new ZAP alert that will notify you if a message has not been removed by ZAP.
Updates to the ZAP alerts will include:
· Scoping the success ZAP alerts for only ZAP related scenarios. You will no longer be alerted as part of the ZAP alert for Dynamic Delivery scenarios.
· A new failure ZAP alert is being introduced. You will receive an alert when a message was not successfully removed from the mailbox. Manual action will be required to remediate the message. The alert will be correlated and linked to both Automated Investigation and Response (AIR) and Incidents. The alert will be on by default and can be configured in alert policies.
When this will happen:
We expect these updates to roll out in late June (previously mid-June) and expect to be complete by mid-August (previously mid-July).
How this will affect your organization:
Due to these new changes, you can expect a change in the volume of the successful ZAP alerts. The new ZAP failure alert will be on by default and can be configured in the alert policy settings. You can review both default alerts in the portal. However, if you’re exporting these alerts into external systems, you will need to include the new alert generated by the new policy.
What can you do to prepare:
Review the following resources below to Learn More:
· Microsoft 365 alert policies
· Zero-hour auto purge in Microsoft Defender for Office 365
MC341683 — (Updated) Upcoming changes to Office 365 Management API events for Microsoft Defender for Office 365
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
In alignment with the permanent redirection of the Office 365 Security & Compliance Center (SCC), and as previously mentioned (MC320940 - Feb 2022), we will be updating the deeplinks for Microsoft Defender for Office 365 events in Office 365 management API and the Unified Audit logs.
When this will happen:
We will begin rolling this out in late June (previously late May) and expect to complete rollout late July (previously late June).
How this will affect your organization:
As part of this change, deeplinks pointing to Office 365 Security & Compliance Center portal (protection.office.com) will start pointing to Microsoft 365 Defender portal (security.microsoft.com).
Note: There will be no change to any existing data attributes, recordtype or data audit structure. The only change that will happen is that the deeplink will start pointing to entities in security portal as compared to the Office 365 Security & Compliance Center portal.
This change will impact events with the following Recordtypes:
· 28 - ThreatIntelligence
· 40 - SecurityComplianceAlerts (Microsoft Defender for Office Plan 2 and above)
· 47 - ThreatIntelligenceAtpContent
· 64 - AirInvestigation
Example: The field EventDeepLink for Records with Recordtype 28 (ThreatIntelligence) would start pointing to security.microsoft.com, instead of protection.office.com. Once this change is implemented, the deeplinks which were earlier pointing to the Office 365 Security and Compliance portal (protection.office.com), will start pointing to the Microsoft 365 Defender portal (security.microsoft.com). There is no other change to the API itself, as well as the different data attributes that are published today.
What you need to do to prepare:
You should evaluate your use of the event deeplinks and make sure that you update your playbooks and workflows to work within the Microsoft 365 Defender portal. If you are still working fully or partially out of the Office 365 Security & Compliance center, we recommend that you plan your transition, to avoid interrupted experiences.
Learn More:
· Microsoft Defender for Office 365 and Threat Investigation and Response schema
MC333945 — (Updated) Updates to Threat Explorer and Email entity page
Updated June 2, 2022: We have updated the rollout timeline below. Thank you for your patience.
As part of Hunting improvements, we are making updates to the Email entity page, and Threat Explorer and Real-Time Detections. These updates should help provide additional data points and context for security analysts. These updates include:
Updates to Email entity Page will include:
· A section around Threat Detection Details which will contain information around Threat, the corresponding detection technology and if the detection ran into any additional context.
· We will also light up additional email attributes like To, CC, Distribution list, Client information and forwarding (indicating if email forwarding was involved)
· Override information would include the Primary override and Source (Primary override is the override which impacted the delivery of the email) as well as any additional overrides that were applicable to the email.
· If a URL or a File was allowed due to a tenant policy like Tenant Allow/Block list, then that information would be shown in the entity views as well.
Updates to Threat Explorer will include:
· Threat Explorer filters around System Override and System Override source would be renamed to Primary Override and Primary Override source to indicate the specific overrides which impacted the delivery of the email. This will help the analyst to locate malicious emails delivered due to potential config gaps, as well as identifying any tenant or user level configurations which have impacted the delivery of an email.
· In addition to the name updates for the above 2 filters, we will also be lighting up new filters to cover scenarios like if an email contained forwarding or not.
When this will happen:
We expect these updates to begin rolling out in early March and expect the rollout to be completed by late June (previously late May).
How this will affect your organization:
As part of this change, we are updating the name System Overrides and System Overrode source filters to Primary override and Primary override source. Due to these new changes, you should re-evaluate your saved and tracked queries for these specific filters only.
What you need to do to prepare:
No specific action is required as you will start seeing the data and the new filters automatically once the roll out has been completed to your tenant. You should evaluate your Saved/Tracked queries if they contained any references to System Override and System Overrides Source.
Exchange Online
MC395211 — Outlook to block new attachment file types to improve security
As we continually assess to improve security, we are adding additional attachment file types to the list of BlockedFileTypes.
When this will happen:
We will begin rolling out early July and expect to complete by late July.
How this will affect your organization:
The newly blocked file types are rarely used, so most organizations will not be affected by the change. However, if your users are sending and receiving affected attachments, they will report that they are no longer able to download them.
What you need to do to prepare:
There are several ways to send and receive a blocked file. You can save the file to the cloud and send a link to the file, use a file compression utility like WinZip, or even rename the file with another extension, then have your recipient change the name back to the original name after they receive the file.
What file extensions will be added to the BlockedFileTypes list with this change?
Outlook Win32: ".cab",
Outlook on Web: "application", "bgi", "img", ".iso", "cab"
New Outlook on Mac, Outlook Android, Outlook iOS: ".appref-ms", ".cdxml", ".mht", .mhtml", ".pssc", ".udl", ".wsb" ".cab"
Where is the full list of Outlook client block file types?
Outlook Win32: Blocked attachments in Outlook (microsoft.com)
Outlook on Web: Changes to File Types Blocked in Outlook on the web - Microsoft Tech Community
New Outlook on Mac, Outlook Android, Outlook iOS
MC393818 — Add DKIM Domain in Sending Infrastructure for Tenant Allow Block Lists-Spoofing
Microsoft 365 Roadmap ID 93359
For Microsoft Defender for Office 365 and Exchange Online Protection, we are adding support for providing "DKIM verified domain" as the "Sending Infrastructure" within Tenant allow-block lists-Spoofing, so that Security Administrators can better manage Anti-Spoofing activity and override it based on Spoof Intelligence. Currently, what is supported in this field is either the domain from DNS PTR record or /24 IP Subnet. Additionally, being able to specify a 'DKIM verified domain' will help serve scenarios where shared infrastructure provider services are used for sending emails. Since the DKIM domain is unique to each tenant and if it passes verification even when other authentication signals fail, if desired for legitimate business reasons, a spoofed message can still be allowed instead of being blocked.
When this will happen:
Standard: Rollout will begin in early July and is expected to be completed by late August.
Gov Cloud: Rollout will begin in early September and is expected to be completed by late September.
How this will affect your organization:
Once this change is completed, Security Administrators will be able to specify a verified DKIM domain within the Sending Infrastructure field using Tenant allow block lists-Spoofing in order to allow/block a spoofed domain pair using DKIM domain.
What you need to do to prepare:
There is nothing you need to do to prepare for this change. You may want to notify your users about this change and update your training and documentation as appropriate.
MC390410 — Tenant Trusted ARC Sealers for Email Authentication
Microsoft 365 Roadmap ID 85684
Authenticated Received Chain (ARC) is an email authentication mechanism that helps preserve authentication results across intermediaries. Email authentication mechanisms like SPF, DKIM, DMARC are used to verify the senders of emails for the safety of mail recipients, but some legitimate services may make changes to the email between the send and receipt. This intervention from legitimate services may accidentally cause the message to fail email authentication at subsequent hops.
The ARC trusted sealers feature lets admins add trusted intermediaries in the Microsoft 365 Defender portal. This allows Microsoft to honor ARC signatures from your list of trusted intermediaries, to help authenticate the message.
When this will happen:
Tenant Trusted ARC Sealer support will begin to roll out in Microsoft 365 Defender in early June and is expected to be completed by early July.
How this will affect your organization:
If you have had third-party service before Office 365 that modifies the email content and supports ARC, administrators can add these services as a trusted ARC sealers for your tenant. This will help messages pass email authentication checks and prevent these messages from being treated as spoof due to authentication failures.
As we are rolling out the new Email Authentication Settings page gradually, we are also moving DKIM to the DKIM tab in the Email Authentication Settings page.
During the migration, you may see two entries of the DKIM page.
What you need to do to prepare:
Identify any third-parties your organization has located before email is delivered to your Office 365 tenant and also modify content. Check if this service supports ARC and add the ARC sealer to your tenants ARC Sealer trusted domains.
Learn More:
· Make A List of Trusted ARC Senders to Trust Legitimate Indirect Mailflows
· Improving “Defense in Depth” with Trusted ARC Sealers for Microsoft Defender for Office 365
MC389620 — Consistently block delegates or shared mailbox members from accessing protected messages in Outlook
Outlook will provide consistent access control on protected emails (Protected by MIP Sensitivity labels, or RMS protected emails) for Microsoft 365 delegates and shared mailbox members. For delegates or shared mailbox members, when they have full access of the owner's mailbox but are not allowed to read encrypted email, Outlook will have a new cmdlet setting to block the owner's protected email access which covers ad-hoc encrypted email as well as email with protected MIP sensitivity labels.
Microsoft 365 Roadmap ID 88888
When this will happen:
· Preview: We will roll out the preview in early June
· Standard: We will begin rolling out in early July and expect to complete by late August
How this will affect your organization:
Based on customer feedback, we are introducing new Get/Set/Remove-MailboxIRMAcess cmdlets that provide admins with more granular access control of encrypted content, including in scenarios where delegates or shared mailbox members have FullAccess to the shared mailbox
We will introduce new Get/Set/Remove cmdlets which tenant admins to use to limit delegate access to RMS messages at mailbox level.
· Check who is blocked from accessing mailbox owner’s encrypted messages:
Get-MailboxIRMAccess
-Identity <MailboxIdParameter> -User <SecurityPrincipalIdParameter>
· Blocked a user from reading encrypted messages in a shared or delegated mailbox:
Set-MailboxIRMAccess
-Identity <MalboxIdParameter> -User <SecurityPrincipalIdParameter>
-AccessLevel <Block>
· Remove a user from the block list and allowing them to read encrypted mail:
Remove-MailboxIRMAccess
-Identity <MalboxIdParameter> -User <SecurityPrincipalIdParameter>
After any of the above mailbox settings are changed, the Outlook client must be restarted.
Parameter definitions:
· -Identity: The target mailbox. You can use any value that uniquely identifies the mailbox.
· -AccessLevel: Specifies what delegates can do with IRM-protected messages in the specified mailbox. Currently we only support “Block.”
· -User: Specifies the delegate or shared mailbox member who is blocked from reading IRM-protected messages in the mailbox or shared mailbox. The user’s login ID must be used.
Once delegate is blocked to view the owner mailbox's protected email, the delegate will see the following when they trying to open the protected mails
Or Shared mailbox member is blocked to view the mailbox's protected email, the login user will see the following when they trying to open the protected emails.
What you need to do to prepare:
If you do not do any cmdlet settings, there will be no impact on your existing delegate or shared mailbox protected message reading experience. But if you choose to block some of the full access delegate or shared mailbox members to read the protected email, you could configure through the cmdlet above.
MC388229 — Microsoft Defender for Office 365 Preset Security Policies
Microsoft 365 Roadmap ID 93262
We are making enhancements to Microsoft Defender for Office 365 preset security policies. It will provide a way to apply the policy to the entire organization and be able to optionally configure a list of custom users and custom domains to protect against impersonation attacks.
Impersonation protection applies to Microsoft Defender for Office 365 Plan 1 and Plan 2 & Microsoft 365 Defender
When this will happen:
Standard: Rollout will begin in late June and be completed by late September
GCC/GCC-H/DoD: Rollout will begin in late August and be completed by late November
How this will affect your organization:
Security Admins and SecOps teams will be able to apply policy settings to all users of your organization using preset strict/standard policies, however, you can still select specific recipients. SecOps teams will be able to configure custom users and custom domains to protect against impersonation attacks. You will be able to provide a list of trusted senders and trusted domains that you want to allow to be impersonated and it won’t be flagged from such impersonated senders/domains.
Note: Within preset strict/standard policies, the impersonation protections for custom users and domains have always been available and turned ON until now. After this change, when there are custom users and domains added in the list, impersonation protection will be applied to incoming messages and will be quarantined.
What you need to do to prepare:
Review your existing Anti-Phishing policies within threat policies and consider creating/updating preset policies with custom users and/or custom domains to protect against impersonation attacks. We recommend updating your necessary training documents accordingly.
Learn More:
· Preset Security Policies in EOP and Microsoft Defender for Office 365
· Recommended Settings for EOP and Microsoft Defender for Office 365 Security
· Configurable Impersonation Protection and Scope for Preset Security Policies
MC385450 — (Updated) Advanced Room Finder Coming to U.S. Government Clouds
Microsoft 365 Roadmap ID 93293
Updated June 7, 2022: We have updated the content below with additional resources. Thank you for your patience.
Room Finder is a web-based feature that you can set up for your users to find available meeting rooms and workspaces that are suitable for their use. Every meeting room and workspace must be set up in Exchange Online and added to a room list for it to display properly in Room Finder.
The Advanced Room Finder enables users to browse or search for Buildings/Room Lists by city and then filter by room type, capacity, floor and features.
When this will happen:
The Advanced Room Finder is currently available in WWMT. It will begin rolling out to U.S. Government Clouds in early June and be completely rolled out by late June.
How this will affect your organization:
Users will be able to browse and search for Buildings/Room Lists and then filter for rooms in a Building/Room List by type, capacity, floor and features.
What you need to do to prepare:
Admins should ensure Room and Workspaces Mailbox properties are set to ensure users can browse and filter, especially location and feature related properties. The Advanced Room Finder currently uses: City, Capacity, Floor, AudioDeviceName, VideoDeviceName, DisplayDeviceName, IsWheelChairAccessible, and Tags.
Learn More:
· How to Configure the New Room Finder in Outlook
· Use the Scheduling Assistant and Room Finder for Meetings in Outlook
· Configure rooms and workspaces for Room Finder in Outlook
MC384330 — (Updated) Microsoft Defender for Office 365: Password protected download of quarantined messages
Microsoft 365 Roadmap ID 93305
Updated June 16, 2022: We have updated the rollout timeline below. Thank you for your patience.
With this change we are giving the ability to password protects items they download from quarantine. We want users to be confident that the items they are downloading to their systems will not execute involuntarily without their consent, and this capability will allow them to safely transport the items to external analysis tools.
When this will happen:
· Standard: will begin rolling out in early July (previously mid-June) and be completed by mid-July (previously late June).
· Government: will begin rolling out in late July (previously early July) and be completed by early August (previously late July).
How this will affect your organization:
This new feature will enable tenant Admins and users to download quarantined messages and embed a password in those downloaded items.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
MC383901 — (Updated) Microsoft Defender for Office 365: Hourly option for notifications
Microsoft 365 Roadmap ID 93304
Updated June 21, 2022: We have updated the rollout timeline below. Thank you for your patience.
We are adding a new hourly option to end user quarantine notifications, which will allow users to rely on receiving prompt notifications about quarantined items when appropriate. With this feature, users will be updated frequently once new items land in their quarantine folder.
When this will happen:
Standard: will begin rolling out in early September (previously late July and be completed by mid-September (previously mid-August).
Government: will begin rolling out in late September (previously late August) and be completed by early October (previously mid-September).
How this will affect your organization:
Using the quarantine policy, Admins will be able to configure an hourly notification frequency for users in their organization.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
MC383875 — (Updated) Microsoft Defender for Office 365: updates to quarantine folder storage
Microsoft 365 Roadmap ID 93302
Updated June 7, 2022: We have updated the content below for clarity. Thank you for your feedback.
Microsoft Defender for Office 365 is making some changes to quarantine folder storage. The experience for users will remain the same and users can leverage the delete action to maintain the storage folder for their quarantined messages.
When this will happen:
Standard: will begin rolling out in mid-June and be completed by late June.
Government: will begin rolling out in early July and be completed by late July.
How this will affect your organization:
Non delivery report (NDR):
In the case that a user’s quarantine storage is full, new incoming messages routed to quarantine will be rejected and an NDR will be generated for those messages.
In the case of Zero hour Auto Purge, where malicious items need to be zapped from inbox to quarantine but there is no space, these messages will be instead, added to the junk mail folder.
Note: When there is a False positive Zero hour Auto Purge, messages wrongly moved to the Junk mail folder can be added back to their original location.
New hard delete experience:
Previously, when messages were deleted by users from quarantine, those deleted messages could still be retrievable within a 30-day period after deletion was made. To help users better manage their storage, we will be introducing a hard delete experience whereby once the messages are hard deleted, they can’t be recovered.
Note: End users will only be able to delete quarantine messages that their Administrators has given them access to through the quarantine policy.
What you need to do to prepare:
The goal for this communication is mostly for informational awareness. You may consider updating your training and documentation as appropriate.
MC373880 — (Updated) Migrating the Safe Links Block List to Tenant Allow Block List
Updated June 14, 2022: At the beginning of June, we attempted to migrate all entries on the Safe Links Block List to the Tenant Allow/Block List. Entries that were successfully migrated do not require any additional action. Entries that were unable to be migrated will require manual intervention. In the coming weeks tenants will be able to review and take action on the entries that were unable to be migrated.
Note: Any entry migrated from the Safe Links Block List to the Tenant Allow/Block List will adopt the behavior of TABL. This means that any message with the URL present will be moved to Quarantine. If deleting an already migrated entry from TABL, it needs to be removed from BlockURLS to avoid migration.
As a reminder beginning in June tenants will no longer have the ability to add to the Safe Links Block List in the Global Setting menu. Then we will attempt to migrate the Safe Links Block List to the Tenant Allow Block List (TABL) on behalf of the organization. Any entries that are unable to be successfully migrated, they will be marked as such in the Block List and organizations will have the ability to take action as needed beginning in July.
Another update will be sent closer to July as a reminder for tenants to review the migration status of the Block List. Beginning in June organizations will no longer have the ability to add to the Safe Links Block List in the Global Setting menu. Following this, we will attempt to migrate the Safe Links Block List to the Tenant Allow Block List (TABL) on behalf of the organization. For any entries that we are unable to migrate, they will be marked as such in the Block List and organizations will have the ability to take action as needed.
When this will happen:
· Early June: Organizations will no longer have the ability to add to the URL/Domain entries to the Safe Links Block List in the Global Settings flyout and we will attempt to migrate all the entries in an organization's Safe Links Block List to TABL on their behalf
· Mid-June through November: Organizations will have the ability review entries that were not able to be migrated and resolve the issue(s)
· December: The Safe Links Block List will be retired
How this will affect your organization:
Organizations who are utilizing the Safe Links Block List will need to review the list to ensure all entries were migrated successfully. Any entries that are unable to be migrated will be marked as such and organizations will have the ability to resolve that entry, at which point migration will run again.
Organizations will use the Tenant Allow Block List to manage URL/Domain blocks moving forward.
What you need to do to prepare:
In June an update to this Message center post will be sent notifying organizations that the first migration has been completed and they will need to review their Safe Links Block Lists for potential actions.
MC365786 — (Updated) Configuration Change in Name parameter for Exchange Online
Updated June 28, 2022: Based on customer feedback, we have made the decision to provide additional time for organizations to prepare for the change. We have updated the rollout timeline below. Thank you for your feedback.
We're making some changes to the way Name parameter is being set in Exchange Online. We will be making a change to utilize unique ExternalDirectoryObjectId (EDOID) in the place of Name parameter in Exchange Online only.
When this will happen:
We will begin rolling this out in early September (previously late June) and expect to complete late October (previously late August).
How this impacts your organization:
After this change administrators may no longer be able to see subsequent CN value change in Exchange on-premises to be reflected in the object’s Name property in Exchange Online.
The updated naming logic would take effect only during new user creation. Existing users won’t get impacted in any way.
Please note that since we will start using EDOID as Name in Exchange Online, we shall stop allowing changes in CN to reflect in Name property in Exchange Online for all users (both new and existing).
What you can do to prepare:
We recommend that Administrators evaluate any scripts or other automation that may rely on the Name property and update them accordingly.
For additional details please refer Change in naming convention of user’s Name parameter.
MC342072 — (Updated) Safe Links Global Settings Migrated to Custom Policies
Updated June 28, 2022: As a reminder within the next week we will begin enforcing the policy settings for "Use Safe Links in Office 365 Apps", "Track Clicks", and "AllowClickThrough" as you have it configured in the custom policies under Safe Links.
Beginning in June we will begin enforcing the policy settings for "Use Safe Links in Office 365 Apps", "Track Clicks", and "AllowClickThrough" as you have it configured in the custom policies under Safe Links. If you have already reviewed your custom policies and made configuration changes no action is required. As a reminder the default value for this policy is "On" and any users, domains, or groups specified under a policy will be covered. Part of this change will include deprecating the "Use Safe Links in Office 365 Apps" and subsequent settings from the Global Settings menu.
Customers that have "Use Safe Links in Office 365 Apps" turned on, will need to create a custom policy in order to maintain safe links protections in Office 365 Apps. This change was planned to be deployed in conjunction with the completion of the Built-In Protection. However, the two changes will reach customers at differing times. Beginning mid-April tenants will see the policy setting Use Safe Links in Office 365 Apps in both the Global Settings menu and Custom Policy. As a reminder in the future tenants will not be able to manage this setting in the Global Settings menu.
Only the policy setting "Use Safe Links in Office 365 Apps" configured in the Global Setting menu will be enforced at this time. Another update will be sent prior to removing the policy setting from the Global Setting menu."
To create a more consistent user experience across all policies in Microsoft Defender for Office portal the following Safe Links policy attributes will be migrated from the Global Settings flyout to the custom policy settings.
Note: Use Safe Links in Office 365 Apps
· Do Not Track when users click protected links in Office 365 Apps
· Do not let users click through the Original URL in Office 365 Apps
When this will happen:
We will begin rolling this out in early May and expect to complete rollout late June.
How this will affect your organization:
For already existing user scoped properties (Track Clicks and Allow Click Through), this change will not override user scoped settings with current tenant wide settings. This means these values will not change for any existing custom policies.
For customers that have "Use Safe Links in Office 365 Apps" turned on, after the migration this tenant level setting will be enabled by default as part of built-in protection for all users, groups, or domains not named as part of a custom policy. Customers can manage the properties “EnableSafeLinksforOffice”, "Track Clicks", and "Allow Click Through" in custom policies going forward.
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
Learn More:
· Preset security policies in EOP and Microsoft Defender for Office 365
· Safe Links in Microsoft Defender for Office 365
Microsoft 365
MC394931 — Microsoft 365 admin center: Reports in the Admin Center – API available to manage user, group, and site names
Microsoft 365 Roadmap ID 93313
Microsoft is releasing an API that helps Global Administrators change how user, group, and site names are displayed in the Microsoft 365 admin center based on their organization’s privacy practices without having to manually change the setting in Org Settings -> Reports. User, group and site names are concealed by default. When this setting is changed, administrative roles and the report reader role will be able to see identifiable user level information. Global reader and Usage Summary Reports Reader roles will not have access to identifiable user information, regardless of the setting chosen. Showing identifiable user information is a logged event in the Microsoft 365 Compliance Center Audit log.
When this will happen:
We will begin rolling out late June and expect to complete late July.
How this will affect your organization:
The update admin report setting API can be used with Global Administrator permissions. More information on the API can be found here Working with Microsoft 365 usage reports in Microsoft Graph Graph API names are update admin report settings and get admin report settings.
NOTE: This change affects the following products and APIs, and will help companies support their local privacy laws:
· Microsoft 365 Reports in the Microsoft 365 admin center
· Microsoft 365 usage reports in Microsoft Graph
· Microsoft Teams analytics and reporting in the Microsoft Teams admin center
· The reportRoot: getSharePointSiteUsageDetail API (1.0 and beta) for SharePoint site detail
What you need to do to prepare:
There is no specific action required, but you may want to update your documentation as needed.
MC394517 — Run team-owned Office Scripts in Excel for the web
Microsoft 365 Roadmap ID 93767
Office Scripts is an automation feature set in Excel for the web. With this update, users can save their scripts to a SharePoint site, in addition to their OneDrive for Business.
Note: External network calls made within a script that is saved to a SharePoint site are not supported at this time. If any SharePoint-based scripts do contain an external call, the script will return an error when ran and the external call will not be made.
When this will happen:
This change will begin rolling out in late July and will be completed by late August.
How this will affect your organization:
Before this feature update, when a user created an Office Script, their script was saved to their OneDrive for Business, and the owner of the script was the only user who had edit permissions to that script. Now, team members can easily collaborate, edit, view, and run team-owned scripts on their Excel workbooks. Additionally, because script files saved to a SharePoint site follow SharePoint file retention policies, these scripts can be used even after the creator leaves the organization.
Note: SharePoint support for Office Scripts is continuing to be rolled out. You may not see the feature right away.
What you need to do to prepare:
If you do not want users to be able to save their scripts to a SharePoint site so that others can view and run their scripts, please visit the Office Scripts admin pane to disable the feature by late July.
Learn More:
· Manage Office Script settings
· Office Scripts File Storage and Ownership
MC394516 — We're bringing Microsoft Search to GCC High
Microsoft 365 Roadmap ID 93249
Beginning late July 2022, we are bringing Microsoft Search to GCC High. This includes:
· Organization-wide Search via the Search Box navigation header in SharePoint and OneDrive, Office.com, and on Microsoft Search in Bing
· Search suggestions based on Files and Sites in GCCH for Office.com, SharePoint and OneDrive; and on Bookmarks, Q&A, and history in GCCH on Microsoft Search in Bing
· People Answer and Customizable Bookmarks and Q&A Answers
· Search and Intelligence Admin Center
· Search Usage Analytics enabled in the Search and Intelligence Admin Center
When this will happen:
We expect to begin rolling out Microsoft Search to GCC High customers in late July 2022, and we expect to finish in August 2022.
How this will affect your organization:
Microsoft Search brings work answers and search results to familiar search experiences, like SharePoint Online, Office.com, and Bing.
End users will be able to enter search queries into the Search Box in SharePoint and One Drive and Office.com and get organization-wide search results. They'll see People, Bookmarks, and Q&A Answers in the search results.
When enabled, users who go to Bing.com and sign in with a valid work account can easily and securely find the work information they need with Microsoft Search in Bing. For GCC High customers, Microsoft Search in Bing is off by default. Search Admins can turn on Microsoft Search in Bing in the Admin Center (Settings > Search & intelligence settings > Configurations > Microsoft Search in Bing settings). Choose Change settings and turn on Allow your organization to use Microsoft Search in Bing.
Search Admins will be able to customize Bookmarks and Q&A Answers via the Search & Intelligence Admin Center. Search Admins will find Search Usage Analytics in the Search & Intelligence Admin Center.
What you need to do to prepare:
For GCC High customers, Microsoft Search in Bing is off by default.
· Search Admins can turn on Microsoft Search in Bing in the Admin Center (Settings > Search & Intelligence settings > Configurations > Microsoft Search in Bing settings).
· Choose Change settings and turn on Allow your organization to use Microsoft Search in Bing.
Instructions to turn on Microsoft Search in Bing
Learn more about Microsoft Search and customizing Answers here
Find information about Microsoft Search in US Government environments here
This documentation will be updated to reflect the upcoming changes during the release process.
MC394513 — Announcing retirement of the Hide option in the Power BI service
The Power BI service gives you the option to Hide items from the different sections of your Home canvas: Favorites + frequents, Featured, Recents, Shared with me, and My apps. While giving you the ability to add your previously hidden content back to your Power BI Homepage at any time.
Support for the above will be removed and the option to Hide any of your Power BI content from your Homepage will be retired.
When this will happen:
The capability to Hide any of your content through the Power BI service will be retired starting mid-July.
How this will affect your organization:
You are receiving this message as a warning that the option to Hide your content will no longer be supported. With the retirement of the Hide option, you will no longer be able to hide any of your Power BI content.
· If you have hidden any of your Power BI content prior to retirement, that content will stay hidden, and you will have access to your hidden content within your settings pane. But you will not be able to hide any Power BI content in the future.
What you need to do to prepare:
The capability to Hide any of your Power BI content is being retired, now would be a good time to confirm that you can view your previously hidden content within your settings pane in case you would like access to them in the future.
Note: After the retirement of the Hide option, if you decide to unhide any of your content you will not be able to hide it again.
MC393185 — Reminder: Microsoft Office default change – Blocking VBA macros in files from the internet
Microsoft 365 Roadmap ID 88883
VBA macros are a common way for malicious actors to gain access to deploy malware and ransomware. As a reminder (MC322553 Feb '22), to help improve security, we are changing the behavior of Office applications to now block macros in files from the internet. Learn more in this blog post.
This change only affects Office on devices running Windows and only affects the following applications: Access, Excel, PowerPoint, Visio, and Word.
Key points:
· Timing: The change has been available in Version 2203, Current Channel (Preview) and it will complete the rolling out for the entire Current Channel soon. Later, the change will be available in the other update channels, such as Monthly Enterprise Channel, and Semi-Annual Enterprise Channel.
· At a future date to be determined, we also plan to make this change to Office LTSC, Office 2021, Office 2019, Office 2016, and Office 2013.
· Action: Review and assess impact
How this will affect your organization:
Previously, it was possible for end users to enable these macros by simply clicking a button on the Trust bar.
Now, with this change, once a user opens an attachment or downloads from the internet an untrusted Office file containing macros, a message bar displays a Security Risk that the file contains VBA macros obtained from the internet with a Learn More button.
The Learn More button goes to an article for end users and information workers that contains information about the security risk of bad actors using macros, safe practices to prevent phishing and malware, and instructions on how to enable these macros (if absolutely needed).
What you need to do to prepare:
Enterprises should evaluate their use of macros in files obtained from the internet to determine how this new default behavior will affect their users.
To learn more about how to get ready for this change and recommendations for managing VBA macros in Office files, read this article for Office admins.
MC392478 — IE11 desktop application has retired and is out of support as of June 15, 2022 (non-LTSC, non-Server)
As previously communicated, the Internet Explorer 11 (IE11) desktop application has retired and is out of support as of today, June 15, 2022. Following industry best practices, the IE desktop application will be progressively redirected to Microsoft Edge over the next few months and after will ultimately be permanently disabled via a future Windows Update to help ensure a smooth retirement.
If you have not set up IE mode in Microsoft Edge, we recommend doing so as soon as possible to help avoid business disruption.
· If you’ve already set up IE mode, follow these final steps.
· If you’re beginning your transition, see the steps below.
Note: The IE11 desktop application is not available on Windows 11. To continue using legacy IE-based sites and apps on Windows 11, IE mode in Microsoft Edge must be configured before deploying Windows 11.
IE11 desktop application
· Timing: The IE11 desktop application has retired and is out of support as of June 15, 2022.
o The now out-of-support IE11 desktop application will be progressively redirected to the supported Microsoft Edge browser over the next few months during a redirection phase and, after this phase, will be permanently disabled via a future Windows Update.
o Windows 10 LTSC and Server are not affected. For a full list of what is in scope for retirement, see the FAQ.
o IE11 is not available on Windows 11.
· Action:
o To continue using a supported browser, transition to Microsoft Edge.
o To continue using legacy IE-based sites and apps in Windows 10 and Windows 11, you will need to configure those sites and apps to open in Microsoft Edge using Internet Explorer mode.
§ You can use IE driver for automatic, end-to-end site testing in IE mode.
§ Use policy to disable the IE11 application and ensure you’re prepared for retirement.
How this will affect your organization:
The Internet Explorer 11 (IE11) desktop application has retired and is out of support as of today, June 15, 2022.
IE is being retired in two phases to ensure a quality-driven retirement. During the first phase, the redirection phase, devices will be progressively redirected from IE to Microsoft Edge over the next few months after June 15, 2022. Following industry best practices, this progressive redirection will be quality-driven to ensure a smooth IE11 retirement for you and your organization. To minimize the level of potential business disruption within an organization at one time, not all devices will be redirected at the same time. This approach is designed so that you can quickly identify and resolve any potential issues, such as missed sites, before all devices within your organization are redirected. The intent is for the redirection phase for all devices with Windows platforms that are in-scope for IE retirement to be complete in the next few months.
Note: Windows Updates are not used to redirect devices during the redirection phase. We do not recommend skipping Windows Updates as they contain critical operating system security patches.
The second phase of retirement is the Windows Update phase. After the redirection phase completes, IE will be permanently disabled through a future Windows Update on all devices with Windows platforms that are in-scope for IE retirement. It will follow the standard Windows update process as part of an optional preview “C” release followed by a “B” Patch Tuesday release. Given the cumulative nature of Windows Updates, IE disablement will persist in subsequent Windows Updates.
Note: As first seen with the Windows 10 January 2022 C "Preview" release, IE11 has an in-product banner notifying users of the upcoming retirement. This only shows on Windows versions affected by IE11 retirement. To configure, use the "Hide Internet Explorer 11 Application Retirement Notification" group policy found in the Local Group Policy Editor under Administrative Templates\Windows Components\Internet Explorer.
What you need to do to take action:
To take action, we recommend setting up Microsoft Edge in your organization. If your organization needs legacy browser support, you should set up IE mode in Microsoft Edge as soon as possible because this is a multi-step process.
· Use the Configure IE mode guided set up experience to set up IE mode in Microsoft Edge for your environment.
o Create an initial enterprise site list with sites you know are IE dependent.
§ Run Site Discovery in parallel to identify any unknown IE dependencies and add them to your enterprise list as you identify them.
o Get helpful set up tips by watching our IE mode set up webinar and reading our troubleshooting guide.
o Use IE Driver to automate end-to-end IE mode testing.
o Follow the steps here to manage your organization’s transition from IE11 to Microsoft Edge with IE mode.
Support:
· For cost-free help with web app and site compatibility, especially if you have legacy site concerns after configuring IE mode, learn more about the App Assure program.
Additional Information
· Read our June 15th retirement blog here.
· Read our FAQ to help answer your questions and use the troubleshooting guide during setup.
· Visit the Internet Explorer mode website.
· Watch videos from our IE retirement YouTube playlist to learn more.
· Learn more about hosting your IE mode site list in an authenticated cloud endpoint in the M365 admin center.
· Read our original announcement blog (May 2021) and browse our blog series for more information.
We always value feedback and questions from our customers. Please feel free to submit either feedback or questions via Message Center.
MC391126 — Internet Explorer and Microsoft Edge Legacy reporting will be removed from the Microsoft browser usage report
Following the upcoming retirement of the Internet Explorer 11 desktop application on certain versions of Windows 10 (June 15), updates will be made to the reporting in the Microsoft Browser usage report. Beginning at the end of June 2022, all reporting for unsupported Microsoft browsers will be removed. This includes the removal of Internet Explorer (IE) and Microsoft Edge Legacy. Reporting on usage for Microsoft Edge will remain available.
In addition, the current feature that allows IT admins to opt-in to sending users notifications to transition from IE to Microsoft Edge in Microsoft 365 Services will be removed starting at the end of June 2022. For admins that are actively using this feature, it will stop sending notifications to users as of June 15, 2022.
When will this happen?
Internet Explorer and Microsoft Edge Legacy usage reporting will be removed from the Microsoft browser usage report starting at the end of June 2022.
How this will affect your organization:
Administrators currently relying on Internet Explorer and Microsoft Edge Legacy information in this report in the Microsoft 365 admin center will need to adjust workflows where necessary to remove this dependency, as that information will no longer be available.
What you need to do to prepare:
Prepare for the report to be retired at the end of June 2022. If you would like to see historical data, we recommend you capture current reporting before the end of June.
Resources:
· Learn more about the browser usage report with the current documentation (this page will be updated when Edge Legacy and IE reporting are removed)
· Learn more about the Graph Rest API with the current documentation (this page will be updated when Edge Legacy and IE reporting are removed)
· Learn more about the retirement of the IE11 desktop application.
o Use a guided experience available in the Microsoft 365 admin center to help you identify any IE dependent sites in your organization
We always value feedback and questions from our customers.
MC390753 — Personal query history in Microsoft Search
Microsoft 365 Roadmap ID 93347
We're adding a new option in Microsoft Search that allows users to view and manage their personal query history.
When users get results for a search in Outlook, SharePoint Online, and Office.com, the issued query is recorded in their search history. A user’s search history is personal, it isn’t shared with your organization or with Microsoft. Their search history helps them quickly get back to things they’ve found before. As they type a query, matches in their search history are suggested back to them in the search box.
Users can review their search history at any time by downloading it. They can also clear their history at any time. Both actions are done from the My Account portal of their work or school account. Go to the Settings & Privacy page and open the Microsoft Search section. Recording of history can’t be paused.
When this will happen:
We will begin rolling out personal query history in early July and expect to complete the rollout by late July.
How this will affect your organization:
With personal query history, users will see recent search queries across SharePoint Online and Outlook (web) as they begin typing in the search box.
This prompt makes it easier to return to recently accessed insights and information. No need to bookmark or memorize your frequent queries.
Personal query history is managed and downloaded through the Microsoft 365 My Account settings.
What you need to do to prepare:
Review the Microsoft Search documentation for US Government environments at and the Microsoft Search documentation.
MC390412 — (Updated) We're adding more features to Microsoft Search in GCC
Microsoft 365 Roadmap ID 93248
Updated June 16, 2022: We have updated the content below to show as intended. Thank you for your patience.
We are expanding Microsoft Search in GCC. You already have:
· Organization-wide Search via the Search Box navigation header in SharePoint and OneDrive, Office.com, and on Microsoft Search in Bing
· Search suggestions based on Files, Sites, People, and Groups in SharePoint, OneDrive, Office.com
· People Answer, and Customizable Bookmarks and Q&A Answers
New features for GCC include:
· New search suggestions based on Bookmarks, Q&A and History on Microsoft Search in Bing
· Calendar, Files, and Acronyms Answers
· Image search in Microsoft provides a new search vertical to provide better search capabilities for images in your organization
· A new action menu with search results will allow an item not only to be opened in the web experience, but directly opened in the client application, downloaded, shared or copy the link to the item
· Microsoft Search Usage Analytics recently enabled in the Search and Intelligence Admin Center
When this will happen:
We expect to begin rolling out the new Microsoft Search features to GCC customers in July 2022 and we expect to finish by mid August 2022.
How this will affect your organization:
Microsoft Search brings work answers and search results to familiar search experiences, like SharePoint Online, Office.com, and Bing. End users can already enter search queries into the Search Box in SharePoint and One Drive and Office.com and get organization-wide search results. Our new features improve the search suggestions and search results pages, add Calendar, Files, and Acronyms Answers, and provide Search Usage Analytics and Reports from the Search and Intelligence admin center.
Search Admins will be able to customize Acronyms Answers (similar to the existing customizable Bookmarks and Q&A Answers) via the Answers tab in the Search & Intelligence admin center.
Search Usage Analytics and Reports can be found under Insights > Usage Analytics in the Search & Intelligence admin center.
When enabled, users who go to Bing.com and sign in with a valid work account can easily and securely find the work information they need with Microsoft Search in Bing. For GCC customers, Microsoft Search in Bing is off by default. Search Admins can turn on Microsoft Search in Bing in the Admin Center (Settings > Search & intelligence settings > Configurations > Microsoft Search in Bing settings). Choose Change settings and turn on Allow your organization to use Microsoft Search in Bing.
What you need to do to prepare:
For GCC customers, Microsoft Search in Bing is off by default. If you haven't enabled Microsoft Search in Bing yet for your organization, you can take these steps:
· Search Admins can turn on Microsoft Search in Bing in the Admin Center (Settings > Search & Intelligence settings > Configurations > Microsoft Search in Bing settings).
· Choose Change settings and turn on Allow your organization to use Microsoft Search in Bing.
Instructions to turn on Microsoft Search in Bing
Learn more about Microsoft Search and customizing Answers here
Find information about Microsoft Search in US Government environments here This documentation will be updated to reflect the new features as part of the release process.
MC388541 — Microsoft Project trial for Microsoft 365 users
Earlier this year, the self-service trial (MC306669 Dec '21) was rolled out for Microsoft 365 customers to try out Project. Starting in June 2022, Microsoft 365 users will also be able to try Project from “in-app” without payment. In this case, the in-app trial will be available either through Home in Project or in Planner – see the image below as an example. For future reference, in-app trials will become available in other Microsoft 365 apps, which you will receive notifications as these begin to rollout.
Note: These trial capabilities will be available worldwide except for India, starting first with the U.S. tenants. They are not available for Education or Government customers.
Key points:
· Timing: June 2022
· Trials: Beginning with Project Plan 1
· Available to: Microsoft 365 E1, F1, E3, and E5
· Control: Admin control - Manage self-service purchases (Admin)
How this will affect your organization:
Microsoft 365 users will see an option to sign up for a Project trial either from the menu of Home in Project or Planner using their AAD credentials. After the trial expires, they can either use a credit card to directly subscribe or contact their admin to acquire a Project subscription.
What you need to do to prepare:
To manage self-service trials, review your current self-service configuration and ensure it is set appropriately for the in-app trial experience appropriate for your organization.
Discover more on how to manage self-service licenses acquired by users in your organization by reviewing Manage self-service purchases (Admins) | Microsoft Docs.
MC384778 — (Updated) Microsoft 365 Admin Center: GroupID to be Hidden by Default in Microsoft 365 Active User Reports
Microsoft 365 Roadmap ID 93308
Updated June 2, 2022: We have updated the content below for clarity. Thank you for your feedback.
We will be hiding the GroupID variable in Microsoft 365 Usage Reports in the ‘Groups activity’ section of the ‘Active users – Microsoft 365 Services’ and ‘Active Users – Microsoft 365 Apps’ from June 2023.
When this will happen:
We will be rolling this out to all customers beginning in late June and complete roll out by late July.
How this affects your organization:
When this change is implemented, Administrative roles and the Report Reader role will not be able to view Group ID identifiable information in Microsoft 365 Usage Reports. This change will help companies support their local privacy laws.
What you need to do to prepare:
Global administrators can revert this change for their tenant and show identifiable user information if their organization’s privacy practices allow. This can be achieved in the Microsoft 365 admin center by going to the Settings > Org Settings > Services page, selecting ‘Reports’ and unticking ‘Display concealed user group and site names in all reports’. Showing identifiable user information is a logged event in the Microsoft 365 compliance center audit log.
You are receiving this message because our reporting indicates one or more users in your organization are using or have access to Microsoft 365 usage reports in the admin center.
Learn More:
· Microsoft 365 Reports in the Admin Center
MC376706 — (Updated) Microsoft Project usage data in Microsoft Admin Center
Microsoft 365 Roadmap ID 93278
Updated June 14, 2022: We have updated the rollout timeline below. Thank you for your patience.
Project usage data will soon be included in the Microsoft Admin Center Customer facing usage reports.
When this will happen:
We will begin rolling out in mid-June (previously early June) and expect to complete by late June (previously mid-June).
How this will affect your organization:
No action is needed to prepare, and there should be no impact to your organization. If desired, you will be able to view user and usage data for Project desktop (the on-premises desktop app as well as the Project Online Desktop Client) and Project for the Web in the Microsoft Admin Center (along with other products). We will initially show Daily Active Users as well as the number of Project visits. We will provide aggregated views for the tenant as well as per user views.
What you need to do to prepare:
No preparation needed. When we roll out this update, you will see Project data in your Microsoft Admin Center Usage reports section.
MC345833 — (Updated) Temporary Whiteboard collaboration for external and shared device accounts
Microsoft 365 Roadmap ID 66759
Updated June 9, 2022: We have updated the rollout timeline below. Thank you for your patience.
There's a configuration issue with the instructions previously sent for this feature. The external and shared device accounts will work on ODB storage if you have external sharing allowed for SharePoint sites, but if you do not, then these accounts will not work. We are working on a resolution and expect it to be available at the end of May and be fully deployed by mid-June.
Microsoft Whiteboard on OneDrive for Business (ODB) will be leveraging a new capability that allows temporary collaboration during a Teams meeting. This applies to device accounts from Surface Hub and Teams Meeting Room devices, as well as any users who are not in your tenant.
Note: This capability does not enable file-level sharing and does not grant access to the file. It provides temporary access only for the duration of the Teams meeting (similar to PowerPoint Live sharing during a meeting).
When this will happen:
Starting in early April and completing by mid-June (previously late May), this capability will be utilized by Whiteboard.
How this will affect your organization:
This capability is enabled by default. If you choose to disable it, users will have the following experience:
· External users in your organization will continue to see a message in Teams meetings that they cannot see the whiteboard.
· Users in a Teams meeting on a Surface Hub or Teams Meeting Room will not be able to join the whiteboard shared during a meeting. These users should join the meeting from another device to view and collaborate on the whiteboard.
What you need to do to prepare:
If you have the external sharing for ODB allowed, no further action is required. If you have external sharing disabled, you can leave it disabled but you must enable this new setting.
1. Connect to SharePoint Online PowerShell and enable this using the Set-SPOTenant cmdlet.
2. Set-SPOTenant -OneDriveLoopSharingCapability ExternalUserAndGuestSharing
These changes should take approximately 60 minutes to apply across your tenancy. If you do not see these options, please update the PowerShell module.
MC344411 — (Updated) Microsoft To Do iOS and Android apps releasing for GCC users
Microsoft 365 Roadmap ID 85590
Updated June 7, 2022: We have updated the rollout timeline below. Thank you for your patience.
The Microsoft To Do iOS and Android apps will soon be available for GCC customers.
Key points:
· Timing: We will begin rolling this out in late June (previously late May) and expect to complete rollout by late July (previously late June).
· Roll-out: tenant level
· Control type: admin control
· Action: review and assess
How this will affect your organization:
Microsoft To Do is a personal task management app that empowers users to track and focus on the things they need to get done. Your users with Exchange Online accounts will now be able to manage tasks through the To Do iOS app and To Do Android App.
Users with assigned licenses will be able to use the To Do iOS and Android apps.
· Learn how to assign Microsoft To Do license
What you need to do to prepare:
Depending on the SKU(s) you own, prepare to see one or more of the following new service plans – To-Do (Plan1), To-Do (Plan 2), To-Do (Plan 3), To-Do (Firstline).
You might want to notify your users about this new capability and update your training and documentation as appropriate.
MC335605 — (Updated) Microsoft To Do iOS and Android apps releasing for GCC users
Microsoft 365 Roadmap ID 85590
Updated June 7, 2022: We have updated the rollout timeline below. Thank you for your patience.
The Microsoft To Do iOS and Android apps will soon be available for GCC customers.
Key Points:
· Timing: We will begin rolling this out in late June (previously late May) and expect to complete rollout by late July (previously late June).
· Roll-out: tenant level
· Control type: admin control
· Action: review and assess
How this will affect your organization:
Microsoft To Do is a personal task management app that empowers users to track and focus on the things they need to get done. Your users with Exchange Online accounts will now be able to manage tasks through the To Do iOS app and To Do Android App.
Users with assigned licenses will be able to use the To Do iOS and Android apps.
· Learn how to assign Microsoft To Do license
What you need to do to prepare:
You'll be seeing the following new service plans – To-Do (Plan1), To-Do (Plan 2), To-Do (Plan 3), To-Do (Firstline).
You might want to notify your users about this new capability and update your training and documentation as appropriate.
MC318990 — (Updated) Forms: Allow up to 5 million Responses per Form/Quiz
Microsoft 365 Roadmap ID 87750
Updated June 21, 2022: We have updated the rollout timeline below for GCC organizations. Thank you for your patience.
Note: We will not be moving forward with this feature for GCC-High or DoD organizations at this time and the supported number of responses will continue to be 50,000.
The number of responses allowed per Form/Quiz is being increased from 50,000 to 5 million. After a Form passes 50,000 responses, the form can continue to collect additional responses and the Form owner can export the results as a .csv file for further analysis
When this will happen:
· Targeted Release is expected to begin in early March and will fully roll out for General Availability by early April. - Complete
· GCC: We expect to roll this out to government clouds beginning in mid-April and expect that rollout to be completed by mid-July (previously mid-June).
How this will affect your organization:
Customers can continue to use Forms as they do today. There are no changes to forms below the existing 50,000 responses limits and can still be viewed online with full functionality including graphs, summary, individual responses etc.
Forms that exceed 50,000 responses will not have all of the same functionality online but but can continue to collect responses and have those responses exported via .csv for further review.
What you need to do to prepare:
No action required but you may want to update internal documentation as needed.
MC318316 — (Updated) OAuth interface for Office 365 Reporting web service
Updated June 16, 2022: We have updated the rollout timeline below. Thank you for your patience.
Currently, users accessing Reporting Web service use “Basic Authentication” and must provide their credentials. With this feature update, Microsoft will improve the security of your tenant by replacing “Basic Authentication” access in favor of the recommended OAuth user interface which is where we will continue to invest our development resources.
Key Points:
· Timing: Rollout will begin in early May (previously mid-March) and is expected to be complete by mid-July (previously late May).
How this will affect your organization:
No immediate action required. Users could start migrating their programmatic access to Office 365 Reporting Web Service from "Basic Authentication" to "OAuth".
What you need to do to prepare:
You might want to notify your users about this change and update your training and documentation as appropriate.
Learn More:
Microsoft 365 IP and URL Endpoint Updates |
Documentation - Office 365 IP Address and URL web service
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.